In this article, you will learn how to configure the Active Directory Domain password policy.
The domain password policy is critical to ensure security and compliance in your organization.
You will also learn:
What is The Default Domain Password Policy?
By default, Active Directory is configured with a default domain password policy. This policy defines the password requirements for Active Directory user accounts such as password length, age, and so on.
This password policy is configured by group policy and linked to the root of the domain. To view the password policy follow these steps:
1. Open the group policy management console
2. Expand Domains, your domain, then group policy objects
3. Right click the default domain policy and click edit
4. Now navigate to Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy
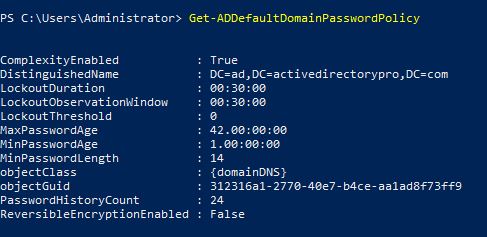
You can also view the default password policy with Powershell using this command.
Get-ADDefaultDomainPasswordPolicy
Important: The default password policy is applied to all computers in the domain. If you want to apply different password policies to a group of users then it is best practice to use fine grained password policy. Do not create a new GPO and link it to an OU, this is not recommended.
You can also get the password policy using the AD Pro Toolkit’s built list of security reports. You can also report on the fine grained password policies and Domain Admins using old passwords.
You can try these reports out for free in your domain. Download a free trial of the AD Pro Toolkit or check out the full list of included Active Directory Reports.
Understand Password Policy Settings
Now that you know how to view the domain default password policy let’s look at the settings.
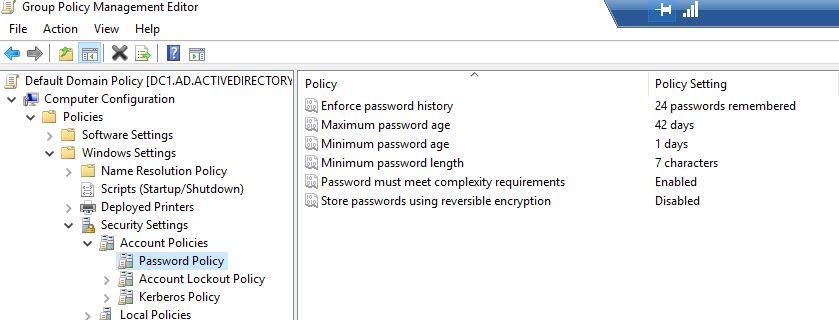
Enforce password history:
This setting defines how many unique passwords must be used before an old password can be reused. For example, if my current password is “Th334goore0!” then I can’t reuse that password until I’ve changed my password 24 times (or whatever number the policy is set to). This setting is useful so users don’t keep reusing the same password. The default setting is 24
Maximum password age:
This setting defines how long in days a password can be used before it needs to be changed. The default setting is 42 days
Minimum password age
This setting determines how long a password must be used before it can be changed. The default setting is 1 day
Minimum password length
This setting determines how many characters a password must have. The default is 7. This means my password must contain at least 7 characters.
Password must meet complexity requirements
If enabled passwords must meet these requirements:
- Not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters
- Be at least six characters in length
- Contain characters from three of the following four categories:
- English uppercase characters (A through Z)
- English lowercase characters (a through z)
- Base 10 digits (0 through 9)
- Non-alphabetic characters (for example, !, $, #, %)
This is enabled by default
Store passwords using reversible encryption
This setting determines if the operating system stores passwords using reversible encryption. This is essentially the same as storing plain text versions of passwords. This policy should NEVER be set to enabled unless you have some very specific application requirements.
Password Policy Best Practices
To improve Active Directory security its recommended to follow password policy best practices. It is also very important that you have an account lockout policy configured to lockout users after so many failed logon attempts. Below I list the password policy best practices from the Microsoft and CIS security benchmarks. Also, your organization’s password policy may be driven by compliance/regulation requirements such as PCI/SOX/CJIS and so on.
Microsofts recommended password settings
These settings are from Microsoft’s Security Compiance Toolkit. This toolkit provides recommended GPO settings from Microsoft.
- Enforce Password History: 24
- Maximum password age: not set
- Minimum password age: not set
- Minimum password length: 14
- Password must meet complexity: Enabled
- Store passwords using reversible encryption: Disabled
NOTE: Microsoft has dropped the password expiration policies starting with the 1903 security baseline. You can read more on this here
I think this is a good decision but some organizations will still need to follow specific guides (like PCI, SOX, CJIS). Hopefully, those will get updated soon.
CIS Benchmark password settings
These settings are from the CIS Benchmarks. The center for internet security is a non for profit organization that develops security guidelines and benchmarks.
- Enforce Password History: 24
- Maximum password age: 60 or fewer days
- Minimum password age: 1 or more
- Minimum password length: 14
- Password must meet complexity: Enabled
- Store passwords using reversible encryption: Disabled
Related:
Modify Default Domain Password Policy
To modify the password policy you will need to modify the default domain policy.
1. Open the group policy management console
2. Expand Domains, your domain, then group policy objects

3. Right click the default domain policy and click edit
4. Now navigate to Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy

5. Now double click one of the settings to edit. For example, I’ll double chick on minimum password length.
I’m going to change this setting from 7 to 14 characters and then click apply.
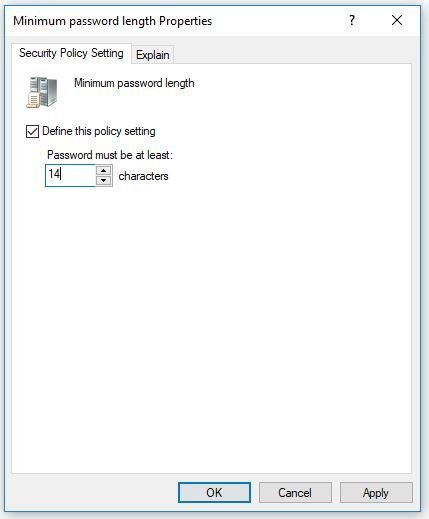
Double click any other password policy setting to change.
I hope you enjoyed this article.
Do you have any questions? Let me know in the comments below.
Frequently Asked Questions
Can I create multiple password policies?
No. You would need to use fine grained password policies to create multiple password policies.
Each domain can only have one password policy and it must be linked to the root of the domain. The default domain policy by default includes a password policy. If you wish to define a new policy it should be linked to the root of the domain.
Can I create a password policy and link it to an OU?
No.
Group policy password policies must be linked to the root of the domain. There can only be one GPO with the password policy and it must be linked to the root of the domain.
When I change a password policy setting will it immediately impact the users?
No. Password policy changes will go into effect when the user’s password expires. For example, if “Password must meet complexity requirements” is disabled and you enable it, the user will not be required to change their password until it expires.
How to override the default domain password policy?
If you need to create a separate password policy for specific accounts, groups, or an OU you should use a fine grained password policy to override the default policy.
We changed our password policy to expire from 90 days to 180 days but users are still expiring after 90 days instead of 180. Why?
The policy change from 90 days to 180 days is not immediate. The policy will go into effect the next time the user changes their password. This can be done by manually changing the user password or letting the current password policy expire.
You can use our Active Directory Reporting Tool to generate a list of all users and their password expiration date.
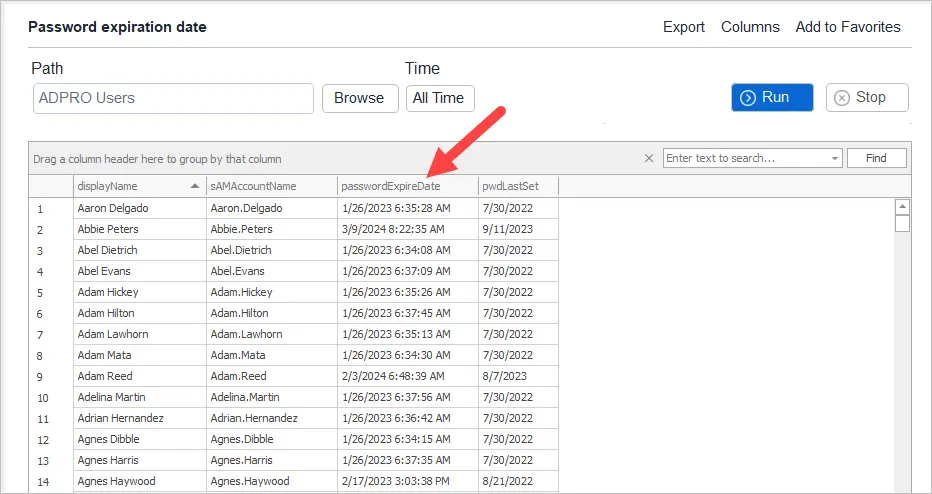
If you liked this post, you might also want to check out:

Question. We are looking to change our Password Policy from 8 characters to 12. Once we apply this setting, will all users be prompted to change their password right away or will they just need to change it when they hit their 90 deration?
Regarding to the last question of the Q&A: “The policy will go into effect the next time the user changes their password. This can be done by manually changing the user password or letting the current password policy expire.”
Hi, may i know why i have set the minimum password length to 12 digits but user can still set the password in 7 digits? is it because the complexity requirements overrides it? there is one line in complexity requirements stated that – Be at least six characters in length. i have run gpupdate /force for the user and make sure the policy applied, Thanks!
Run this command.
Get-ADDefaultDomainPasswordPolicy
What does it say for MinPasswordLength?
Do you have multiple password policies? What about fine grained password policy?
Hi,
the policy is enforced at computer level, so it’s not possible to set up delegation in a way that exclude a user from this GPO. You can only prevent its application by excluding the computer from delegation using deny settings.
Now, I have a non-domain computer that accesses internal network drives after connecting via VPN. When the user password is changed from another pc in the domain, the network drive in the other pc continues to use the saved password, causing the user account to lock.
In the domain server’s event viewer, I see that the lockout originates from the non-domain computer, which I cannot deny in delegation because it’s not part of the domain.
How can this problem be resolved?
Thanks for any hint!
You would need to use FGPP to apply a separate password policy to the domain user account. The domain password policy is applied to the Active Directory database so it applies to all domain user accounts not computers. You can modify the non-domain computer local policy but if you are using a domain user account it will have no effect.
hI Robert,
As I ‘m preparing to implement password policy, I go to each user properties to disable password never expires and users cannot change password. All of a sudden all users are prompted to change password. My default domain policy is not linked and using the default settings. I try looking at other polices whether any password policy being set by my predecessor but to no avail.
Any idea how to check the password policy is using which gpo?
From my understanding password settings can only come from a GPO that is linked to the root of the domain. Do you have any other GPOs linked at the root?
Yes, i have 3 other Gpo they are linked 2 the root, same level as default domain policy but these 3 gpos are configured to do other things.
If i deleted some of the old Gpo from GPO objects, does the settings still applies to the users or computer?
Hi Robert,
I’ve tried to change the password policy setting in the default domain policy, but when I ran the command net accounts and net accounts /domain on the client machine, the result displayed not the same immediately even though I use gpupdate /force
When I tried to test the command net accounts and net accounts /domain the next day, the result displayed the same.
What should I do in this situation when I need the result of the 2 commands to be the same as when I’ve made the change?
Instead of using fine grained password policy, can I add domain admin group into default domain policy and deny its use under delegation tab and advance button?
I just want the domain admin accounts to be excluded.
Thankyou
That is not recommended and could cause issues. The recommended method is to use fine grained password policy.
Hi Robert,
When I enable the password policy in default domain policy, how to ensure it doesn’t apply to domain administrator or any service accounts on the servers?
Just wanted to make sure the password policy applies to users only. Thankyou
It will apply to all accounts. You will need to create a fine grained password policy to set a different policy for specific accounts.
i don’t wish to apply a different password policy for admin and service accounts. Quick method can we enable password does not expires in these accounts?
Yes, on the account tab you can select “password never expires”.
Amazing Article!
I’m planning on introducing a password in an organization as of a future date.
What’s the best way to go about this, Currently everyone ticked for “Password Never Expires” is it just a case of set up the requirements needed and untick that box on the day?
Users will be forced to change their password passed on the policy configured and when the user last changed their password. Even if you uncheck “Password Never Expires” it will not immediately force a password change.
We changed our policy from 90 days to 365 and, expected that those passwords set prior to the date we changed the policy would be required to be changed after 90 days. That does not seem to be happening.
Any ideas. We changed on 8/1
The policy change is not immediate. It will go into affect the next time the user changes their password.
Hi,
i would like to understand how the order works if i have default domain password policy. and i have also applied the Password Settings Container, added a policy there.
which will take effect?
do i need to disable the policy in the GPO and create a default one under the Active Directory Administrative Center?
thanks
Great Article BTW.
I have my default domain policy , Password policy set and it does work, however when i run this command Get-ADObject (Get-ADDomain).distinguishedname -prop * | select *pwd* or this one Get-ADDefaultDomainPasswordPolicy they don’t totally match. the one line that doesn’t match the default domain policy is MinPwdLength it shows 6 but within my gpo it is set as 8 any clue on why those wouldn’t match up? i noticed they do not match up within your screenshot above as well, you have yours set for 7 in the GPO but the PS SS shows 14.
Is this just a MS thing, as when a user has to change their password, it has to be at least 8 characters, so it’s working it just doesn’t match between the GPO and powershell command.
Thank You
If they do not match it means you have another GPO that is applying password policy settings. Check for other GPOs that are linked to the root of the domain and review them.
I think my screenshot doesn’t match because I was changing settings and didn’t wait long enough. I just checked it again and the command output matches the GPO settings.
Robert,
Thank you, I currently only have 4 policies at the root level.
one that denies our contracts the log on locally
the default domain policy which does not have anything configured for password policies.
one that is just for adding a disclaimer when users go to login to a machine one that is just for setting the password policy.
I have just literally triple checked these and ran group policy results wizard and the only policy that is doing anything with passwords is the one that is just for setting the password policy.
Would you know where it looks for the password length value? that may help me track it down if so as i’m not finding any other policies applying password requirements.
Thank you again
From my research, Active Directory will only apply password policies from GPOs that are linked to the root of the domain. So it would seem there are multiple GPOs linked at the root of the domain that have password policy settings applied. If multiple GPOS linked at the root have a password policy setting, the one with the highest linked order will take precedence.
Also, make sure the domain controllers OU does not have blocked inheritance enabled. This would block the GPO from applying to the DC with the PDC emulator role.
Hi Robert,
great article. I’m trying to update my organisations password policy, but the changes are not taking effect. When I run Get-ADDefaultDomainPasswordPolicy the result doesn’t match what is set in the Default Domain Policy. Further complicating the issue, my predecessor has moved the Default Domain Policy from the root of the domain to a sub OU. This GPO is not applied to the DCs.
There is a Default Domain Controllers Policy GPO, but changing the settings here also has no effect.
I’ve also tried creating a new GPO linked to the root of the domain, but, again, not change to the result from Get-ADDefaultDomainPasswordPolicy.
Where/what in the domain do these settings need to be applied?
Thanks
Steve
The Default Domain Policy should be linked to the root of your domain. Use this GPO for account lockout and your password policy. Do not create multiple GPOs with a password policy as MS will only apply one PW policy.
Hi Robert,
thanks for your speedy reply. I’m ensuring that the policy settings are only defined in 1 GPO at any one time, however I still can’t get my policy to take effect.
I’ve created a new GPO solely for account lockout and password policy, linked it to the root of the domain, but still I’m not getting the result I expect from Get-ADDefaultDomainPasswordPolicy.
RSOP on the DCs shows the lockout and password policies as Not Defined.
Is there anywhere else these settings can be defined? There are no fine grained password policies configured as well.
Thanks
Steve
You can only have one account policy in the domain and it should be linked to the root of the domain. You need to make sure no other GPO has account policies defined.
Also, the command Get-ADDefaultDomainPasswordPolicy might only be checking the default domain policy GPO. Since you have the password policy in another domain I’m not sure if that command will work correctly.
Thanks Robert.
I’ve been through and this is the only GPO with these policies defined.
However, I have also look at the Local Computer Policy for the PDC, and that seems to be where the account policy is being defined. There doesn’t seem to be a way to set these policy settings to Not Defined. Is there an obvious way to override the Local Computer Policy on the PDC with a GPO?
Thanks
Steve
The password policy applies from the policy linked to the root of the domain and having Link Order 1.
By default this is Default Domain Policy, however it can be changed.
Hi, if I set “Maximum password age” there is a method to manage number of days and number of advises send to users before their PW expiration?
thanks
Do you want to send a notification to users before the password expires? There are a few options.
1. There is a GPO setting that will prompt users it is called “Interactive logon: Prompt user to change password before expiration”
2. Use 3rd party software to email users
3. Create a PowerShell script and email users.
Hi – Is there anyway to stop admins changing their password directly in the AD console instead of pressing CTRL, ALT, Del? As if they change it directly in AD it bypasses the password policy
Not that I know of. Changing it in the AD console will still require the password to meet the password policy requirements.
If I change the password policy and I want to enforce it immediately (not wait for the expiration date), how do I enforce it for those users who do not already comply with the requirements?
You would need to enable “user must change password at next logon” for those users.
Hai Robert Allen,
How to get users group names using logon name and password with power shell script.
See this article Export Active Directory Group Members-directory-group-members/
If in our current policy we do not have passwords set to expire then when would changes take effect on, for example password length change?
Also, if change from min length 6 to 12 if a user’s password is already 12 or more then they would not be affected?
I believe the password expiration depends on when the password was last set (pwdLastSet) so it will be different for each user.
If a user already meets the min length they would not be affected.
Hi Robert, and if the user does not meet the “new password policy length” prior to enabling the new policy? will that user be affected right away? will it prompt the user to change his password as soon as the policy is enabled for his account?
If yes, is there a way to avoid that?
Changes to a password policy go into affect the next time the user changes their password.
1. When the user’s password expires and is forced to change it.
2. The user account is set to change the password at the next logon.
3. User requests to change their password.
Hey Robert,
Thank for covering most common but critical topic here.
We have a requirement to enforce minimum 2 special characters (Non-alphabetic characters (for example, !, $, #, %)). Just wanted to check if that is possible. If yes, how ?
Hello. AD server is connected to other computers. After around 42 days, it is required for other computers to log-in AD server with same password(not changed required.)
Could you advise me which of setting I should check?
Now I changed password policy maximum password age 42 days to 0 day. Hopefully it will work..
If the max password age was 42 and the user logs in with the same password it would prompt to change the password. Are you saying they did not get prompted to change password?
Thanks its works for me
How does affect the setting “min password length” the complexity requirements?
For example:
I have enabled the complexity rules in the AD, who has min pw length of 8 digits. An I set the min pw lenght to 6 digits. Which setting overrides the other?
Great article!
If you update the password max age from 90 days to 365 days, does that proactively change the password expiration timestamp on everyone’s user accounts, or do they still expire on on their current scheduled expiration time stamp?
For example, if my account’s password is set to expire on 12/24/2020, and I update the domain password max age policy from 90 to 365 days on 12/5/2020, my password will still expire on 12/24/2020 as currently scheduled, correct?
Matt. Yes, that is correct.
I have set user account to ‘password never expires’ (flag the checkbox) but after some time, the user account having issue to login and found out that the user account is expired. When I check in Active Directory, the checkbox unflagged. Is there any setting that cause such scenario?
Sounds like a replication issue. Do you have multiple DCs?
I set the password expiry date to 90 days, if the computer not connecting to local network (can’t find Active Directory) longer than 90 days, what would happen on the computer please?
Hello, I need to improve that password with two consecutive equal characters are not allowed. There is a way to implement this kind of policy?
You can create a password filter. Here is a link to Microsofts documentation on this
https://docs.microsoft.com/en-us/windows/win32/secmgmt/installing-and-registering-a-password-filter-dll
If you utilize Azure Active Directory (and sync your AD passwords) you can make use of the banned passwords functionality.
I wish MS would provide this for Active Directory without requiring azure p1 licenses.
For example, I used September01 as a new password and it’s not accepting. Then I used September01# and that’s also not accepted. I used other passwords that meets this requirement and none of them are accepted.
What are your password policy settings?
You can check it with this ps command
Get-ADDefaultDomainPasswordPolicy
I changed a user password in AD, for a short period of time (probably about 10 mins) the old password would still work.
Any idea what setting might cause that?
Was the computer on the network with access to the domain controller? It’s possible the account was logging in with cached credentials. It could also be a replication issue and the password change had not replicated to all DCs yet. You can test for replication issues with the dcdiag command.
Hi, Do you need to run any command after making some changes on the policy?
The default group policy refresh interval is 90 minutes. You can run gpupdate /force on a computer to force a group policy update.
It’s ABC process after promote your server to play domain control any admin will do it nothing new here.
Thank you so much
No problem
Hi ,
If I change the minimum password length, how will it affect existing accounts?
We have service account that i’m concern might be affected.
It should not affect accounts until their password expires. For example, user1 password doesn’t expire until 9/1 and you change the policy on 8/10, user1 would would remain unchanged until 9/1 when its password expires.
Is there a way to ensure that a group of service accounts are never forced to change their passwords? I have my service accounts in a global group, can I deny them read access to the policy?
You would need to check “Password never expires” for each account. I would not block them from the default domain policy.
So, once the ‘Password must meet complexity requirements’, does it prompts the user to change the passwords to meet this requirement at the next login?
Thank you
No, it will take effect when their password expires and they must change it.
Hi,
Nice article and thanks for detailed explanation. The complexity criteria is defined as below
“Contain characters from three of the following four categories:”
Can this be changed to mandatory four categories?
Please share your expert opinion
Thanks
There is no native way in active directory to accomplish this. You would need to find a 3rd party tool that integrates with Active Directory password policy. I would suggest making the password length requirement longer rather than adding more complexity. Longer passwords are very effective and is now recommended by several security standards such as NIST. Its hard enough for end users to remember 3 mandatory categories adding another one will blow their minds. Set minimum password length to 15 and you will have a stronger password policy than most organizations.
Great.. Thanks a lot.
No problem.