In this post, I’ll show you two options on how to get the last logon timestamp for Active Directory user accounts. The Active Directory last logon date is often needed for security audits and to track when a user last logged on to their computer or network.
In this article:
- LastLogon vs LastLogonTimeStamp vs LastLogonDate
- Option 1. Get AD Last Logon using the AD Pro Toolkit
- Option 2. Get AD Last Logon using PowerShell
LastLogon vs LastLogonTimeStamp vs LastLogonDate
It’s important to understand the difference between the logon attributes as they are used for different reasons. When using PowerShell you will see three different lastlogon properties.
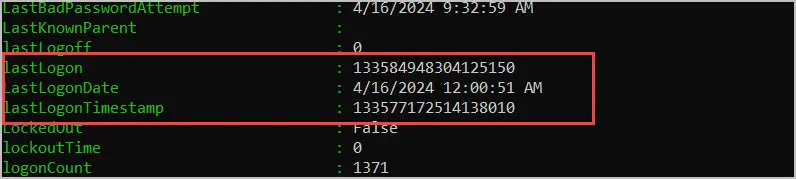
LastLogon
When a user authenticates to the network this attribute is updated on the domain controller that performs the authentication and is not replicated.
When to use? You should use the LastLogon attribute to get an accurate report of a users last logon. The problem is you will need to get the LastLogon attribute from each domain controller to show the real Last Logon date. This is automatically done with the AD Pro Toolkit, examples below.
LastLogonTimeStamp
The LastLogonTimeStamp attribute also records the timestamp of when a user logs onto their computer or network. This attribute is replicated to all domain controllers but it has a delay (9-14 days behind the current date).
When to use? The LastLogonTimeStmap should be used to find stale accounts in Active Directory. Due to the delayed timestamp value, this attribute is not intended for creating last logon reports.
LastLogonDate
LastLogonDate is not an attribute its the calculated value of LastLogonTimeStamp when using PowerShell.
When to use? Use LastLogonDate when using PowerShell and you want an easy to read format of the LastLogonTimeStamp.
Option 1. Get AD Last Logon using the AD Pro Toolkit
Follow the steps below to create a last logon report using the AD Pro Toolkit. You can download a trial of this tool and try the report for free.
- Click on “Logon Reports” then click “True Last Logon Report”.
- Click “Run” to get the last logon date for all users or click “Browse” to select an OU or group.
- Optionally, you can click the “Time” button to change the time range.
- Click “Run” to start the report.
Note: If you have a lot of users and multiple domain controllers this report can take several minutes to complete.
Below is an example Last Logon Report from the toolkit. You can click “Export” and save to CSV, Excel, or PDF file.
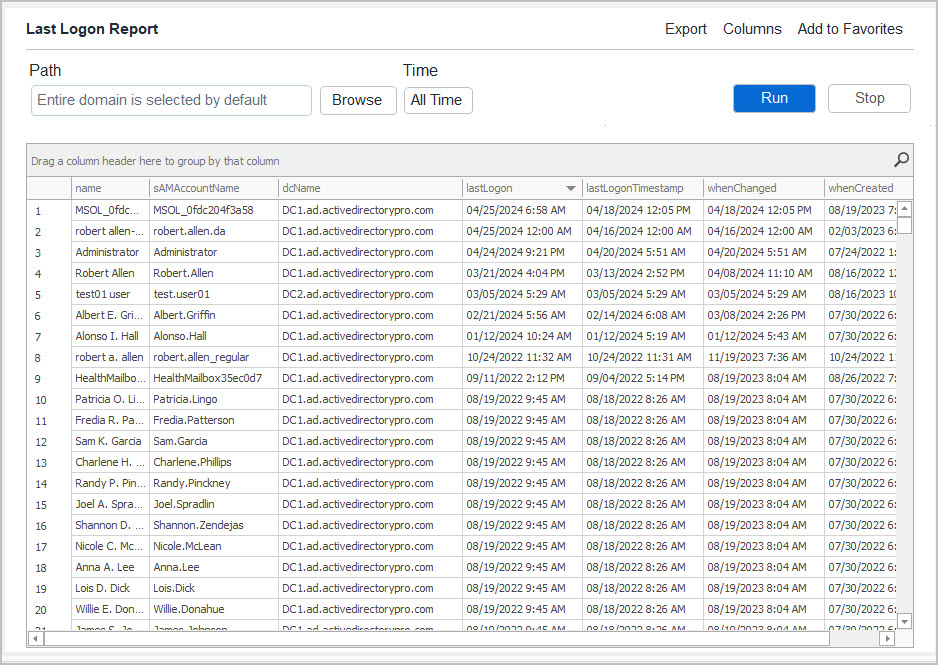
You can see in the screenshot above the tool returns the users name, account name, domain controller name, and the last logon date. You can click on any column to sort the results in ascending or descending order.
The AD last logon Reporter eliminates all the manual work of checking the lastlogon attribute for all users across all domain controllers. It would be very time consuming and difficult to return the real last logon time without this tool.
Our Active Directory Reporting Tool includes over 200 built-in reports.
Option 2. Get AD Last Logon using PowerShell
Tip: Keep in mind to get the TRUE last logon date with PowerShell you would need to run the script on all domain controllers as the value is not replicated. The AD Pro Toolkit automatically gets the real last logon date and time from all domain controllers.
Step 1: Log into a Domain Controller
If you don’t run this from a DC, you may need to import the Active Directory PowerShell modules.
Step 2: Use Get-ADUser PowerShell cmdlet
Open PowerShell and use the command below to get all domain users LastLogonDate.
Get-ADUser -filter * -Properties "LastLogonDate" | select name, LastLogonDateYou should get similar results to the screenshot below.
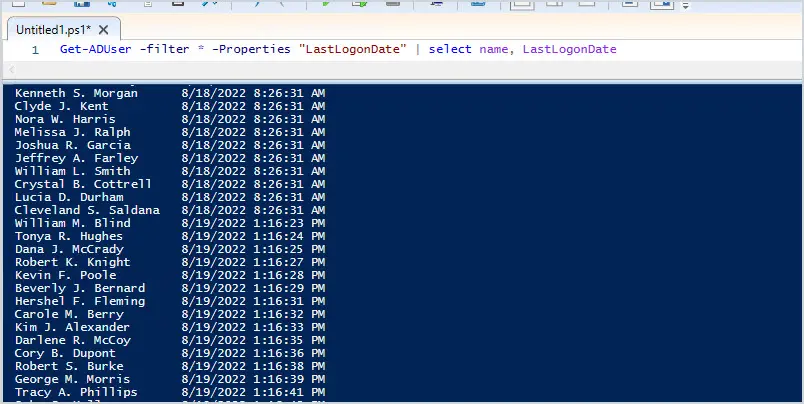
The above example gets the last logon date for all users, for a single user run the command below.
Get-ADUser -identity robert.allen -Properties "LastLogonDate" | select name, LastLogonDateIf you add the lastlogon date you may notice some users are blank. This is because lastlogon is not replicated and the user may have never authenticated against the DC.
Get-ADUser -filter * -Properties LastLogonDate,lastlogon | select name, lastlogon,LastLogonDate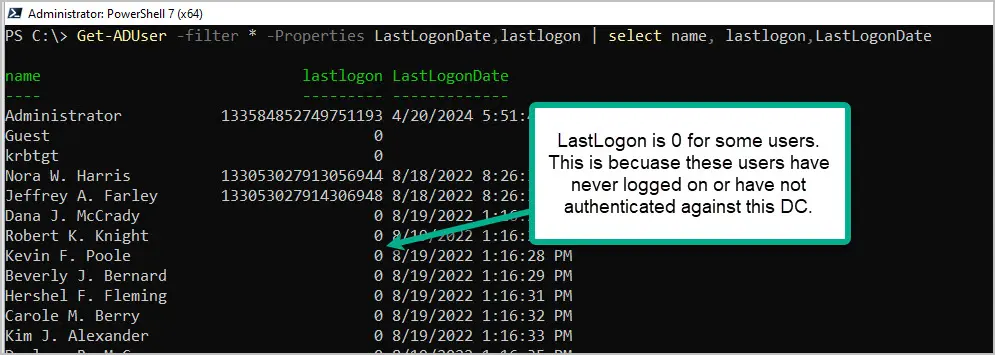
Video Demo of Last Logon Date
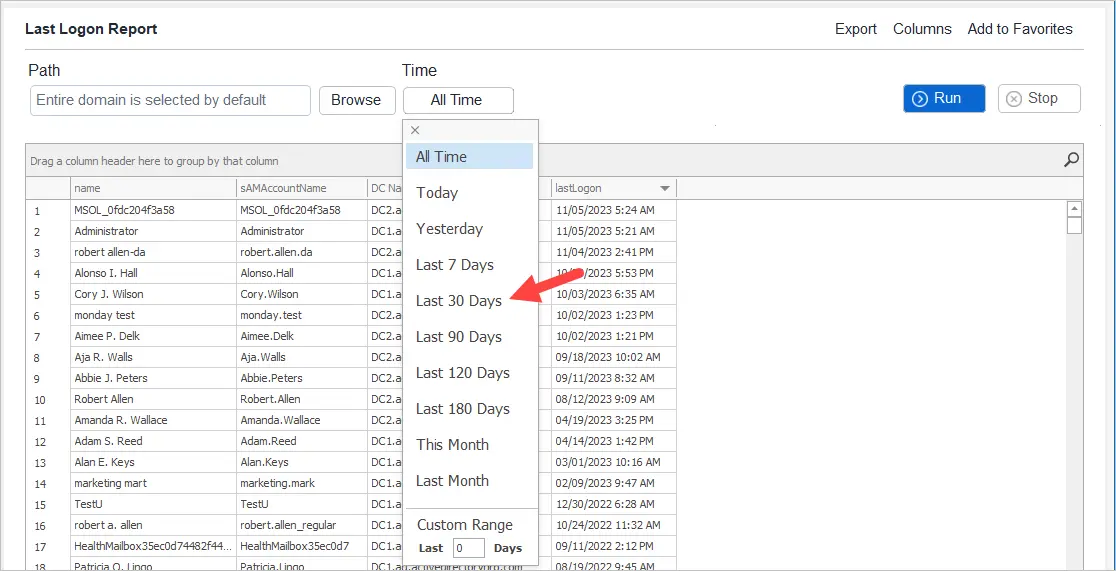
Get Last Logon 30 days
To get users that have logged on in the last 30 days click the time button and select “Last 30 Days”
Summary
In this guide, I walked through three methods on how to get the Active Directory Last Logon for domain user accounts.
It is important to review the last logon date for user accounts on a monthly basis to find stale user accounts. This can also be used to check the last time a user authenticated to the network. The PowerShell get-aduser cmdlet works great to get user’s last logon details from a single domain controller. To automatically collect the last logon details from all Domain Controllers I recommend the AD Pro Toolkit.
If you have questions or comments please leave a comment below.
Related AD Reports
Resources:

Hi everybody, I am not an IT but an auditor. I am ckecking the last log in of an user (a former employee of my organisation) to our AD. I have used Method#1 that is explained in thia topic and the check shows that the user has logged in to the AD on 06.Nov.2022 but in fact she has left the organisation in August. Can I assume that the user account is compromised or the date of the last log in may show that a process or a system has been used the account for something? I am not sure I am explaining the situation well, but I will be grateful if you help me understand the meaning of this date!
Hi,
Is there a way to find the last login date\time and what was the hostname used logged on to?
Hi, Robert.
The script worked, thanks.
Now I can search by computer and I will get the user.
Is possible to search by user and get the computer name?
Get-UserLogon -All – this command took more then 30 minutes
I would like to insert the name of the user and see the last computer logged.
will be possible?
Hi, Robert.
I need a simple help like the Eugene.
Sometimes I need to identify by username the last computer used or still using.
I tried a lot of scripts but I cannot find a simple one for that.
Thanks for the help.
This would require checking the logs on the local computer as this info is not stored in Active Directory.
You can do this with PowerShell, here is an example, https://theposhwolf.com/howtos/Get-LoginEvents/
I get this request a lot so I might include this in a future release of my GUI toolkit.
Hi, Robert.
Thanks for the help.
Robert, I found this;
https://sid-500.com/2018/02/28/powershell-get-all-logged-on-users-per-computer-ou-domain-get-userlogon/
But I cannot run the command GET-USERLOGON.
The point of this is to identify the computers used by username.
If I need to check locally will not help because I don’t know the computer name.
This script is also running locally. It is running the command “Invoke-Command -ComputerName $u.Name -ScriptBlock {quser}” against each computer to see who is currently logged on. It will only report if someone is currently logged on.
Copy the script into PowerShell ISE click the run button then you will be able to use the Get-UserLogon command.
Hi, Robert.
Sorry to bother you.
Robert I tried but at ISE I got this;
PS C:\Users\Administrator.GPRO> Invoke-Command -ComputerName $u.Name -ScriptBlock {quser}
Invoke-Command : Cannot validate argument on parameter ‘ComputerName’. The argument is null or empty. Supply an argument that is not null or empty and then try the
command again.
At line:1 char:30
+ Invoke-Command -ComputerName $u.Name -ScriptBlock {quser}
+ ~~~~~~~
+ CategoryInfo : InvalidData: (:) [Invoke-Command], ParameterBindingValidationException
+ FullyQualifiedErrorId : ParameterArgumentValidationError,Microsoft.PowerShell.Commands.InvokeCommandCommand
Thanks for the help.
Did you copy the entire script lines 1 to 155 into ISE?
I tested it and didn’t get any errors.
Is there a way to display the last logon date per user PER COMPUTER? for example, i login to multiple computers and want to know when the last time i logged in to a specific one.
Thank you.
I have to know LastLogon I have the exported excel file in LastLogon Field it is Showing
132635534097464000
how can i know the time
This should do it.
Get-ADUser -Identity “username” -Properties “LastLogon” | Select Name, @{N=’LastLogon’; E={[DateTime]::FromFileTime($_.LastLogon)}}
How do you get the computer name they last logged into as well?
Just wanted to say Thank you, this is very useful information…
Am I able to use the “-match” command for the “username” in -Identity to find a list of users with RegEx?
Hi,
This is a simple powershell script which I created to fetch the last login details of all users from AD.
STEPS:
———
1) Login to AD with admin credentials
2) Open the Powershell in AD with Administrator elevation mode
3) Run this below mentioned powershell commands to get the last login details of all the users from AD
Get-ADUser -Filter * -Properties * | Select-Object -Property Name,LastLogonDate | Export-csv c:/lastlogon.csv
This will create a CSV file in your C Drive with the name lastlogon.csv which will contain the information of last login time of all the users
If you want to store the CSV file in different location, just change the path accordingly
Regards,
Shahul
Shahul, thanks for sharing.
Hi,
this step is very help me thank you….
Step 3: Run the following command
Get-ADUser -Identity “username” -Properties “LastLogonDate”
Replace “username” with the user you want to report on.
Hi Robert, the LastLogon attribute logs successful and unsuccessful logins?
2. What is special about the Active Directory built-in account in relation to schema admin, enterprise admin and domain admin?
LastLogon is only updated on successful logons on the DC that performed the authentication.
2. Not sure I understand the question. This link provides good details on what permissions the built-in administration, schema admin, EA and DA have https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/appendix-b–privileged-accounts-and-groups-in-active-directory
May i know how can i get the Security folders last login date, please suggest me.
You would need to turn on auditing for files and folders for those events to be logged in the event viewer.
Check out this article for more info https://docs.microsoft.com/en-us/windows/security/threat-protection/auditing/apply-a-basic-audit-policy-on-a-file-or-folder
Really helpful n correct information… Thanks
This advice seems very old fashioned and amateur (not “pro”), and I have no idea how this page is so high in Google rank.
“LastLogon” queried in this way is only accurate for a domain where there is one domain controller. The LastLogon time attribute is not replicated between domain controllers, and it only applies to the DC where you’re reading the value from. If you query the user information on another DC, it can be completely different (and generally *is* different).
You can use LastLogonTimestamp (which is replicated to all DCs) to find a last logon time that’s accurate to within 14 days (I don’t know why it’s this interval). That is, for a date that’s more than 14 days ago, that was the last time the user logged on at any DC in the domain. This is useful if you want to know accounts that last logged on a long time ago, such as more than 3 months ago or whatever.
If you need to know the last time an account logged on within 14 days, you need to query the LastLogon attribute for the user on *every DC* in the domain and get the most recent time from those results. There are plenty of scripts available on the internet that will help you do this.
TrixM,
Thanks for the detailed explanation. You are correct, I failed to mention in my article that the LastLogon attribute does not get replicated between DC. I’ll update the post. The LastLogonTimestamp can be updated even if a user has not logged on. That is why it’s better to use the LastLogon attribute to accurately report a user’s last logon time.
So glad I read the comments to find this little gem tidbit. LastLogonTimestamp saved the day for me.
To get this info for all users:
Get-ADUser -Filter * -Properties Name,LastLogon,Displayname, EmailAddress, Title | select Name,
@{Name=’LastLogon’;Expression={[DateTime]::FromFileTime($_.LastLogon)}},DisplayName, EmailAddress, Title | Export-CSV “C
:\temp\Email_Addresses.csv”
Last log on report comes like this “133135731765050000” Not sure how we can convert this to display properly, tried few methods in excel under number formatting but no luck, any help would be much appreciated.
Hi,
This is perfect article but i would like to pull last logon for all users how to go about
Thanks
Hi Abdallah,
Good question.
The free version of AD Tidy will easily pull the last logon for all users.
http://www.cjwdev.com/Software/ADTidy/Info.html
You can also use a powershell script.
Hi Abdallah,
You can easily do this with AD FastReporter Free – https://albusbit.com/ADFastReporter.php
Klaawz,
Thanks for the suggestion.
I saw your blog post on how to create a last logon report with AD FastReporter. Is there a way to save the report for quick access or do you have to manually create it each time?
In the Free version, you can export a report to a CSV, XLSX, or HTML file.
In the Pro version, all reports are stored in a local database and are available at any time for viewing or exporting.
Thanks Klaawz
Get-ADUser -Filter * -Properties * | Select-Object Name, msDS-FailedInteractiveLogonCountAtLastSuccessfulLogon | Sort-Object -Descending msDS-FailedInteractiveLogonCountAtLastSuccessfulLogon
Taken from – https://4sysops.com/archives/use-powershell-to-get-last-logon-information/
Wrong PS for what they are asking.
Man… I sure do get tired of people who want you to write the code for them. >.< Learn powershell guys.