In this post, we will look at the Microsoft account lockout tool and the lockout and management tool from the AD Pro Toolkit.
Both tools can be used to quickly get the lockout status of Active Directory user accounts. In addition, these tools are used to unlock accounts, reset passwords, and filter the logs for the lockout event ID.
Table of Contents
What is a Lockout Status Tool?
An AD lockout tool is used to check if an Active Directory user account is locked out or not. These tools are faster and easier to use than the provided built-in Microsoft Tools. These tools also include additional features such as password reset, unlocking accounts, and troubleshooting.
For example, the screenshot below is from the AD Pro Toolkit, with a single click it quickly displays all locked user accounts.
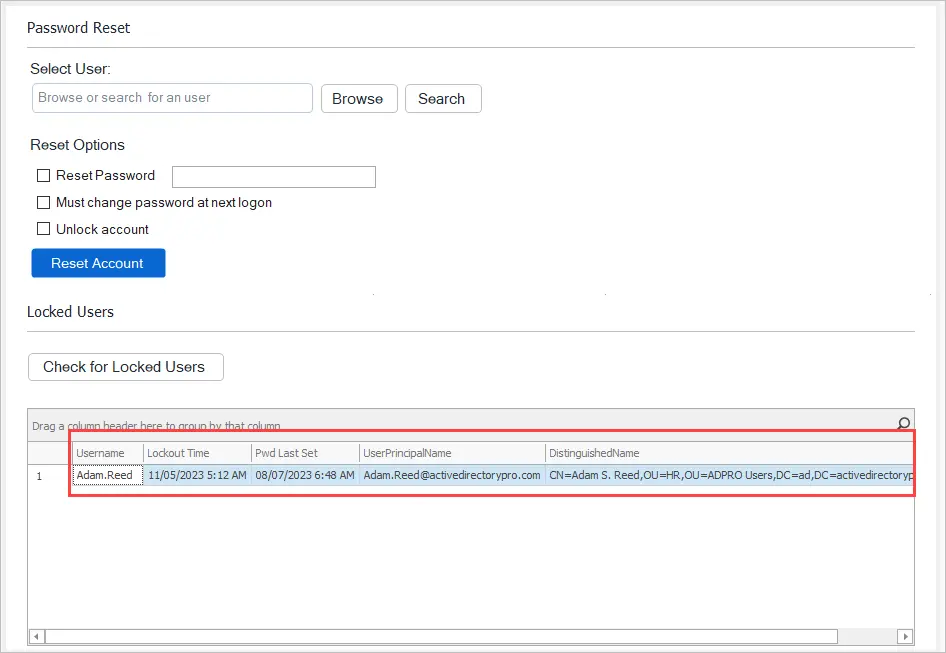
AD account lockouts are one of the top support calls helpdesk staff deal with on a day to day basis. The built-in Microsoft tools do not provide a quick and easy way to check the status of user accounts. When a user calls and says they are locked out, you need the right tools to quickly check the user status and resolve their issues.
Tools such as the Microsoft Account Lockout Status (LockoutStatus.exe) are often used in favor of the Built-in tools. Below are additional features of an AD lockout tool.
- Bad Password Count – Displays the pad password count for the user. Each time a user enters an incorrect password this will increase the counter.
- Lockout Time – Displays the date and time the account was locked out.
- Last Bad Pwd – The date and time of the last bad password for the account.
- Lockout DC or Orig Lock – Lockouts occur on specific domain controllers this will display which DC the lockout occurred on.
- All locked users – Displays all locked domain user accounts
- Source of the account lockout – Gets the event logs from the domain controller to help troubleshoot the source of an account lockout.
Now let’s dive in and see how to use these tools.
Microsoft Account Lockout Tool
Below I’ll walk you through the requirements and show you how to use the Microsoft Account Lockout Tool.
Step 1. Requirements
The following requirements must be set or the AD lockout tool will fail to run properly.
- An audit policy must be set on all computers and domain controllers, details are below. I recommend using group policy to manage the audit policy on all the computers.
- You need to have the account lockout policy configured so accounts will be locked out after so many failed logon attempts.
- You must have permission to view the security logs on the domain controllers and computers.
Step 2. Configure the Audit Policy with Group Policy
For the domain controllers, configure the audit policy settings in the Default Domain Controllers Policy.
For the computers, you can set this in the Default Domain Policy.
See my Group Policy Best Practices guide for tips on the default domain policy.
- In the Group policy management console expand computer configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy
- Enable Audit account logon events and audit logon events, enable both success and failure.
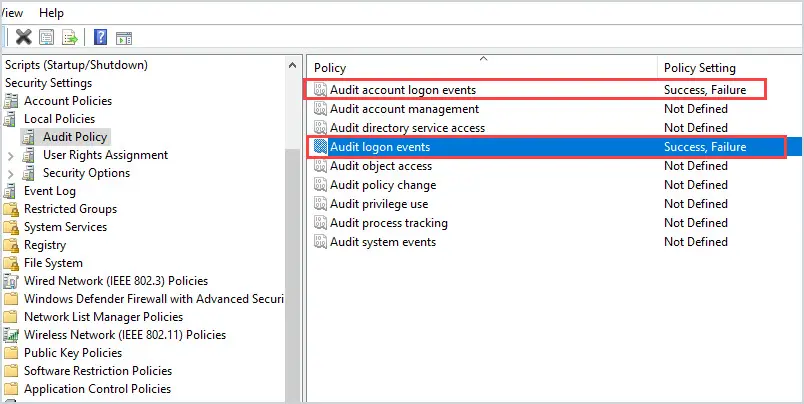
What is the difference between the two policy settings?
Audit account logon events: For domain accounts, this policy will capture logon/logoff events on the domain controller. So when you log into the domain the events will get logged on the domain controller.
Audit logon events: This policy will capture logon/logoff events at the workstation.
Step 3. Download and Install the Account Lockout Tool
The install just extracts the contents to a folder of your choice.
1. Download the Microsoft Account Lockout and Management Tools here
2. Accept the End User License
3. Type the location where you want the tools extracted and click “OK”.
Once the file is extracted you should have a list of files like below. The download contains several files and tools, for this article I’ll focus on the LockoutStatus tool.
Step 4. Open the Lockoutstatus.exe tool
1. Run the Lockoutstatus.exe tool.
2. Click on File > Select Target
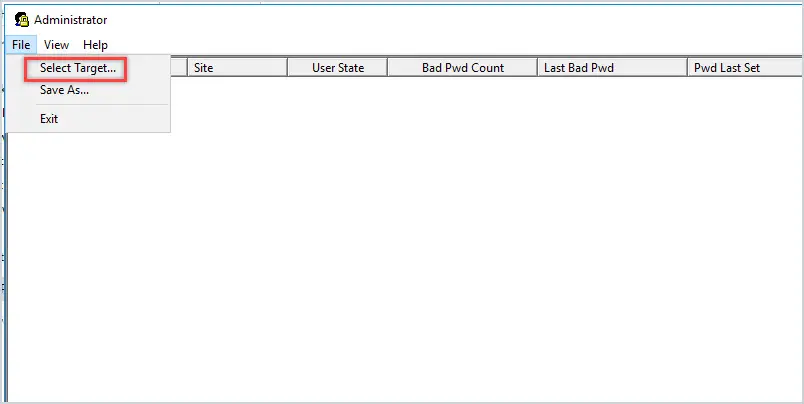
3. In the target user name box enter the user’s login name (also called the SAMAccountName) for example I’ll enter robert.allen.
4. In the target domain enter your domain.
5. Click OK
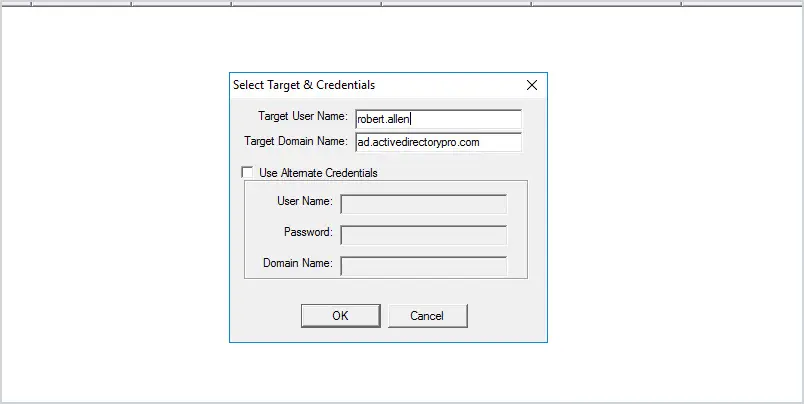
You should now see the lockout status of the account you selected. In the screenshot below you can see the user state shows Locked, which means the account is locked out.
If the account is not locked the status will show “Not Locked”
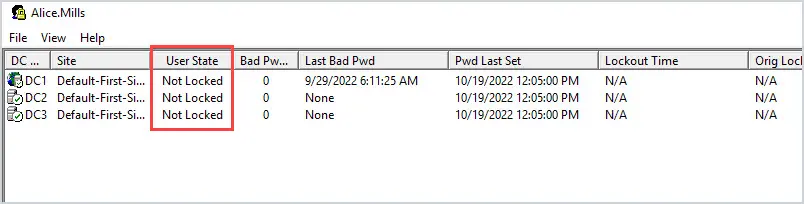
To unlock or reset the account’s password, right click on the account and select the option. You can see the lockout status tool has many options but the first two options are the most common.
That is it for the Microsoft Account Lockout tool, as you can see it is pretty easy to use. Next, I’ll walk through how to use the AD Pro lockout tool.
AD Pro Toolkit Account Lockout Tool
The AD Pro Toolkit is a collection of Active Directory Management Tools. The lockout status tool makes it very easy to find all locked users, unlock, reset passwords, and troubleshoot locked out users.
Click here to download a free trial
To find all locked users open the password reset tool and click on “Check for Locked Users”
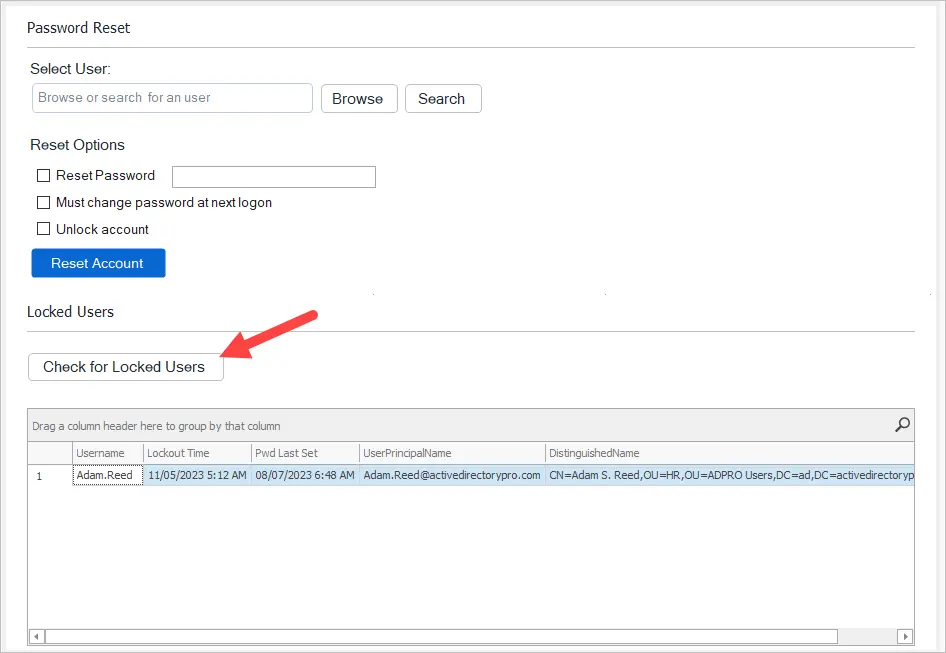
The tool will display the following details for any locked user.
- Username
- Lockout Time
- Password Last Set Date
- UserPrincipalName
- DistinguishedName
To unlock the account right-click and select unlock.
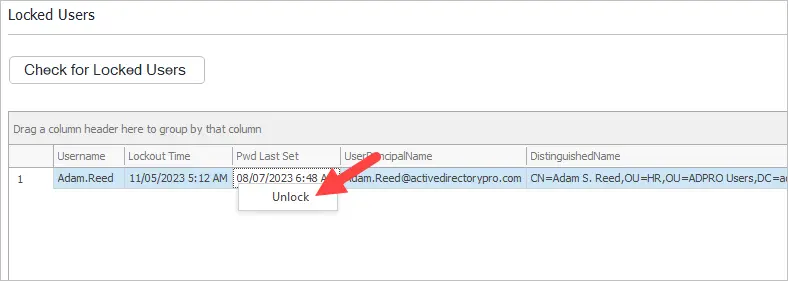
To reset the account’s password select the user and select the reset options.
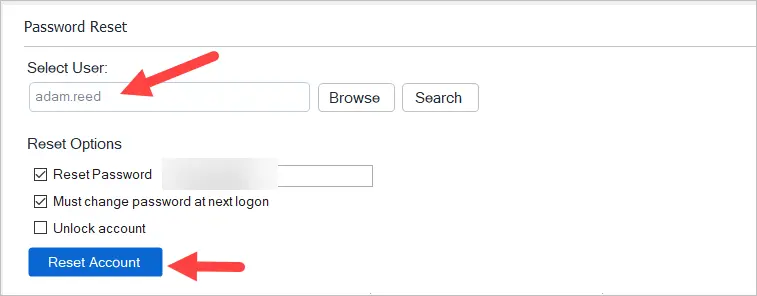
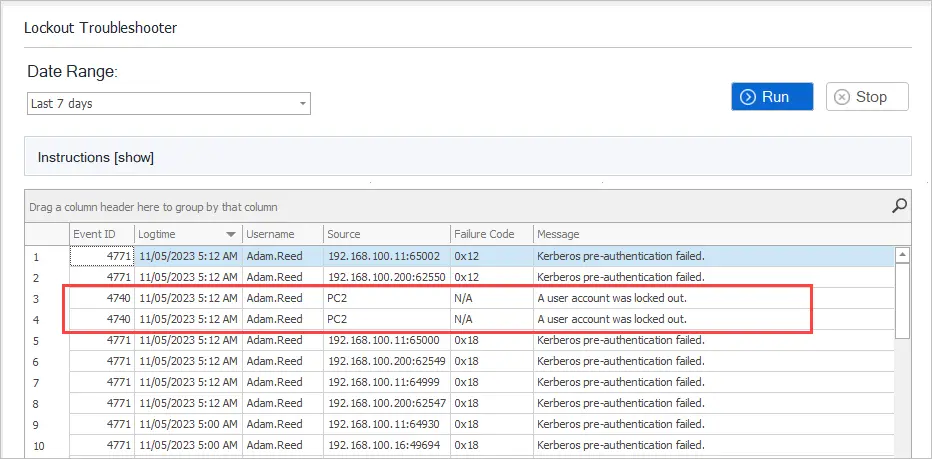
To troubleshoot an account click on “Lockout Troubleshooter” and click Run. This will show you where the lockout originated from. This comes in useful when you have accounts that keep locking out and you need to know what computer or device it is coming from.
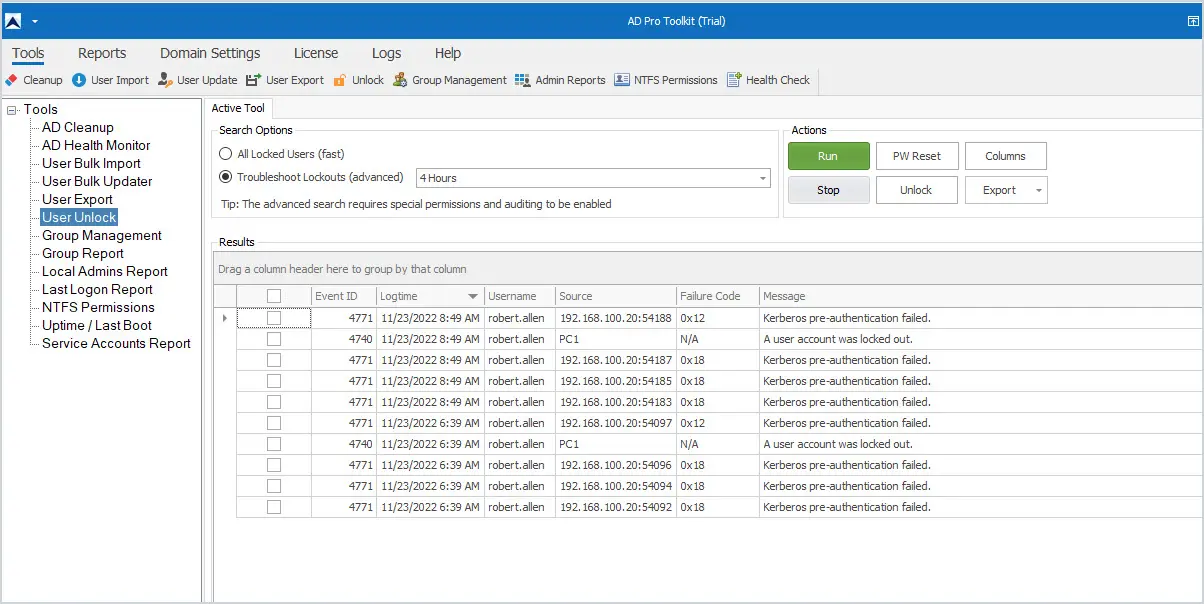
The AD Pro lockout status tool is much easier to use than the Microsoft account lockout tool as it doesn’t require entering an account, you simply click the run button to find all locked users.
Summary
If your job consists of supporting user accounts then you need a tool that lets you quickly check the status of an account. As I mentioned in this article the built-in Microsoft tools are not the best option for this. The Microsoft account lockout tool and the AD Pro Toolkit Lockout Status are great alternatives to getting an account lockout status. They also provide additional features that simplify user account management.
What is the time zone in the LockoutStatus Reports? Is it UTC? EST? Or just the local time zone that you’re in?
We recently tightened the permissions for some accounts, one of the side-effects was to make the AccountLockout.exe tool no longer usable for the updated accounts.
Is there a list of base AD permissions required for the tool to work? So far I haven’t been able to determine what specifically is needed. I realize I could do incremental permission changes and keep testing, but it isn’t a viable option.
LockoutStatus.exe should be able to check the account status with regular permissions. It looks like all of the info comes from the users AD account (which by default, regular users can read). To unlock accounts the user will need “Read lockoutTime” and “Write LockoutTime” permissions.
I can want lock out my account and show my e-mail or password
Great post.
On top of it I’d recommend to check https://www.netwrix.com/account_lockout_quick_troubleshooting_guide.html which we compiled to support IT community in troubleshooting of most common lockout scenarios.
Another useful tool to try is https://www.netwrix.com/account_lockout_examiner.html
Hi guys,
This is s great tool! Though how can I distinguish the Caller Computer Name? It is blank on my search.
Very Helpful. Thank you.
I had the same requirement in my company where helpdesk was looking for a tool that can show them where the account was getting locked out so I have created a small tool that presents these DC lockout events in a nice GUI.
Hope this helps someone, download the tool now from here:
https://github.com/ltiwana/GetLockedOutADAccounts
LT very nice.
I like that it doesn’t require any additional permissions on domain controllers.
Thanks Robert
Hello,
Thank you for this. Is there a way to pull a report of accounts that have been locked out during a time period (e.g. locked out accounts now, accounts that have been locked out the past 6 months, 9 months one year, etc)
Thanks
Hi Lyle.
Yes there is.
The best way to accomplish this is to pull the logs into a centralized logging server, you can then save the logs for as long as you want and run reports on them. Keeping 6+ months of logs on a domain controller is not recommended and will kill your performance. There are plenty of log server options, some good free ones are Windows Event Forwarding (built into Windows) Elk and Loggly. Here is a guide on setting up WEF https://www.blackhillsinfosec.com/end-point-log-consolidation-windows-event-forwarder/
My favorite premium log server for Active Directory is ManageEngine Audit plus, splunk is also great but its expensive.
Hi
Thanks for this article.
Although, I will like to know if the Caller Computer is a random 12 characters name like: BB54J3K84GRR, what will be the best way to track it?
Pinging the random name doesn’t bring up results as it’s not resolving.
My guess is user workstation is compromised as it’s getting lockout frequently.
Hi John,
You would need to use a program like ManageEngine Audit Plus, it constantly pulls the event logs from any server and displays all account lockouts and the caller computer. This would allow you to quickly see computers that have random names. This could also be scripted with PowerShell but in my experience PowerShell is really really slow at searching the event logs.
One of my most daily used tools. Mobile devices most common cause after password renewals.
TSD,
Yup phones are the most common device I see that causes lock out issues.
Hi Mug,
Currently using the lockoutstatus tool at the company I work for and it’s incredibly useful as you’ve shown. I’m wondering if you might know whether it can be told to ignore particular, or only look for certain DC’s?
For example in the first column, “DC Name”, there is a green tick as the tool is able to query successfully. However in my situation there are a number of DC’s which are installed but not fully online.
This means that when refreshing the tool, there is a considerable delay while it runs the “Collecting Data” progress bar. While assisting a user it’s often useful to be able to refresh the tool quickly, however I’m not sure where I would tell it to ignore the unavailable DC’s. Any ideas?
Best Regards,
Kev
Hi Kev,
I don’t think you can do that with this tool, it requires the domain name which searches for all DC’s. Unfortunately, I think you would run into this problem with other tools as well. Your best option would be a powershell script that would query against a specific DC, this could be as simple as searching the event logs for the logout event ID.
I’m wondering how you have DC’s installed but are not fully online, seems like that would be causing some major issues.