I’ve grouped terms together in different sections to make it easier to understand and reference. Some topics can be very technical, but I’ve provided short and easy to understand terminology. I then provide additional resources at the end of each section if you wish to learn more.
Table of contents:
- Active Directory Basics Terms – Start Here
- Active Directory Services
- Active Directory DNS
- Active Directory Replication
- Active Directory Security (Authentication, Security Protocols, Permissions)
- Active Directory Management Consoles
- DHCP
- Group Policy
Active Directory Basics Terms
These are basic terms you should be familiar with when dealing with Active Directory.
Active Directory
Active Directory is a directory service that centralizes the management of users, computers, and other objects within a network. Its primary function is to authenticate and authorize users and computers in a windows domain. For example, when a user signs into a computer on the domain it checks the username and password that was submitted to verify the account. If it is a valid username and password the user is authenticated and logged into the computer.
Don’t get confused with the following three terms they all refer to Active Directory.
- AD – This is just an abbreviation for Active Directory
- AD DS – This is a server that is running the Active Directory Domain Services Role
- Domain Controller – This is also a server running the Active Directory Domain Service Role. It is recommended to have multiple domain controllers for failover reasons.
Active Directory Web Servers (ADWS)
This service was introduced in Windows Server 2008 R2. It is automatically installed with ADDS or ADLDS role and is configured to run automatically. This service provides remote management of any local directory services.
Domain
The domain is a logical structure of containers and objects within Active Directory. A domain contains the following components:
- A hierarchical structure for users, groups, computers and other objects
- Security services that provide authentication and authorization to resources in the domain and other domains
- Policies that are applied to users and computers
- A DNS name to identify the domain. When you log into a computer that is part of a domain you are logging into the DNS domain name. My DNS domain is ad.activedirectorypro.com, this is how my domain is identified.
Domain Tree
When you add a child domain to a parent domain you create what is called a domain tree. A domain tree is just a series of domains connected together in a hierarchical fashion all using the same DNS namespace. If activedirectorypro.com was to add a domain called training, or videos it would be named training.activedirectorypro.com and videos.activedirectorypro.com. These domains are part of the same domain tree and a trust is automatically created between the parent and child domains.
Functional Levels
Functional levels determine what capabilities are available in the domain. Higher functional levels allow you to use the latest and greatest technologies in your Active Directory domain. When possible use the highest functional levels for your domain controllers.
Forest
A forest is a collection of domain trees. The domain tree shares a common schema and configuration container. The domain tree is connected together through a transitive trust. When you first install Active Directory and create a domain you are also creating a forest.
FQDN – Fully Qualified Domain Name
A fully Qualified Domain name is the hostname + the domain, for example, my domain is ad.activedirectorypro.com, a computer in the domain with hostname PC1 so the FQDN would be pc1.ad.activedirectorypro.com.
FSMO
A domain controller has multiple functions that are referred to as the FSMO roles. These roles are all installed on the first domain controller in a new forest, you can move roles across multiple DCs to help with performance and failover.
- Schema Master – The schema master is a forest wide role that handles all the changes to the Active Directory schema.
- Domain Naming Master – This is a forest wide role that is the master of domain names. It handles the namespace and adding removing domain names.
- PDC Emulator – This role handles password changes, user lockouts, group policy and is the time server for the clients.
- RID Master – This role is responsible for processing RID pool requests from all DCs within the domain. When objects such as users and computers are created they get assigned a unique SID and a relative ID (RID). The RID master role ensures objects do not get assigned the same SID and RIDs.
- Infrastructure master – This is a domain wide role used to reference objects in other domains. If users from Domain A are members of a security group in Domain B, the infrastructure master role is used to reference the accounts in the correct domain.
Objects
When working with Active Directory you will primarily be working with objects. Objects are defined as a group of attributes that represent a resource in the domain. These objects are assigned a unique security identifier (SID) that is used to grant or deny the object access to resources in the domain. The default object types created in a new domain in Active Directory are:
- Organizational Unit (OU) – An OU is a container object that can contain different objects from the same domain. You will use OUs to store and organize, user accounts, contacts, computers, and groups. You will also link group policy objects to an OU.
- Users – User accounts are assigned to primarily assigned to users to gain access to domain resources. They can also be used to run programs or system services.
- Computer – This simply is a computer that is joined to the domain.
- Groups – There are two types of objects, a Security group, and a distribution group. A security group is a grouping of users accounts that can be used to provide access to resources. Distribution groups are used for email distribution lists.
- Contacts – A contact is used for email purposes. You cannot log on to the domain as a contact and it cannot be used to secure permissions.
- Shared Folder – When you publish a shared folder in Active Directory it creates an object. Publishing shared folders to AD makes it easier for users to find shared files and folders within the domain.
- Share Printer – Just like shared folders you can publish printers to Active Directory. This also makes it easier for users to find and use printers on the domain.
LDAP (Lightweight Directory Access Protocol)
LDAP is an open platform protocol used for accessing directory services. LDAP provides the communication mechanism for applications and other systems to use interact with directory servers. In simple terms, LDAP is a way of connecting and communicating with Active Directory.
Global Catalog (GC)
The global catalog server contains a full replica of all objects and is used to perform forest wide searches. By default the first domain controller in a domain is designated as the GC server, it is recommended to have at least one GC server for each site to improve performance.
Jet Database Engine
The Active Directory database is based on Microsoft’s Jet Blue engine and utilizes the Extensible Storage Engine (ESE) to work with the data. The database is a single file named ntds.dit, by default, it is stored in the %SYSTEMROOT%\NTDS folder and each domain controller.
Recycle Bin
The Active Directory recycle bin allows administrators to easily recover deleted items, this is not enabled by default. How to enable the Recycle Bin step by step guide.
Read-Only Domain Controller (RODC)
RODC servers hold a read-only copy of the Active Directory database and do not allow changes to AD. Its primary purpose is for branch offices and locations with poor physical security.
Schema
The Active Directory schema defines every object class that can be created and used in an Active Directory forest. It also defines every attribute that can exist in an object. In other words, it is a blueprint of how data can be stored in Active Directory. For example, a user account is an instance of the user class, it uses attributes to store and provide information about that object. A computer account is another instance of a class that also is defined by its attributes.
There are many classes and attributes unless your programming or troubleshooting some advanced issue it is not necessary to know everything about the schema.
SYSVOL
The sysvol is a very important folder that is shared out on each domain controller. The default location is %SYSTEMROOT%\SYSVOL\sysvol and is made up of the following:
- Group Policy Objects
- Folders
- Scripts
- Junction Points
Tombstone
Tombstone is a deleted object from AD that has not been removed from the database, the object technically remains in the database for a period of time. During this period of time the object can be restored.
Object Name Attributes
The following are some important attributes that you should be familiar with when working with Active Directory.
- userPrincipalName (UPN) – This is a common logon name that is in the format of an email address. A UPN looks like this, robert@ad.activedirectorypro.com, a UPN can be used to log into a windows domain.
- objectGUID – This attribute is used to uniquely identify a user account. Even if the account is renamed or moved, the objectGUID never changes.
- sAmAccountName – This attribute is user for account logons to a domain. It was the primary means to logon to a domain for older Windows versions, it can still be used on modern versions of Windows.
- objectSID – This attribute is the security identifier (SID) of the user. The SID is used by the server to identify a user and their group membership to authorize users access to domain resources.
- sIDHistory – This attribute contains previous SIDs for the user object. This is only needed if a user has moved to another domain.
- Relative Distinguished Name (RDN) – The RDN is the first component of the distinguished name. It is the name of the object in Active Directory relative to its location in the hierarchical structure of AD
- Distinguished Name (DN) – The DN attribute locates objects in the directory. This attribute is commonly used by services and applications to locate objects in Active Directory. a DN is made up of the following components:
- CN – common name
- OU – organizational unit
- DC – domain component
Groups
Groups are used to collect user accounts, computer, and contact objects into management units. Creating groups makes it easier to control permissions to resources and assign resources such as printers and folders. There are two types of groups
- Distribution – Distribution groups are used by email applications t easily send an email to a group of users.
- Security – Security groups are a group of accounts that can be used to easily assign to a resource or apply for permissions. For example, if I wanted to lock down a folder for the HR department I could just put all the employees in a security group and apply the group to the folder instead of every individual account.
Group Scope
Group scope identifies if the group can be applied in the domain or forest. Here are the three group scopes:
- Universal – Can contain objects from other universal groups and any domain in the tree or forest.
- Global – Can contain objects from the domain and be used in any domain tree or forest.
- Domain Local – Can contain objects from any domain but can only be applied to the domain it was created in.
Active Directory Services
Active Directory includes several other services that fall under the Active Directory Domain Services, these services include:
Active Directory Certificate Services (AD CS)
This is a server role that allows you to build a public key infrastructure (PKI) and provide digital certificates for your organization. Certificates can be used to encrypt network traffic, application traffic, and used to authenticate users and computers. When you see https in a browser address that means it is using a certificate to encrypt the communication from the client to the server.
Active Directory Domain Services (AD DS)
See Active Directory description
Active Directory Federation Services (AD FS)
The federation service allows single sign on to external systems like websites and applications. Office 365 is a common use for federation services. When you sign into office 365 the username and password is redirected through the federation server and the credentials are checked against your on-premise Active Directory. So this allows you to provide authentication to external systems by using your local Active Directory to authenticate the username and password.
Active Directory Lightweight Directory Services (AD LDS)
This service provides directory services using the LDAP protocol without the need to deploy domain controllers. This is primarily used to provide directory service functionally to directory enabled applications. This does not replace AD DS.
Active Directory Rights Management Services (AD RMS)
This service provides methods for protecting information on digital content. It protects documents by defining who can open, modify, print, forward or take other actions on documents. You can also use certificates to encrypt documents for better security.
Active Directory DNS
Domain Name System is a service that provides name resolution, most commonly hostname to IP address resolution. In this section, you will learn about some of the important components of DNS.
Resource Records
A resource record is an entry in the DNS system that helps locate resources based on IP or a domain name. There are many types of resource records, below is a list of common record types:
- A – maps a hostname to an IPv4 address
- AAAA – Maps a hostname to an IPv6 address
- CNAME – Maps an alias to a hostname
- MX – Used to locate a mail server
- NS – Specifics a name server for a domain
- PTR – Maps an IPv4 address to a hostname. The reverse of an A record.
- SOA – Contains administrative information
- SRV – Used to locate servers that host specific services
- TXT – Can contain various data. Often used for verifying domains and security reasons.
Dynamic DNS (DDNS)
Dynamic DNS is a method for clients to register and dynamically update their resource records with a DNS server. This allows clients that use DHCP to auto update their DNS record when their IP address changes.
Host Name
This is most often the DNS A record, the DNS name of a device that can be communicated with. For example, a server with the name of DC1. If DC1 was registered in DNS you would refer to that as the hostname.
Zones
A zone is used to host the DNS records for a particular domain. The most important and commonly used zone type is Active Directory integrated zones. There are several other zones you should be familiar with, I cover the other zones in my article, Windows DNZ Zones Explained.
DNS Aging and Scavenging
This is a feature that can be enabled to help automate the cleanup of stale DNS records. I’ve created a separate post that explains more and provides step by step instructions to configure DNS Aging and Scavenging.
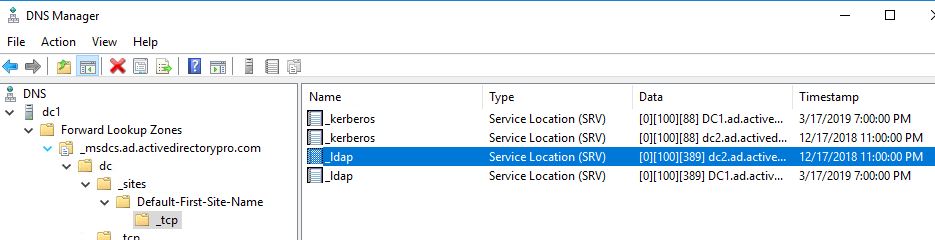
SRV Records Used by Active Directory
In a Windows Domain, SRV records are used by clients to locate domain controllers for Active Directory. When you install the AD DS service the process will automatically create the SRV records for Active Directory.
- Active Directory creates its SRV records in the following folders, where Domain_Name is the name of your domain:
- Forward Lookup Zones/Domain_Name/_msdcs/dc/_sites/Default-First-Site-Name/_tcp Forward Lookup Zones/Domain_Name/_msdcs/dc/_tcp
Here is a screenshot from my DNS:
Forwarders
DNS forwarders are servers that resolve hostnames that your internal DNS server cannot resolve, primarily external domains such as internet browsing. You can set up to forward DNS requests to any server of your choosing, often times an ISP is used.
Root Hints
Root hint server is another method to resolve hostnames that your internal server cannot resolve. The difference is these servers serve as the root DNS zone for the internet. They are managed by several large organized for security and redundancy. You can use either root hints or forwards to resolve external names.
Resources:
- Complete List of DNS resource record types
- How to verify that SRV DNS records have been created for a domain controller
- Root Hints vs Forwarders
- DNS Best Practices
Active Directory Replication
Replication is the process that ensures changes made to one domain controller are replicated to other domain controllers in the domain.
Connection Objects
The connection object specifics which domain controllers replicate with each other, how often and their naming contexts.
KCC
The Knowledge Consistency Checker (KCC) is a process that runs on all domain controllers and generates a replication topology based off the sites, subnets and site link objects.
Subnets
A subnet is a logical portion of an IP network. Subnets are used to group devices into a specific network, often by location, building or floor. If you have a multisite environment, Active Directory needs to know about your subnets so it can properly identify the most efficient resources. If this information is not provided clients can authenticate and use the wrong domain controller.
Site
A site is a collection of subnets. The Active Directory sites help define the replication flow and resource location for clients such as a domain controller.
Site Link
Site links allow you to configure what sites are connected to each other.
Site link Bridge
A site link bridge is a logical connection between sites. It is a method to logically represent transitive connectivity between sites.
Site Topology
The site topology is a map that defines the network connectivity for replication and location for resources in the Active Directory forest. The site topology consistent of several components including sites, subnets, site links, site link bridges, and connection objects.
Intra-Site Replication
This is replication that occurs between domain controllers in the same site.
Inter-Site Replication
In an environment with multiple sites, a change in one site needs to be replicated to the other site. This is called Inter-Site replication.
Resources:
Active Directory Security (Authentication, Security Protocols, Permissions)
Kerberos
Kerberos is a security protocol that securely allows users to prove their identity to gain access to domain resources.
Ticket Granting Ticket (TGT)
The TGT are files created by the KDC, they are used to grant users access to network resources.
Key Distribution Center (KDC)
KDC is a service that runs on domain controllers and supplies session tickets used in the Kerberos authentication protocol.
Service Principal Names (SPN)
SPN is a unique identifier of a service instance.
NTLM
NTLM is a collection of security protocols used to authenticate, provide integrity and confidentiality to users. Kerberos is the preferred authentication protocol and is used in modern Windows versions, NTLM is still available for older clients and systems on a workgroup.
NTFS Permissions
NTFS permissions allow you to define who is authorized to access a file or folder. Below is a list of the basic permissions you can set:
- Full Control – This gives users the rights to add, modify, move and delete files and folders.
- Modify – Gives users view and rights to modify
- Read & Execute – Gives users view and execute rights
- Read – ready only rights
- Write – right to a file and add new folders
Share Permissions
Share permissions define the level of access to shared resources such as a folder. There are three basic shared permissions:
- Read – Gives users view rights to the folder and subfolders
- Change – Gives users read and modify rights
- Full Control – Gives users modify, change and read rights.
Discretionary access control list (DACL)
A DACL identifies what account is allows or denied access to an object such as a file or folder.
Access Control Entries (ACE)
DACL contains ACEs, the ACE defines what account and what level of access is to be granted to the resource. If no ACE is present the system denies all access to the object.
System Access Control List (SACL)
The SACL enables admins to log attempts to access a security object.
Fine Grained Password Policy
A feature in Windows 2008 and above that allows you to define different password and account lockout policies for different accounts. Generally, all accounts should have the same policy but you may have a service account or a very specific account that needs a different policy. For example, our guest wifi account kept getting locked out due to bad password attempts. I used a fine granted password policy to set a higher account lockout then the rest of the domain.
Resources:
- Kerberos for the Busy Admin
- Windows Authentication Technical Overview
- Differences Between Share and NTFS Permissions
- Access Control Lists
Active Directory Management Consoles
This section includes the management consoles you will need to use to manage the various Active Directory technologies. You will need to install the Remote Server Administration Tools (RSAT) to access these management consoles.
Active Directory Users and Computers (ADUC)
This is the most commonly used console for managing users, computers, groups, and contacts.
Shortcut: dsa.msc
Active Directory Administrative Center (ADAC)
Starting with Server 2008 R2 Microsoft introduces the ADAC to manage their directory service objects. This console can be used to create and manage user accounts, computer accounts, groups, and organizational units. It provides the same functionality as the Active Directory Users and Computers tool. Due to the complicated interface, I prefer ADUC over this console.
Active Directory Domains and Trusts
This console is used to raise the domain mode or functional level of a domain or forest. It is also used to manage trust relationships.
Shortcut: domain.msc
Active Directory Sites and Services
This is the main console for managing replication. This console is used to manage site topology objects, connection objects, schedule replication, manually force replication, enable the global catalog, and enable universal group caching.
Shortcut: dssite.msc
ADSI Edit
Active Directory Service Interfaces Editor is a GUI tool that can be used to manage objected in Active Directory. This tool provides access to object data that is not available in Active Directory Users and Computers.
Shortcut: adsiedit.msc
DFS Management
This console is used to manage DFS namespaces and DFS replication.
Shortcut: dfsmgmt.msc
DHCP
This console is used to create DCHP scopes, view lease information and all things DHCP.
Shortcut: dhcpmgmt.msc
DNS
This console is used to create DNS zones, resource records and manage all things DNS.
Shortcut: dnsmgmt.msc
Group Policy Management
This console is used to manage group policy and group policy objects.
Shortcut: gpmc.msc
PowerShell
Although this is not a management console it is the most powerful tool to automate administrative tasks. PowerShell can speed up many routine tasks that the GUI management tools cannot do.
Resources:
Dynamic Host Control Protocol (DHCP)
Dynamic Host configuration protocol is a service that provides centralized control of IP address. When your computer connects to a wired or wireless network a DHCP server is contacted to find and assign you an available IP address.
Scope
A DHCP scope is a collection of IP address settings that are configured for devices such as a computer to use. You can create multiple scopes for different device types and subnets. For example, I have a scope for computers and different scopes for IP phones. When you setup a scope, you will need to configure the following:
- Scope name – This is the name of the scope. Give it a descriptive name so it is easy to identify which devices it is for.
- IP address range – This is the IP range that you want the devices to use. For example 10.2.2.0/24
- IP address exclusions – You can specify to exclude IP address from the scope. This is useful if you have devices on the subnet that need a static IP like a router or server.
- Lease duration – The lease specifies how long a client has an IP address before returning it to the pool.
- DHCP options – There are a number of different options you can include when DHCP assigns an IP address. More on this below
DHCP options
There are many DCHP options, below are the most commonly used options in a Windows domain.
- 003 router – The default gateway of the subnet
- 005 DNS server – The IP address of the DNS server clients should use for name resolution.
- 015 DNS Domain Name – The DNS suffix the client should use, often the same as the domain name.
DHCP filtering
DHCP filtering can be used to deny or allow devices based on their MAC address. For example, I use it to block mobile devices from connecting to our secure wifi.
Superscopes
A superscope is a collection of individual DHCP scopes. This can be used when you want to join to scopes together. Honestly, I’ve never used this.
Split Scopes
This is a method of providing fault tolerance for a DHCP scope. Using DHCP failover is not the preferred method for fault tolerance.
DHCP Failover
DCHP failover was a new feature starting in server version 2012. It allows two DHCP servers to share lease information providing high availability for DCHP services. If one server becomes unavailable the other server takes over.
Resources:
Group Policy
Group policy allows you to centrally manage user and computer settings. You can use group policy to set password policies, auditing policies, lock screen, map drives, deploy software, one drive, office 365 settings and much more.
Group Policy Objects (GPO)
GPO’s are a collection of policy settings that you use to apply to computers or users.
Group Policy Refresh Frequency
Client workstations and member servers refresh their policies every 90 minutes. To avoid overwhelming the domain controllers their is a random offset interval added to every machine. This prevents all the machines from requesting group policy upgrades from the DC at the same time and potentially crashing it.
Policy Processing
Group policies apply in the following order
- Local
- Site
- Domain
- Organizational Unit (OU)
Block inheritance
By default, group policy objects are inherited. To change this behavior you can use the block inheritance option at an OU level.
No Override
If you want to enforce policies and prevent them from being blocked use the no override option.
User Settings
In a GPO there are user and computer settings. User settings only apply to user objects. If you configure user settings in the GPO, the GPO must be applied to user objects.
Computer Settings
The computer settings in a GPO are settings that can be applied to a computer. If you configure the computer settings the GPO must be applied to computer objects.
Resultant Set of Policy (RsoP)
Resultant Set of Policy is a Microsoft tool that is built into Windows 7 and later versions. It provides administrators a report on what group policy settings are getting applied to users and computers. It can also be used to simulate settings for planning purposes.
I have a complete tutorial in my article How to use RSoP to check and troubleshoot group policy settings.
Group Policy Preferences
Group Policy Preferences are primarily used to configure settings that can later be changed at the client level. Preferences also have the option to do some advanced targeting such as applying to a certain OU, Windows version, users in a group and so on. Preferences are commonly used to configure the following:
- Drive Mappings
- Registry settings
- Install printers
- Schedule tasks
- Set file and folder permissions
- Set power settings
Templates
You can install additional group policy templates to extend the default GPOs supplied by Microsoft. Some common templates used are Office 365, Chrome, Firefox and those supplied by 3rd party applications. Templates are xml based files usually in a ADM format or ADMX file extension.
Thanks a lot robert
Thanks for this post, it’s useful!
No problem.
how many roles and features in AD?
Nice, simple and clear explanation! One of the best for Ad!
I am really impressed with this Article. All basic details are covered.
Thank you.
Thanks Nanda
It’s really helpful, clearly explained in a simple and understandable way.
Very Helpful,kudos to you.
Thanks a lot! Robert, for providing us with such great knowledge you’ve covered much content with ultimate understandable terms and made the concept very clear.
Thank you sir, I really appreciate your efforts to provide such a great stuffs.
I have been working on both Windows and Macintosh OS X close to a decade or two.
I have received a process on Active Directory which was very much new to me.
This article shared has fulfilled my inquisitiveness and has helped me to know better about Active Directory and its features.
Kudos to the job done and hat’s off to the exemplary work done in defining each step better.
Thank you once again
Best explanation! Thank you so much.
Excellent Summary
One of the best article on AD
Thanks MJ
Fabulous Article ! Good job. How easy you have made it to understand AD
An excellent coverage of all basics pertaining to AD. Really admired your effort and thanks a lot for sharing. I wish to give more than 5stars, if alllowed.
Amazing Write Up! Haven’t ever found something that just summarized the high level AD concepts and terms like this. Thank You.
Thanks for the feedback!
Very easy to understand and covered most of the AD topics. Simple and superb.
Sathish, thanks for the feedback.
It was a very helpful article.
Awesome! Thanks for the feedback.
Simple and clearly explained…
Its a very nice article with all the required information for the beginners of Active Directory.
this article is best,
very helpful
regards
very good for beginner sir. thank you.
also suggest me for dns,dhcp which i refer.
this most informative for beginner. sir and thanks
Very informative for beginners. Thanks
You are welcome ❗
Excellent! Informative.
Thanks SS
its very helpful me.
A good one, with lot of information and handy.
Thanks Anthony
Best Active directory article by none. Thanks mate for sharing such valuable information.
A simple and clear explanation. ***** 5Stars from me….
Thanks for the feedback.
One of the best refrence available in internet . Almost all basic concepts are covered and explained in simple way. Thank you very much and kudos for the efforts
Hi Amith, thanks for the feedback!