In this guide, I’ll show you how to remove local admin rights using group policy.
I’ll also show you how to add users or groups to the local administrator group.
By using group policy you can gain control over local admin rights and ensure no user is added back to the local administrator group without your approval.
Topics in this guide:
- Create a Report of Users with Local Administrator Rights
- How to Remove Local Admin Rights Using Group Policy
- Create a New GPO
- Run gpupdate or Reboot Computer
- Excluding Computers from the GPO Policy (Allow certain users to keep admin rights)
Why Local Administrator Rights is a Huge Security Risk
You do not want your users to log into computers and perform daily work with administrator rights. Exploiting administrator rights is a primary method attackers use to spread and gain control of systems inside an organization.
Scenario 1: A user is logged in to their computer with administrator rights, this person is fooled into opening an email that contains a malicious attachment. This attachment contains executable code and is executed on the computer. Because the user is logged in with administrator rights this malicious code has full rights to the computer, it could install a keylogger, sniffer, run ransomware and encrypt all the files, install remote control software, and so on. Not good.
Scenario 2: Someone..maybe a helpdesk tech created a local user on multiple computers with the same password and added it to the local administrator group. If an attacker cracked this password the attacker then has administrator access to all the machines that this account is created on. The attacker could then move laterally from system to system dropping malicious files, stealing data, and so on.
Both scenarios can be mitigated by getting control of your local admin groups. Now… Let’s move on to the tutorial.
Create a Report of Users with Local Administrator Rights
It’s very important that you first run a report on all computers to see who has local admin rights. Then review this report with staff members to discuss why these users or groups have local admin rights on their computers. The next step would be to get approval to remove these users.
I’ve been through this process with large organizations and people get very angry when you remove their admin rights. Plus things can break. I highly recommend you communicate these changes and get proper approval.
In this example, I’ll be using the AD Pro Toolkit to create a local admin report.
Here are the steps:
1. Download and Install Toolkit – You can download a free trial here.
2. Open toolkit -> Local Admin Report
3. Select Search Options (Select the entire domain or an OU/Group)
4. Click Run
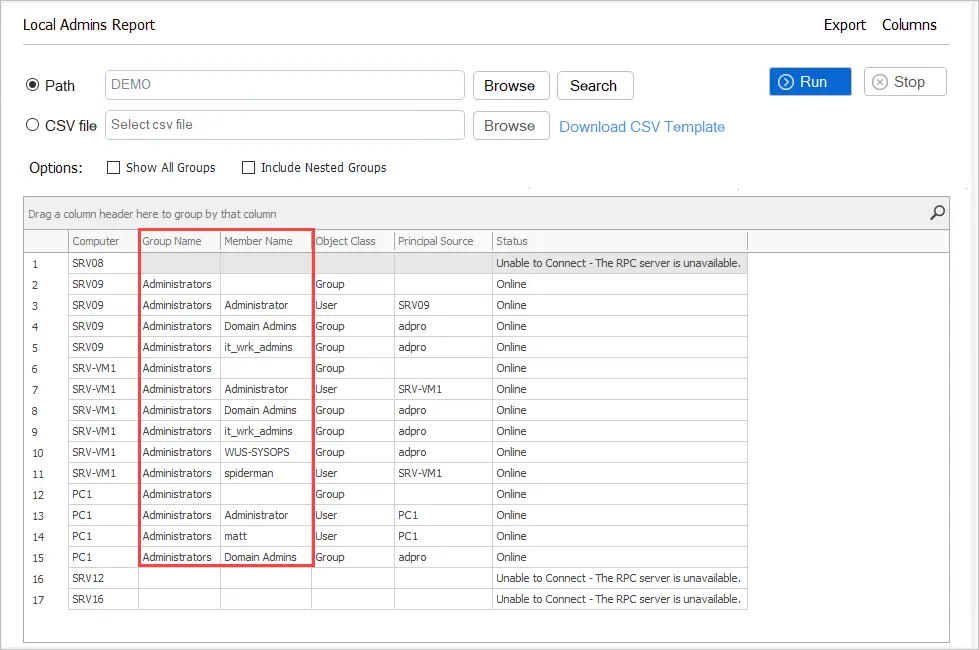
When it is done running you can sort and filter on any column. You can export this report to CSV for your records. It’s a good idea to share this report with staff so they have an idea of who has admin rights and who will be removed.
How to Remove Local Admin Rights Using Group Policy
Tip: I recommend you test these changes on a single computer or user before implementing them on all production systems.
First, let’s check a computer and see what accounts are in the local administrator group. This can easily be done by using the following PowerShell command.
Get-LocalGroupMember administrators
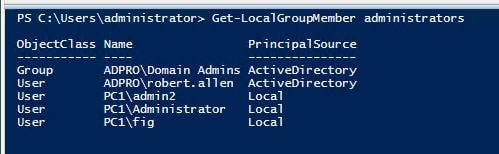
You can see in the screenshot there are several local and domain users in the administrator group.
You can also get this report from the AD Pro Toolkit.
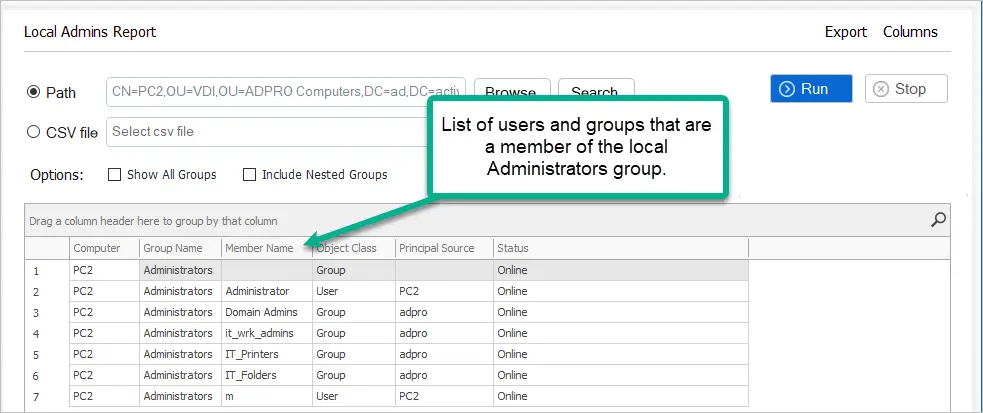
This is bad.
You can see PC2 has a local user and three domain groups that are a member of the local administrator’s group.
Using group policy I can not only remove these accounts but I can control what user accounts or groups are members of this group. If someone tried to manually add a user to this group the group policy would override it.
I like to put all computers in an organizational unit, this makes it easy to apply group policies to computer accounts.
Create a New GPO
Step 1. Right-click the organizational unit where you want the GPO applied and select “Create a GPO in this domain, and link it here”
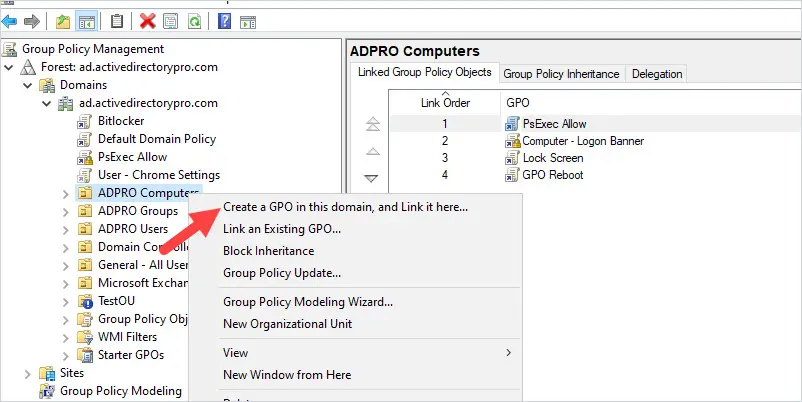
Step 2. Name the GPO and click OK
Now you need to edit the GPO.
Step 3. Right-click the GPO and click edit
Step 4. Browse to the following GPO settings
Computer Configuration -> Preferences -> Control Panel Settings -> Local Users and Groups
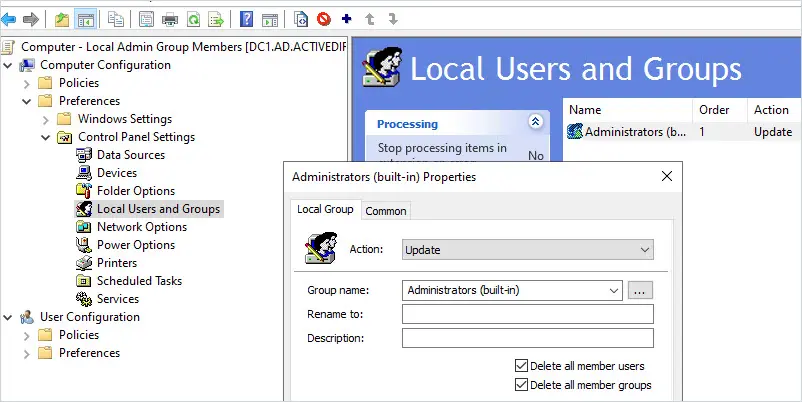
Now right-click in the right side window and select new -> Local Group
New Local Group Properties
- Action: Update
- Group name: Administrators (built-in)
- Delete all member users: This will delete all the users from the local administrator group. I’m going to check this box.
- Delete all member groups: This will delete all the groups from the local administrator group. I’m going to check this box.
Members:
Click add and select the members you want to be added to the local administrator group. You probably want to keep the local administrator account and domain admins group as local admins… but that is totally up to you. I’m going to also add a group that has the helpdesk staff so they have local admin rights on the computers.
Screenshot of my settings
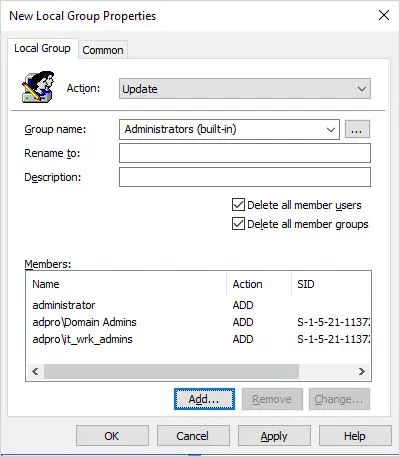
The above settings will delete all users and groups from the local administrator’s group and then add back the users specified in the member’s box. This will clean up all unwanted accounts and add only the accounts you have approved via the GPO.
Note: A user with admin rights could still modify the group membership locally but when the GPO refreshes it will revert back to the GPO settings.
Run gpupdate or Reboot Computer
Now that the GPO is created and linked to an organizational unit let’s test it.
On PC1 I will run the following command to force a group policy update.
gpupdate /force
Once the command completes I’ll check the group membership again. Below is a screenshot of the before and after. You can see the GPO has removed the members of the local administrator group and configured the members to the GPO settings.
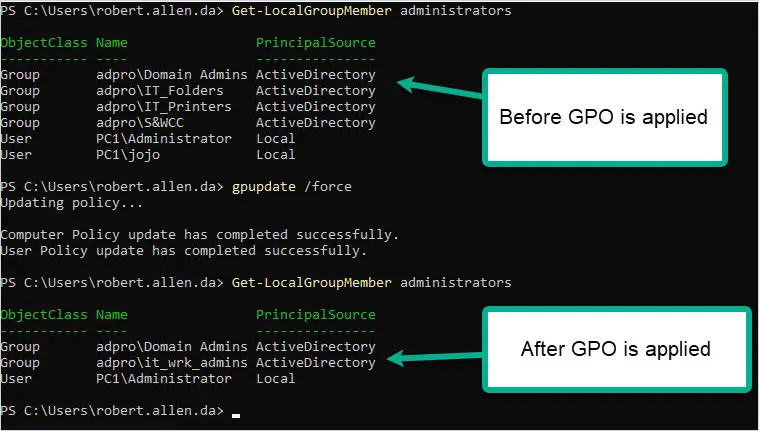
Pretty cool right?
You can see from the screenshot that the unwanted accounts have been removed from the administrator group. The GPO removed three groups and two local user accounts. It then added the domain admins group, the IT_Wrk_Admin group, and the local administrator account.
Any computer you apply this policy to will get these exact settings. If you choose to delete all member user and group accounts it will indeed remove those accounts from the local administrator’s group. I recommend you test this before rolling it out into production.
Exclude Computers from the GPO Policy
If you need to exclude a computer from this policy follow these steps:
Tip: There are many poorly coded programs out there that don’t run without giving users admin rights. If you can avoid these programs please do so. It’s ridiculous that there are still companies selling software that cannot run with admin rights…again try to avoid these programs. If you can’t then look into privilege escalation programs like BeyondTrust and PolicyPak. These programs allow you to configure programs to run without giving the user administrator rights.
Step 1. Create a new active directory group. Name it whatever you want.
Step 2. Add the computer account that you want to exclude into this group.
Step 3. In the group policy management console, select the GPO you created and select the delegation tab.
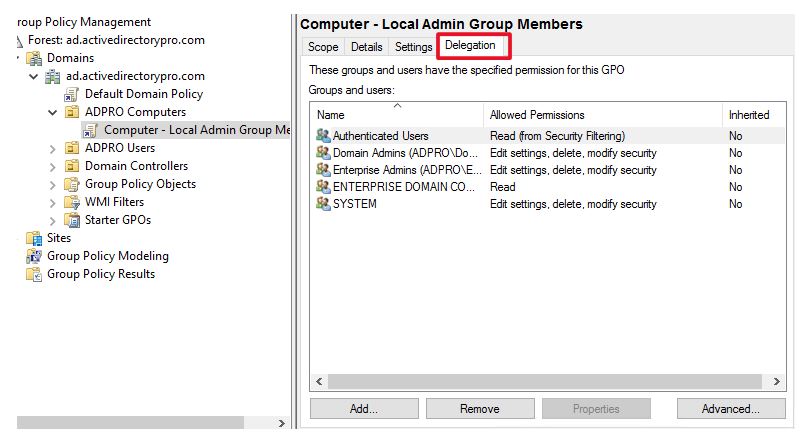
Now click the advanced tab
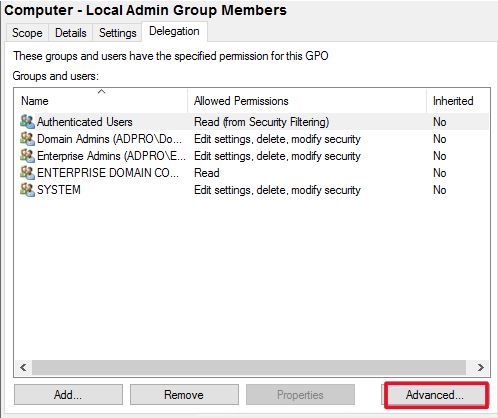
Click add and select the group you just created.
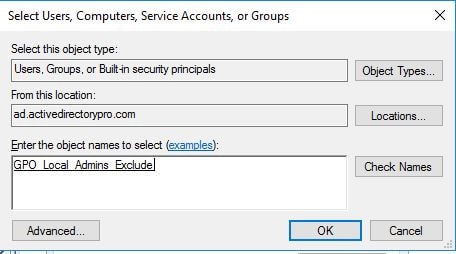
Now make sure this group has only these permissions:
Read: Allow
Apply group policy: Deny
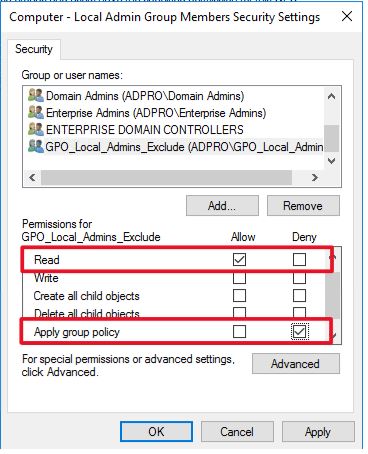
This will deny any member of this group from applying the GPO. This is a very simple approach to excluding computers from applying this GPO. It also makes it easy to manage, if you want to know who is excluded from a GPO you can just check the members of the AD group.
Now, I’ll verify the computer is excluded by using the gpresult command.
To see all the GPOs applied to a computer and user type this command.
gpresult /r
You will need to be an administrator on the computer to get the computer results.
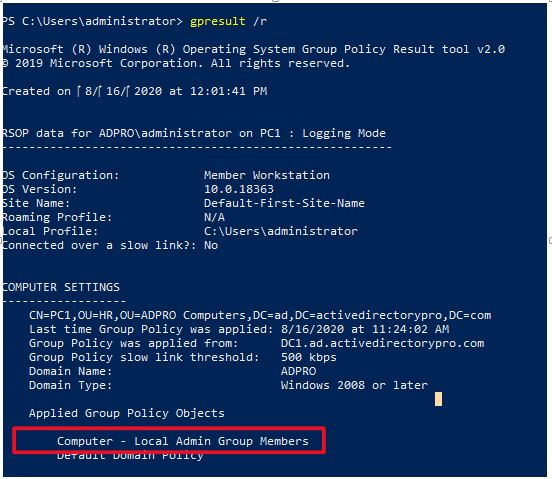
You can see the GPO “GPO Computer – Local Admin Group members” is applied to this computer. I will reboot the computer and run the command again. Once I reboot I should no longer see that GPO being applied to this computer because it’s being denied from applying.
I will run gpresult /r again
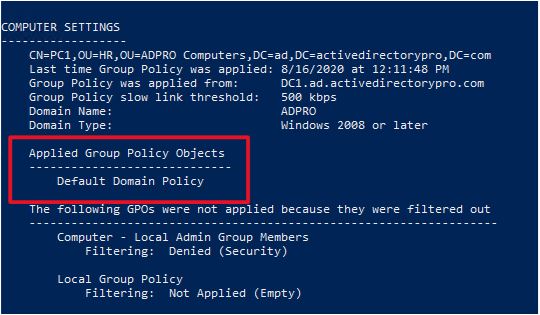
You can see the GPO is no longer applied to this computer. To learn more about filtering group policies check out my group policy management guide.
Tip: You should first do an audit of user rights and understand why they have local admin rights. You don’t want to enable this policy on all computers without first testing and understanding its impact. Unfortunately, there are programs that still need elevated rights, and applying this policy could break and prevent programs from running.
You can use the AD Pro Toolkit to easily create a report and export it to CSV file.
If you have any questions post them in the comment section below.
“Exclude Computers from the GPO Policy”
Why not use item level targeting instead of doing it this way ?
Yes, you can use item level targeting for this.
I’ve had this working for a couple months now, but recently had a problem with a user’s laptop at home via VPN. It seems that the GPO ran and deleted all members and groups from the local administrator’s group, but then didn’t add anything back in, so now the local Administrators group is empty and they are having problems. We have tried rebooting and gpupdate /force but cannot get anything back into that group. Seems like the only option is to rebuild, but not sure.
My guess is it’s an issue downloading the GPO from the DC due to being connected via VPN. Is it possible to bring the laptop into the office and connect to the LAN? Maybe it will update and add the users back while connected to the LAN instead of the VPN. Strange that it deleted everything but didn’t add anything back.
Hi
Is there a way to not remove some specific users from the admin local
And can I ban to not add user (user removed admin local) to admin local anyone
Thanks you by advance for your help
This is not working for me. I created the GPO and chose the “Delete all members users” and the “Delete all member group” and chose to Add Domain Admins and LocalAdminGroup.
I added to specific OU’s cause I don’t want touch servers. I enforced the GPO too. I ran a report and it still shows the same users are local admins.
From the computer, open the command prompt (make sure it is running as administrator) and run the gpresult /r command.
Is your GPO listed under “Applied Group Policy Objects” in the computer settings section?
Hi
How to remove admin groups in AD for disabled user
Hello Robert,
Thanks for a helpful article! How could one exclude some individual account that have the same naming pattern (ex. LADMIN-xxx) from those accounts that are being deleted? Thus we want to remove everything except those that are in a specific format. Is that possible at all?
I don’t know of a way to exclude by pattern name. What you could do is put these accounts into a security group and then deny read access to the GPO. This would block the GPO from applying to the accounts in the group. Or you could target users in a group and use item level targeting.
how would you add a local admin account to the local administrator group.
I have my action set to: update
members: Action:
domain admins ADD
administrators ADD
localadmin ADD
waitied for an hour and still no changes applied yet
how would you add a specific security group to only few workstations and not all in the environment.
need abc security group to be added to power users group locally
how to apply GPO to only hit the ABC security group folks
You can use item level targeting to apply a GPO to a specific security group.
Was able to remove all groups, but it only added back the local admin and none of my other groups.
hi
Actually, I got it working . My bad . Thanks for great KB 🙂
That is great. Glad you got it working.
What did you use to run a report that would show all users with local admin rights? I have been looking to do that but have not found a reliable method.
Thank you!
Hi Robert
I removed some days ago all admin rights on all local acounts(I checked delete all member users and I delete all members group). For the moment only specific AD users member of a group named LocalAdmin are Admins.
I realized that it could be a good idea to have a local user on each computer with admin rights : for example in case of link broken with the domainServer (ex: workstation ejected from the domain for any reasons…)
So I would like to update my GPO by adding a localuser for each workstation. Do you think it is still possible?
If my user is named localPerson on all workstation, I just have to add LocalAccount into members area?
thank you by advance for your help
To add a local user just put the username without the domain in the GPO, like this.
user1
adpro\workstation admins
adpro\helpdesk
You will have to create the local account first, this does not create it.
Great article, just a few comments:
We use this for years now and in our group policies we removed the local admin from the administrators group too. That said, we found that still the local administrator is a member of the administrators group on every system!
Individual administrators can be added by using variables in the GPO and matching groups in AD. So for example %DomainName%\%computername%_admins in the GPO. Only thing you should keep in mind is that this could be abused of course and so assign to the lowest OU possible.
Finally you can stack up several policies from highest to lowest OU. For example the first GPO on domain level removes all members, the second on highest OU level adds the DomainName\Workstation_admins, the third adds the DomainName\US_Sales_admins on the US Sales OU and on the Washington Sales OU the fourth GPO adds the mentioned %DomainName%\%computername%_admins to the local administrators group then on all computers for those a corresponding AD group exists.
Thanks for sharing. I’ve also been using something similar for years now, it really helps to keep control of the local admin group. Prior to this, I would run reports on who is in the local admin group and then complain to the helpdesk to stop adding users as local admins. This put an end to that nightmware.
I dont know why, but instead of add admin group to group Administrators (built in) it create another group with that name and add admin groups here. I cant find why. GPO is applied. But doesnt work. Any idea?
That is strange. I would delete the GPO and re-create it.
Do you need to specify %computername%\administrator or administrator or any local username should work?
just the account name. You do not need to put %computername%\
Hi Robert i have a question i have set this policie so now each local computer has an local account without admin right. A few dans later I would like to set admin right to the local account for 2 workstation. Is it possible to do it ?
Thanks you by advance for your help
Yes. Just create a new GPO that gives the local account admin rights and apply it to just those 2 workstations.
Great!
Great information but I have a question. When you delete all member users and then add the local administrator account back in, what is the password for the administrator? Does it remain the same that it was prior to being deleted by putting a check in the box to delete all members?
Thanks!
The password is the same. It doesn’t delete any accounts on the local computer it just removes them from the administrator group.
What if the account didn’t exist? Say for example all new computers you set up an account named Owner that you want as an admin on the local machine as well, but maybe that account didn’t exist on some of your older machines. If it didn’t exist on the computer before, does it create that Owner account or just ignore it? If it creates it, what does it use as the password?
It will not create the user if it doesn’t exist, it will just ignore it.
You should use LAPS for local admin accounts.