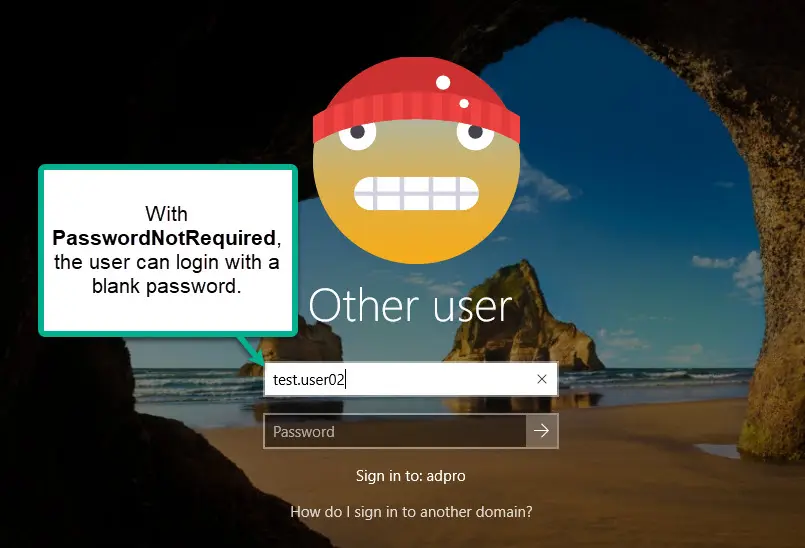
In this post, you will learn how to find Active Directory user accounts with PasswordNotRequired set to true. When a user is configured with Password-Not-Required this means they can have a blank password. I’ll also show you how this attribute is set and how to remove it.
What is the PasswordNotRequired Attribute
In Active Directory there is no attribute called PasswordNotRequired, instead this is a value stored in the userAccountControl attribute. When a user account is configured with a PasswordNotRequired this means the user account can have a blank password. This does not initially set the password to blank but it allows the user to set a blank password when they change or reset it.
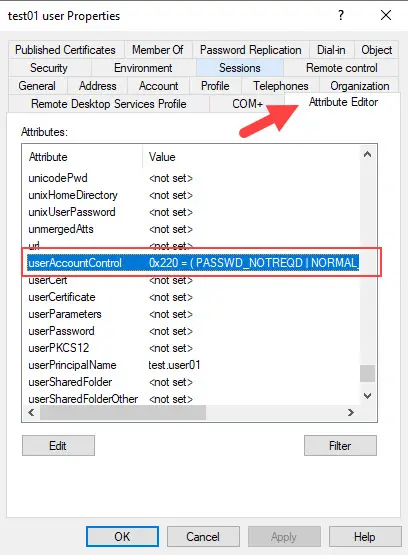
The below screenshot shows the user test01 is configured with a Password Not Required.
How are users configured with Password not required (Blank Password)?
There are multiple ways a user can be configured to allow for a blank password.
- PowerShell
- ADUC
- Accounts created incorrectly
Option 1. PowerShell
Below is an example PowerShell command to set the PasswordNotRequired flag to true. When you run this command, it updates the value of UserAccountControl (again there is no actual attribute called PasswordNotRequired).
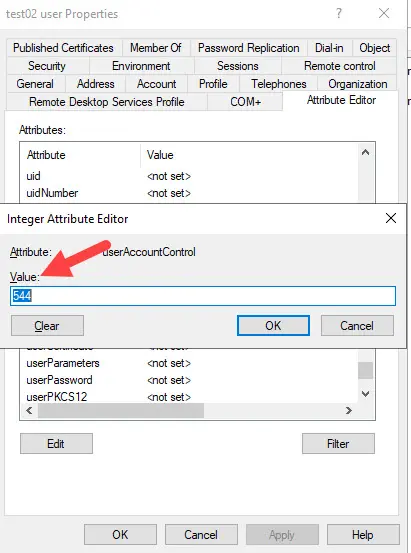
set-aduser -Identity test.user02 -PasswordNotRequired $trueOption 2. ADUC
In Active Directory Users and Computers, you can edit a user account and set the userAccountControl value to 544. This is not something an administrator would typically do and changing this attribute can be a risk.
Option 3. Accounts created incorrectly
AD User accounts can be created with an incorrect flag, this means when the account is created the password not required flag might be set (and other options). If you use a 3rd party tool or script to create accounts, make sure you check the userAccountControl value.
What are the security risks if a user is configured with a blank password?
When a user is configured with no password (blank password) it poses several security risks.
- Unauthorized Access: With no password, anyone that knows the account name could login and access company data.
- Compromised accounts: Attackers can easily exploit accounts with blank passwords to access sensitive data, launch phishing attacks and spread viruses.
- Compliance violations: Many compliance standards require users to have a password. Using blank passwords can lead to violations and legal repercussions.
- Data Breaches: Blank passwords make it easy for unauthorized individuals to access company data which can result in a data breach.
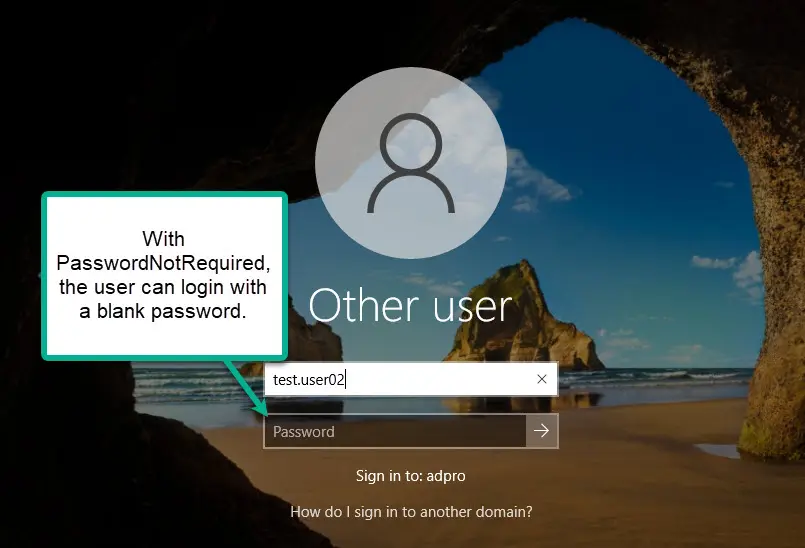
Without password authentication, all you need is the account name to log in to a Windows computer.
I have a domain password policy set with Group Policy, can users still set a blank password?
Yes.
For example, my domain password policy is configured to require a minimum password length of 8 characters.
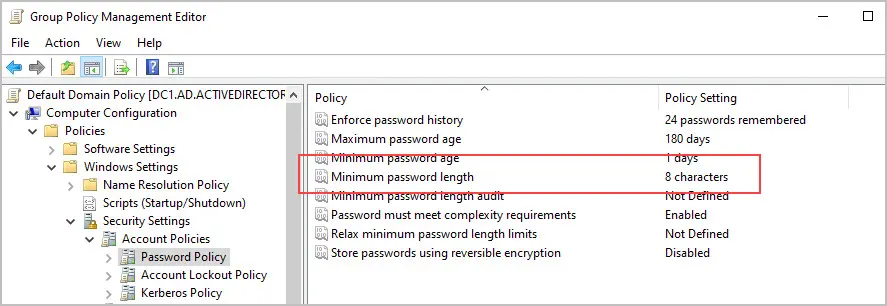
Even with the above policy in place, users can be configured with a blank password, login to computers and access company data. When an account is configured with PasswordNotRequired it basically bypasses the domain password policy. This is a big security concern and why it’s important to report and audit user account password settings.
How to Find Active Directory users with PasswordNotRequired (Blank Password allowed)
It’s very important to regularly run an audit on your Active Directory user accounts to check for insecure settings. This can be done with PowerShell and 3rd party tools.
With PowerShell you can easily find all users that do not require a password with the command below.
Get-ADUser -Filter {PasswordNotRequired -eq $true} -properties PasswordNotRequired | select name, PasswordNotRequired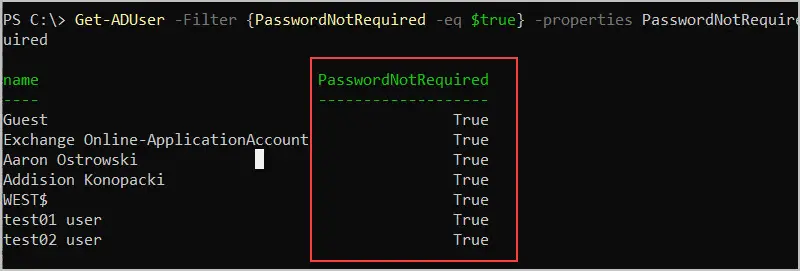
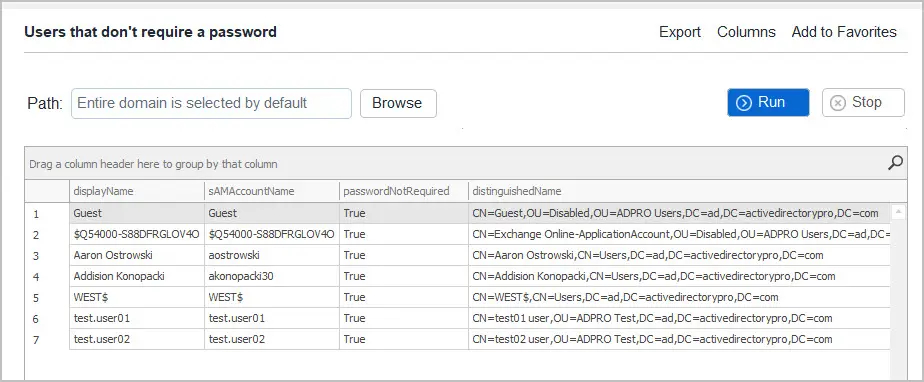
With the AD Pro Toolkit there are multiple password and security reports to help you audit your users. These reports can be set to run on an automated schedule.
Password Reports > Users that don’t require a password.
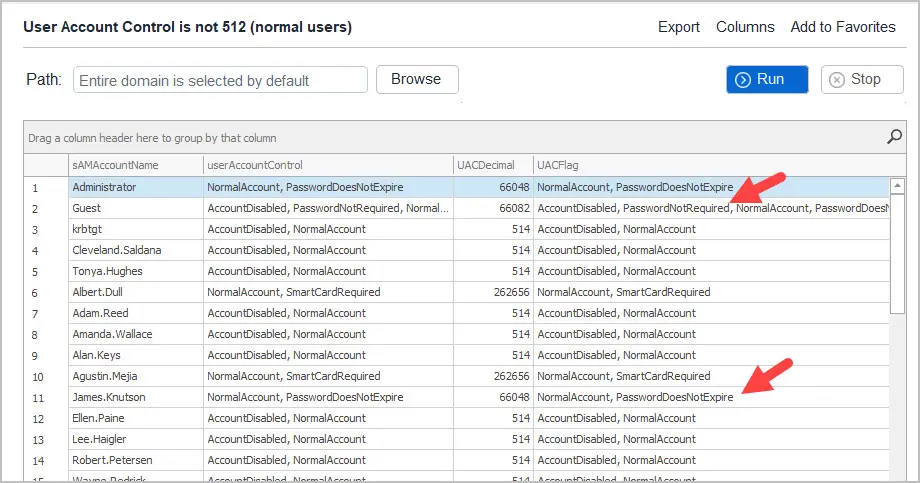
User Reports > User Account Control is not 512
This report will show you all the accounts that are not normal, meaning they have a special flag set.
The AD Pro Toolkit includes over 200 built in reports for users, computers, groups, security and more.
How to Remove PasswordNotRequired for AD Users
There are multiple ways to remove the PasswordNotRequired if configured on an account.
Option 1. PowerShell
With PowerShell you can use the below command, this changes the PasswordNotRequire value to false.
Set-ADUser -itentity test.user1 -PasswordNotRequired $falseOption 2. ADUC
In Active Directory you can change the user userAccountControl value to 512. This will set the account back to normal.
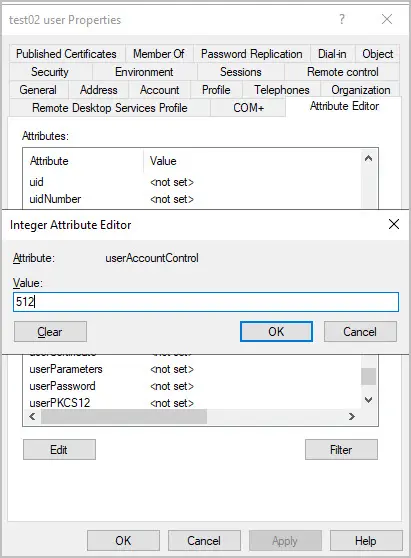
Option 3. Remove PasswordNotRequired for multiple accounts
If you have multiple accounts that need the PasswordNotRequire removed, then you can use the AD Pro Toolkit. This tool lets you easily bulk modify user accounts.
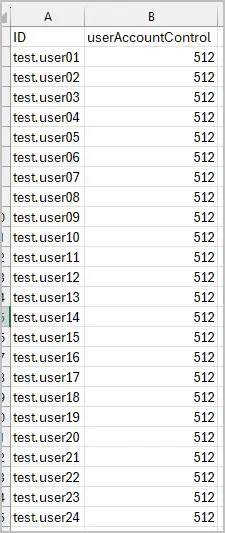
Step 1. Created a csv with an ID column and useraccountcontrol column.
Enter the users in the ID column and set the userAccountControl value to 512.
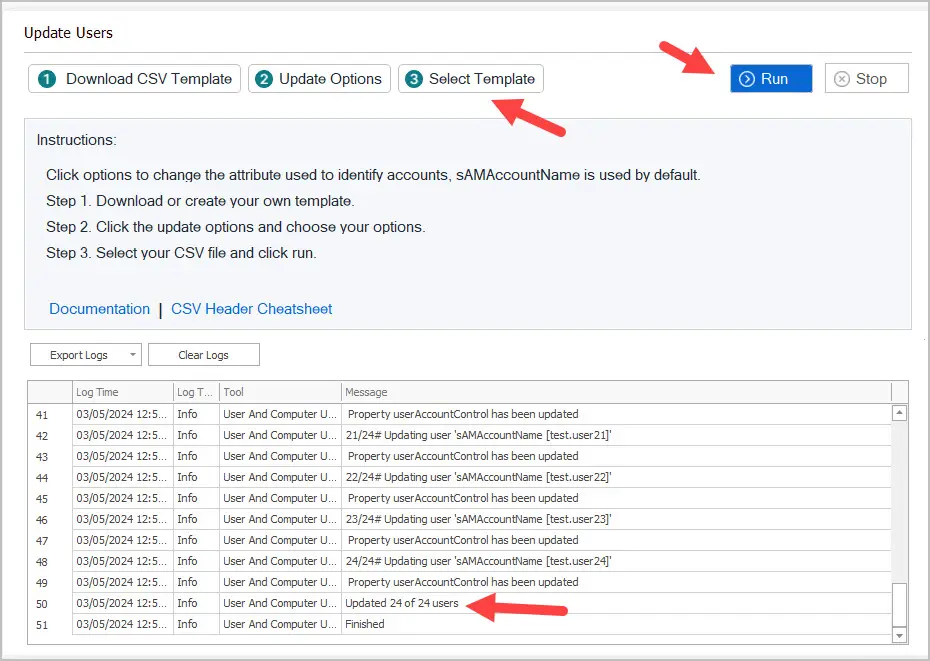
Step 2. Run the bulk update users tool
Click the select template button and select your csv file.
Click Run to start the update process.
Automate Finding Insecure and Risky User Accounts
Manually checking accounts in Active Directory for insecure settings can be time consuming and error prone. In addition, PowerShell can be complex and requires constant changes to run specific reports.
AD Pro Toolkit provides over 200 built in reports that can be run with a click of the button. Here are some reports that can help you find security issues.
- Users that don’t require a password
- Users with a password set to never expire
- Users who have never changed their password
- Users with expired password
- Bad password attempts
- Users with account that does not expire
- Users with an expired account
- Inactive accounts in x days
- Users that have not logged on in last x days
- Users not protected from accidental deletion
- Admins with old passwords
Summary
User accounts configured with a blank password are a huge security risk. It is highly recommended to scan your domain accounts and find any account that is configured with the PasswordNotRequire flag. In addition, you should run a scan for insecure accounts on a regular basis, I recommend at least once a month. In some environments you maybe require running an audit more frequently or even in real time.
In this guide, I showed you what the PasswordNotRequired attribute is, how blank passwords are configured and how to scan your domain for accounts that have password not require set to true.
You might also like: