In this guide, I’ll show you two options on how to find locked accounts in Active Directory. Users are locked out after so many failed logon attempts, this is typically due to the password being entered incorrectly. An Account Lockout Policy defined in group policy determines how many invalid logon attempts before an account is locked out.
In this article:
- Check if an Account is locked in Active Directory
- Check if Account is locked using PowerShell
- Find all locked accounts with AD Pro Toolkit
- Find where account is being locked out from
Check if an Account is locked in Active Directory
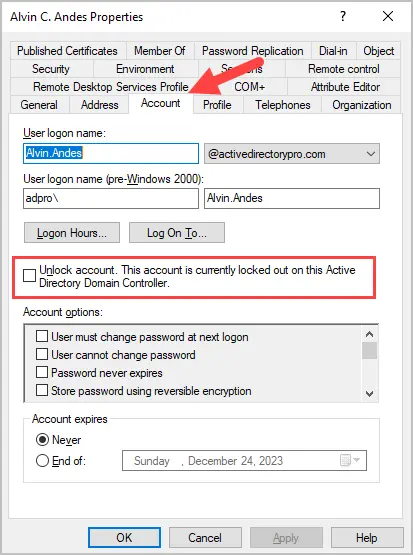
To check if an account is locked in Active Directory follow these steps:
- Open ADUC
- Open the user account you want to check
- Click the Account tab
- If the account is locked it will say “Unlock account. This account is currently locked out on this Active Directory Domain Controller”.
Check if Account is locked using PowerShell
In this example, I’ll use the Get-ADuser PowerShell cmdlet to check if a user is locked out or not. This will display the value (True or False) for the Locked Out property.
Get-ADUser robert.allen -Properties * | Select-Object LockedOut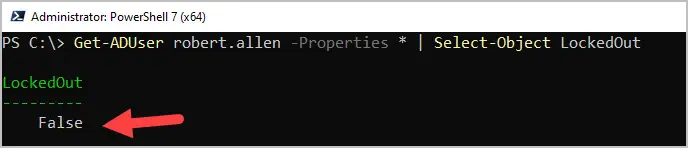
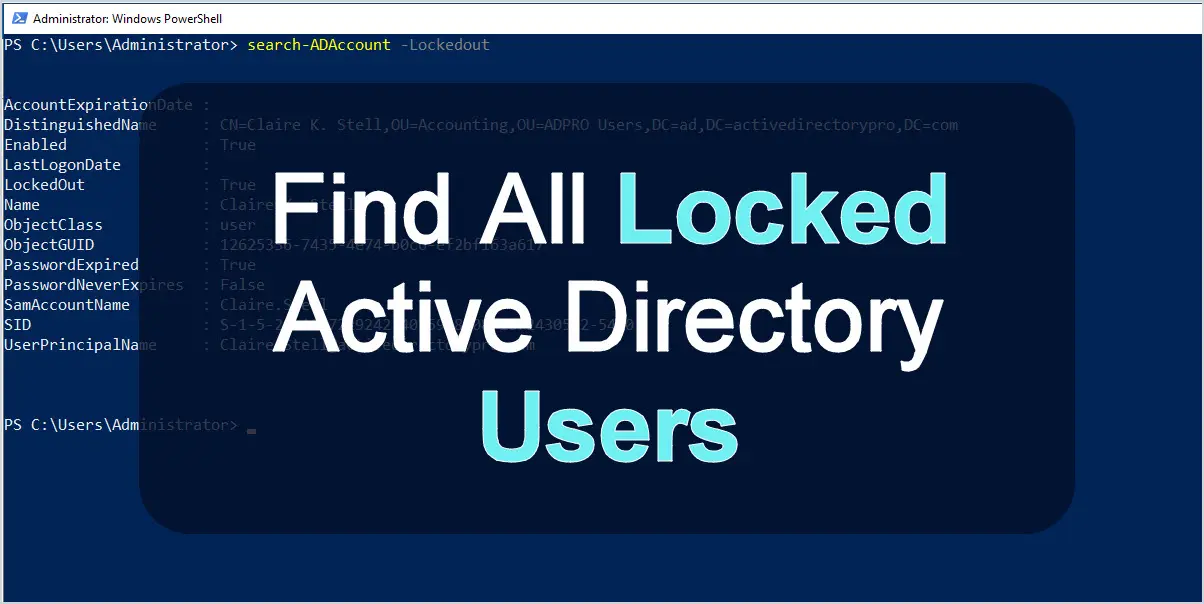
If you want to find all currently locked AD users run this command.
Search-ADAccount -LockedOut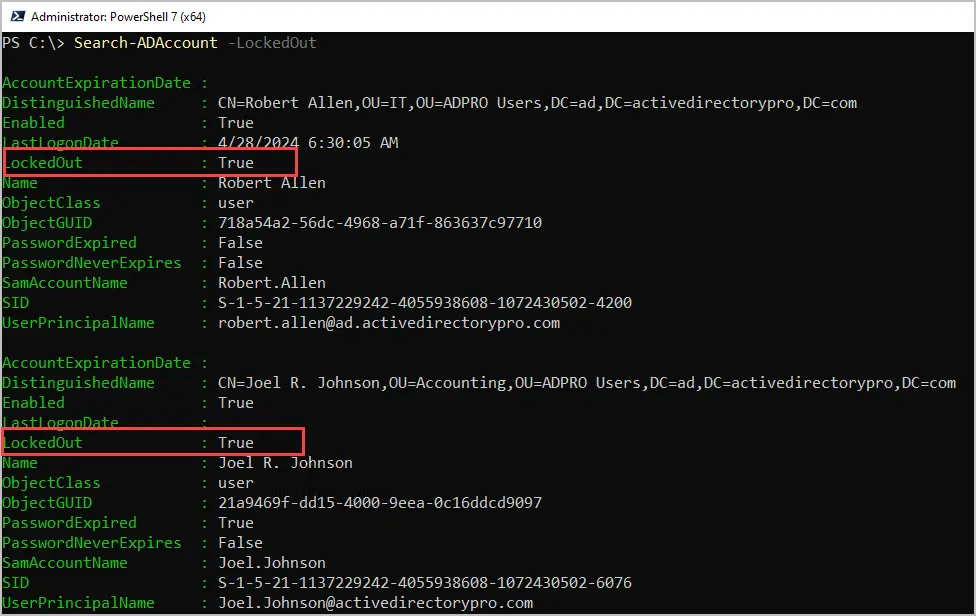
In the screenshot above you can see I have two accounts that are locked out.
If you want to find all locked accounts for enabled users only use this command.
Search-ADAccount -lockedout | where-object {$_.enabled -eq 'True'}Find all locked accounts with the AD Pro Toolkit
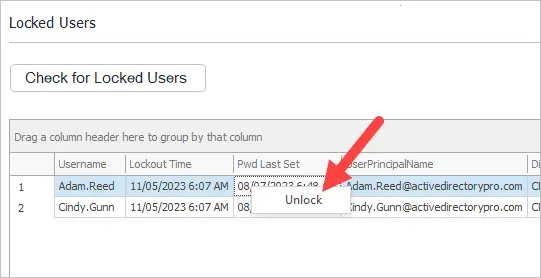
In this example, I’ll use the AD Pro Toolkit to quickly check for locked users. This tool will display all locked users, the lock out time and their password last set date. In addition, you can right click an account to unlock it.
Step 1. Open the Password & Unlock Tool
Step 2. Click the “Check for Locked Users” button
Step 3. Review the list of locked accounts.
Scheduled Locked out Reports
With the AD Toolkit you can schedule the locked out user report and have it email you the results daily, weekly or monthly. You can also choose from over 200 other AD reports to run on a schedule.
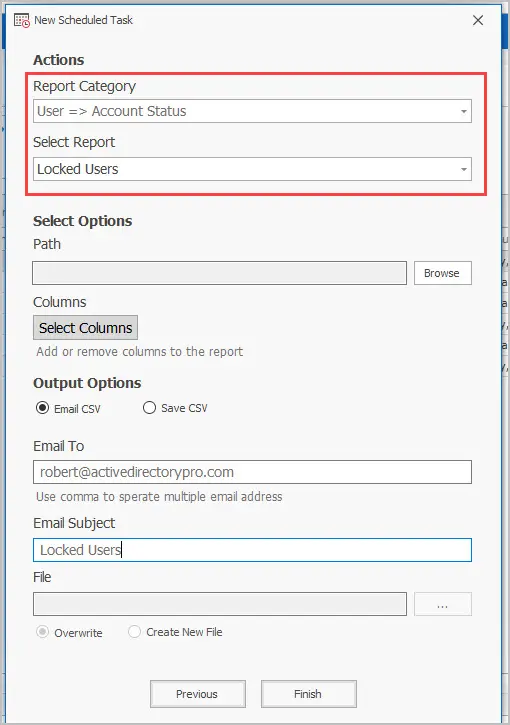
To schedule locked out report follow these steps.
- Click on the scheduler.
- Give the task a name
- Set the schedule frequency
- Select the report category of User > Account Status
- Select the report “Locked Users”
- Enter in the email details and click “Finish”.
Find Where an Account is Being Locked Out From
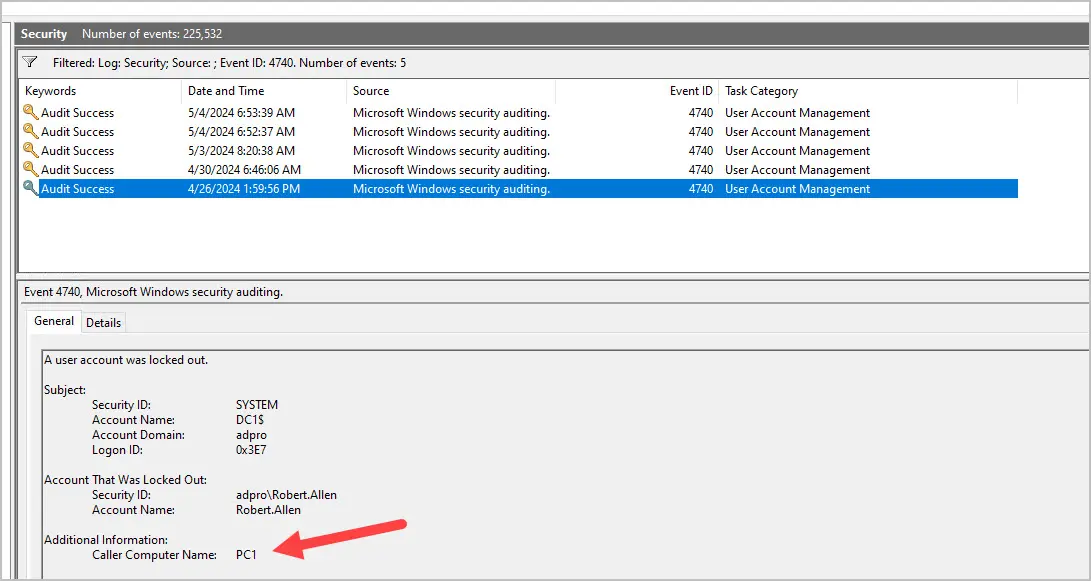
You can find where an account is being locked out from by looking at event ID 4740 on your domain controller. This event is not replicated so you would need to know which DC the lock out occurred on and then filter the logs for this event.
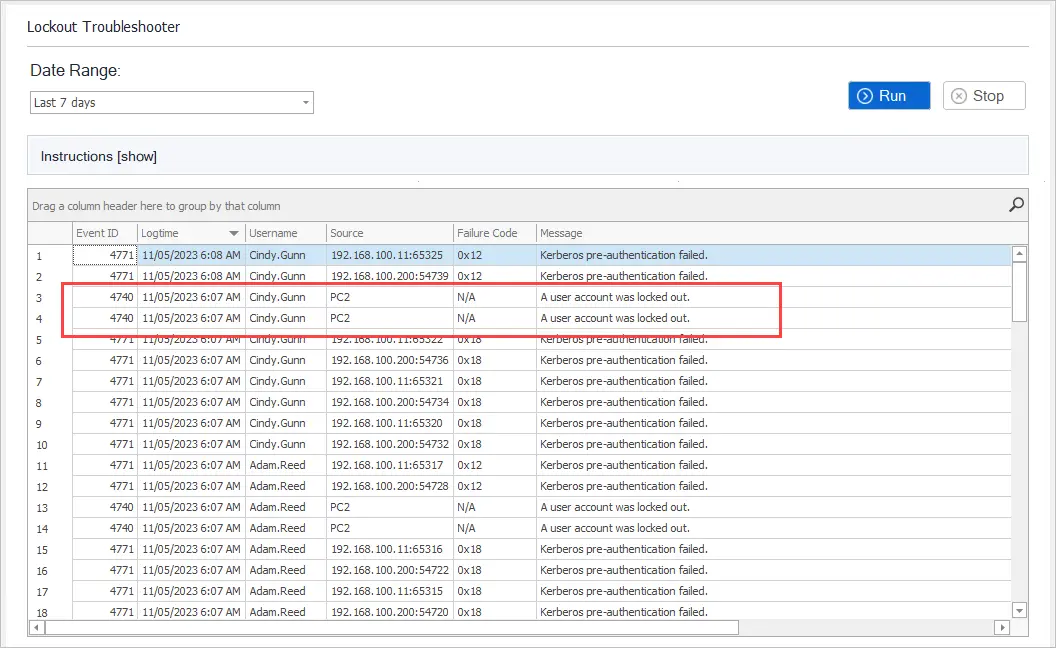
The AD Pro Toolkit includes a lockout troubleshooter tool that makes it very easy to find where accounts are locked out from. This tool will get the lockout event from all your domain controllers and display it in an easy to read format.
You can see in the screenshot below the user “Cindy.Gunn” had locked the account from PC2.
This does require permission to the logs on your domain controllers. You can delegate these permissions to helpdesk staff by giving them even log reader rights, you also need to have auditing turned on.
You can download a free trial of the user unlock tool and try it in your domain.
If you need help with turning on the audit logs check out the administrator guide for the tool.
Summary
In this guide, I showed you two options on how to find locked user accounts in Active Directory. The PowerShell Search-ADAccount cmdlet is a very easy way to display all the locked users in your domain. If you want an alternative to PowerShell and something that has more options then check out the AD Pro Toolkit. The GUI toolkit is very user friendly and requires no PowerShell experience.
If you have comments or questions let me know I’ll be happy to answer them below.
Related: Find User accounts with passwords set to never expire
Hi Robert,
Looking at the script above (AD locked user) I want the result to show me only the NON DISABLED accounts for which (Search-ADAccount -lockedout | where-object {$_.enabled -eq ‘True’}) works but I also want to sort the result by date – i.e Last Log On Date.
Much appreciated
Seems the AD Query method can also show accounts that aren’t actually locked.
I suspect it’s when an account is locked out, and it then unlocks itself due to the lockout period policy being reached.
It seems the lockouttime flag is still greater than one in this instance, despite the user account not being locked.
You can clear and remove these from the query view by ticking the “Unlock Account” option in the user properties, even though the account isn’t locked. This seems to then put that flag back to 0.
Hi Carl,
I’m also experiencing some inaccurate results with the LDAP query. I would stick to using PowerShell for this, it seems more accurate and is easier to use in my opinion.
Is there a way to just search for one specific user?
Yes, use this command to check a single user. Change username to the account name you want to check.
Get-ADUser username -Properties * | Select-Object LockedOut
I add that query to our AD, the it gives user list. Then I open a user account in ALL Locked User Accounts folder but they did not show that user is locked.
I have noticed the query is inaccurate on 2012 and newer domain controllers. I would use PowerShell instead.
Sir new id user locked
Is there a way to get rid of the disabled users in the search?
Joey, yes you can filter and just show locked users for enabled users. This should do it.
Search-ADAccount -lockedout | where-object {$_.enabled -eq 'True'}SO you have the locked out account, but the user already came to you advising you the same. I found this post searching to hoping to find the cause of the lockout. I’ve ran Lockoutstatus.exe from Microsoft and we already reset the user’s account (he will most likely be back tomorrow). I see nothing from the powershell results or the Microsoft result showing the root cause of the lockout(s). Microsoft gave me a list of our DCs which is nice but not useful in this case. Ideas?
Tracking down the source of account lockouts will require the use of the security logs. I have an article that covers this https://activedirectorypro.com/account-lockout-tool/
What would be the command to omit disabled accounts, I tried to add (Enabled=1), didn’t like that very much.
For the PowerShell command, users may need to type
Import-Module ActiveDirectory
before the search-adaccount command will work.
If you have PowerShell V5 or later you shouldn’t need to use the import module command. When you run PowerShell it should load any modules that you have installed.