Are you looking for a quick and easy solution to bulk modify Active Directory user attributes?
Then you are in the right place.
In this post, I’m going to show you the AD Bulk User Update Tool that makes it easy to bulk update active directory user attributes.
This is a GUI tool that updates AD user attributes from a CSV.
Let’s jump right into some examples:
- Bulk Modify Users Office Attribute
- Bulk Modify Users Department and Title
- Bulk Update User Employee ID and Employee Number
- Bulk Remove User Attributes
- Understanding LDAP Attributes (Cheat Sheet)
Example 1: Bulk Modify Users Office Attribute
In this example, I’m going to mass update the Office attribute for 378 AD users. If there is a value already present it will get updated.
The AD Bulk User Modify tool uses a CSV file to bulk modify Active Directory user accounts. All you need is the users sAMAccountName (user’s login name) and the LDAP attribute you want to modify.
If you are not familiar with LDAP attributes you may want to jump to the LDAP attributes section for a quick overview. I’ve created an LDAP cheat sheet to quickly find the correct LDAP values.
Step 1: Setup the CSV File
One of the following attributes must be present in the CSV template and will be used to identify the accounts to update.
- sAMAccountName (default)
- EmployeeID
- EmployeeNumber
- UserPrincipalName
For example, in the csv below I’m using the sAMAccountName column to identify the accounts to update.
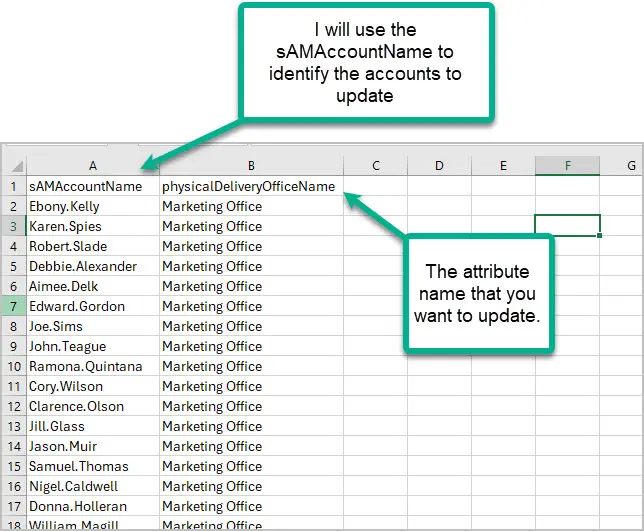
The next column needs to be the attribute you want to modify followed by the value. You can export users to a csv file using PowerShell or a GUI tool. This makes it easier to configure the CSV.
TIP: The Active Directory names do not always match the LDAP attribute name. This is how Microsoft designed it. This can be confusing and is why I created a cheat sheet that shows the most common Active Directory names to LDAP attribute names. See the end of this post for the cheat sheet.
Looking at the cheat sheet the LDAP attribute for office is physicalDeliveryOffice. Below is a screenshot of my CSV.
Step 2: Run AD Bulk User Modify Tool
Now the easy part.
Open the AD User Bulk Update tool, select the CSV file, and click run.
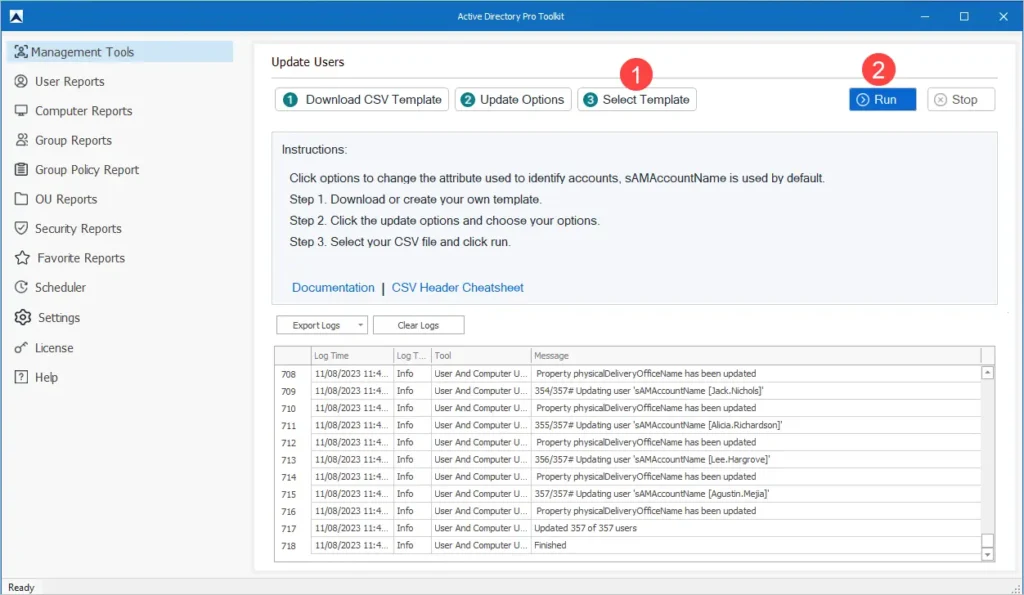
When the update is complete check an Active Directory user to verify the changes.
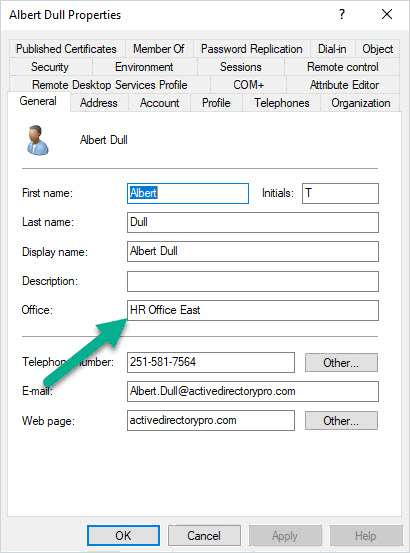
You can see above the user “Albert Dull” has had their Office attribute updated.
Step 3: Verify the changes
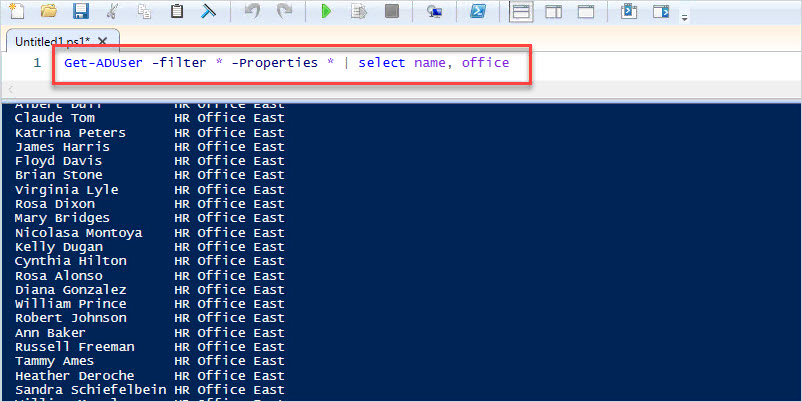
To verify the changes for all users you can use the below PowerShell command.
Get-ADUser -filter * -Properties * | select name, office
Another option is to check the logs within the bulk updater tool. The logs will track all changes and also log any errors. You can filter and search the logs.
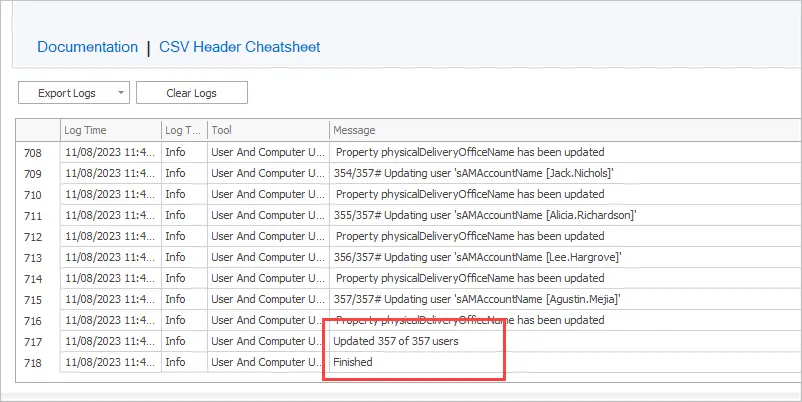
Looks great!
Example 2: Bulk Update User Department and Job Title
In this example, I will update the department and title attributes at the same time. You can modify as many attributes at once as you wish.
Again, if a value is already set it will be overwritten.
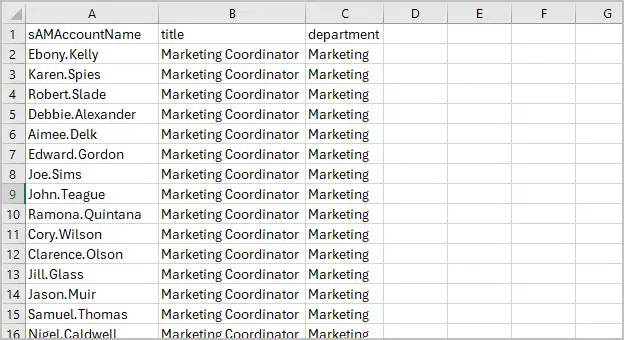
I look at the LDAP cheat sheet and see I need attributes department and title.
Now, I’ll enter the user’s info in the CSV file.
Ready to go, I’ll open the tool, select the CSV file, and click run.
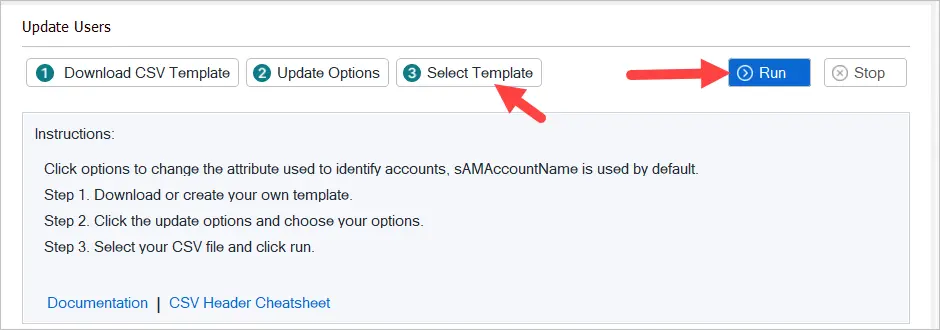
The tool runs and makes the changes set by the CSV file.
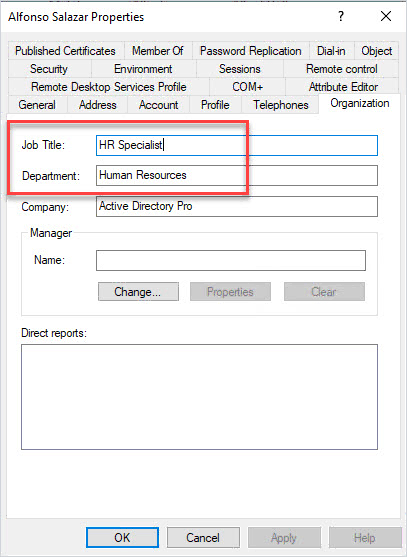
Now I’ll open an account to verify the changes.
To verify for all users use the below PowerShell command.
Get-ADUser -filter * -Properties * | select department, title
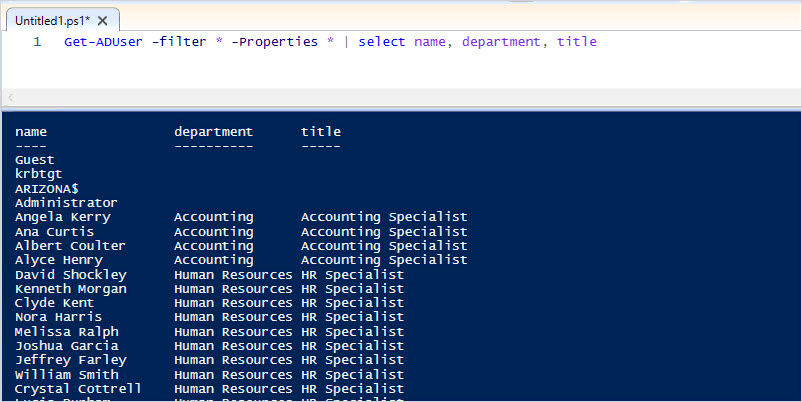
Perfect!
I just modified the department and job title for 300 users in 15 seconds.
Example 3: Bulk Update User Employee ID & Employee Number
In this example, I’ll update the Employee ID & Employee Number values for all the accounts in the HR department.
These two values only show up in the attribute editor, the values do not show up on any of the tabs in Active Directory Users and Computers.
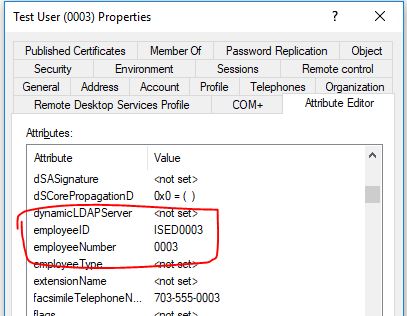
The LDAP attribute names are employeeID and employeeNumber.
I’ll update my CSV with the LDAP attribute name and set the values I want.
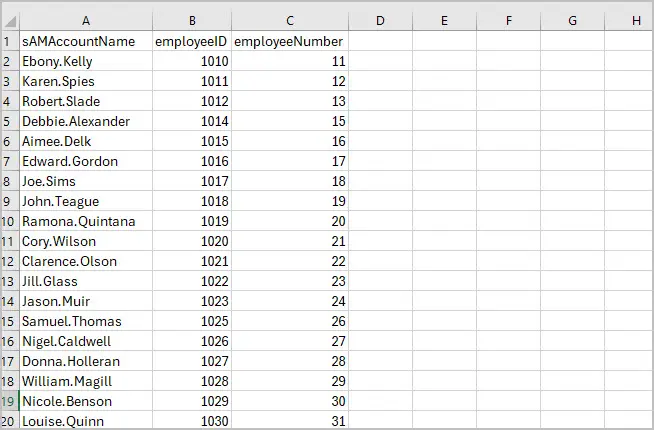
Now I’ll run the tool to update the attributes.

These two attributes are not available to add as a column in ADUC. So you will need to use PowerShell to mass verify the changes.
Get-ADUser -filter * -Properties * | select name, employeeid, employeenumber | sort name
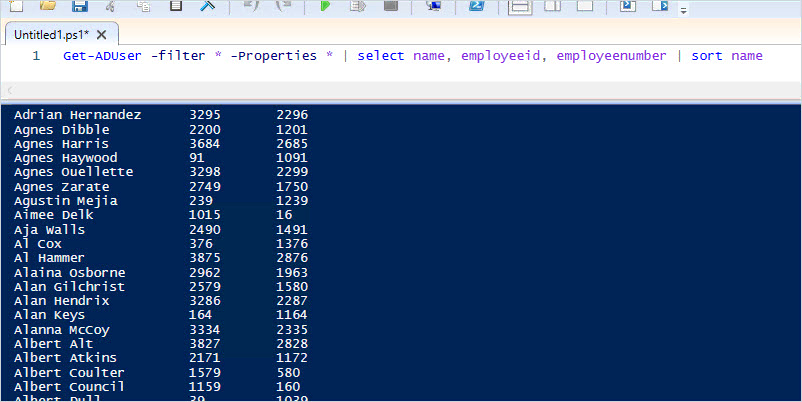
Looks good. I can scroll down the list and see all the HR accounts have been updated.
In about a minutes worth of work, I just updated the employeeid and employeenumber on 300 accounts.
Example 4: Bulk Remove User Attributes
In the first three examples, I showed you how to mass update user attributes but what if you want to bulk remove user attributes?
No problem.
The process is almost the same, just add the LDAP attribute to the CSV and for the value put remove.
I’ll remove the values for the employeeid and employeenumber.
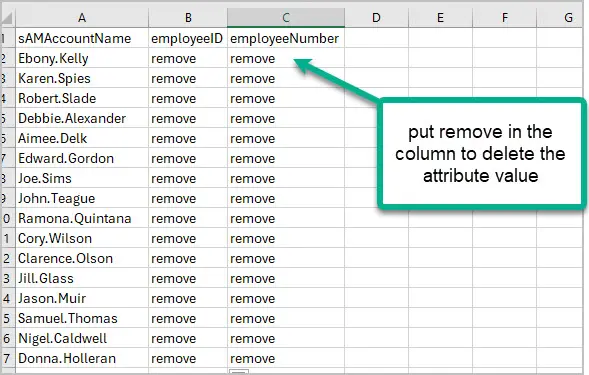
Now just run the tool, select the CSV and click run.
I’ll verify the changes in ADUC.
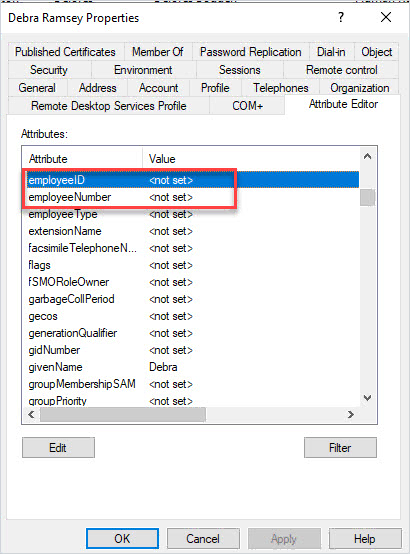
Looks good the values have been removed.
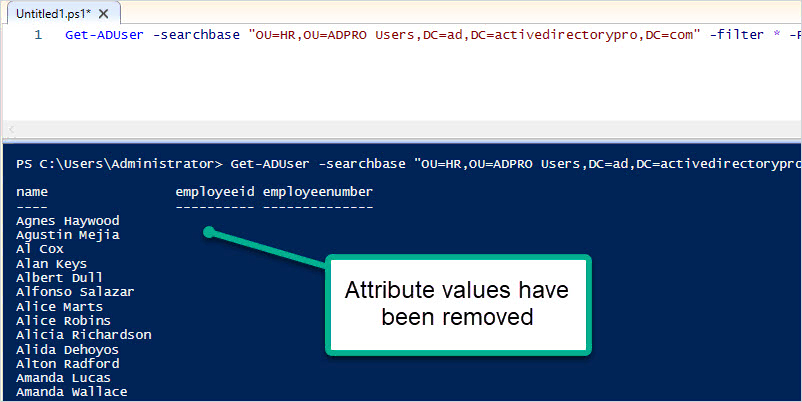
To verify with PowerShell use this command.
Get-ADUser -filter * -Properties * | select employeeid, employeenumber
Bonus! You can remove and update values at the same time.
Understanding the LDAP Attribute Names (LDAP Cheat Sheet)
Active Directory stores details about objects such as users into LDAP attributes. These attributes are basically a key value pair for example:
givenName = Robert
GiveName is the attribute name and Robert is the value.
This is the method Active Directory uses to store details about objects.
Here is where it gets a little confusing and is why I created the LDAP cheat sheet.
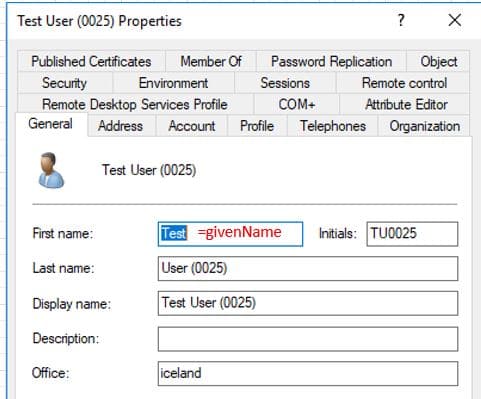
The field names you see in Active Directory Users and computers do not always match the LDAP attribute name.
For example, in ADUC the First Name field has an LDAP attribute value of giveName
Below is a table of the most commonly used ADUC fields and the LDAP attribute mappings. I’ve grouped them based on the ADUC tabs General, Address, Profile, Telephones, and Organization.
You can use this to quickly look up what LDAP attribute name to setup in the CSV file.
LDAP Attribute Cheat Sheet
This is a downloadable PDF.
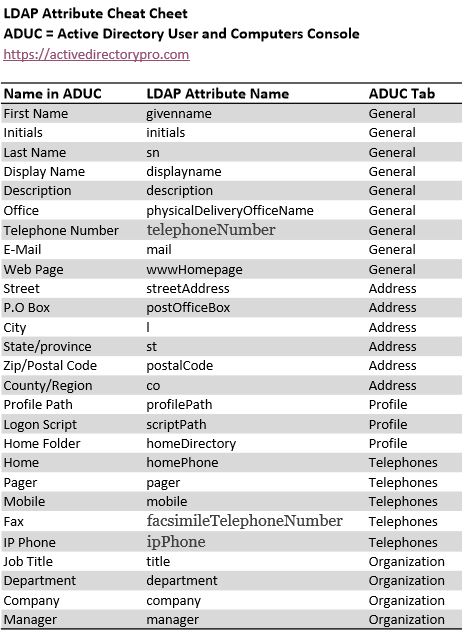
The AD Bulk modify tool is not limited to the table above, again those are just common fields. The AD Bulk Modify tool will update any LDAP attribute.
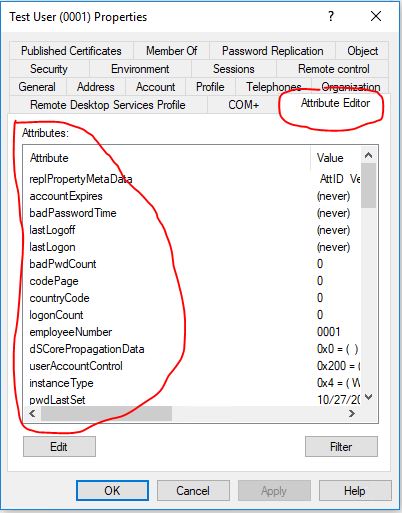
You can use the attribute editor on any account to find other attributes you may need to bulk update.
Screenshot of the attribute editor on an account, this lets you see all the attributes.
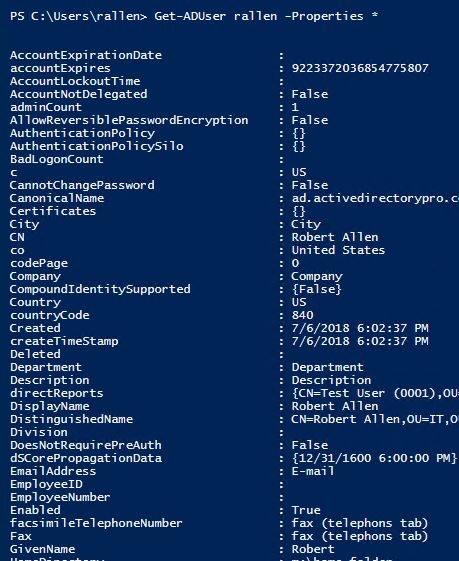
You can also use PowerShell to view the LDAP attributes.
Change username to the account you want to view
Get-ADUser username -Properties *
Final Thoughts
There comes a time when every administrator faces the need to make bulk changes to Active Directory user accounts. I have faced this challenge several times and have struggled with it in the past. With the AD User Bulk Update Tool this is no longer a problem for me or my team to deal with. This tool makes it very easy and saves a great amount of time when dealing with modifying user accounts.
This tool is included in the AD Pro Toolkit. You can download a free trial here.
Hi, I am working on a powershell to add new employees to the AD server but I am facing error when trying to addthe manager for new users and change the manager for existing users.
Please help me with script as I am unable populate manager fields
To modify the manager attribute use the set-aduser command.
Here is an example of updating the manager attribute.
set-aduser -Identity Agnes.Haywood -Manager adam.reed
I’ve got a complete how to guide on modifying the manager attribute.
https://activedirectorypro.com/update-manager-attribute-in-active-directory/
Can I use the user Bulk updater to Change all SAMAccountname to lowercase? I tried putting it in the csv as all lowercase to see if that would work, but it doesn’t seem as though it does anything.
Currently not supported. Why change it?
I am trying to update users phone numbers in AD and every line is giving an error “The server is unwilling to process the request”, what do I need to do to resolve this?
Thanks
Joe
Will this tool allow for a mass update of OUs for users?
The Bulk update tool update source is a CSV. What you can do is use the export tool to export all the users from the OU then use it with the bulk updater.
Does it work only on SAMaccountname as the Reference key/Filter , I have a requirement to update some fields but the only reference they can give me is the email address of the users not the SAMAccountname.
the secondary issue is that it’s likely the data they given me may have spelling errors etc in the email addresses, i can’t see any examples of the system handling errors in the input file or an output file that can be reviewed?
how does the system handle errors and is there a log file that can be reviewed.
Note:- the issue here is the request for change is coming from HR and they don’t want to work with the SAMaccountname.
The GUI tool is limited to the SAMAccountname. With PowerShell you can use distinguished name, GUID, security identifier (SID), or Security Account Manager (SAM).
Do you have the email address populated in AD? If HR is just giving you the email addresses you should be able pull the SAMAccountname by looking up the accounts based on email.
What are the least amount of privileges an AD account would need to be able to use the bulk modify tool to modify, let’s say, all the first/last names of all AD users in a domain?
You need modify rights to accounts. You can use the delegation wizard to delegate these rights out if you don’t want to give domain administrator rights.
Hi Robert,
Thanks for the great scripts, can you help if I have to update the manager attribute from another trusted forest what is the quick and scripted way to achieve this? I have added users in the DOmain Local group from the trusted forest it is not part of the same tree so only way to acheive is to import users in DL group and extract the foreign security principal.
Thanks any assistance will be great help.
after updating a field which was temporar, I tried to clear it. But it does not clear the filed, it adds the word “remove” in the field. I was trying to clear the city field.
This was a bug that was fixed. Please login and download the latest version.
Hi Robert
Is there any steps on how to change user account email in on premises active directory which syn to 0365
I have AD on prem and also has Azure AD + 0365 – normally the changes is done on local active directory
I did few test and was not able to log in to email account after changing the email from local AD
Any suggestion will be much appreciate
Sqito
The bulk update tool can update the email and proxyaddress attributes. Here is a guide I created that also shows how to do this with PowerShell.
https://activedirectorypro.com/how-to-bulk-update-proxyaddresses-attribute/
The Arabic characters are not supporting in the updater templates, as we use Arabic name in some fields for all users.
Matthew, email me the CSV file so I can test and get this working.
Thanks
Robert
This tool looks great and almost just what I need except there are 2 parts and you just have the user part.
There are user accounts and OU pc name accounts.
I would buy your tool if there was a way to bulk change info on both. So in the
computer ou ability to change -managed by
Thanks for the request. I’ll have my team check into this. Stay tuned!
Hi Robert,
I’m attempting a simple import as a test, but every attribute I try to update I get:
[06:08:14] INFO: Unable to set property: postalCode
Any ideas?
Thanks
Hi Tom,
Make sure you log in and download the latest version. If that doesn’t resolve the issue, please send me an email.
Great – thanks!
Thanks great tools. All work fine except for two feature I’d have liked with Bulk Update
Is there anyway to update the samaccountname? A number of ours were incorrectly created with uppercase names and we’d like them to conform to our organisation policy of all lower case – this feeds on to email addresses and other things. I know that the value doesn’t affect logging in and even bulk user update gets the right account if I use the new lower case only value but it doesn’t attempt to update it (no reason why it should). I tried adding it as a second column hoping it would recognise that as meaning I wanted a new value but it didn’t work of course – wishful thinking!
Hi Colin,
Currently my bulk user update tool does not have the option to update the samaccountname. I’ll try to add that in a future release.
Another option is to use PowerShell. Take a look at this example
https://stackoverflow.com/questions/20220616/powershell-set-aduser-modify-samaccountname/20222212
Thanks – I’ve found another little issue, part of which is about my setup which you might have an idea on but part of which needs a small correction in ythe template you provide for bulk update 🙂
When updating givenName and userPrincipalName on one DC, everything works fine. But on another (completely different network neither will update:
[18:55:31] INFO: Processing: z.hunt
[18:55:31] INFO: Looping through properties for z.hunt
[18:55:31] INFO: givenName property detected
[18:55:32] INFO: Actioning all property updates
[18:55:32] INFO: Unable to set property: givenName
[18:55:32] INFO: Looping through properties for z.hunt
[18:55:32] INFO: userPrincipalName property detected
[18:55:32] INFO: Actioning all property updates
[18:55:33] INFO: Unable to set property: userPrincipalName
[18:55:33] INFO: Done Processing z.hunt
The template file you give suggests using givename for the attribute but it should be givenName.
givenName works on one of my servers but not on the other – same problem with userPrincipalName
Any thoughts?
Colin,
Let me send you an updated version of the tool to see if that resolves the issue.
by me:
The term ‘set-adattribute’ is not recognized as the name of a cmdlet, function, script file, or opera
ble program. Check the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:1
+ set-adattribute
You will need to purchase and install the module. You can purchase the tool from this page https://activedirectorypro.com/bulk-user-update-tool/