In this guide, I share my Windows Defender Firewall Best Practices and tips.
Most of these best practices are geared towards enterprise networks that use group policy or Intune.
These are the settings I’ve used in the real world. They took careful planning, lots of testing, and approval. No two networks or organizations are the same, so these settings may not work for you. I recommend you test and get approval before making changes to production systems.
List of Firewall Best Practices:
- Centrally Manage The Firewall with Group Policy
- Create a Baseline Firewall Policy
- Create Separate GPOs for Specific Rules
- Leave Default Inbound & Outbound Rules
- Enable All Firewall Profiles
- Disable Rule Merging
- Enable Logs
- Limit the Scope of Firewall Rules
- Enable the Firewall
- Firewall Rule Naming Convention
- Document Settings & Use GPO Comments
Do I Really Need the Windows Firewall?
The Windows firewall can help protect your computer from unwanted traffic. It is considered an Active Directory security best practice by Microsoft and other security professionals. Disabling and leaving the firewall off can make your computer more vulnerable to viruses, ransomware, and other malicious attacks. Even if you have a network-based firewall on the perimeter of your network it is still recommended to have a host-based firewall enabled. The more layers of security you have the better you will be protected.
Many security organizations such as the Center for Internet Security recommend enabling the Windows firewall. Here is a screenshot from the CIS Security Controls regarding firewalls.
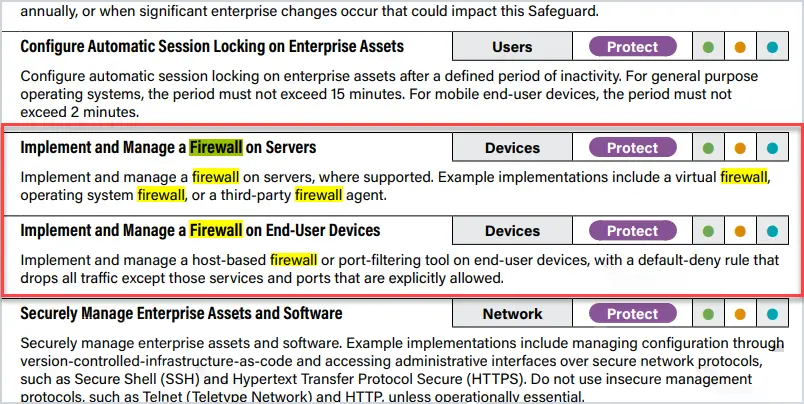
How Do I Check my Firewall Status?
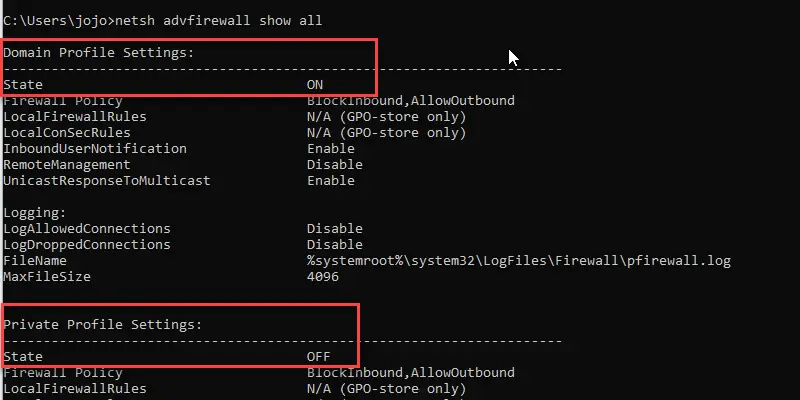
There are a few ways to check if the Windows Firewall is on.
The below command will show the firewall status for all three profiles:
netsh advfirewall show all
Another way to check the firewall status is to click the windows start button and type firewall then select “check firewall status”
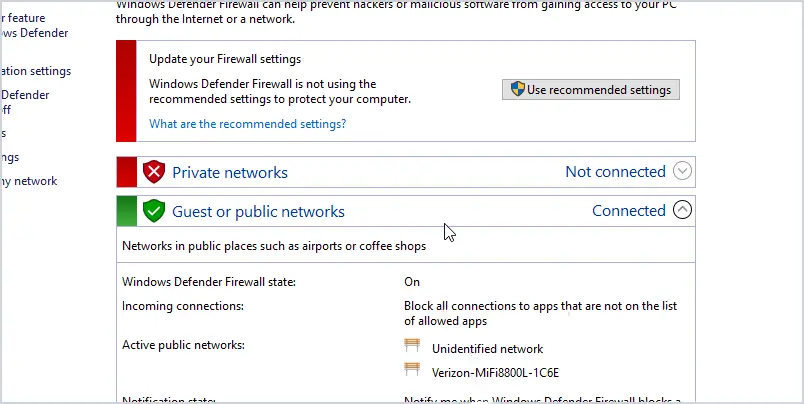
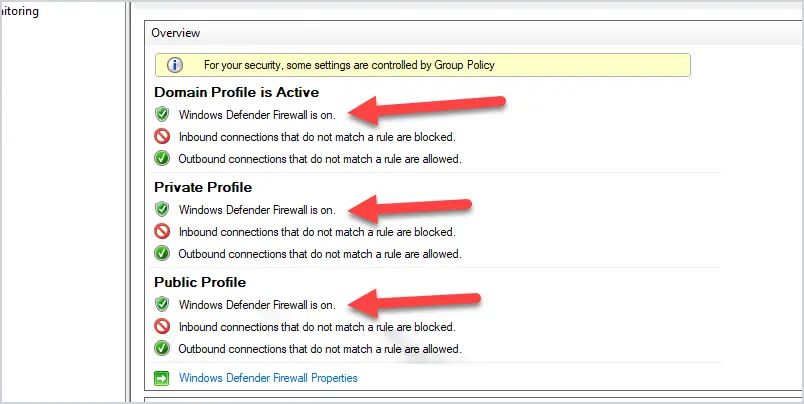
In the picture above you can see the firewall is on for the public network but not for the private networks.
1. Centrally Manage the Firewall with Group Policy
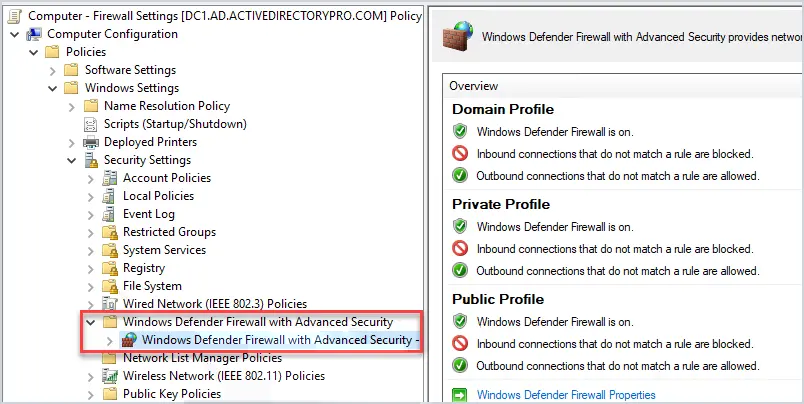
If you have an Active Directory environment or Azure with domain joined computers you should centrally manage the firewall settings. You do not want users to have the ability to manage rules or worse, disable the Firewall. I see too often the firewall popup and say something was blocked, then users just click to add the rule. This could be a disaster and weaken your endpoint security.
Centrally managing the Firewall helps to ensure you have consistent Firewall rules across all systems.
2. Create a Baseline Firewall Policy
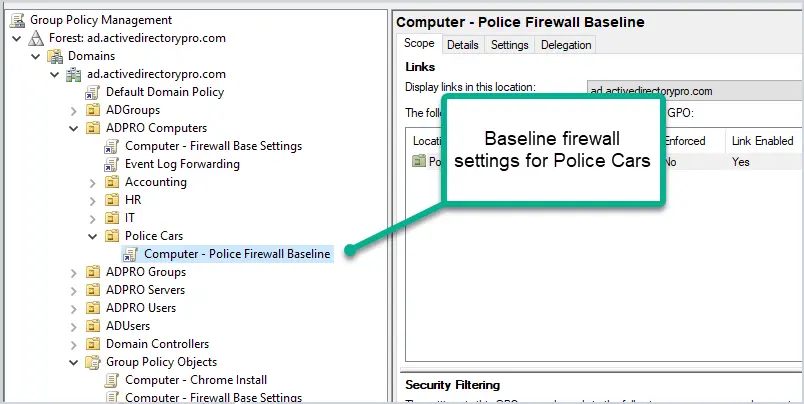
I like to create a baseline firewall policy that can be applied to all computers or a large set of computers. This would include common programs that most computers would have installed. These would be things like Microsoft Teams, Outlook, Java, Office apps, Adobe, and so on.
I create a separate baseline policy for servers and other special use computers that would require more strict rules. For example, mobile computers in police cars would get a separate baseline policy.
When creating the baseline, I only allow what is needed. Again, I’m looking for just the common programs that are used by most users. Specific things like FTP, or allowing SMTP will go into a separate GPO which I’ll go over in tip #4.
3. Create Seperate GPOs for Specific Rules
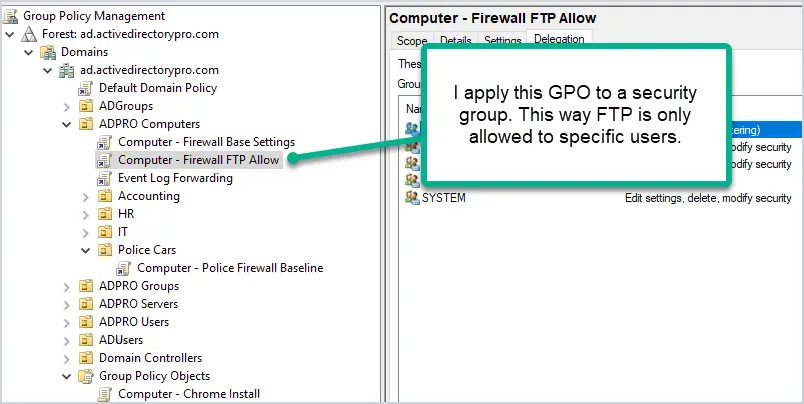
Let’s say you rolled out a baseline firewall GPO and then someone needs FTP unblocked, what do you do? Do you add it to the baseline? NO WAY. This would unblock FTP for a large group of users and weaken your security.
What I do, and also has worked out great, is create a new GPO that unblocks FTP (or whatever is needed) and only apply it to a security group. This works great for two reasons. First, it only unblocks FTP for a small group of users and keeps it blocked for all other users. Second, by using a security group you can easily see which users or computers have specific rules open.
How do you apply a GPO to a security group?
Use the Delegation tab on the GPO to change the permissions and only allow it for a group. You will need to change Authenticated Users to Deny for Apply group policy. Then add your new group and give it Read and Apply group policy allow permissions. Be sure to test this before rolling it out.
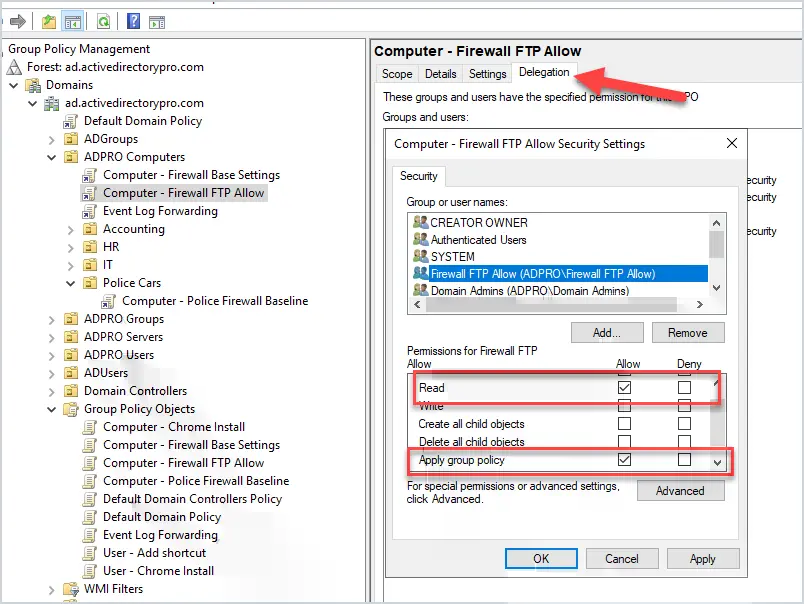
This helps to minimize GPOs needed and to allow the firewall to be 100% managed by GPO.
4. Leave Default Inbound & Outbound Rules
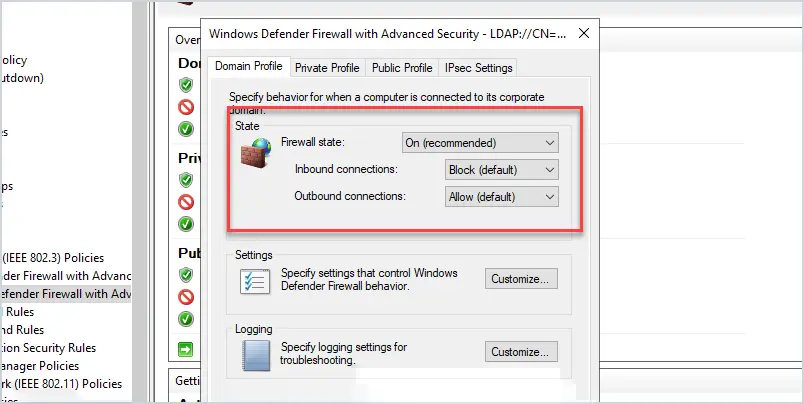
Microsoft says “These settings have been designed to secure your device for use in most network scenarios”.
I agree as this blocks unwanted inbound connections by default. What I mean by unwanted, is connections that your computer did not initiate. For example, if someone tried to admin share (c$) or RDP to your computer it would be blocked. This will also block lateral movement from hacking tools and viruses. Huge Win!
This still allows your computer to make outbound connections that your computer initiates. For example, when you open chrome or firefox this would be allowed with these default rules. These default rules make it easy to implement a secure configuration with less disruption to the users.
If you have strict requirements and need to control all inbound and outbound traffic then don’t use the defaults allow outbound rule. For example, if you just want to allow port 443 outbound to a specific address then do not use these defaults.
It’s possible you could end up with a mix of GPOs that use the defaults and others that do not. Maybe your baseline is default but then have specific computers that block everything by default. Every organization is different and there is no one size fits all for firewall rules.
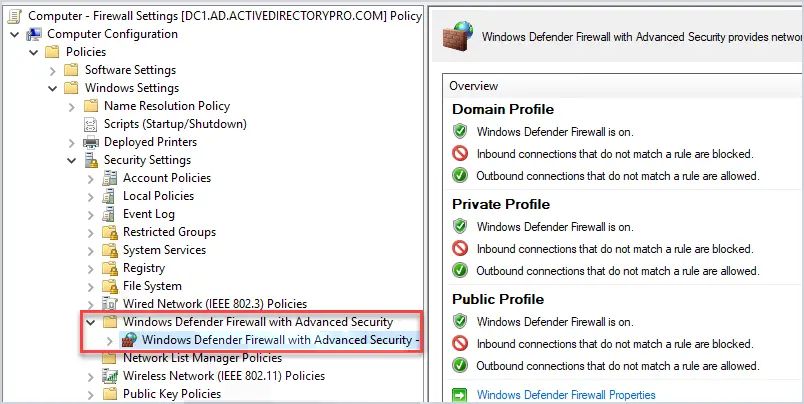
5. Enable All Firewall Profiles
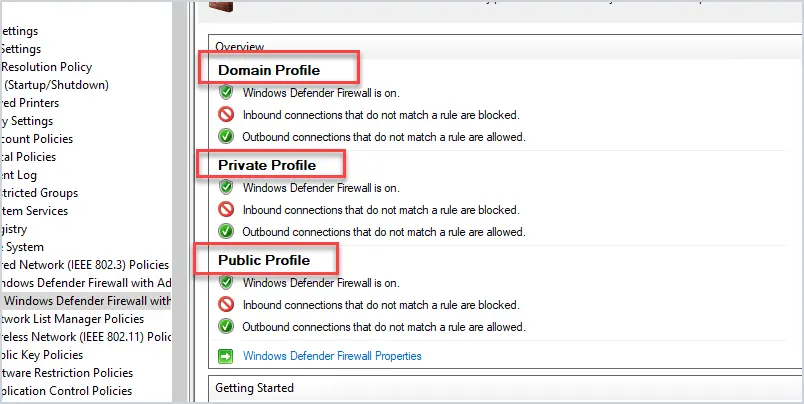
The Windows Firewall has three profiles, domain, private and public.
Domain profile: This profile applies to networks where the computer can authenticate to a domain controller.
Private profile: This profile is a user assigned profile and is used for private and home networks.
Public profile: This is used when connected to public networks such as public wifi.
The best practice is to enable all three profiles. When creating new firewall rules you can then set the rule to the group that best applies (sometimes it will be all three).
For example, if you are creating a rule to allow access to an internal FTP server then there is no need to apply this to the public profile. If you don’t apply very strict rules and applied this to the public profile then you just opened inbound FTP connections from the internet (when connected to a public network).
6. Disable Rule Merging
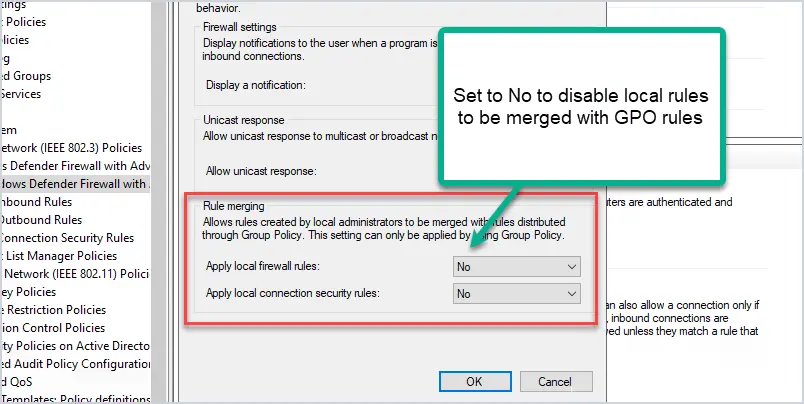
Disable rule merging means local firewall rules are ignored. The endpoint Firewall settings will be 100% managed by group policy. This is my preference.
If it’s not 100% centrally managed then how can you maintain a security posture? I don’t want apps or users to create their own Firewall rules, that is just going to shoot holes in the firewall.
If you added firewall rules locally on the computer and set this to “No” the local rules will no longer apply.
7. Log Settings
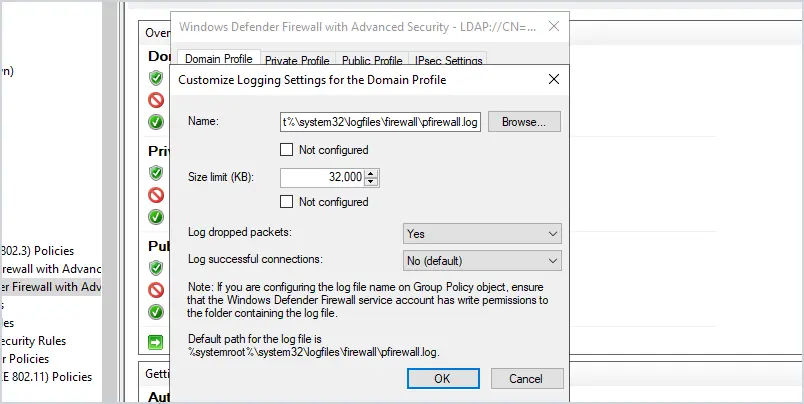
I recommend enabling logging of dropped packets and increasing the size of the log file. There will be times when the firewall is blocking a legit program and you or someone else will need to troubleshoot it. Logging the blocked connections makes it super easy to identify when the firewall is causing a connection issue.
Firewall No Log File Issue
A lot of times the default log file location is missing the permissions to write the log file. I guess this is a Microsoft bug because it happens a lot. To fix this the computer will need to have the mpssvc service account have write permissions to the c:\windows\system32\logfiles directory.
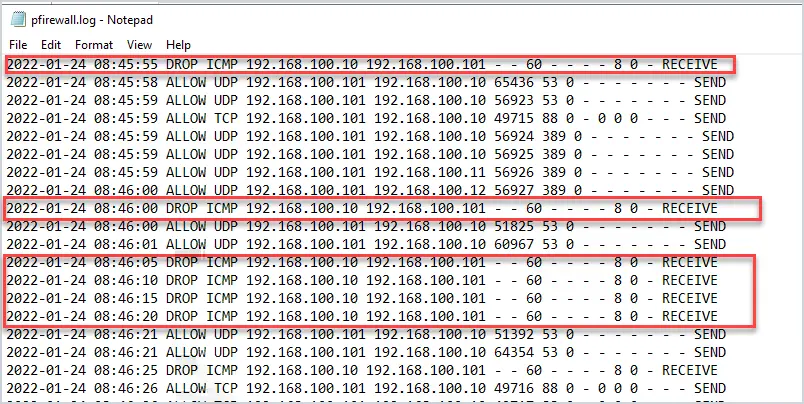
Here is an example of the log file.
8. Limit the Scope of Firewall Rules
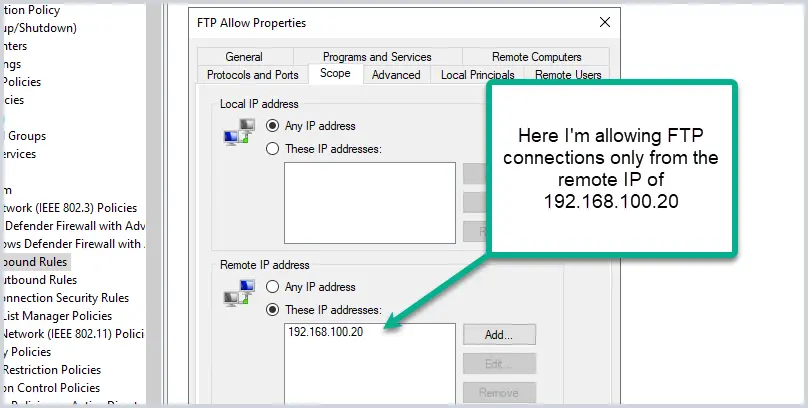
When unblocking a program or service, limit access to remote IP addresses, or authorized computers. For example, if you allow Jim’s computer to allow FTP connections, don’t just allow FTP from any IP address. You can limit the scope, for example, I will just allow Jim’s computer to accept FTP connections from 192.168.100.20.
The golden rule with firewalls is to only allow what is needed. Allowing Jim’s computer to accept FTP connections from any remote address is a security risk. There are multiple ways to do this. I would also recommend locking the rule down to an application, the port number, and the remote address.
This may not always be possible but when you can, lock it down as much as possible.
9. Enable the Firewall
I’m shocked at how many organizations still disable the Windows Firewall or have it poorly configured.
The Windows Firewall provides many security benefits including:
- Control inbound and outbound connections
- Block viruses and ransomware from spreading on your network
- Block users from sharing folders and printers on their computers
- Reduce network threats
- Encrypt network communication on your network
- Slow down attackers from moving latterly on your network
- Block insecure ports by default
Most security organizations such as sans CIS and CISA recommend using a host based firewall to mitigate malicious network activity.
When first released, the Windows Firewall with XP was so bad everyone disabled it. It had limited features and was difficult to configure. Due to all the complaints, Microsoft made major improvements, and it’s been a good enterprise firewall ever since.
Unfortunately, it’s still widely disabled. This is a huge mistake.
Most organizations have a network based firewall and think they don’t need the Windows firewall. This is false and bad practice. Security is all about layers, the more layers you have the better you will be protected. You need a Network firewall at the parameter of your network and the firewall enabled on all endpoints.
10. Firewall Rule Naming Convention
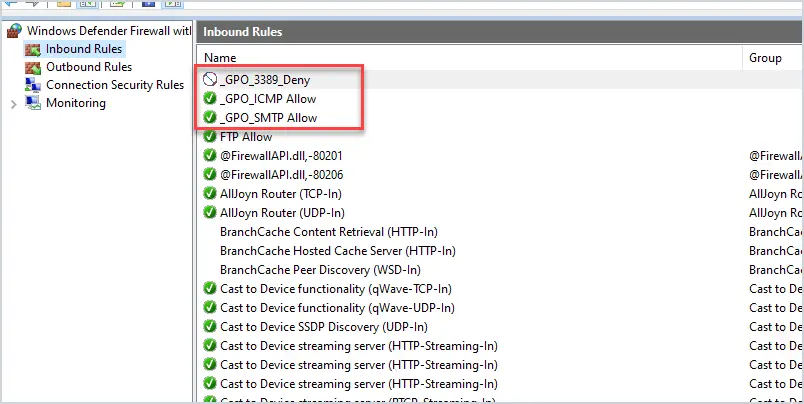
The endpoints will most likely have all the default rules in place unless you applied a policy to clear them. The local firewall rules will not be working but will still show up. This can be confusing and make it difficult to find rules you push out with group policy.
I like to start the GPO rule name with an underscore or a three letter appreciation. This makes it easy to find my GPO Firewall rules on the local endpoint.
For example, in the picture above I started them with _GPO_, now when I open the local firewall all of my GPO rules are at the top and easy to find.
Again when you disable rule merge (tip#7) all of the local firewall rules will not be applied. It’s not as big of an issue as you think when using tip#5.
11. Document Settings & Use GPO Comments
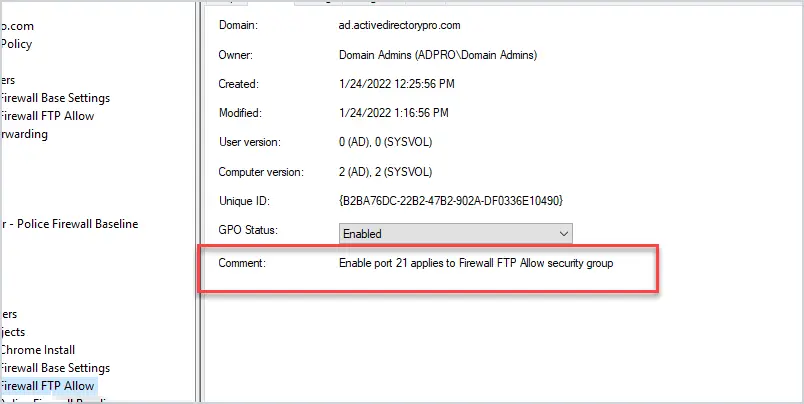
Document the firewall GPO settings and share them with your staff. The firewall is often blamed for everything so it helps when your staff knows what the GPO rules are doing. Even when they do know they will still often blame the firewall. When this happens this is when you show them the firewall logs and prove the firewall is not blocking anything.
The comment section in the GPO is helpful and provides administrators with a quick way to know what the GPO is used for.
You can access the comment by right clicking the GPO > properties then click on the comment tab.
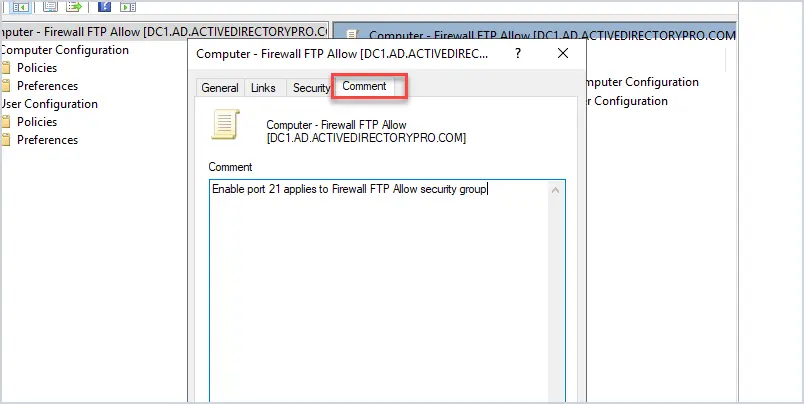
Now click the comment tab.
Summary
Host based firewalls are essential to an organization’s security strategy. To have good security you must have many layers of defense and the Windows Firewall adds another layer. Plus it’s free.
One huge benefit that is not often talked about is how host based firewalls can block lateral movement in your network. This is a common tactic hackers and viruses use to compromise systems and the entire network. Implementing these best practices will block this lateral movement and many other unwanted connections.
If you currently disable the firewall or do not centrally manage it then I recommend you start looking into changing that.
Sources
- Best practices for configuring Windows Defender Firewall
- Basic Firewall Policy Design Example
- Implemented these rules in small to large production networks
Hi Robert,
So I know that you cannot play for all the scenarios for every company but I would like your advise on one issue I am finding.
I have followed your article above and when I deploy the Firewall GPO, I noticed that I cannot run GPupdate /force. I am looking for the solution to allow the GPupdate /force command. When I run it is cannot find the computer name in DNS. As soon as I remove the firewall policy, it works again.
Thoughts?
Todd
Your FW policy might be blocking 135/RPC and 445/SMB from the client to the DCs (or some other port). If you enabled the logging of dropped packets it should show you exactly what the firewall is blocking.
Hi there,
what about the windows default firewall settings and disable rule merging. Are they still active or do i have to set them all in the gpo?
For example: Core Networking, File and Printer Sharing etc.
greetings
Mark
Both questions are addressed in the article.