In this guide, you will learn how to use group policy to create a lock screen policy. In addition, I’ll show you how to disable (exclude) the lock screen policy from specific users and computers.
In this example, I’ll create a policy that locks the screen after 15 minutes of activity. You can change the timeout settings to whatever meets your needs. This guide will work on Windows 10, Windows 11, Server 2012, and later operating systems.
Table of Contents
- How to Enable Lock Screen GPO
- How to Verify the Lock Screen GPO is Applied
- How to Disable the Lock Screen for specific computers
How to Enable Lock Screen GPO
Step 1. Determine GPO Location
The lock screen policy is a computer policy, this means anyone who logs into the computer will get the lock screen policy applied. Later I will show you how to exclude specific computers from the policy.
It’s best to apply this policy to all computers but there will always be exceptions. I’ve had requests to exclude conference room computers, computers that are used for 24/7 monitoring, then of course there are always a few users that complain and want it disabled. These requests should all be approved by upper management.
Depending on your OU structure you could apply the GPO to the root and let the sub OUs inherit the policy or you could apply the policy to specific OUs.
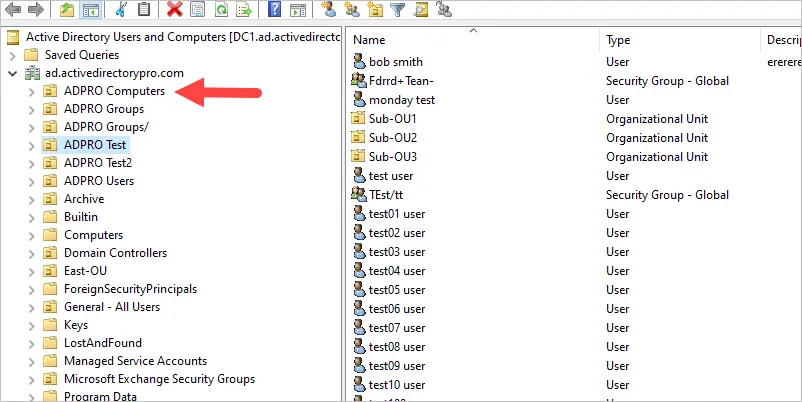
In this example, I want the policy to apply to all computers so I’m going to link the GPO to my ADPRO Computers OU. All the sub-OUs will inherit the policy. In step 4, I’ll show you how I exclude specific computers from the policy.
Step 2: Create a New GPO
Do not add these settings to the default domain policy. It is group policy best practice to not modify the default domain policy and instead create a new one.
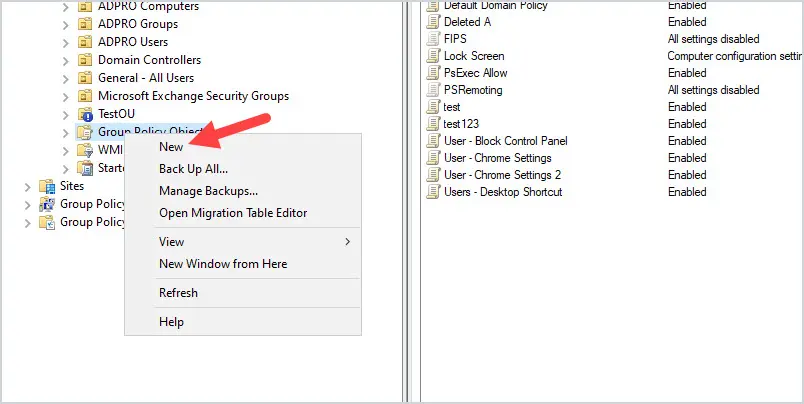
1. Open the group policy management console
2. Right Click “Group Policy Objects” and click new
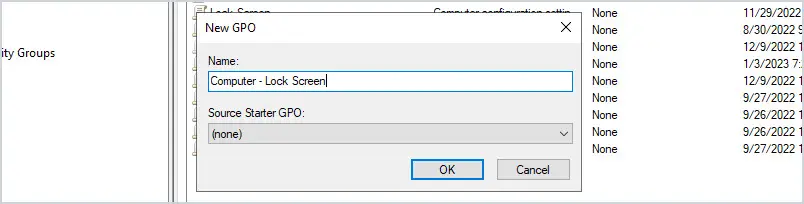
Give the new GPO a name. For example, I named my GPO “Computer – Lock Screen”.
The GPO is created but now we need to set the idle timeout settings.
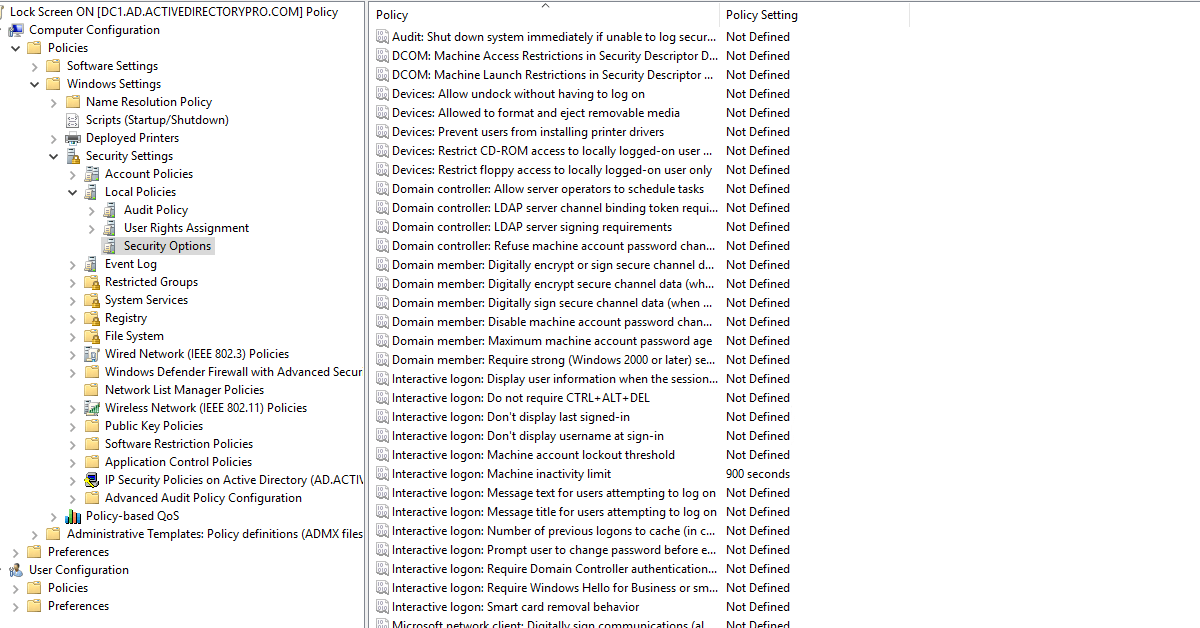
There is only one group policy setting that needs to be set. It is the “Interactive Logon: Machine inactivity limit”
Browse to -> Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options
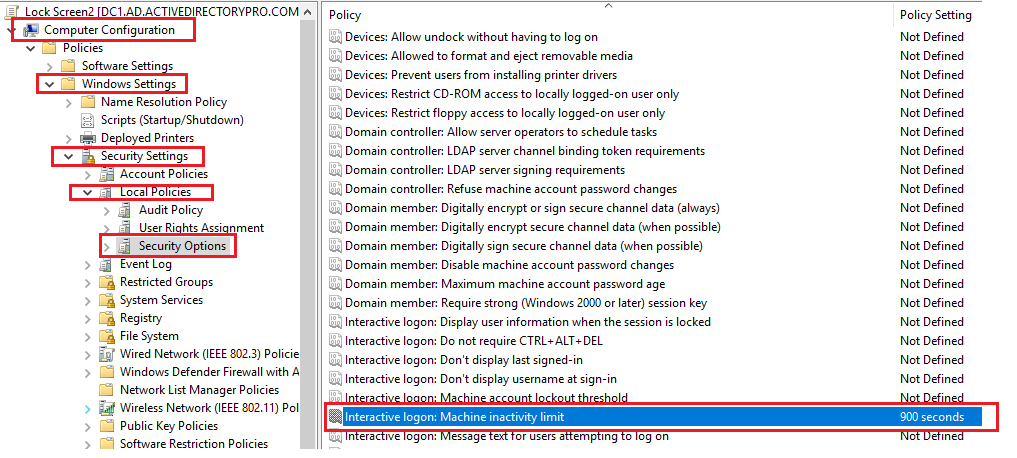
Change the value to whatever you want. I set mine to 900 seconds which is 15 minutes.
Step 3: Apply the Lock Screen GPO
The GPO is created and the policy settings have been enabled. Now you just need to link the GPO to the correct OU.
Since this is a computer policy you must apply the GPO to an OU that contains computer accounts. If you apply the GPO to an OU with users only the lock screen will not work.
1. In the group policy management console right-click an OU and select “Link an Existing GPO:
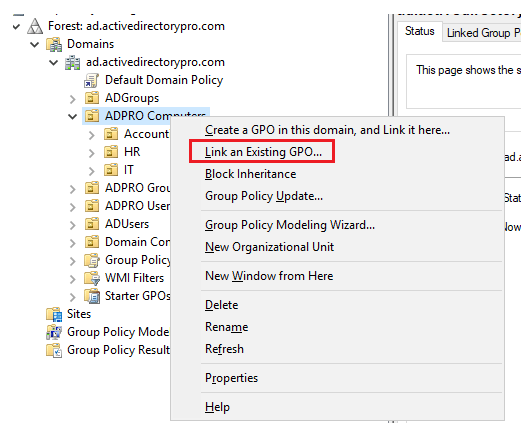
2. Select the GPO you created in step 2 and click OK.
The GPO is now linked.
The GPO refresh interval is 90 minutes on a computer. So keep in mind it could take up to 90 minutes before this policy gets applied to all computers. You can instantly refresh this by rebooting the computer or running the gpupdate /force command.
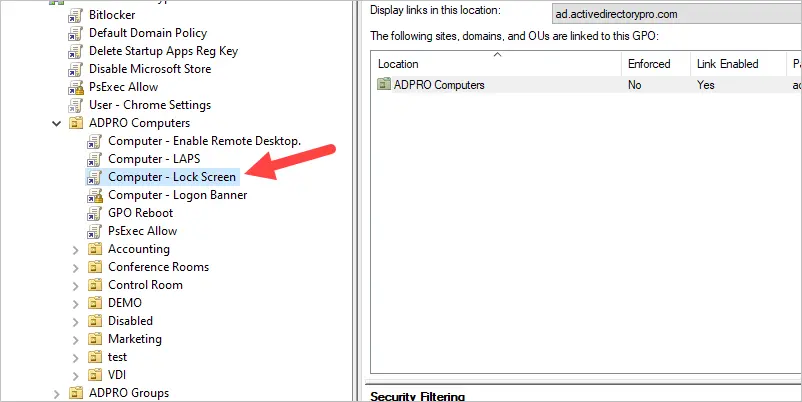
Above is a screenshot showing the GPO linked to my ADPRO Computers OU. All of the sub-OUs will inherit this policy. So computers in the Accounting, HR, and IT OU will get the lock screen GPO applied.
How to Verify the Lock Screen GPO is applied
To verify the GPO is applied to a computer you can use the gpresult /r command. You will need to open the Windows command prompt as administrator or it can fail to pull the computer policies.
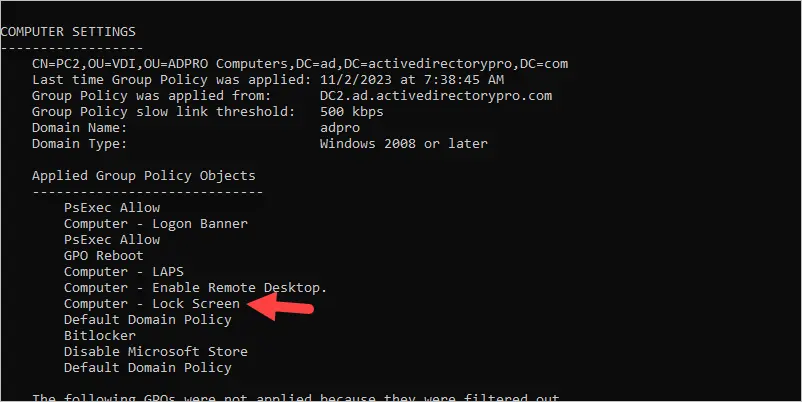
You can see above the “Computer – Lock Screen” GPO is applied to this computer.
How to Disable the Lock Screen for Specific Computers
Let’s say you have the lock screen GPO applied to all computers but now you need to disable it on specific computers.
There are two options:
- Option 1: Move the computers into a new OU and not link the GPO to this OU. This works and I’ve used this method for several clients.
- Option 2: Create a security group, add the computers, and deny the policy from applying to this group. This is my preferred method as I think it prevents moving computers around between OUs.
I’m going to show you option 2.
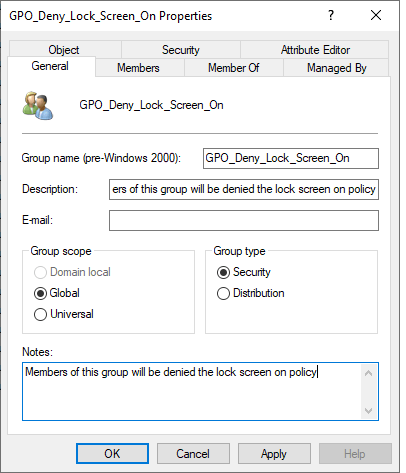
1. Create a security group and add the computers that you want the lock screen policy disabled on. It’s very important to name the group with a descriptive name and use the description box.
2. Go into the group policy management console, select the GPO click the delegation tab then click Advanced.
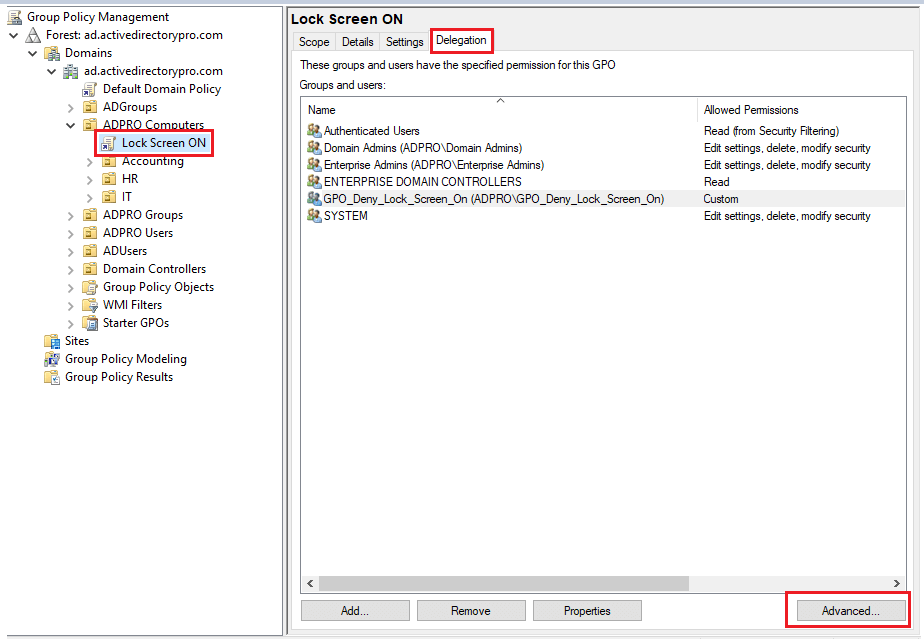
4. Add the security group and click ok
5. Make sure Read is set to “Allow” and Apply group policy is to “Deny”.
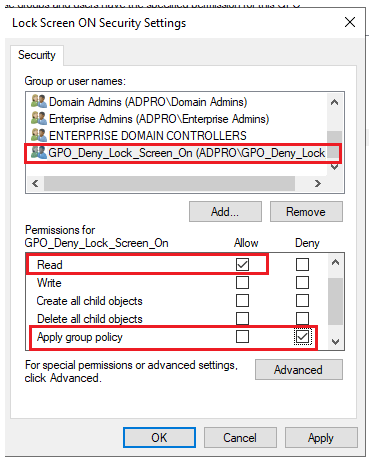
That should do it. The computers in your deny group will need to be rebooted.
When you check a computer with the gpresult /r command the policy will show as denied
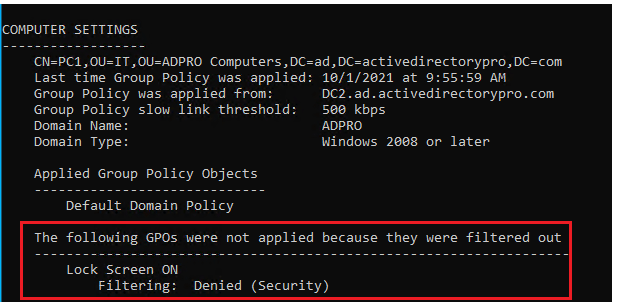
To deny any additional computers all you have to do is add them to the security group. I find this method more convenient than moving computers around to different OUs.
Download a free trial and create your own GPO reports.
Enforcing the lock screen on company computers is a very common requirement. Any company that gets audited will always get asked if this policy is in place, regardless it’s a good policy to have in place. Have fun with those exclusions.
This does not work for me for some reason. I have two completely separate domains (Work and Home). Both are running Server 2019 with a mix of Windows 10 Pro and 11 Pro machines. I have verified that the GPO is applying using gpresult /r. But the machines are simply not locking. I have rebooted them several times, re-verified the policy is applied and even waited overnight. But they do not lock. No screen saver is set on these machines either. Any idea what the issue could be?
This guide does not set a screen saver only configures the lock screen.
Run the rsop command and verify the policy settings from the GPO are applied to the local machine.
Hey there Robert. The policy did apply and works in that the screens are locking after 15 minutes. I just needed to wait it out. gpupdate /force and reboots didnt cut it. It took a full 24 hours or more and then screens started locking.
HOWEVER, the override is not working. On the PC’s I applied the override to, I can clearly see the Lock screen policy is not getting applied anymore. However, the original Lock Screen setting was left intact.
So yes, the machines initially had the lock screen policy applied. Then the decision was made to override for them (as per usual). But the screens are now still locking even after the policy is no longer being applied. Did you ever figure out why that is happening?
Part of me thinks I should create a send policy that changed the lock timeout value to 0 (never) and apply it to those computers in the override group. However, that would also mean that the same policy would apply to all the other workstations that are in the OU and not in the override group.
Thoughts?
Hi Robert – great article – thanks
The only issue we are having is that it only displays on one screen. I’ve read lots of articles about changing it within Windows, but not from a group policy. Any Ideas?
Thanks – Simon
How did you deploy the settings?
For multiple user accounts not computer need to disable lock screen, what group policy to be applied. They need the session to be active 24/7.
You would need to move them to an OU that does not get the lock screen policy. An alternative is to add them to a group and use GPO security filtering.
You never mention whether the GPO should be ‘Enforced’ (right-click – Enforced). Does that make a difference and if not, why? If so, why did you not mention it?
I would think the policy would not take effect even if it is linked until it is enforced, is this the correct way to think about it?
Enforced prevents overriding the policy settings. It’s a really bad name by Microsoft, it should be called NO Override. I’ve never had the need to set GPOs to Enforced.
They GPO works fine for 90% of my user. They other 10% lock out after 60 sec.
I can fixit by going into Screen Saver Settings. Turning it on, change the value 1 min to 15 min. And turn it back off. Now the user doesn’t lock out after 60 sec.
But why is this happening and can I make this change on a global scale ?
I’m having this same issue. Any luck with a resolution?
Thanks Robert,
I created a GPO to lock screen after 15 minutes. It worked on all domain joined computers. I then created a group to deny the lock screen policy for a specific Dept. and I can see that it’s denied using gpresult /r however those computers still lock after 15 minutes. Sleep settings are set to never. Any ideas?
Same happened to me.
Even if I disable the whole setting via GPO, computers in domain still have the last setting. I have no idea how to resolve this. How can I put all this back to default?
Same here! Did you figure out a solution for this?
I wonder if the screen lock GPO was applied first then you denied it. If it was applied first the denied option might not work because the registry is already changed. I need to test this.
it looks to be that a user with local-admin priv’s can change the actual screen-saver to a diff selection and then adjust the wait-time. Seems to require addt’l user-level settings in the GPO to completely nail that down ?
If the settings are not configured in a GPO then yes a local admin can change them. But it would be changing the local GPO settings and would only affect the local computer.
Hi Robert,
It worked to mine too.
BTW, do you have configuration of “Moderating Access to Control Panel”?
I tried to do the configuration Microsoft recommendation but it’s not working.
Thank you
Hi,
Yes, see this article.
https://activedirectorypro.com/restrict-control-panel-access-using-group-policy/
This worked for me with Windows 10 pro and windows 11, thanks!!
Hi, great article.
I have a small issue, I created a test Win10 VM. I joined it to my domain. I moved it to the OU i wanted to link the gpo with. I created the GPO and linked it. Did gpupdate /force. But for some reason the GPO is not being applied on that VM.
I waited 90minutes. VM and DC are on the same network. Another GPO is working.
Do you have an idea what it could be?
Thank you for
Double-check that you configured a computer policy and not a user policy.
Try these GPO troubleshoot steps.
https://activedirectorypro.com/group-policy-guide/#troubleshooting-group-policy
Hi Robert,
I create the lockoff GPO in 2 mins (120 sec) to test.
the GPO applied to the client work station properly (Windows 10 enterprise), and I check the local GPO and see it there. But it doesn’t lock off after 2 mins; even I waited longer than that without any activities. You have any idea? Thank you!
How is this achieved on Windows 11? This GPO does not work.
Just tested this on Windows 11 and it works.
Thanks so much, Robert. These steps worked for me.
Hello,
Is there a way to log off the user after 30min of inactivity?
If they are RDP sessions there are some GPO policies that can handle this. For console logons, you would have to create a scheduled task like this https://community.spiceworks.com/how_to/37465-auto-log-off-users
Hi,
works geat.
Is there a way to do the following:
After 10 minutes => show lock screen
After 30 minutes => show screensaver
When i set the “Interactive Logon: Machine inactivity limit” parameter, the screensaver is starting immediately.
Many thanks.
Hello, I can’t see the “local policies” in the security settings. Windows server 2019.
Your path is incorrect, according to your picture. Should be:
Browse to -> Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options
Thanks, I have updated it.
How do i browse to this Computer Configuration?
Just to let you know that you need to use Windows 10 Enterprise. This isn’t supported with the Pro version.
Eric, that is incorrect. This works and is supported with the pro version.
Thank you for the reply and for the references to other policy management solutions.
Appreciate it.
-Dave
No problem. There are other solutions those are two I’ve used recently.
Does this setting assume (and only work for) domain-connected workstations? How does it affect a remote user? A domain user, but who is working off the domain?
Does “Interactive logon: Machine inactivity limit” require that the user have their password checked by a domain controller after x minutes, or will the local “cached credential” will be accepted and unlock the workstation?
If some (most nowadays due to WFH and COVID) users are not connected to the domain (no VPN, not using Azure AD), there will not be a server available to confirm their password.
The screensaver on the other hand, doesn’t actually authenticate the user, it will allow the user into the computer if the correct “cached credential” password is entered.
The computer would need to connect to the domain at least once to download the GPO lock screen policy, it would then work offline.
There are other options for pushing policies out to non-domain-joined computers such as Intune and PolicyPak.
hi sir,
as per your steps, I’m applied on my network same steps.
my policy his applied but my lock screen not showing.
What is the best way to change the lockscreen image for Windows 10 Pro with a domain GPO? Can that be done?
Hi, Bill
There is a GPO for this called “Force a specific default lock screen image” policy location is -> Computer Configuration > Policies > Administrative Templates > Control Panel > Personalization
You will need to host the image in a location that can be accessed by all computers such as a file server (with a shared folder).
Hi there,
is there a way to make this work for multiple images?
for a company for instance – group policy
Hi Robert,
Thanks for replying and for a really helpful AD/GP website!
I did get this to work.
What are your thoughts on the Microsoft Article and why they state the Screen Saver needs to be enabled? Its seems misleading.
Hi Robert,
It seems according to Microsoft’s own article you have to Enable the screensaver setting under the User Configuration for this to take affect.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-machine-inactivity-limit
I would be glad to know if you found another way around that would allow the screen to lock without using the User Configuration – Enable Screen Saver setting?
Did you try the steps in my guide? I double-checked and it works. You don’t need to enable any screensaver settings (user configuration or computer).
I tested with a windows 10 computer running 2019 domain controllers.
Hi Robert,
Thanks for replying and for a really helpful AD/GP website!
I did get this to work.
What are your thoughts on the Microsoft Article and why they state the Screen Saver needs to be enabled? Its seems misleading.
The screen saver is different than the lock screen so not sure why they said it should be active. It might be saying the lock screen also activates when the screensaver activates.
Hi Ryan, thanks for the link to the that article it has answered a question that arose from following the steps above.
From what I can read in that article from Microsoft they can’t make up their mind. The screen saver doesn’t have to be active to force the logout in my opinion. The inactivity setting being defined actually affects the screen savers behaviour not the other way round. If you define inactivity limit it doesn’t matter if the screen saver is not set to require a login or if the screen time out in power saving kicks in first you will still need to log in again no matter what.