In this guide, I’ll show you how to find inactive users in Active Directory with PowerShell. I’ll also show you how to find all unused accounts with the Active Directory Cleanup Tool.
It is important to review stale and inactive users to maintain security and eliminate any potential threats to your Active Directory environment.
In this article:
- How to Find Inactive Users in Active Directory
- Option 1. Find Inactive Users with PowerShell
- Option 2. Find Inactive Users with the AD Cleanup Tool
- Why You Should Review Inactive User Accounts
- Best Practices for dealing with Inactive Users
How to Find Inactive Users in Active Directory
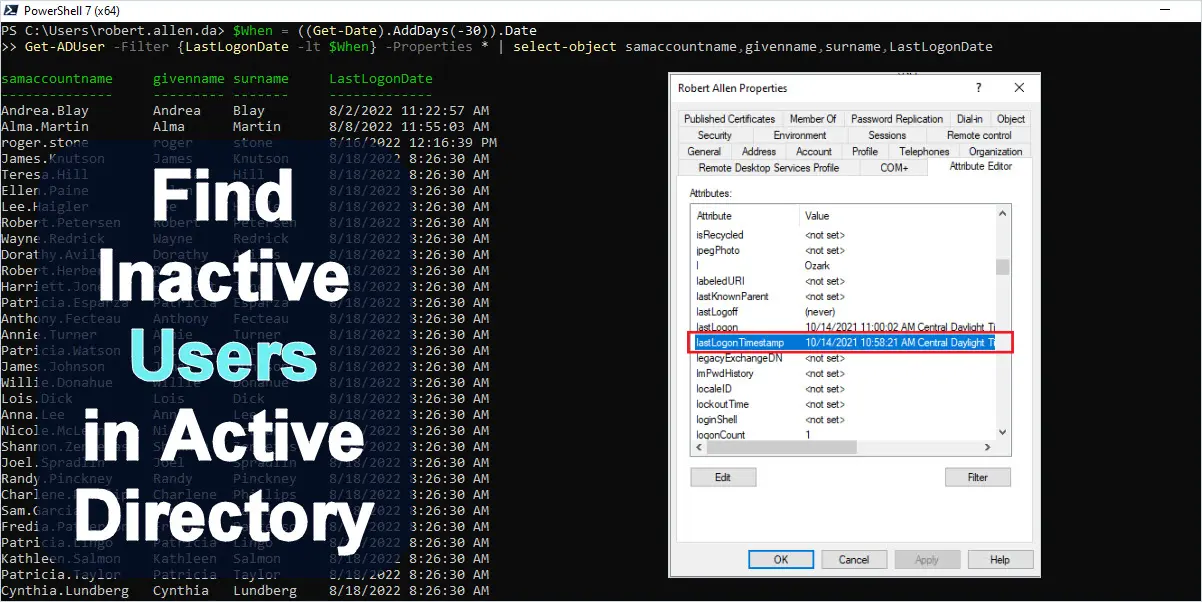
You can find inactive and stale users by reviewing a user’s lastLogonTimestmap attribute. This attribute is updated when a user logs on to their computer or the network. Typically, you want to find accounts where this attribute has not been updated in a certain period of time such as the last 90 days. This would mean the user has not logged on in 90 days.
To check if an Active Directory user is inactive follow the steps below.
- Click on “Properties” for a user account.
- Click on the “Attribute Editor”.
- View the lastLogonTimestamp value.
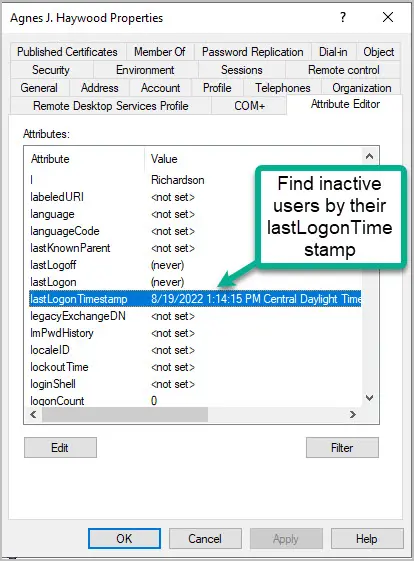
In the screenshot above, you can see the users lastLogonTimestamp has not been updated in a very long time. I would consider this a stale account because it has not been used in over a year.
In the examples below, I’ll show you how to use PowerShell and the AD Pro Toolkit to quickly find all users that have not logged on in at least 90 days. You can also choose a different timeframe such as the last 30, 60, 180 or whatever works for you.
Option 1. Find Inactive Users in AD with PowerShell
To find inactive accounts with PowerShell you will need the RSAT tools installed or run these commands on the domain controller.
All of these examples use the LastLogonDate property which is the converted value of the LastLogonTimestamp.
Find inactive accounts in the last 60 days
$When = ((Get-Date).AddDays(-60)).Date
Get-ADUser -Filter {LastLogonDate -lt $When} -Properties * | select-object samaccountname,givenname,surname,LastLogonDate
Find inactive accounts in the last 30 days
$When = ((Get-Date).AddDays(-30)).Date
Get-ADUser -Filter {LastLogonDate -lt $When} -Properties * | select-object samaccountname,givenname,surname,LastLogonDate
Here is an example from my domain.
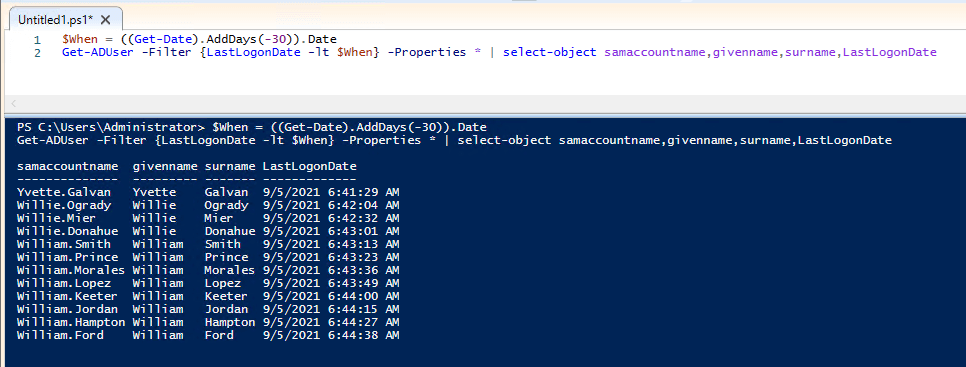
You can export the results to CSV by adding | export-csv -path c:\ps\inactiveusers.csv
$When = ((Get-Date).AddDays(-30)).Date
Get-ADUser -Filter {LastLogonDate -lt $When} -Properties * | select-object samaccountname,givenname,surname,LastLogonDate | export-csv -path c:\ps\inactiveusers.csvTo limit the scope to an organizational unit use the SearchBase parameter with the distinguished name of the OU.
$When = ((Get-Date).AddDays(-30)).Date
Get-ADUser -Filter {LastLogonDate -lt $When} -SearchBase "OU=Accounting,OU=ADPRO Users,DC=ad,DC=activedirectorypro,DC=com" -Properties * | select-object samaccountname,givenname,surname,LastLogonDateFind inactive users and disable the accounts
$When = ((Get-Date).AddDays(-30)).Date
Get-ADUser -Filter {LastLogonDate -lt $When} -Properties * | select-object samaccountname,givenname,surname,LastLogonDate | Disable-ADAccountIn the above example, I added | Disable-ADAccount at the end to disable all inactive accounts.
You can also use these commands to search computer accounts just change Get-ADUser to Get-ADComputer
As you can see It’s easy to identify inactive user accounts with PowerShell by filtering on the user’s LastLogonDate. If you are into PowerShell you can create a very powerful tool for cleaning up AD.
Option 2. Easily Find Inactive Users in Active Directory with the AD Cleanup Tool
The AD Cleanup Tool makes it very easy to find all inactive users in your network. You can then disable, delete, move and export the list of inactive accounts.
Step 1. Click on “AD Cleanup Tool” from the home page
Step 2. Select the inactive time range (default is last 90 days) and click “Run”.
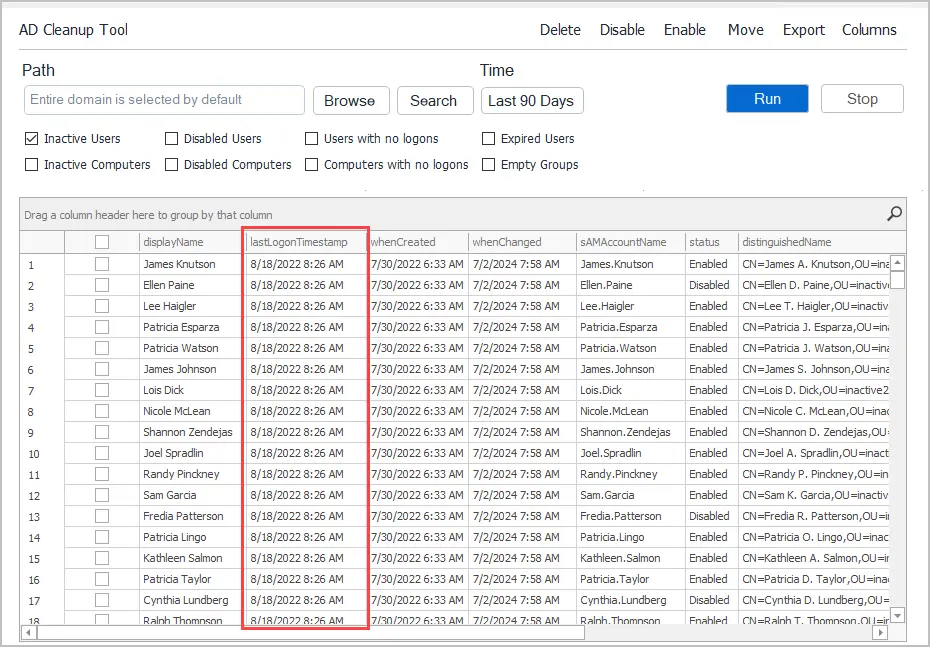
Step 3. Review the list of accounts and choose from the following actions. I recommend disabling accounts for x period of time. You can select all accounts or individual accounts.
- Delete
- Disable
- Move
- Export
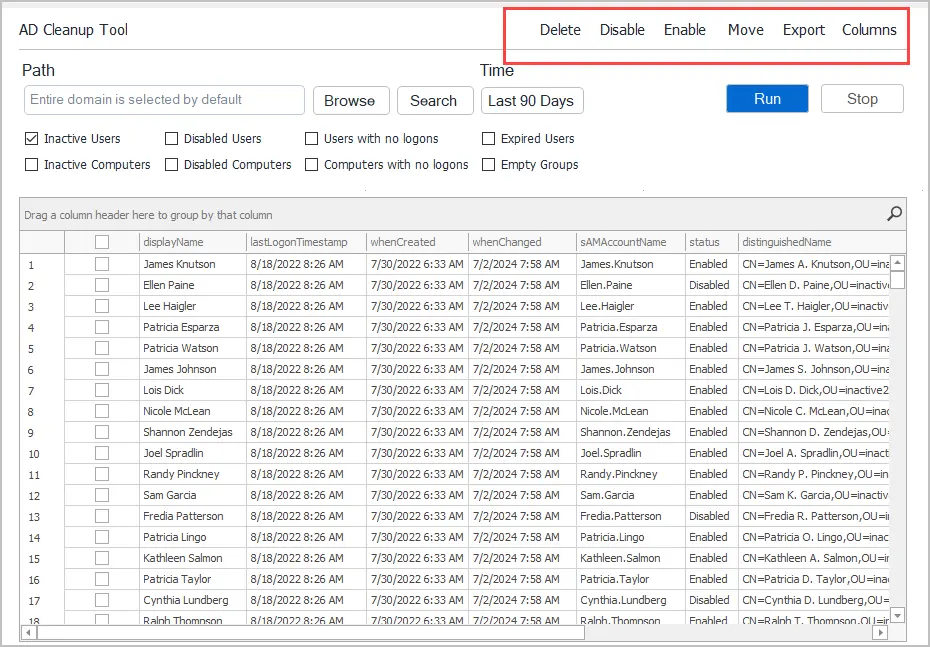
The AD Cleanup tool has several other filters to help you find inactive user accounts.
- Disabled Users
- Users with no Logons
- Expired Users
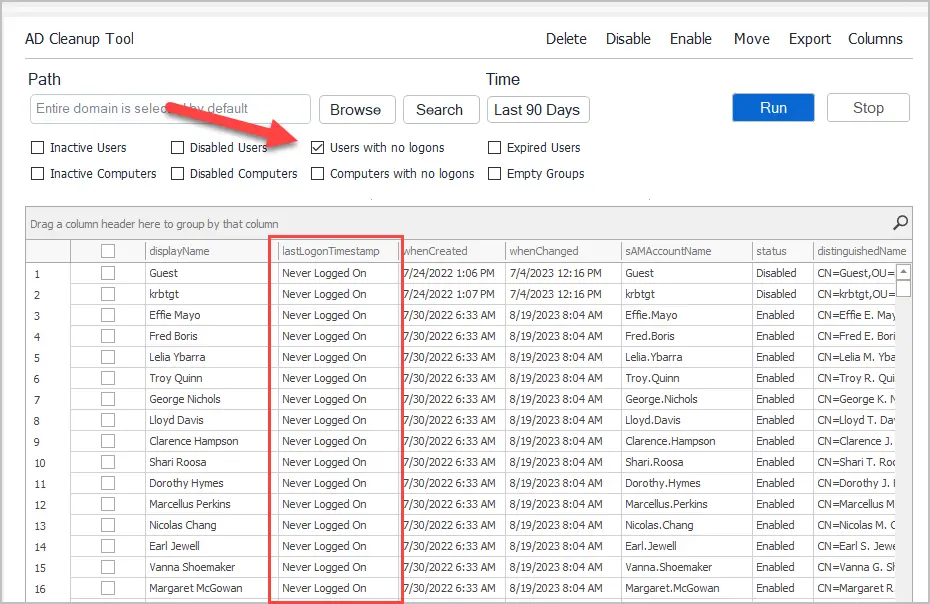
Find all Unused Accounts in Active Directory
To find unused accounts in Active Directory click on “Users with no logons”. These are accounts where the lastLogonTimestamp has never been updated.
Why You Should Review Inactive User Accounts
Security is the #1 reason for cleaning up inactive user accounts. Here is the complete list.
- Security Risks – CIS controls #5 says “There are many ways to covertly obtain access to user accounts, including weak passwords, accounts still valid after a user leaves the enterprise, dormant or lingering test accounts, shared accounts that have not been changed in months or years, service accounts embedded in applications for scripts” I highly recommend you download the CIS controls it is a great source to help defend and secure environments.
- Inventory & Tracking Issues – Active Directory is a centralized database. Not only can you use it to track your assets but it can be integrated with other systems for a complete asset management solution. If you don’t cleanup your AD assets, then your inventory system will inaccurate.
- Ease of management – Kinda along the same lines as#2. A cluttered AD environment leads to a difficult and stressful environment to manage. Think about running a PowerShell script or trying to deploy software to hundreds of computers or users. You will get a lot of returned errors when trying to manage an environment with stale and inactive accounts.
- Data Integrity – A lot of these have the same thing, data integrity. Again, AD is a centralized database and can be integrated with many systems. If the data in AD is incorrect then all systems connected to AD will be incorrect.
- Licensing – Here is a real world example. Your AD User accounts sync with a 3rd party system such as McAfee. Mcafee charges you based on user accounts. If you have hundreds of inactive accounts syncing with 3rd party products you could be paying for a lot of extra licenses you don’t need. This is the case when syncing AD with cloud products also.
Best Practices for dealing with Inactive User Accounts
Here are some best practices for cleaning up inactive user accounts.
- Never immediately remove accounts that are identified as inactive. Disabled them first for at least 30 days (longer the better).
- Search for accounts with a lastLogonTimestamp that is 45 days or older, meaning the AD account shows no logon activity for 45 days or longer.
- Disable the accounts for at least 30 days, I typically go with 60. With remote access, VPNs, laptops sometimes AD doesn’t get updated. By disabling an account first it’s very easy to re-enable it and give the user their access back.
- Add a description to the account with the date disabled and your initials. This is very helpful for other admins in case someone asks why an account is disabled.
- An inactive on-premise account might not mean an inactive Office 365 account. This would be for hybrid environments that sync with Office 365. The disabling of the account vs immediately deleting is critical for these types of environments. You could have users working from home who never authenticate to the on-prem AD environment but log into Office 365 daily.
- Run the cleanup process every month.
In this article, I showed you how to find inactive user accounts in Active Directory. I highly recommend you add this to your monthly maintenance checklist. If you have questions, please post them below in the comments.
Hi Robert,
Thank you for sharing these incredibly useful tips! Is it possible to use two -Filter checkpoints – one on LastLogonDate for 90 days inactivity, one on Title – with one Get-ADUser cmdlet?
Regards
Yes, you can have multiple filters using get-aduser
example.
Get-ADUser -Filter {(LastLogonDate -lt $When) -and (title -eq “HR Specialist”)} -Properties * | select-object samaccountname,givenname,surname,LastLogonDate
You mentioned “Add a description to the account with the date disabled”. Can a note like that be done in the script as well?
Path is incorrect for the csv commands.
Should be:
c:\ps\inactiveusers.csv
rather than:
c:\ps|inactiveusers.csv
Thanks for the tips! I appreciate your articles.
Thanks, Chuck. I’ve updated the path.