In this guide, I’ll show you how to find inactive Computers in Active Directory with PowerShell and the AD Pro Toolkit.
Inactive computers can lead to big problems such as inaccurate reporting, group policy slowness, software distribution issues, and security issues.
Find Inactive Computers in Active Directory with PowerShell
In this example, I’ll use the Get-ADComputer PowerShell command to find computers were the LastLogonDate has not been updated in at last 60 days. This means no one has logged into the computer for 60 days or more.
Step 1. Open PowerShell as Administrator.
Step 2. Copy and run the command below.
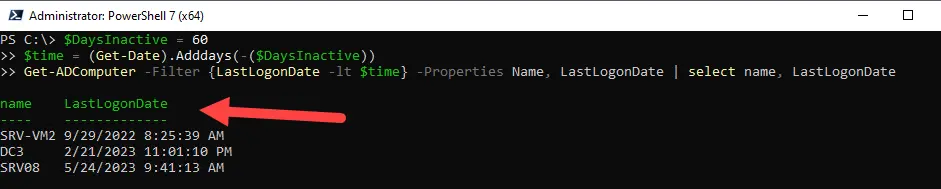
$DaysInactive = 60
$time = (Get-Date).Adddays(-($DaysInactive))
Get-ADComputer -Filter {LastLogonDate -lt $time} -Properties Name, LastLogonDate | select name, LastLogonDateBelow is a screenshot from my domain.
Step 3. To export the list of inactive computers, use this command.
$DaysInactive = 60
$time = (Get-Date).Adddays(-($DaysInactive))
Get-ADComputer -Filter {LastLogonDate -lt $time} -Properties Name, LastLogonDate | select name, LastLogonDate | export-csv -path c:\temp\inactivecomputers.csvYou can change the inactivity time to anything you want. For example, to change it to 90 days change this line.
$DaysInactive = 90Find Stale and Inactive Computers with the AD Cleanup Tool
The AD Cleanup Tool makes it very easy to find inactive computers in Active Directory. This tool is part of the AD Pro Toolkit and includes multiple AD management tools and reports.
- Quickly list all stale user and computer objects
- Automate inactive user and computer reports
- Delete, Move, Disable or Export inactive computers to CSV.
Step #1: Open the AD Cleanup Tool
Click on AD Cleanup from the left menu.
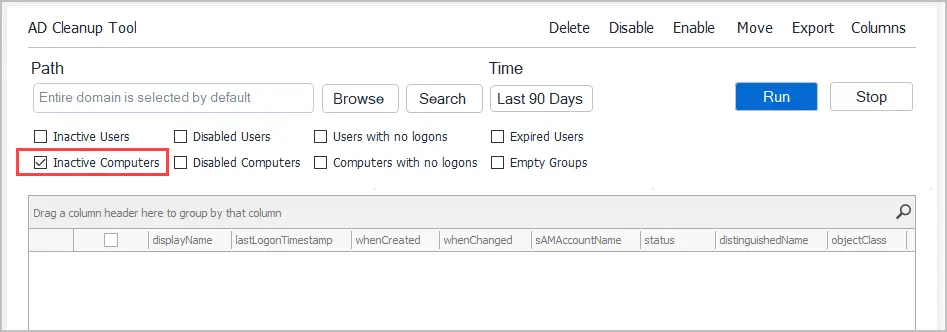
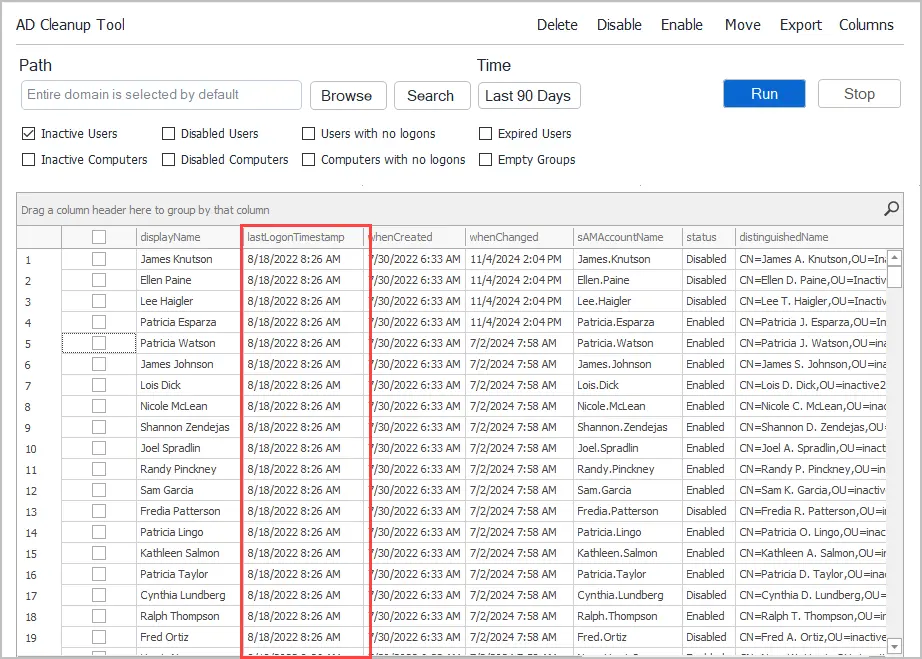
Step #2: Select Inactive Computers
Select “Inactive Computers” from the list of options. You can also include inactive users in the report.
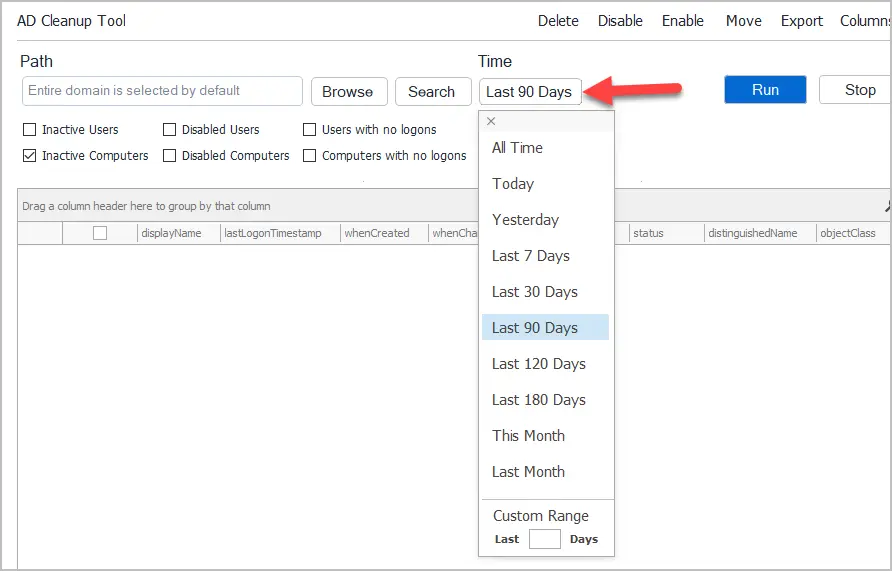
Step #3: Select Inactivity Time
By default, the tool will find computers with no logon activity in the last 90 days. Click the Time button to select a different time period.
Step #4: Click Run
Click the “Run” button to scan your Active Directory and get a list of inactive computers.
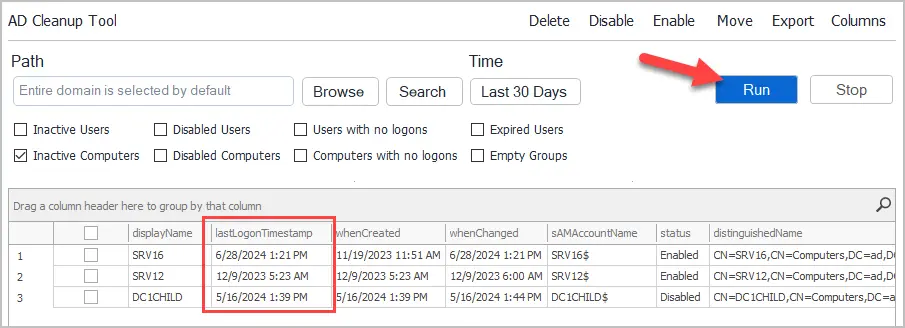
You can also list other inactive objects such as user accounts.
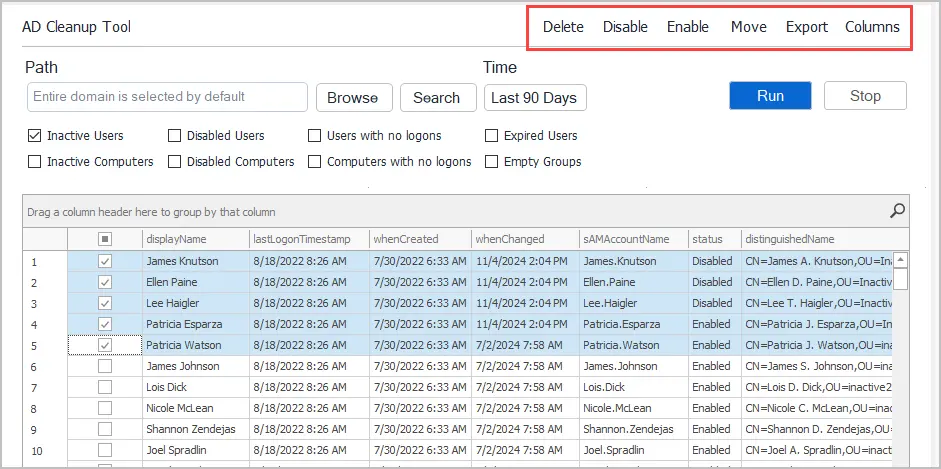
Step #5: Choose Actions
When you select a computer from the report the following actions are available:
- Delete: You can delete the computer object.
- Disable: Disabled the computer object.
- Enable: Enable the computer object.
- Move: Move the computer to another OU.
- Export: Export the list of computers to CSV, Excel or PDF.
Move Inactive Computers to another OU
To move computers, select one or more from the list and click the move button.
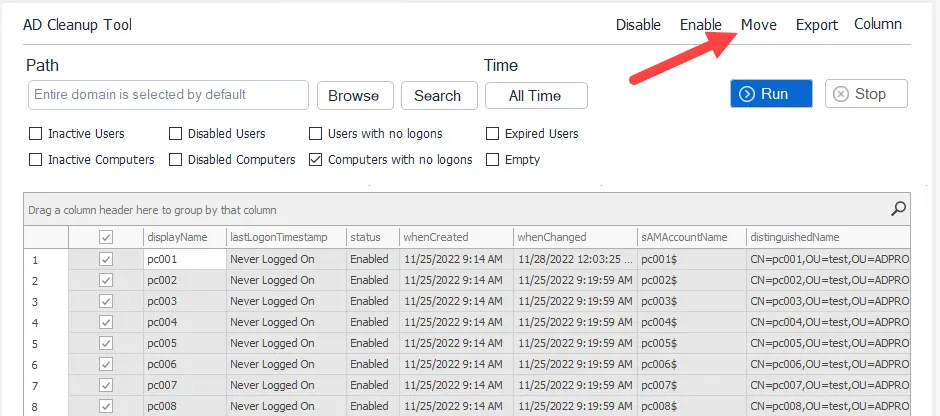
You will be prompted to select an OU. I recommend creating an OU called disabled or inactive.
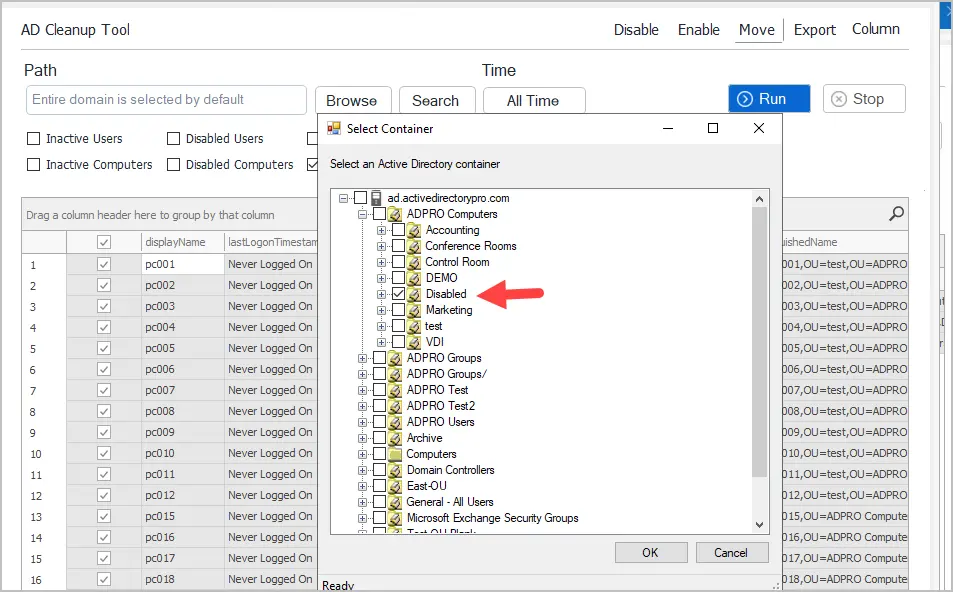
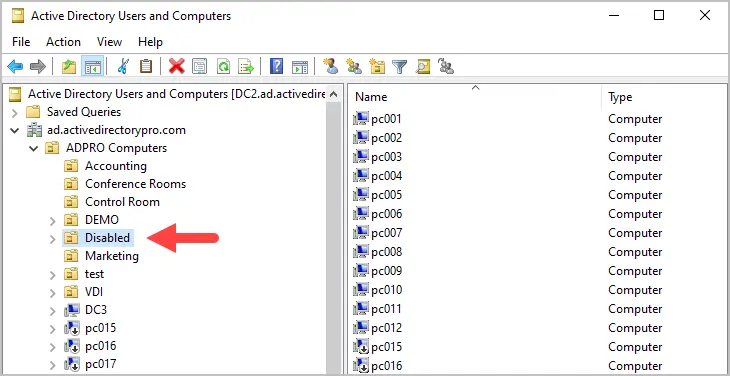
Now if I check the OU in Active Directory, I’ll see that the accounts have been moved.
Best Practices for Handling Inactive Computers in AD
Here are my recommendations for dealing with inactive and stale computer accounts.
- Define inactivity time: Set a clear policy for how long a computer can remain inactive before being acted upon. I recommend at least 90 days of inactivity before taking action.
- Disable first: Disable the computer account for x period of time (such as 90 days) before deleting them. There are many reasons why a computer account can report inactive so it’s a good idea to have a long grace period.
- Move Accounts: Move inactive and disabled computer accounts to a dedicated OU, such as one labeled “Disabled” or “Inactive”. This helps keep things organized and makes it easy for everyone to see all the inactive computer accounts.
- Share Inactive Report: Export the list of inactive computers and share it other staff members. It’s important to communicate with staff about objects in AD that have been disabled or deleted.
- Add Description: When you disable the computer object add a description with the date and your initials. This is very helpful for other admins in case someone asks why a computer was disabled.
- Enable AD Recycle Bin: Make sure you enable the AD Recycle Bin. This will come in useful if you delete an object that was still in use.
- Delete inactive computers after x days: After the computer account has been disabled for at least 90 days then it is probably safe to delete the account.
- Regular review: Run a cleanup process on Active Directory once a month. You can use tools such as the AD Cleanup Tool to automate the cleanup process.
Hopefully, you found this tutorial helpful. If you have questions or run into any problems, post a comment below.
Related Article: How to find inactive users in Active Directory

will you please tell me the way to allow non administrators (IT support team)
to join workstation to domain and perform some troubleshooting tasks, such as running network diagnostics task,installing softwares etc.
You can use the delegation control wizard to allow non administrators access to perform certain tasks.
Here is a video I made for delegating reset permissions to a security group for the helpdesk.
https://www.youtube.com/watch?v=VXDVwRGW-Qs
The last three powershell commands worked great.
You should add that they need to be run sequentially.
Inactive accounts and their access permissions can be used to access network resources. So it is necessary to manage and remove inactive Active Directory accounts using PowerShell and Solution:
https://www.lepide.com/how-to/manage-inactive-ad-accounts-with-lepideauditor.html
http://expert-advice.org/active-directory/powershell-to-find-inactive-ad-users-and-computers-accounts/
Peter,
You are absolutely right, if inactive accounts are not removed they can be used to gain access to resources. This is why I run a monthly task to check and remove inactive computer and user accounts.