In this guide, I share my Active Directory Cleanup Best Practices.
This is the same process I used for years working in medium and large Active Directory environments to keep AD nice and clean.
Let’s get started.
1. Disable Accounts for 90 Days Before Deleting Them
Don’t just start deleting users and computers from Active Directory. There are many reasons why a user or computer account may appear to be inactive but in fact, could still be a valid account. This is also true for groups and group policies. More details on this are below.
It is best to disable accounts for a period of time such as 90 days before deleting them. After 90 days and no one has screamed, then you can delete the account.
I’ve worked in environments with a lot of temporary staff and contract employees. Sometimes these users don’t logon for months or only work for a few months out of the year. I’ve deleted these types of accounts many times and had to recreate them.
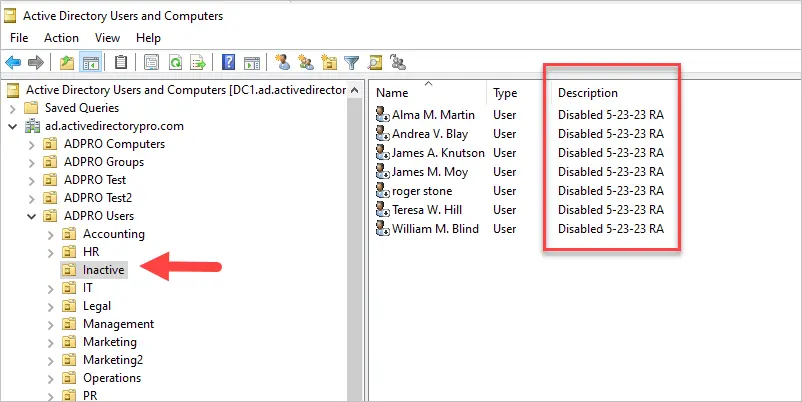
What I like to do is disable the accounts and move them to an OU called Inactive. This way anyone can easily see all of the accounts that have been disabled during the cleanup process.
How to Steps:
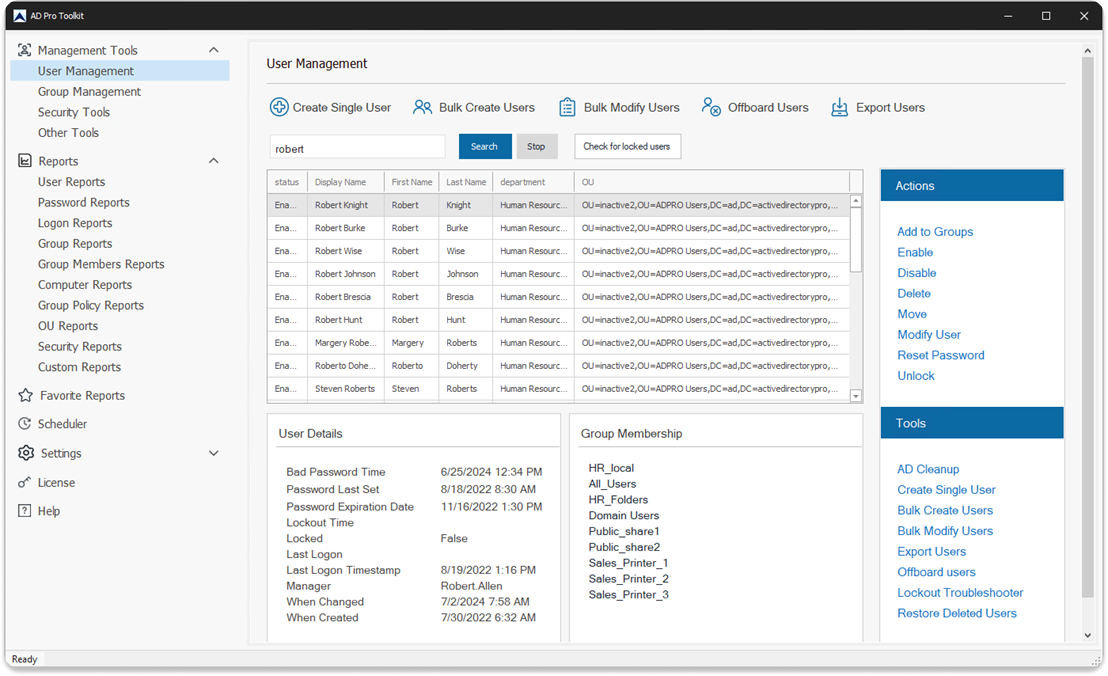
You can bulk disable and move accounts with the AD Cleanup Tool. If you don’t have this tool, you can click here to download a free trial.
Select the accounts to disable and click the “Disable” button. To move the account, select the Move button.
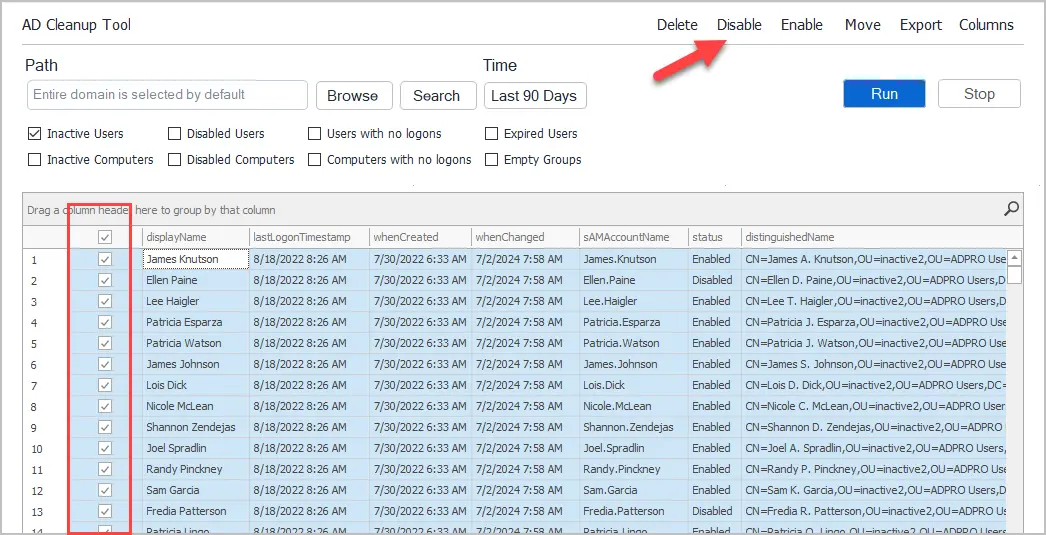
I also like to add the date and initials to the description field. This way if someone has a question as to why an account was disabled, they know who to ask.
2. Find Inactive Users in the Last 90 Days
Inactive users can be identified by the lastLogonTimestamp attribute. This attribute is replicated to all domain controllers, but it has a delay (not real time). This attribute was added by Microsoft for the purpose of finding inactive user and computer accounts. There can be many reasons why a user’s LastLogonTimestamp is not updated. This includes working at a remote site or at home, they are on vacation, maybe they are logged in with cached credentials or using VPN.
For those and many other reasons, I recommend searching for accounts where the LastLogonTimestamp has not been updated in at least 90 days. But be prepared, there will be exceptions to this. There will be an intern or a contract worker or a user on extended leave that are valid employees but don’t log in very often. You will need to keep a list of these users and exclude them from the cleanup process.
How to Steps:
Using the AD Cleanup Tool it defaults to finding inactive accounts with no activity in at least 90 days. You can easily change this to any time frame using the time button.
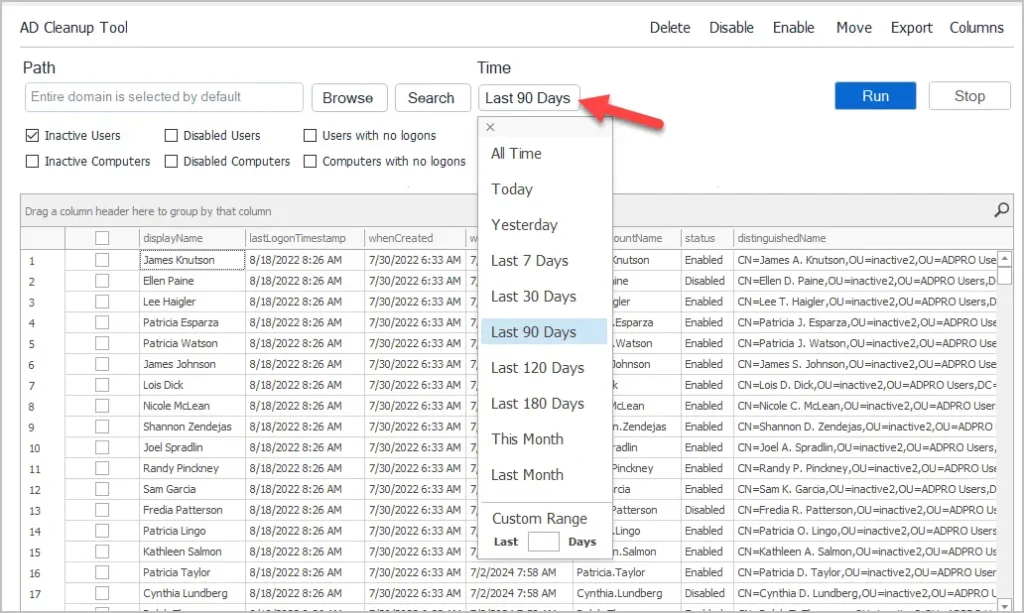
3. Find Inactive Computers in the Last 90 Days
Inactive computers can also be identified by the lastLogonTimestamp attribute.
I recommend searching for computer accounts where the LastLogonTimestamp has not been updated in at least 90 days.
Like users, there are many reasons why a computer may not update the lastLogonTimestamp but be an active computer.
When I worked for the local government, they had 4g connections in the police cars. These were domain joined computers, but they logged in locally to the computer. So, the computers would often not be connected to the domain and therefore the lastLogonTimstamp would go months without updating. We had to exclude these laptops from the cleanup process.
Working from home made this challenging as a lot of users never connected to the VPN. We required these users to either connect or come into the office to ensure their laptops would update.
How to Steps:
By default, the AD Cleanup Tool will display inactive users. If you only want to see inactive computers, select “Inactive Computers”.
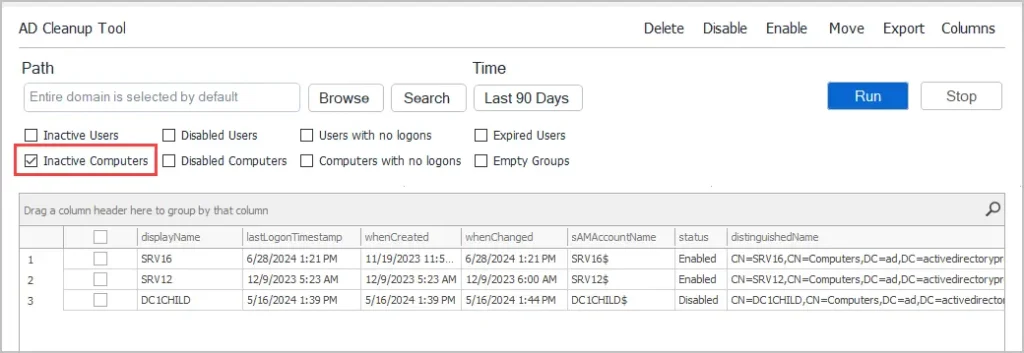
4. Find Accounts with No Logon History
You will be surprised by this one!
Accounts with No Logon History are accounts that have no date in the lastLogonStamp field. I was shocked the first time I ran this report, why would there be so many accounts that have never been used? The most common reason is new employees that never showed up or quit on their first day.
When searching these accounts, you want to also look at the whenCreated attribute. If the lastLogonTimestamp is blank and the whenCreated is within a few days, you may not want to disable the account. I recommend using the 90 days rule for the whenCreated attribute on this report.
How to Steps:
In the AD cleanup tool, click filters and select Users Without Logon History. Make sure the options box is unchecked. Accounts that have no logon history will display Never Loggon On in the lastlogonTimeStamp column.
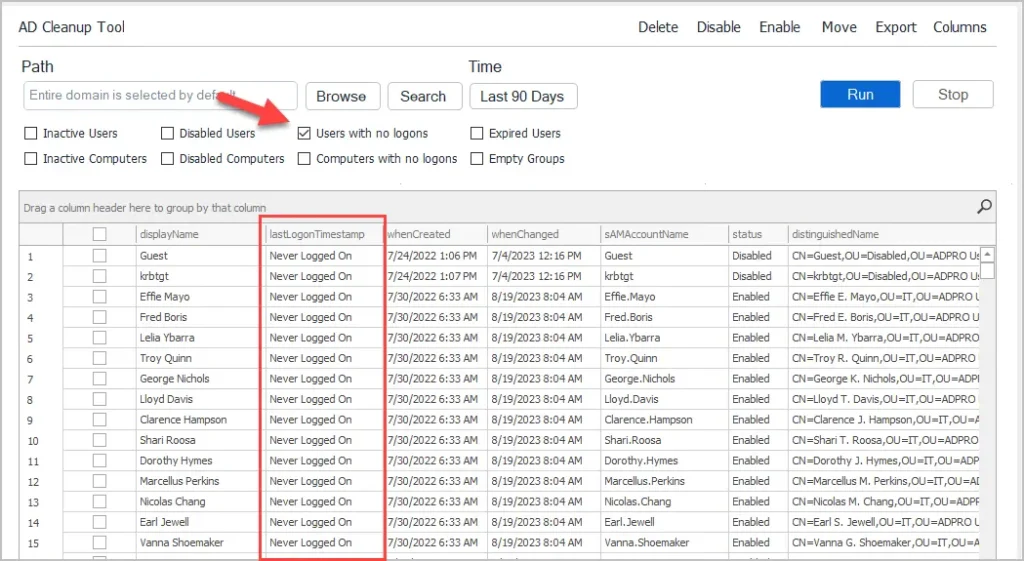
In the screenshot above you can see I have several accounts with no logon history. I then check the whenCreated column and see these accounts were created over 90 days ago so they are safe to disable.
5. Find Expired User accounts
Expired accounts are accounts that have been set to expire on the user accounts page. These accounts cannot be used unless the expiration date is changed or set to never. Expired accounts are often looked over or forgotten about.
These are often contract workers, temporary employees (summer programs), auditors, and so on. When I know an account is temporary, I would often set an expiration date for them, this way they get automatically disabled.
How to Steps:
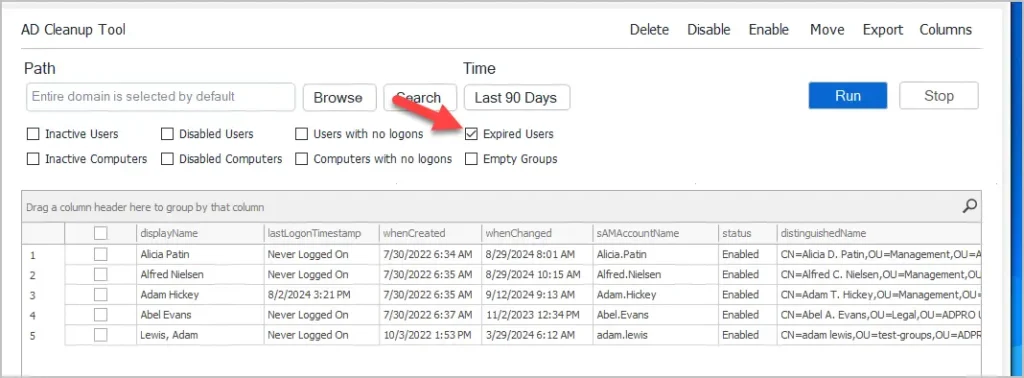
To find all expired users click filters and select Expired Users.
Since the accounts are expired and cannot be used, I would go ahead and disable them. I don’t see a need to wait 90 days before disabling these accounts.
6. Accounts with Weak or No Passwords
You want to search for accounts that have the following set:
- Users that don’t require a password – I have no idea why this is even an option but accounts can be configured to accept a blank password. This is a really bad security practice and needs to be disabled.
- Users with a password set to never expire – User account passwords should be changed frequently. You need to find the accounts that are configured to never change their passwords and fix them.
- Admins with old Passwords – Privileged accounts such as domain admins should be reviewed to make sure they are changing their passwords frequently.
How to Steps:
Using the AD Pro Toolkit click on Reports -> Password Reports. Scroll to the Password Status section and select one of the reports to run.
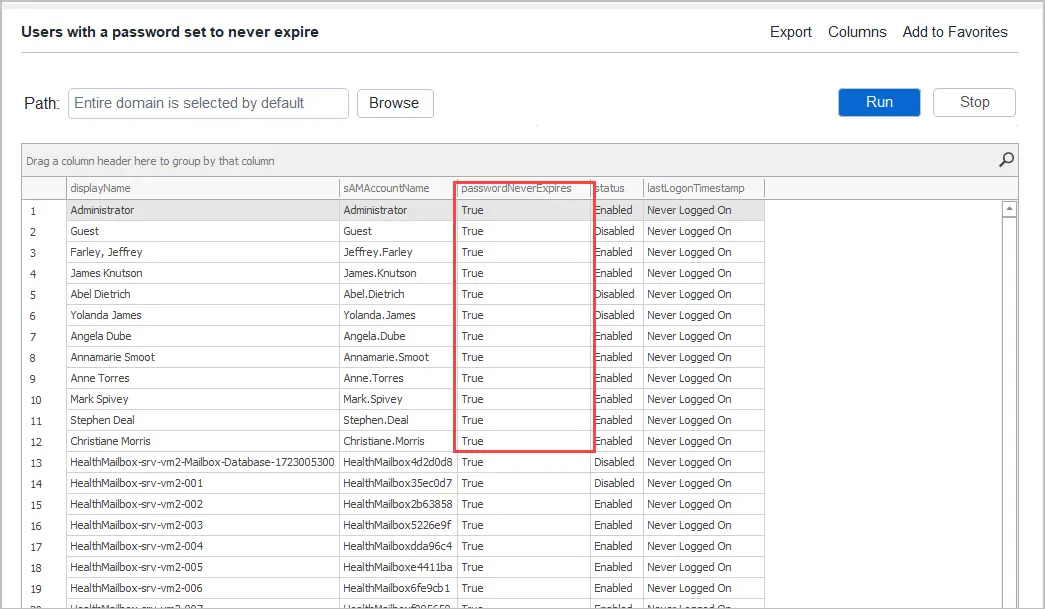
The Admins with old Passwords report is located under Reports -> Security
7. Find Empty Active Directory Groups
How many times have you created a group and never used it? Or created a group for testing reasons but never removed it when the testing was completed. This happens a lot. When you have multiple admins working in Active Directory you can end up with a lot of unused and empty groups.
You should review the empty groups in your domain and remove them if they are not needed.
Warning: There are many built-in groups that have no members by default, do not delete the default groups.
How to Steps:
Using the AD Pro Toolkit click on “Group Members Reports” and then “Groups with no members”.
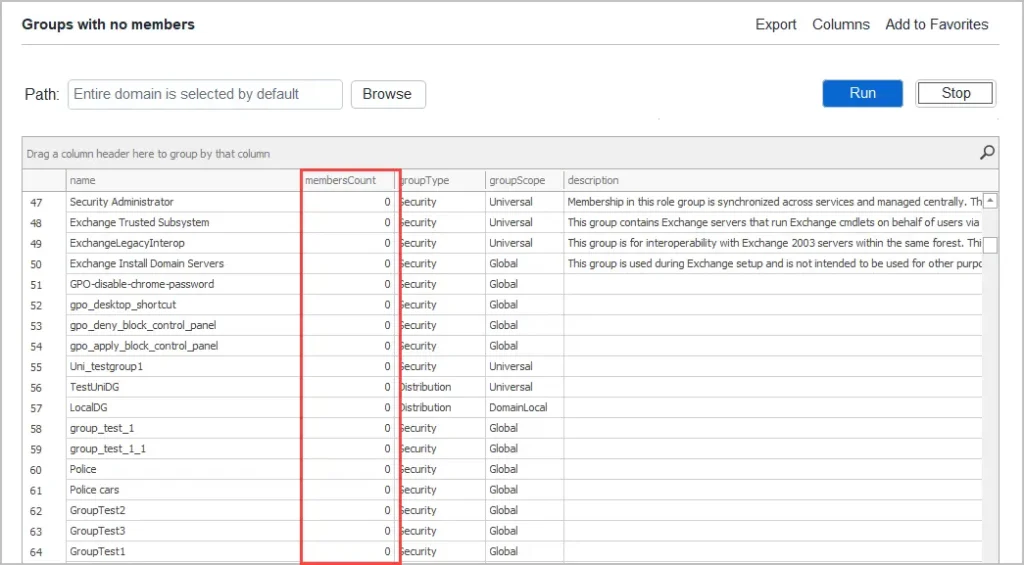
You can see above I have several empty groups.
What I like to do is export this list and email it to my team to review. Maybe another administrator is using one of these and it’s a good idea to check before deleting them.
I often get asked how to find inactive groups. There is no easy solution for this that I know of. You will have to scan your network (folders, applications, systems) and check if a group is being used. If you know of a solution for this post a comment below.
8. Inventory Groups and Organizational Units
Cleaning up groups and organizational units is not easy. This is especially true in large organizations that have thousands of users and domain objects.
Before going down the rabbit hole of removing groups and OUs I recommend running some reports on what objects you have. You can export these reports and then review them with other team members.
One report I find useful is to list all OUs and the object count. I often find many OUs that have 0 objects in them. These might be some OUs you can delete.
How to Steps:
Click on Reports -> OUs and run the All OUs and object count.
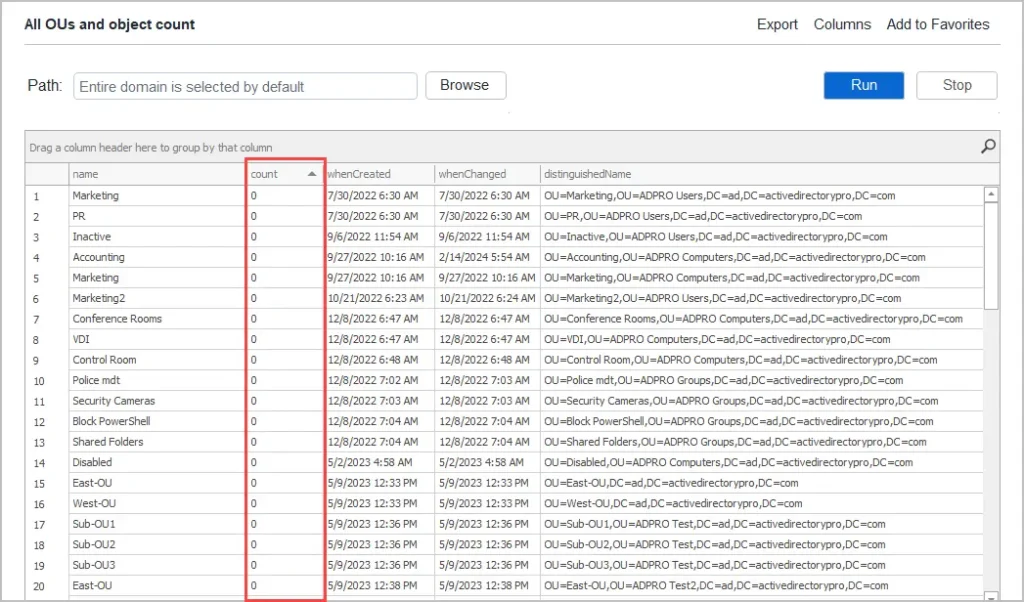
You can see above I have several OUs that have no objects in them. I created these for testing and they are currently not in use.
9. Automate Active Directory Cleanup
I recommend running an Active Directory Cleanup every 30 days. You could manually run through all the cleanup steps but it would be much more efficient to automate it, plus it will save you a lot of time.
Currently, the toolkit includes several reports that can be automated and emailed to you on a schedule. An alternative is to create a PowerShell script and use the task scheduler to run it on a schedule.
10. Communicate Active Directory Account Changes
True Story.
Years ago when I first started deleting old user and computer accounts I did not communicate it with anyone. Not long after disabling accounts the helpdesk would call and say “this user can’t login”, I reset their password but the user still can’t login. Oh! Yea, I disabled that account, I didn’t think it was being used. The helpdesk wasted a lot of time troubleshooting this because I disabled the account.
Same issue with computer accounts. Helpdesk would call and say the user can’t login. I’ve spent hours troubleshooting the computer but no luck. Hmm… oh yea I disabled their computer.
When you disable AD accounts, I recommend you export the list to Excel and email it to all your system admins, IT tech, and helpdesk. This way they are aware of the accounts you have disabled and don’t spend hours troubleshooting them.
How to Steps:
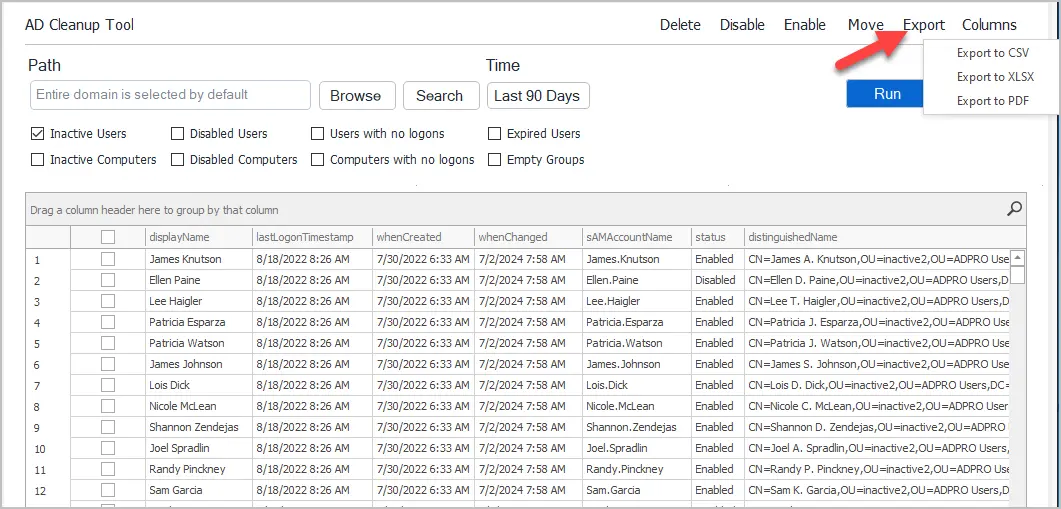
With the AD Pro Toolkit, you can easily export any report by clicking on the export button.
Bonus: Cleanup Unused GPOs
You probably have several group policy objects that are not being used, or GPOs that are blank.
With the AD Pro Toolkit, you can easily find all unused GPOs. Click on Group Policy Reports > Unlinked GPOs. It will list any GPO that is not linked to the domain or an OU.
There you have it, that is my list of Active Directory cleanup best practices. I hope you found this article useful, post any comments or questions below.