In this article, you will learn about the UserAccountControl attribute in Active Directory. In addition, I’ve created a table that lists all of the UserAccountControl property flags with a description, you can search and filter the table.
Table of contents
What is the UserAccountControl attribute?
UserAccountControl is an attribute on user and computer objects in Active Directory. This attribute represents various settings and flags that tells Windows which user account options to enable. For example, when an account is disabled the UserAccountControl value for that account will be 514.
You can use the UserAccountControl attribute to search for accounts with a specific setting or update user account settings. When viewing this attribute, the value will be displayed in Decimal or Hexadecimal format. You can use the table below to see a description of each value.
UserAccountControl Attributes are Cumulative (Important)
This is very important to understand when working with the UserAccountControl attribute.
The UserAccountControl Attribute value is cumulative, meaning the number will increase when additional account properties are set. This is important to understand when searching for accounts with a specific flag, as you may be searching for the wrong value.
Let’s look at an example.
When a user account is created it typically has the value of 512 (0x200 in Hexadecimal).
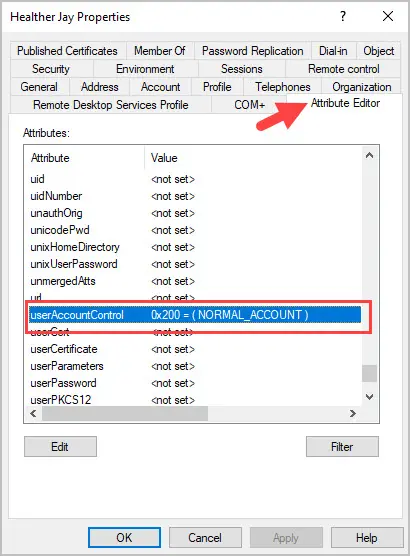
When the account is disabled the value changes to 514 (0x202 in Hexadecimal). If you look up the UserAccountControl value for a disabled account, it will be 0x002 (Decimal 2). So why did the account change to 514?
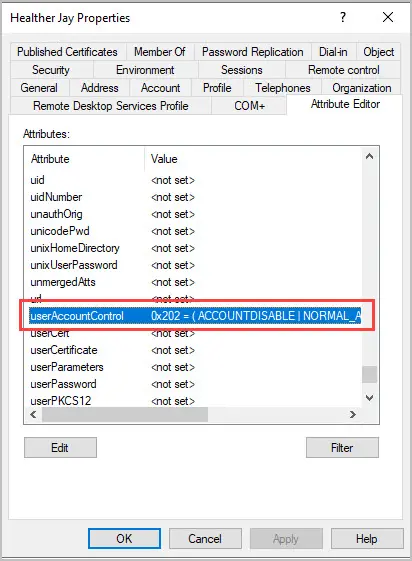
Why does the value change to 514?
- Normal User Account = 512
- Disabled Account = 2
- Add these together you get 514
Pretty straight forward but is important to know when searching and looking at the UserAccountControl value for user accounts.
List of UserAccountControl Property Flags
Tip #1: UserAccountControl flags are cumulative (see above).
Tip #2: You can’t set some of the values because these values can only be set by the directory service.
| Property flag | Hexadecimal Value | Decimal Value | Description |
|---|---|---|---|
| SCRIPT | 0x0001 | 1 | The logon script will be run. |
| ACCOUNTDISABLE | 0x0002 | 2 | The user account is disabled. |
| HOMEDIR_REQUIRED | 0x0008 | 8 | The home folder is required. |
| LOCKOUT | 0x0010 | 16 | The account locked |
| PASSWD_NOTREQD | 0x0020 | 32 | No password is required. |
| PASSWD_CANT_CHANGE | 0x0040 | 64 | The user can’t change the password. |
| ENCRYPTED_TEXT_PWD_ALLOWED | 0x0080 | 128 | The user can send an encrypted password. |
| TEMP_DUPLICATE_ACCOUNT | 0x0100 | 256 | It’s an account for users whose primary account is in another domain. |
| NORMAL_ACCOUNT | 0x0200 | 512 | It’s a default account type that represents a typical user. |
| INTERDOMAIN_TRUST_ACCOUNT | 0x0800 | 2048 | It’s a permit to trust an account for a system domain that trusts other domains. |
| WORKSTATION_TRUST_ACCOUNT | 0x1000 | 4096 | It’s a computer account for a computer that is running Microsoft Windows NT 4.0 Workstation, NT 4.0 Server, 2000 PRO or 2000 server and is a member of this domain. |
| SERVER_TRUST_ACCOUNT | 0x2000 | 8192 | It’s a computer account for a domain controller that is a member of this domain. |
| DONT_EXPIRE_PASSWORD | 0x10000 | 65536 | Represents the password, which should never expire on the account. |
| MNS_LOGON_ACCOUNT | 0x20000 | 131072 | It’s an MNS logon account. |
| SMARTCARD_REQUIRED | 0x40000 | 262144 | When this flag is set, it forces the user to log on by using a smart card. |
| TRUSTED_FOR_DELEGATION | 0x80000 | 524288 | When this flag is set, the service account (the user or computer account) under which a service runs is trusted for Kerberos delegation. |
| NOT_DELEGATED | 0x100000 | 1048576 | When this flag is set, the security context of the user isn’t delegated to a service even if the service account is set as trusted for Kerberos delegation. |
| USE_DES_KEY_ONLY | 0x200000 | 2097152 | (Windows 2000/Windows Server 2003) Restrict this principal to use only Data Encryption Standard (DES) encryption types for keys |
| DONT_REQ_PREAUTH | 0x400000 | 4194304 | (Windows 2000/Windows Server 2003) This account doesn’t require Kerberos pre-authentication for logging on. |
| PASSWORD_EXPIRED | 0x800000 | 8388608 | (Windows 2000/Windows Server 2003) The user’s password has expired. |
| TRUSTED_TO_AUTH_FOR_DELEGATION | 0x1000000 | 16777216 | (Windows 2000/Windows Server 2003) The account is enabled for delegation. It’s a security-sensitive setting |
| PARTIAL_SECRETS_ACCOUNT | 0x04000000 | 67108864 | (Windows Server 2008/Windows Server 2008 R2) The account is a read-only domain controller (RODC). It’s a security-sensitive setting. |
How to View the UserAccountControl Attribute
In this section, I’ll show you how to view the UserAccountControl attribute using Active Directory and PowerShell.
Step 1. Open ADUC
Open Active Directory users and computers console.
Step 2. Open a User Account
Open any account and click on the attribute editor tab. Scroll down to the UserAccountControl attribute.

In the Attribute Editor box, it’s going to display the Hexadecimal value. If you edit the attribute, it will display the Decimal value.
Step 3. Using PowerShell
To get the UserAccountControl value using PowerShell use this command.
get-aduser -identity USERNAME -properties * | select name, useraccountcontrol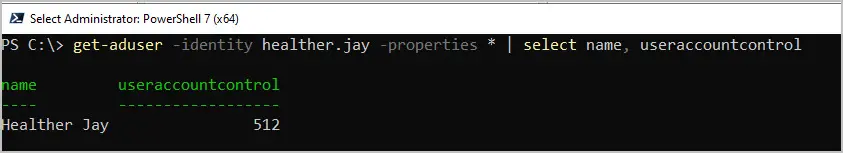
How to Find Accounts with a Certain UserAccountControl Flag
You can easily search Active Directory for accounts that have a specific UserAccountControl Flag.
Example 1. Find accounts with the 512 (Normal) flag
In this example, I use equal to PowerShell operator to for the 512 value.
get-aduser -filter * -properties UserAccountControl | where {$_.UserAccountControl -eq 512} | select name, UserAccountControl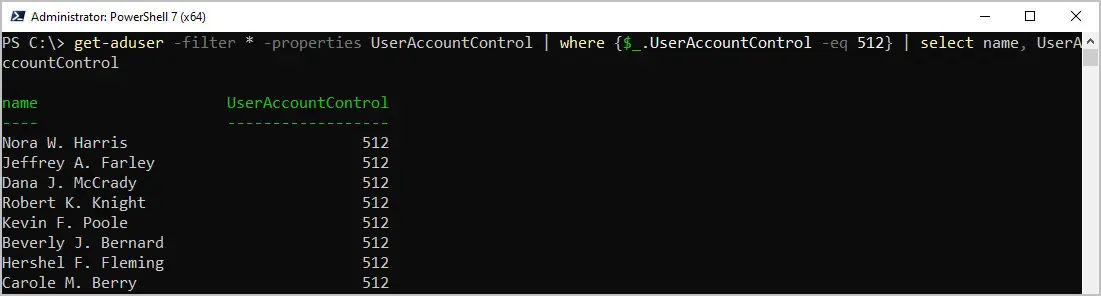
Example 2. Find accounts that are not normal
In this example, I use the not equal to operator to list all accounts that are not 512.
get-aduser -filter * -properties UserAccountControl | where {$_.UserAccountControl -ne 512} | select name, UserAccountControl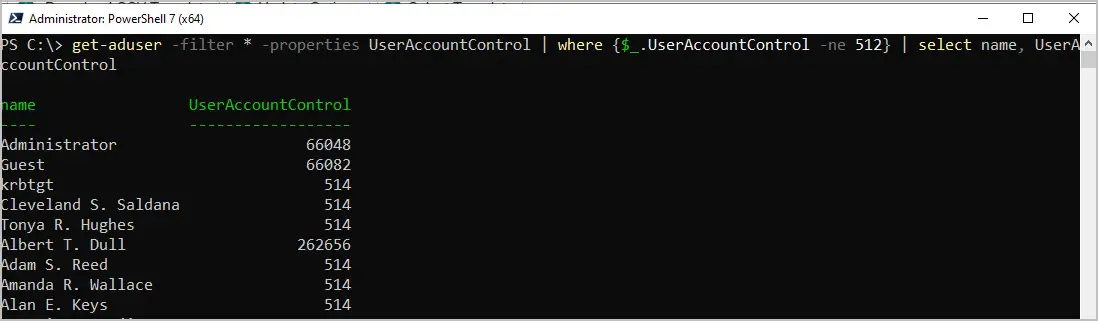
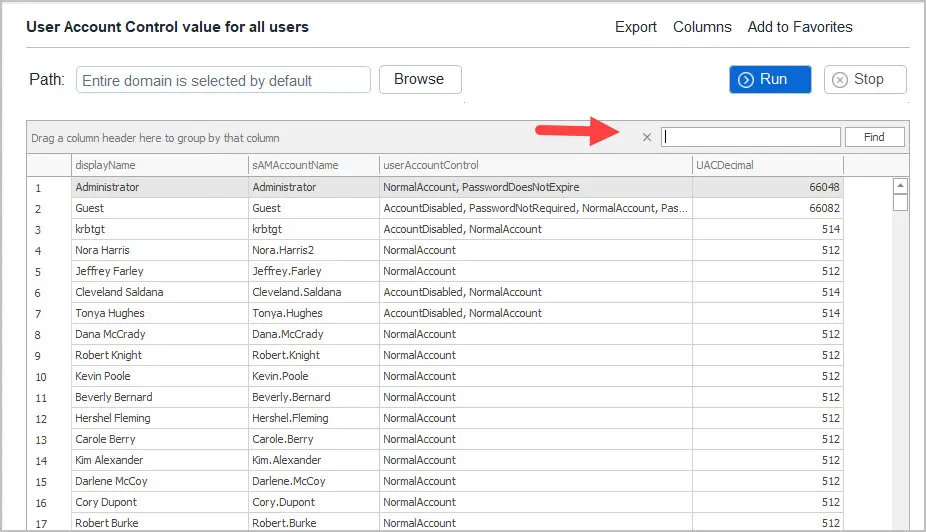
Example 3. AD Pro Toolkit
The AD Pro Toolkit includes over 200 built in reports. You can quickly run reports with just a few mouse clicks. The search box lets you filter and search the report.
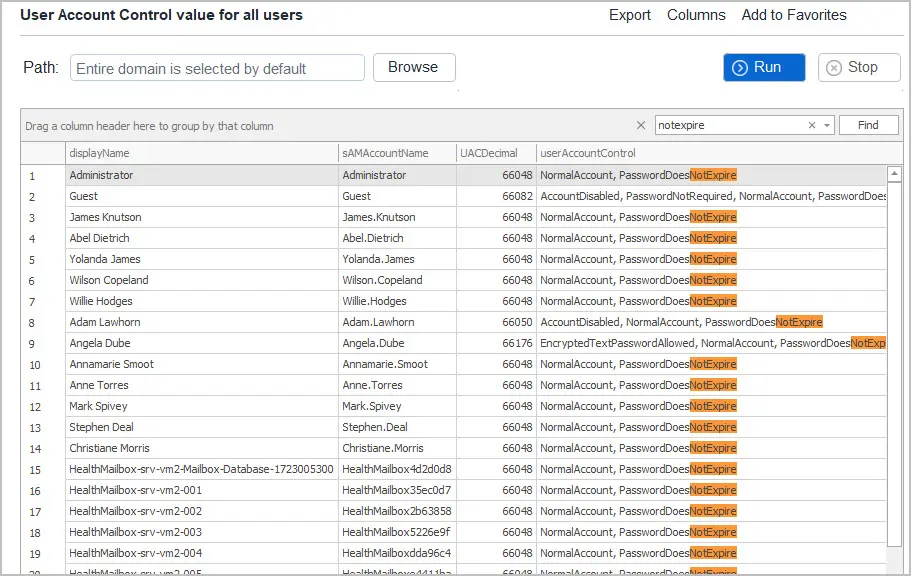
In the below screenshot, I search for any account that is set to PasswordDoesNotExpire. You can see the UAC Decimal numbers are different for some users, this is because accounts have multiple settings enabled. With the toolkit you can search on all columns which makes it easy to find specific accounts.
How to Change UserAccountControl Attribute
Warning: You should not blindly change the UserAccountControl attribute. This is not a typical task and should only be done under specific circumstances. In addition, if you’re going to do this for multiple accounts, you should test it on 1 or 2 to make sure it has the desired effects.
There are a few ways you can change the UserAccountControl attribute.
- Manually using ADUC
- PowerShell
- AD Pro Toolkit
Manually using ADUC
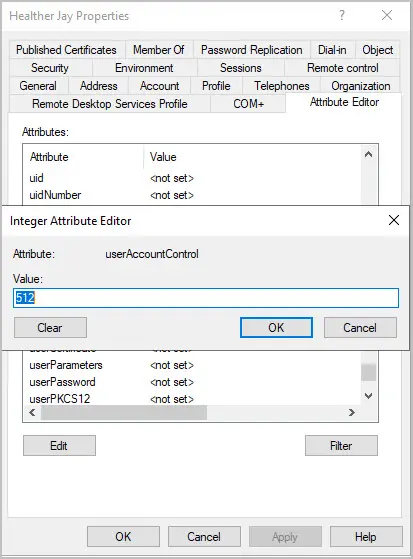
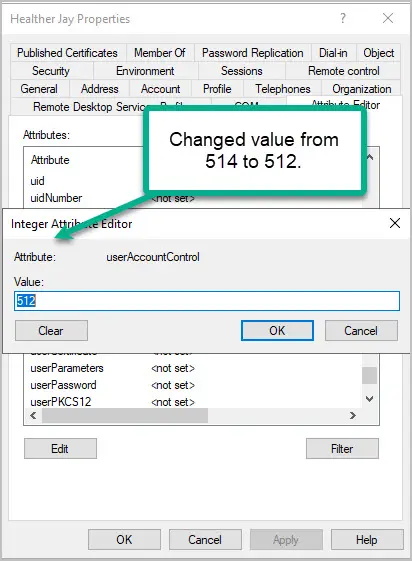
With ADUC you can open the user account and edit the userAccountControl attribute then enter a new value. For example, this accounts value is 514, I will change it to 512.
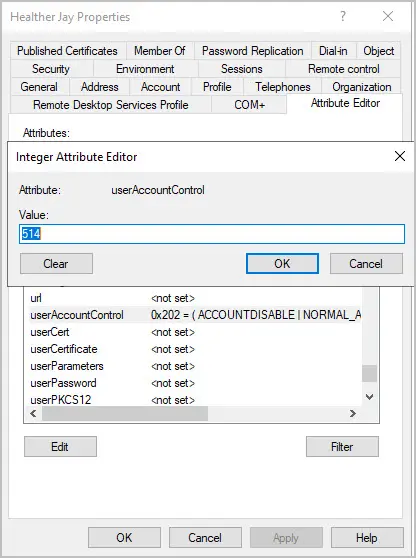
In the value box I will enter 512 and click OK.
Change UserAccountControl with PowerShell
You can use the set-aduser cmdlet to change the UserAccountControl attribute. In this example I change the value from 514 to 512.
set-aduser -identity healther.jay -replace @{useraccountcontrol=512}There is also the set-ADAccountControl cmdlet that lets you modify the UserAccountControl values.
Set-ADAccountControl -Identity healther.jay -PasswordNotRequired $False