Do you need to demote a domain controller?
Is your domain controller dead and do you want to manually remove it?
No problem.
In this guide, I’ll walk through two options to remove a domain controller. If you still have access to the server then option 1 is the preferred choice.
- Option 1: Demote a Domain Controller Using Server Manager
- Use this option if you still have access to the server.
- Option 2: Manually Remove a Domain Controller
- Use this option if the server is dead or you no longer have access to it.
In both examples, I’ll be using Windows Server 2016 server but these steps will work for Server 2012 and up.
Tip #1 Starting with Server 2008 domain controller metadata is cleaned up automatically. Windows Server 2003 server or earlier will require using the ntdsutil command to cleanup metadata. With that said you still need to manually remove the server from sites and services.
Tip #2 Make sure there are no other services running on the server (like DNS or DHCP) before shutting down the server. If you can avoid this you may save yourself a big headache.
Tip #3 If the domain controller you are removing has FSMO roles configured they will get transferred to another DC automatically. You can check this with the netdom query FSMO command.
Video Tutorial
If you don’t like video tutorials or want more details, then continue reading the instructions below.
Option 1: Demote a Domain Controller Using Server Manager
This is Microsoft’s recommended method for removing a domain controller.
Step 1. Open Server Manager
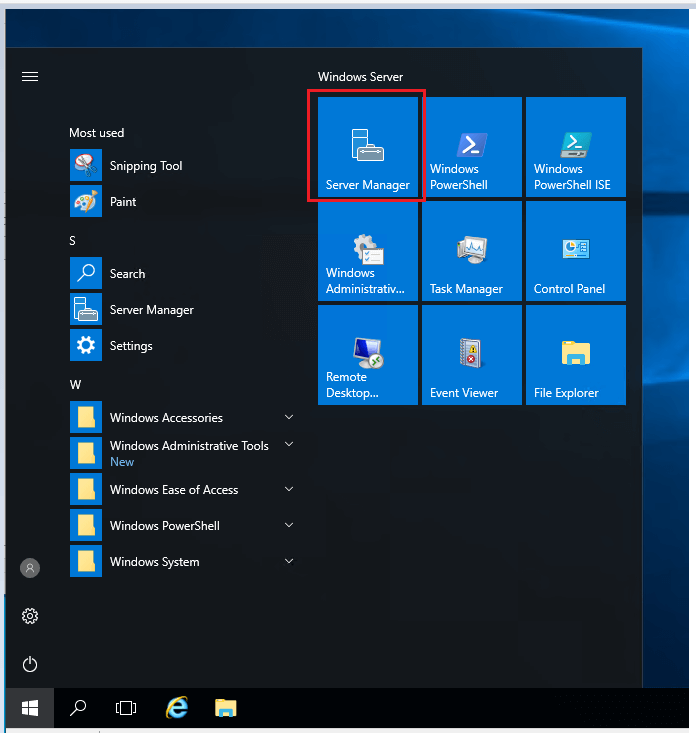
Step 2. Select Manage ->”Remove Roles and Features”
Click next on the “Before you begin page”
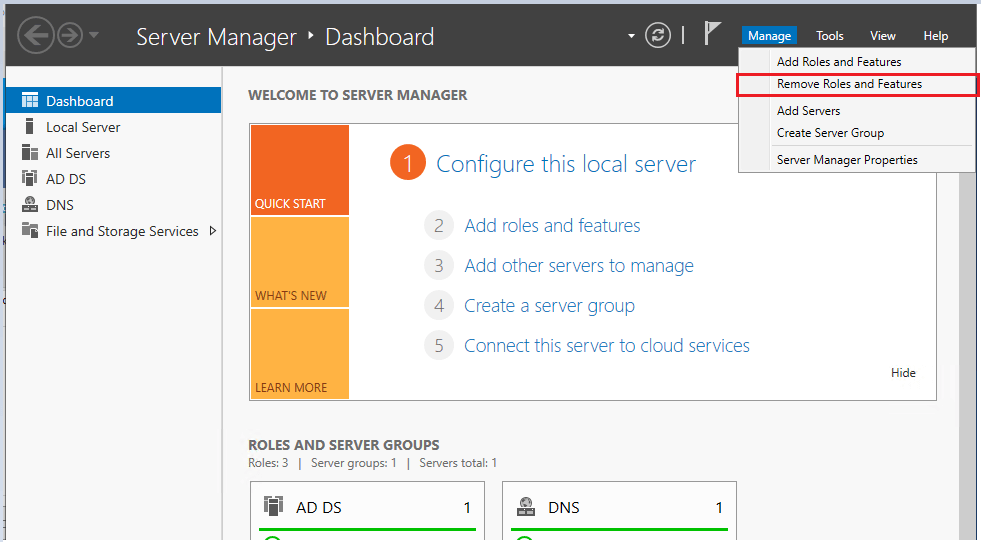
Step 3. On the server selection page, select the server you want to demote and click the next button.
In this example, I’m demoting server “srv-2016”
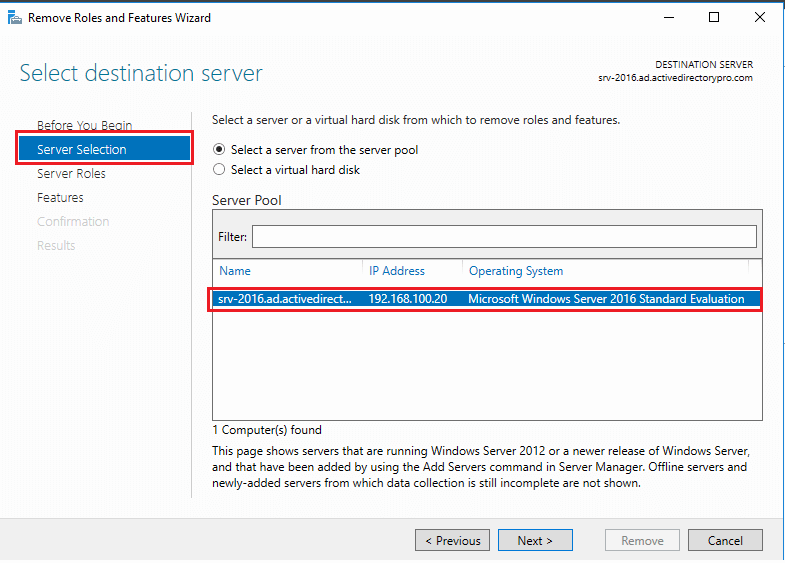
Step 4. Uncheck “Active Directory Domain Services” on the Server Roles page.
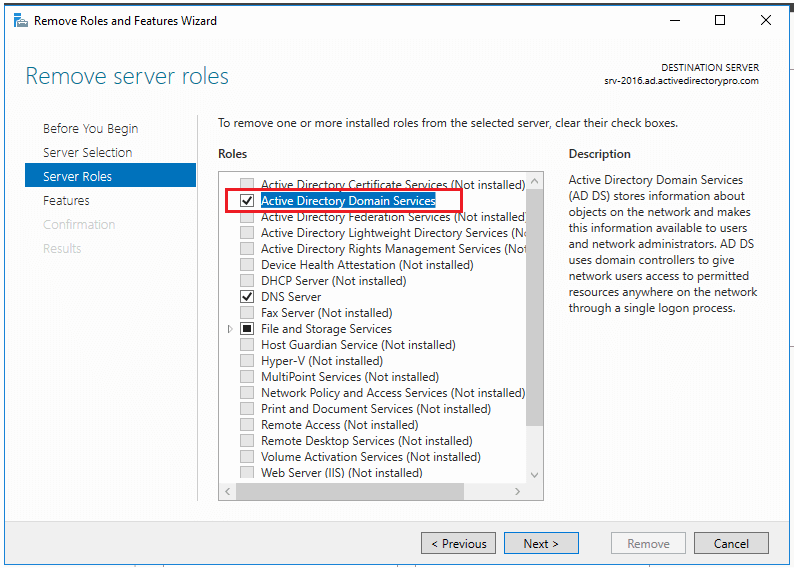
When you uncheck you will get a popup to remove features that require Active Directory Domain Services.
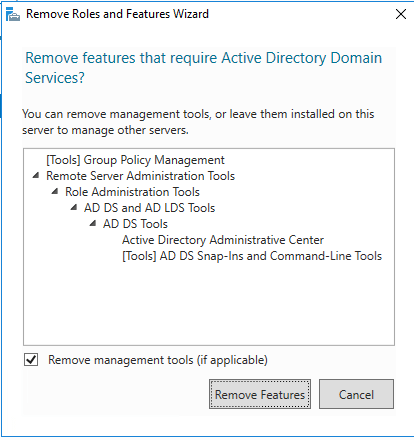
Step 5. Select Demote this domain controller
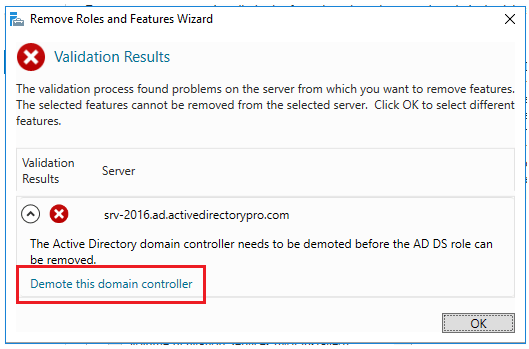
On the next screen make sure you DO NOT select “Force the removal of this domain controller”. You should only select this if you are removing the last domain controller in the domain.
You can also change credentials on this screen if needed.
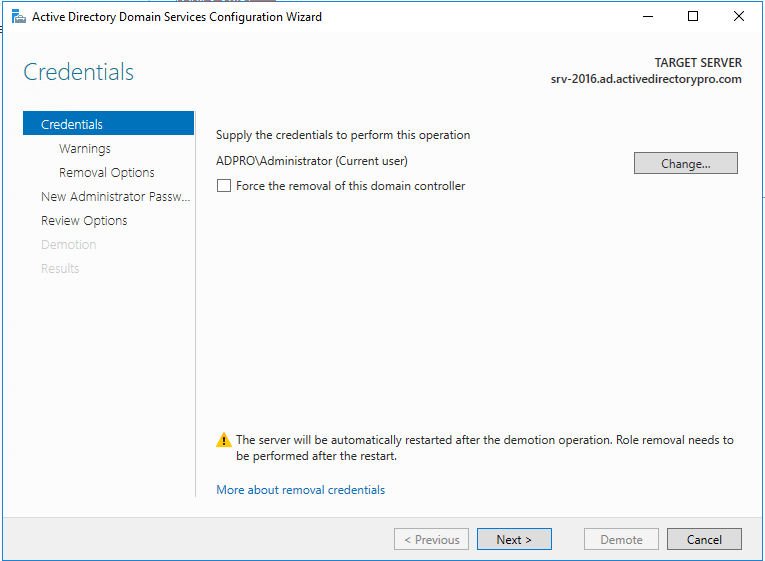
Click Next
Step 6. On the warnings screen, it will give you a warning this server hosts additional roles. If you have client computers using this server for DNS you will need to update them to point to a different server since the DNS role will be removed.
Check the box “Proceed with removal and click next
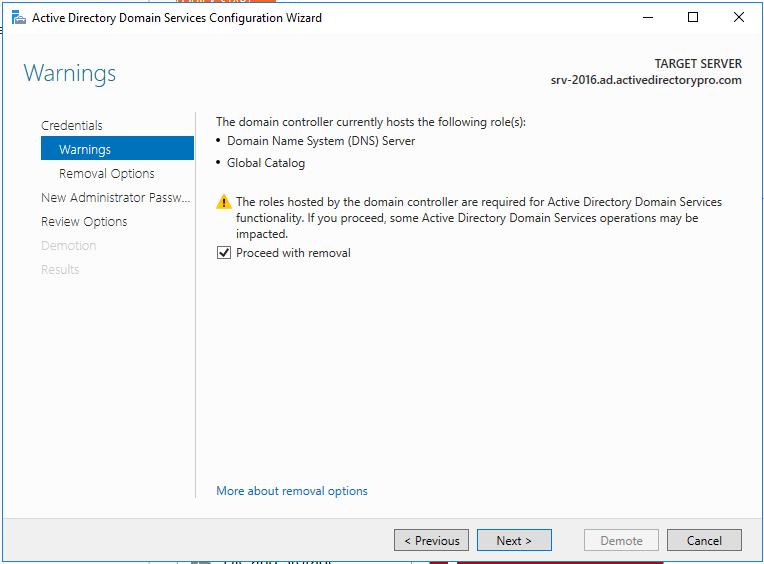
Step 7. If you have DNS delegation you can select “Remove DNS delegation and click next. In most cases, you will not have DNS delegation and can uncheck this box.
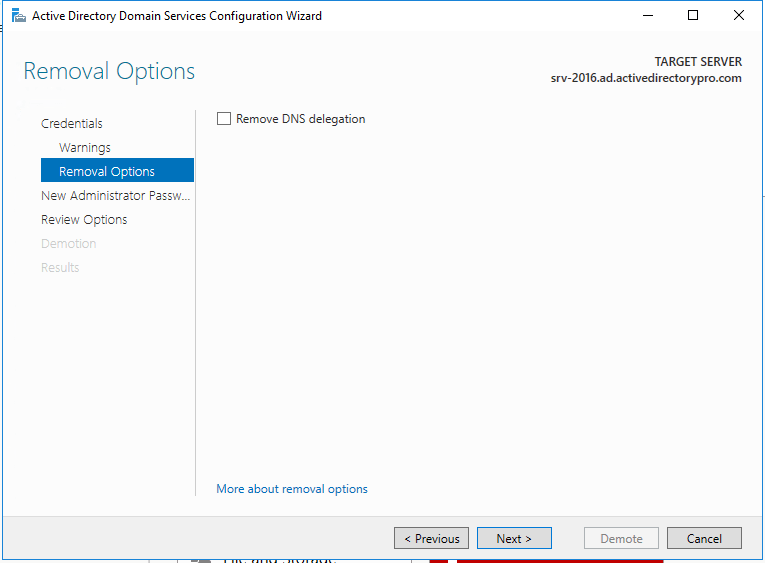
Step 8. Now put in the new administrator password. This will be for the local administrator account on this server.
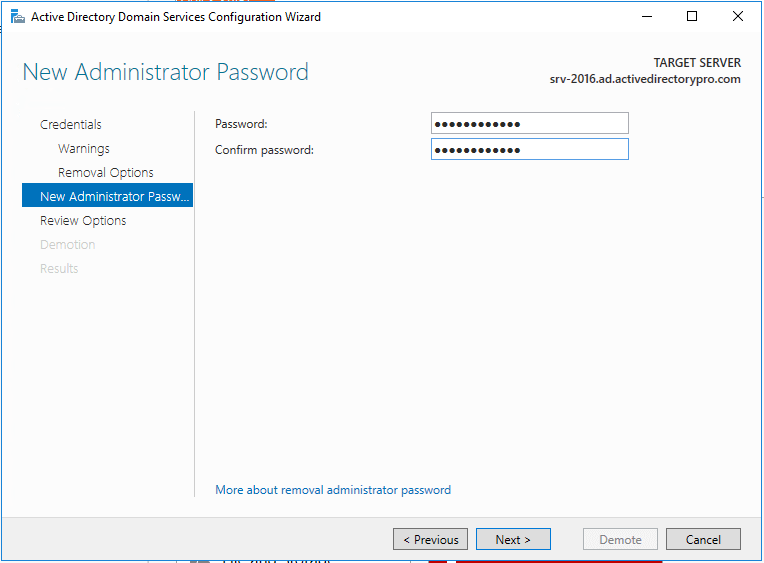
Step 9. Review options and click “Demote”
#Tip – There is a “view script” button that generates a PowerShell script to automate all the steps we just walked through. If you have additional domain controllers to remove you could use this script.
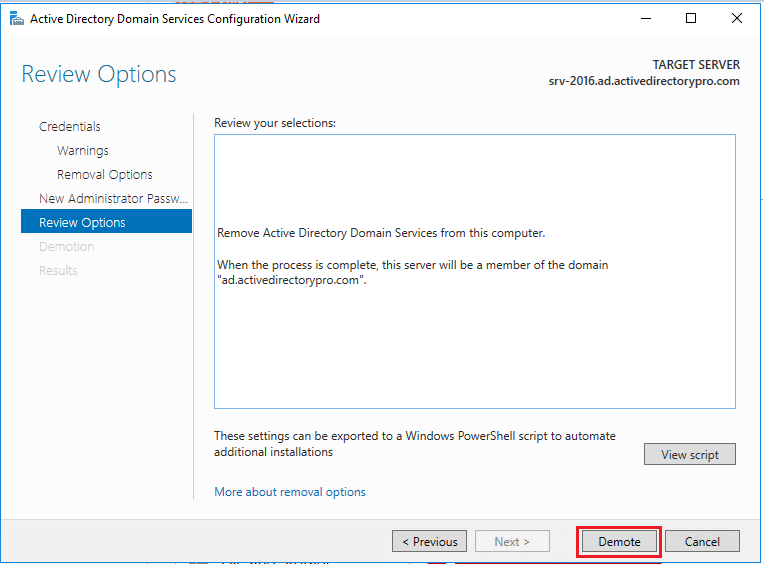
When you click demote the server will be demoted and rebooted. Once it reboots the server will be a member server. You can log in with domain credentials to the server.
Additional Cleanup Steps
For some reason, Microsoft decided not to include sites and services in the cleanup process. Maybe it’s left there in case you want to promote the server back to a domain controller. If you are not going to promote the server back to a DC then follow these steps.
Step 1. Open Active Directory Sites and Services and remove the server
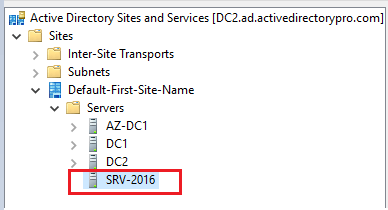
You can see above the server I just demoted is still listed in sites and services. I’ll just right-click on it and delete it.
That is it for option 1. You can go into the “Domain Controllers” folder and verify the server is removed. It’s also a good idea to run dcdiag after removing a DC to make sure your environment has no major errors.
You may also need to review and test replication. You can use the repadmin command to test for replication issues.
Option 2: Manually Remove a Domain Controller
Use this option if the server is dead, disconnected, or you just can’t access it. There is really only 1 step.
Step 1. On another domain controller or computer with RSAT tools open “Active Directory Users and Computers”
Go to the domain Controllers folder. Right click the domain controller you want to remove and click delete.
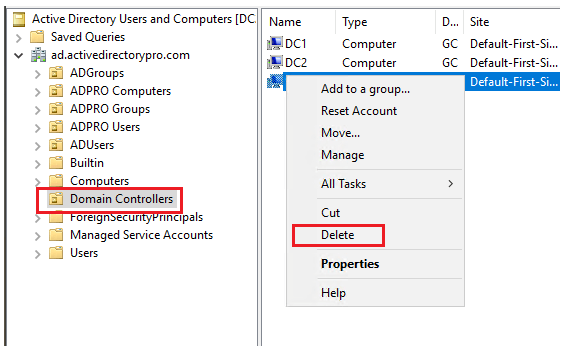
On the next screen select the box “Delete this Domain Controller anyway” and click delete”
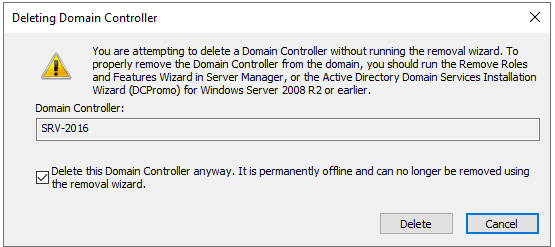
If the DC is a global catalog server you will get an additional message to confirm the deletion. I’m going to click Yes.
That is pretty much it. Easy hu?
The last step would be to remove the server from Sites and Services just like I showed you in option 1.
As I mentioned at the top of this article starting with server 2008 the metadata cleanup is done automatically with both options. Most how to guides will tell you to open the command prompt and run the ntdsutil to cleanup the metadata. This is not needed if your server operating system is 2008 or above.
It seems easier to just manually remove the DC than going through the server manager wizard. Technically I’m not sure what the difference is but Microsoft recommends using the removal wizard if you can. Use the manual method as a last option.
Automate Domain Controller Health Check
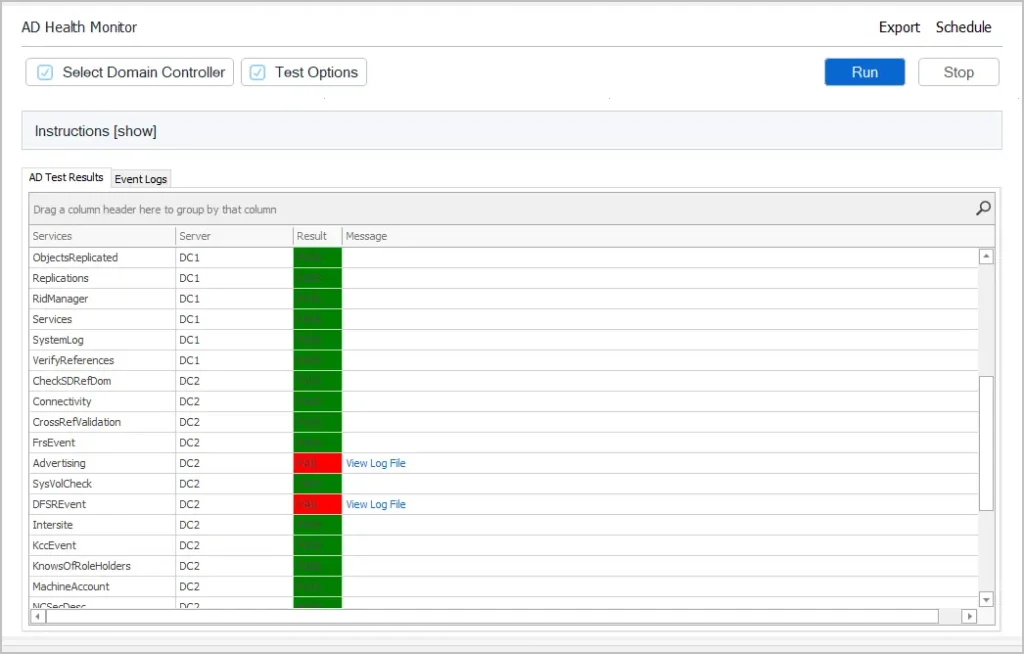
As a system administrator, I know how critical it is to ensure domain controllers are running without errors. I created a simple AD Health Check Tool to automate testing the health of all domain controllers and send me a daily email report. This has been a huge time saver and allowed me to focus on other important tasks. You can download this tool for FREE and try it on in your domain. The free version is limited to 1 domain controller.
I have three DCs in environment.
we want to demote one of DC (it’s not primary DC), but that DC also has AD CS role running.
Does demoting DC affect AD CS role?
Do i need to transfer that AD CS to another DC before demoting?
I don’t have experience with this. Below is a link to someone with the same question, unfortunately it looks like a mix of responses.
https://community.spiceworks.com/t/questions-about-demoting-domain-controller/814147/11
Thanks for the documentation and gotcha notes.. this is the kind of stuff you don’t do every day.
First hello…
Now…the problem:
I have a lot DC´s in the organization.
In one of the DC´s, I need demote DC service, but in the same DC I have the Print Server.
The question is:
When I demote DC, is the Print Server still working?
Thanks for your dedicated time!
Print server should still be working. After demoting the domain controller will be a member server and any other services should still work.
After “Demoting” the Server via Server Manager and the automatic reboot, I had to start the ‘Remove Role process’ once more.
So after completing Step 9, I had to do Steps 1-4 again.
Otherwise it showed me, that there are still domain controller configurations present, when trying to do the cleanup via Sites and Services.
Not 100% sure, if this is mandatory, but prevents a kinda confusing warning.
I accidentally forced the removal of the DC and didn’t get the FSMO role migration wizard, but the new DC replacing it shows as a GC in ADUC, and has been working fine with the old DC powered off for the past 4 days. Is there a way to make sure I didn’t mess anything up by forcing the removal?
thanks for the guide, i have succefully removed my DC but there seems to be entries in the DNS zones (forward and reverse) for the removed DC. How can i remove all entries for the DC -one by one or is there a better way?
Hi Robert,
Thanks for your guide. I am trying to demote a domain controller, but when I do I am asked if I want to Remove DNS Delegation, this DC is not in a child domain and there are other DC’s still active in the domain, I am not quite sure how to proceed here as the Microsoft documents say:
“The options only appear if applicable to this domain controller. For instance, if there is no DNS delegation for this server then that checkbox will not display.”
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/deploy/demoting-domain-controllers-and-domains–level-200-
So going off that quote, DNS Delegation is applicable to this domain controller and I should leave it ticked, do you know how to verify DNS Delegation is applicable or not?
Thank you
You most likely do not need this box ticked.
DNS delegation is typically used on a subdomain. You would have delegated the authority of the zone to another DNS server.
Here is a really good video explaining DNS delegation. At 11:15 in the video, it shows you how to check if you have DNS delegation configured.
https://www.youtube.com/watch?v=VtSPwXnHK0s
Thank you! that’s perfect.
I need to make a 2022 server a domain controller in a 2012R2 domain without upgrading the OS on an existing DC (windows 2012 R2). Is it possible to set up a new domain, e.g. acme.com on the 2022 DC, run run “Set-ADForestMode –Identity “acme.com” –ForestMode Windows2012R2Forest” then just remove the domain from it but leave all the services from it 2012R2 level without changing the level
Yes, you can promote a 2022 server to a domain controller in 2012R2 domain. If you want to remove the 2012 server, transfer the FSMO roles first and then demote the server.
have one server 2016 files server also hold DC role. Active Directory is not synced with other DC, with errors. Would like to demote DC to remove the AD. Will still have few DC in the domain.
Question:- after demote, it will be under workgroup. I still need the file sharing. should i rejoin it to the domain after deleting the server_name inside sites_directory_domaincontroller/?
Thank you
If you have shared a folder on the old domain controller and users still need access to the share then yes rejoin it to the domain. If the old DC is running an unsupported OS version I would migrate the file share to a supported version.
sysvol folder not replicating. will a demote of 20212 still work?
new 2019 has all fsmo roles
if using option 2, how to remove DNS?
The DNS record or the service?
For the record, you can try the ntdsutil command. If that doesn’t do it you will need to open the DNS console and manually delete it. For the service, open server manager and use the remove roles and features wizard. In either case, you want to make sure no clients are still using the server for DNS.
Wound up with the old DC still listed in Sites and Services because it contains “DNS Settings; msDNS-ServerSettings”. I can’t get a clear answer anywhere. This seems to be due to the DNS key master role, but as best as I can tell we’re not using secure DNS, so this may have no value. But I can’t get a clear answer anywhere on how safe it is to delete this record. I’ve kept the DC demoted and turned off for well over a month with no apparent impact. Any reason not to delete?
I need to demote my domain controller since my server has moved to azure .my sql server is still responding to the domain controller ip address . i need to check which services are connected from sql end to the domain controller . how can we do that ?
On the sql server run the command netstat -abn
This will show the exe that is making the connection to the domain controller.
Can I demote (cause DNS was not running& not sync to primary DC) then 2 hours later promote again
Yes. I would verify it was removed from all DCs before promoting again.
I really don’t know that method in step 1. Thank you!
God bless you
Thank you so much! This worked very well along with the links to check AD after decommissioning.
very well detailed steps , thanks for elaborated articale
i have 3 windows server 2016, only the primary DC is still alive, the other 2 are completely dead and missing.
just tried method 2 to remove them manually, and i got the error message saying :
“Windows cannot delete object LDAP://[ some ldap info here ] because : Access is denied”.
i tried in both the “Active Directory Users and Computers” console, as well as the “Active Directory Sites and Services” console, both have the same error messages.
any idea how can i proceed with the removal ?
Check if “Protect object from accidental deletion” is enabled.
1. Open up Active Directory Sites and Services.
2. Expand the site name where the DC you want to delete is, expand the Servers folder and finally expand the DC you want to delete.
3. Right click on NTDS Settings for the DC you want to delete.
4. Click on the Object tab.
5. Uncheck the “Protect object from accidental deletion” checkbox.
6. Click OK to save your changes.
Now you will be able to delete the domain controller from Active Directory Users and Computers.
Great article Robert
I need to demote a RWDC to RODC. Demote the RWDC to a member then DCPROMO to a RODC. Can I return the server as a domain member then DCPROMO to RODC without rebooting? If DNS and DHCP roles are removed in the process I am thinking I can add those roles back once DCPROMO to RODC? What becomes of those roles in-between the time it takes to move to a member and promoting back to a RODC? Any concerns?
I have a problem on my network whereby ADDS doesn’t synchronize between the two domain controllers. One is Server 2008 and the other Server 2019. On the Server 2019 DC there is a large data store. If I take the Server 2008 offline, then clients can’t successfully authenticate to access the shares on the Server 2019. I’ve used dcdiag extensively on both servers and think the issue lies with the Server 2019. Therefore, I’d like to demote this server and then add DS again to see if this will fix the problem. The question is, if I does this will I make the data on this server inaccessible in the future to users or clients on the network? Obviously the data is backed up.
I would spin up another 2019 DC, move everything off the 2008 server and demote it. Make sure everything is migrated from the 2008 server before demoting it (FSMO roles, shares, any other roles (DNS, DHCP, etc).
Dcdiag should display errors for a failing DC, the event logs can also be helpful.
https://activedirectorypro.com/dcdiag-check-domain-controller-health/
Thank you so much sir,
It is very easy to understand.
Thank you sir..
Hi
Will this work if the DC is tombstoned after been switched off for months on end ?
I can survive without this DC as it was a backup
thanks
You will need manually remove the DC (option 2).
Hi, thanks for this guide.
Option 1, step 2 had me confused for a second.
It says: Select “Remote Roles and Features”.
I know you mean “Manage > Remove Roles and Features” Like the screenshot shows, but still…
Thanks. I have updated it.
This is good information.
Question though, my Exchange 2013 is installed in a server with BackUp Domain Controller. Will there be any issues, demoting the server? I am not removing the server yet as I need it as a member server for the Exchange 2013. Any thoughts?
Thank you
oh man… that is a scary one! Assuming you have multiple DCs and everything is healthy it should be ok. Exchange 2013 schema should be replicated to other domain controllers so verify that first. I would use dcdiag to check the health of all DCs first and also verify replication.
Do you have plans to move email to office 365? Might be worth waiting.
The instructions worked flawlessly. I just want to point something out that happened in my case that wasn’t mentioned here. I removed the DNS Role first and then rebooted. When attempting to demote I got this checkbox: “Remove this DNS zone (this is the last DNS server that hosts the zone)”, it didn’t let me continue unless I checked it, but that message was scary as heck. The thing was that the server still had its network interface set up with the localhost IP address as primary DNS Server (from when it had the DNS Role I think). So I exited Server Manager, then changed the DNS Settings with the new DNS Servers IP addresses and restarted the process again. The check didn’t appear again and the process continued smoothly.
Thank you very much for this guide, it was very helpful.
Hi Julius,
Thanks for sharing this.
Good information!
Just curious though how would you go about removing a server for 30 days and then promoting back to the network with out any issues but this scenario will happen multiple times a year.
If you have redundancy in place there should be no issues. Make sure your systems are configured to use an alternative DNS and DHCP server. The biggest issue I have run into is all the systems that are manually configured to a domain controller for authentication and DNS. In larger networks, this can get out of control with other admins making changes. I put together a checklist for changing the IP address on DCs that can also help when demoting servers. https://activedirectorypro.com/change-ip-address-on-domain-controller/
Thank you for the detailed steps.
Hi Ray. You are welcome.
Thanks for the guide! Once all this is done, would you remove the member server from the domain before shutting it down for good?
If the member server is proving no services then yes remove it from domain and shut it down. What I do if I’m not 100% sure is shut it down for 1-2 weeks and if nothing breaks or no one screams then delete it.
“…What I do if I’m not 100% sure is shut it down for 1-2 weeks and if nothing breaks or no one screams then delete it.”
this is the way
SOP 🙂
What about the DNS role?
See step 6, it will be removed.