In this guide, you will learn how to use the gpresult command line tool to verify what group policy objects are applied to a user or computer.
The gpresult command can help you troubleshoot group policy settings by showing which policies are applied to a user or computer.
Table of contents:
What is gpresult
GPResult is a command line tool that shows the resultant set of policy for group policy objects. In other words, it creates a report that displays what group policy objects are applied to a user and computer.
If you are using group policy in your environment, then you definitely should know how to use this tool.
It’s possible for administrators to apply overlapping policy settings to a user or computer, the gpresult command can display these results and help in troubleshooting group policy issues.
Group Policy is an effective way for administrators to control policy settings, deploy software, apply permissions, and so on across the entire domain.
When you have multiple Group Policy Objects you need a way to verify those objects are getting applied to a user or computer.
This is exactly what GPresult was built to do.
How to install gpresult
- The gpresult command is included by default in Windows 10 and later editions for the Pro, Enterprise and Education editions.
- All server versions since 2003 have gpresult by default or available through adding features.
To verify the gpresult command is installed open PowerShell, type gpresult and press enter. You should receive the gpresult help information.
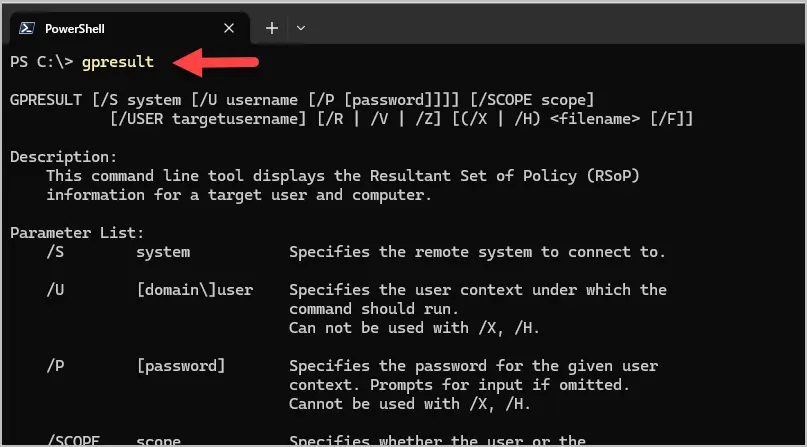
How to use gpresult command
The gpresult /r command is the best way to check what GPOs are applied to a user and computer. The steps below walk through how to use and review the command output.
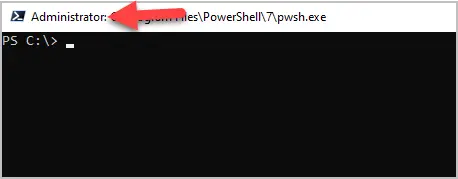
Step 1. Open PowerShell as Administrator
Import: If you don’t open PowerShell as administrator, the gpresult command will only display results for the user and not the computer.
It should display “Administrator” in the upper right corner.
Step 2. Type gpresult /r and press enter
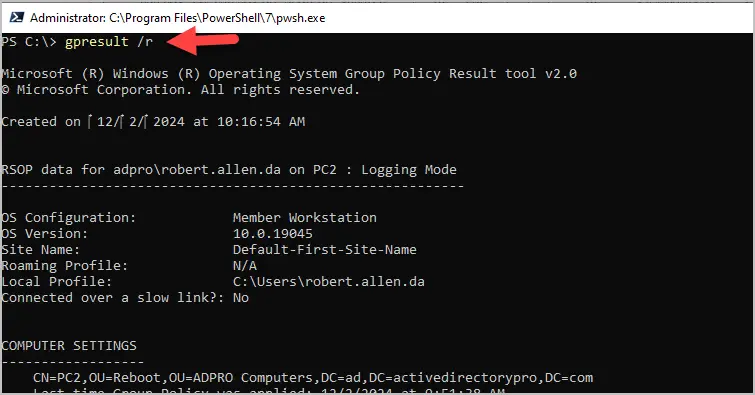
Step 3. Review the results
Below I’ll walk through the gpresult /r output from my computer and show you what I find most useful. Please note that your output will be different than mine.
Computer Settings
The computer settings section shows you two important details:
- Last time group policy was applied = This could be from a reboot, refresh cycle or manually running the gpupdate command.
- Group policy was applied from = Shows the domain controller the computer updated its GPOs from.
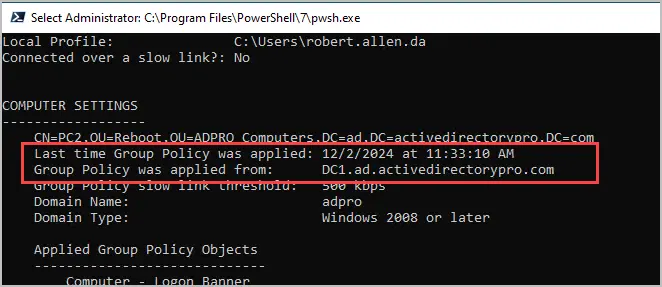
Computer settings > Applied group policy objects
These are the GPO objects that are applied to the computer. This is important because it will help you verify that the GPO is being applied to the computer object.
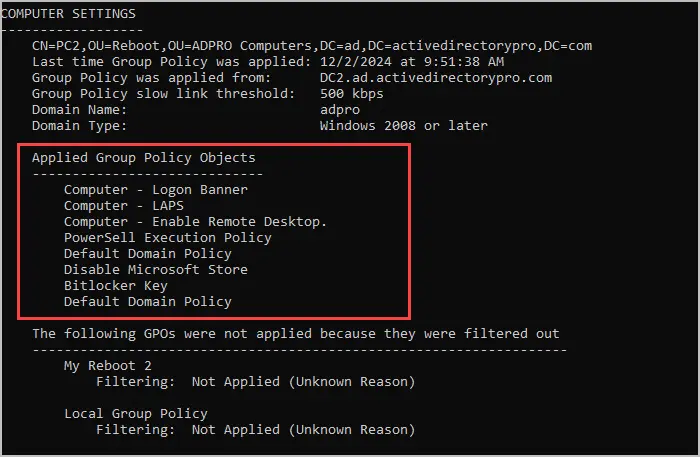
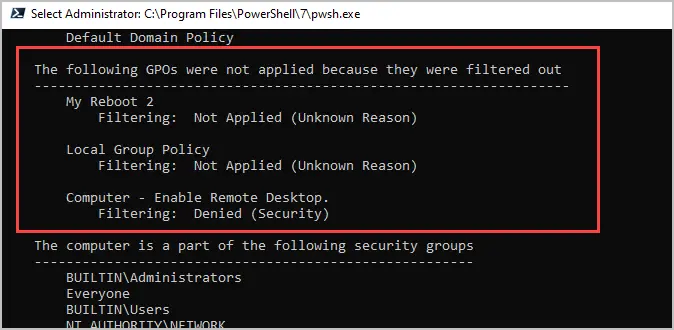
Computer settings > The following GPOs were not applied because they were filtered out
These are GPOs that are linked to the computer but are not applied. This can be useful when troubleshooting why a GPO is not being applied. Check the delegation tab in the group policy management console to see if the GPO is being denied.
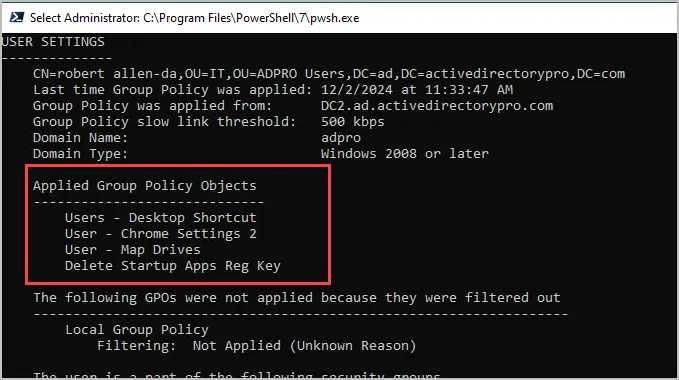
User Settings > Applied group policy objects
These are group policy objects that are applied to the user account. This will help you verify if the GPO is being applied to the user or not.
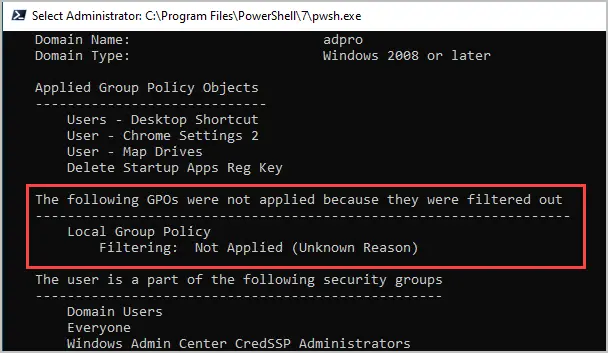
User Settings > The following GPOs were not applied because they were filtered out
These are GPOs that are linked to the user but are not applied.
GPResult Additional Examples
There are several command line switches available with the gpresult command, to view all the options use this command.
gpresult /?Key Parameters
- /S: Specifies the remote system to connect to.
- /U: Specifies the user context under which the command should run.
- /P: Specifies the password for the given user context
- /scope: Specifies whether the user or the computer settings need to be displayed.
- /H: Saves the report in HTML format
- /R: Displays RSoP summary data.
- /V: Specifies that verbose information should be displayed
Tip: Run the command prompt as administrator or you may run into issues with the command returning computer settings.
Display GPOs applied to a specific user
If you don’t want to see both User and Computer GPOs then you can use the scope option to specify user or computer
gpresult /r /scope:user
Display GPOs applied to a specific computer
gpresult /r /scope:computer
Display GPOs applied on a remote computer
gpresult /s pc2 /r
Save gpresult to html
This generates an html report of the applied group policy objects. If you don’t specify a path, it will save it to the system32 folder. In the above example, I’m saving the html report to c:\temp\reports.html
gpresult /h c:\temp\reports.html
Export to a text file
You can redirect the output to a text file with the command below. This is helpful if the results are producing lots of information.
gpresult /r >c:\results.txt
Group Policy Reports
If you want to create a report on GPO objects in your network, I recommend the AD Pro Toolkit. It includes over 200 built-in reports on users, groups, group policy, and security.
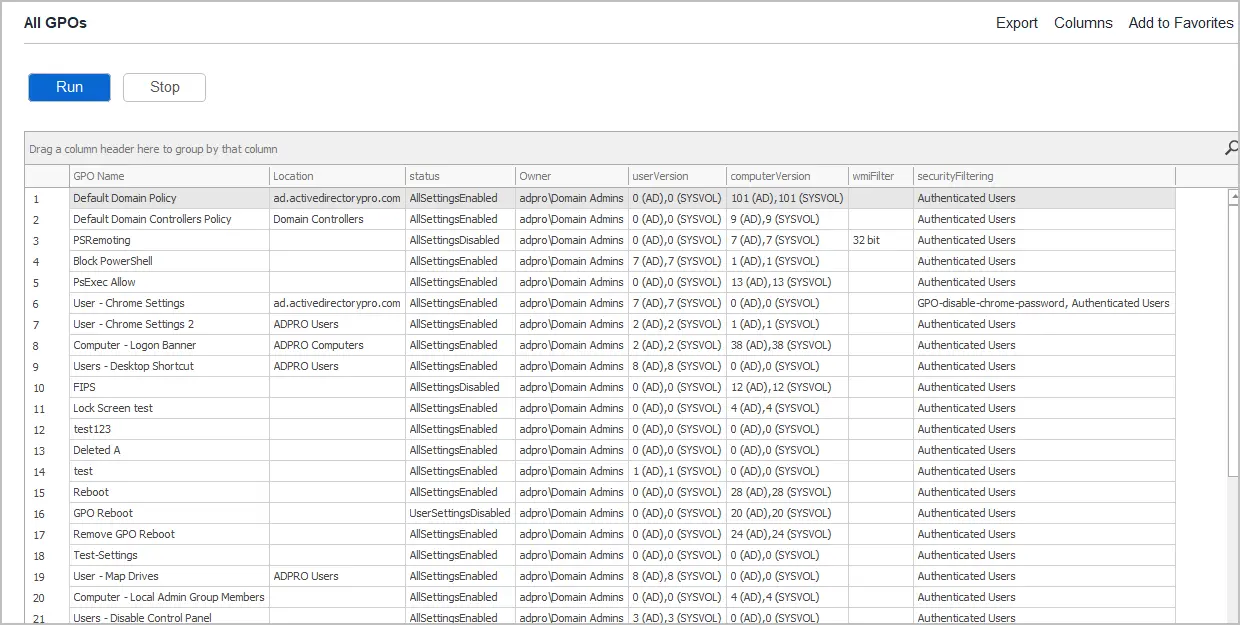
This easy to use tool will quickly generate a report on all GPOs, disabled GPOs, recently modified, and created, GPOs that are not linked, and much more. Below is a complete list of GPO reports.
General Group Policy Reports
- All GPOs
- All settings disabled
- All settings enabled
- Computer configuration disabled
- User configuration disabled
- Deleted GPOs
- GPOs created in last 7 days
- GPOs created in last 30 days
- GPOs created in last 60 days
- GPOs modified in last 1 days
- GPOs modified in last 7 days
- GPOs modified in last 30 days
- Link not enabled
- Block inheritance enabled
- OU linked GPOs
- Site linked GPOs
- Domain linked GPOs
You can download a free trial and test the reports on your own network.
Group policy can be a pain, even when best practices are followed group policy can still be challenging. Knowing how to use these built in tools will help you to verify and troubleshoot group policies in your environment. Go give it a try and let me know if you have any questions.
Thank you! Will be usefull
Hello… Thank you for the presentation/info…
(I’m new to GPO stuff..)
Is this tool can be used to show “Computer Config > Windows Settings > Security Setting >User Rights Assignment > “Log on as a service” is applied?
How can I check if a account has this right assigned? (I know how to add in the GPEdit….
Thank you very much!!
Check where the GPO is applied. Go to Group Policy Objects, select the GPO that has the settings and under scope you can see where the GPO is applied.
For example, I have a GPO called “users- lock screen” and this GPO is applied to the Accounting OU under my Users OU. This means everyone in the Accounting OU will get this GPO applied.
You can verify it is being applied by using the GPResult command as demonstrated in this guide.
Hope that helps.
i am having this issue on my domain joined computer can anyone look and help me with that
while
i have checked everything on domain controller by running dcdiag /c /v and every test goes smooth no error occurred. but on user end i am facing this issue i use all methods like (GPUPDATE, Restart system etc)
Applied Group Policy Objects
—————————–
Local Group Policy
The user is a part of the following security groups
—————————————————
ERROR: An unexpected error occurred.
Make sure to run the command prompt in administrator mode. If it just says command prompt in upper left then you are not in administrator mode.
Great Post! When running “gpresult /scope:computer /r” is there a way to only display the GPO’s that are listed in the Applied Group Policy Objects section for the output?
Good post, thanks! There is also great post about gpresult here – https://sysadminpoint.com/2020/08/18/group-policy-diagnostics-with-gpresult-command/
Metalline, good article. Thanks for sharing.
dead link
Please help running “gpupdate /force” runs without an error but when I run “gpresult /r”, Applied group Policy Objects shows N/A. What could be the problem here?
im probably too late, run your command line in administrator mode, if not you will see only the “users” part of the GPO
Martin, great tip. A very common mistake when running gpresult /r
Great Demo
Thanks Charley
great
bro
Thanks salman
yes thanks
There is also a professional tool called gytpol Validator which will validate all endpoint configurations against the GPO and Active Directory
Thanks Matthew. I have not used that tool, I’ll check it out.
Good Post.. thanks alot
Good post.