In this tutorial, I’ll show you how to use the Dcdiag command line utility to perform a domain controller health Check and test DNS.
I’ll also show you a GUI tool that lets you check the health of multiple domain controllers at once.
Be sure to check the examples section below and I’ll show you the output of a normal domain controller and one that has issues.
Table of contents:
- What is Dcdiag
- How to install Dcdiag
- Check Active Directory Health Using Dcdiag
- Check Domain Controller Health with AD Pro Toolkit
- Automate AD Health Check (Email Report)
- Active Directory Diagnostic Tests
Let’s dive right in.
What is Dcdiag
Dcdiag is a Microsoft Windows command line utility that can analyze the state of domain controllers in a forest or enterprise. You can choose to analyze a single domain controller or all DC’s in a forest.
You might be thinking, how well does a command line utility really do at testing and finding issues with domain controllers?
Well, it actually does a pretty good job! I was surprised to find out how many different tests this command actually did.
I counted a total of 30 different tests, and some tests had multiple tests.
So what does Dcdiag actually do? What kinds of tests does it perform?
You can view a list of tests in the command help menu, run dcdiag /? to see the help menu.
I’ll have to admit the descriptions from the help command are not that helpful. I came across a good blog post by Ned Pyle called What does DCDiag actually do that explains each test in more details. If you are interested in learning exactly what the Dcdiag command does then I recommend you read that post.
How to install Dcdiag
If you want to run Dcdiag or use the Active Directory Health Check tool you will need to install the RSAT tools.
There is a really good chance that you already have the Dcdiag tool installed.
If you have the AD DS role installed then Dcdiag is already installed.
If you have the Remote Server Administration Tools (RSAT) tools installed then you already have Dcdiag installed.
Check Active Directory Health Using Dcdiag (examples)
DCDiag is very easy to use.
There are several different command line switches that can be used with Dcdiag, to view them all just use this command dcdiag /?
Here is an overview of the switches I’ll be using in the examples below.
/s: dcname switch is used to run Dcdiag against a remote server
/v: switch prints more detailed information about each test
/c: switch means comprehensive, this will run all tests including the dns test.
/q: switch will only print errors. This is useful as dcdiag can display a lot of information, if you want to see just the errors then use this switch.
/f: switch is used to redirect the results to a file.
TIP: When running dcdiag it will probably report some errors but this doesn’t necessarily mean you have issues with your domain controllers. For example, the command will query the system logs on the DC and display errors logs, but they could be errors from a computer or another server. Again this may not be a DC issue. You will just have to review and determine if it’s related or not.
Video Tutorial
If you don’t like video tutorials or want more details, then continue reading the instructions below.
Example 1: Use /s to run against a remote server
This will run all the DC tests against the remote server DC1.
dcdiag /s:DC1
To run this on a local server just leave off the /s:servername
Example 2: Using /v to display more details
The verbose switch will display additional details. It does the same tests as the first example it just displays more details about each test.
dcdiag /s:DC1 /v
Example 3: Using /f to save to a log file
By using the /f you can save the results to a text file. This is great for logging the results and reviewing them at a later time.
dcdiag /s:DC1 /f:c:\it\dcdiag_test.txt
Example 4: Using /a to run against all domain controllers
If you have multiple domain controllers and want to test them all at once, then use this command. If you have many domain controllers this will be a lot of information displayed, this is where using the /f option would come in handy.
dcdiag /s:DC1 /a
Example 5: Use /q to only display the errors
DCDiag can display a lot of information, to remove the noise and only display the errors use this command.
dcdiag /s:DC1 /q
Example 6: Use multiple switches (My favorite)
Here are the commands I like to run. It will run all tests, displays all the details, and outputs its to a file.
dcdiag /s:DC1 /c /v /f:c:\it\dcdiag_test.txt
Now that you know how to test your domain controllers I’ll move on to testing DNS. By the way, if you use the last example that includes the /c that switch will run all tests including DNS.
How to test DNS with DCDiag
The DNS diagnostics also includes several tests.
Here are the tests that are performed, by default all tests except external name resolution run.
/DnsBasic (basic tests, can’t be skipped)
/DnsForwarders (forwarders and root hints tests)
/DnsDelegation (delegations tests)
/DnsDynamicUpdate (dynamic update tests)
/DnsRecordRegistration (records registration tests)
/DnsResolveExtName (external name resolution test)
/DnsAll (includes all tests above)
/DnsInternetName: <internet name> (for test /DnsResolveExtName)
Use the following command to run a DNS test
dcdiag /s:dc1 /test:dns
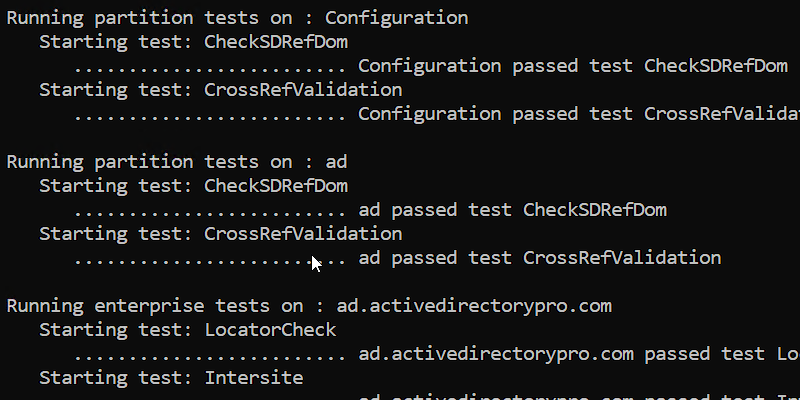
Example: Dcdiag results from a normal domain controller
Directory Server Diagnosis Performing initial setup: * Identified AD Forest. Done gathering initial info. Doing initial required tests Testing server: Default-First-Site-Name\DC1 Starting test: Connectivity ......................... DC1 passed test Connectivity Doing primary tests Testing server: Default-First-Site-Name\DC1 Starting test: Advertising ......................... DC1 passed test Advertising Starting test: FrsEvent ......................... DC1 passed test FrsEvent Starting test: DFSREvent ......................... DC1 passed test DFSREvent Starting test: SysVolCheck ......................... DC1 passed test SysVolCheck Starting test: KccEvent ......................... DC1 passed test KccEvent Starting test: KnowsOfRoleHolders ......................... DC1 passed test KnowsOfRoleHolders Starting test: MachineAccount ......................... DC1 passed test MachineAccount Starting test: NCSecDesc ......................... DC1 passed test NCSecDesc Starting test: NetLogons ......................... DC1 passed test NetLogons Starting test: ObjectsReplicated ......................... DC1 passed test ObjectsReplicated Starting test: Replications ......................... DC1 passed test Replications Starting test: RidManager ......................... DC1 passed test RidManager Starting test: Services ......................... DC1 passed test Services Starting test: SystemLog ......................... DC1 passed test SystemLog Starting test: VerifyReferences ......................... DC1 passed test VerifyReferences Running partition tests on : ForestDnsZones Starting test: CheckSDRefDom ......................... ForestDnsZones passed test CheckSDRefDom Starting test: CrossRefValidation ......................... ForestDnsZones passed test CrossRefValidation Running partition tests on : DomainDnsZones Starting test: CheckSDRefDom ......................... DomainDnsZones passed test CheckSDRefDom Starting test: CrossRefValidation ......................... DomainDnsZones passed test CrossRefValidation Running partition tests on : Schema Starting test: CheckSDRefDom ......................... Schema passed test CheckSDRefDom Starting test: CrossRefValidation ......................... Schema passed test CrossRefValidation Running partition tests on : Configuration Starting test: CheckSDRefDom ......................... Configuration passed test CheckSDRefDom Starting test: CrossRefValidation ......................... Configuration passed test CrossRefValidation Running partition tests on : ad Starting test: CheckSDRefDom ......................... ad passed test CheckSDRefDom Starting test: CrossRefValidation ......................... ad passed test CrossRefValidation Running enterprise tests on : ad.activedirectorypro.com Starting test: LocatorCheck ......................... ad.activedirectorypro.com passed test LocatorCheck Starting test: Intersite ......................... ad.activedirectorypro.com passed test Intersite
Example: Failed kdc service and NETLOGON Service
Here is the dcdiag output when the kdc and NETLOGON service is stopped. I used the /q switch to only display the errors
C:\Users\rallen>dcdiag /s:dc2 /q Fatal Error:DsGetDcName (DC2) call failed, error 1717 The Locator could not find the server. ......................... DC2 failed test Advertising kdc Service is stopped on [DC2] NETLOGON Service is stopped on [DC2] ......................... DC2 failed test Services Warning: DcGetDcName(GC_SERVER_REQUIRED) call failed, error 1717 A Global Catalog Server could not be located - All GC's are down. Warning: DcGetDcName(PDC_REQUIRED) call failed, error 1717 A Primary Domain Controller could not be located. The server holding the PDC role is down. Warning: DcGetDcName(TIME_SERVER) call failed, error 1717 A Time Server could not be located. The server holding the PDC role is down. Warning: DcGetDcName(GOOD_TIME_SERVER_PREFERRED) call failed, error 1717 A Good Time Server could not be located. Warning: DcGetDcName(KDC_REQUIRED) call failed, error 1717 A KDC could not be located - All the KDCs are down. ......................... ad.activedirectorypro.com failed test LocatorCheck
That’s it.
Easy right?
DCDiag is a simple yet very powerful tool to check and diagnose domain controllers. I highly recommend that you become familiar with this tool and run it in your environment from time to time.
Check Active Directory Health with AD Pro Toolkit
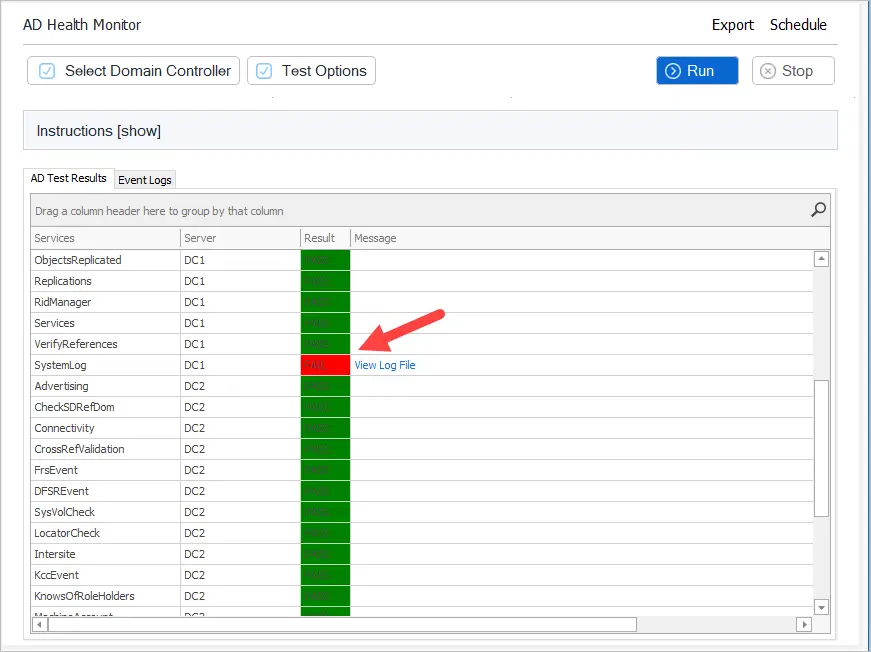
The Active Directory Health Check tool creates easy to read health reports on your domain controllers. It makes it very easy to check the health of multiple domain controllers at once.
The GUI tool has the following benefits:
- Easily check Active Directory health on multiple domain controllers
- Quickly see why a test failed by clicking on a test
- Gets important events from the Windows event logs (errors, warnings, critical errors)
- Export and schedule automated reports
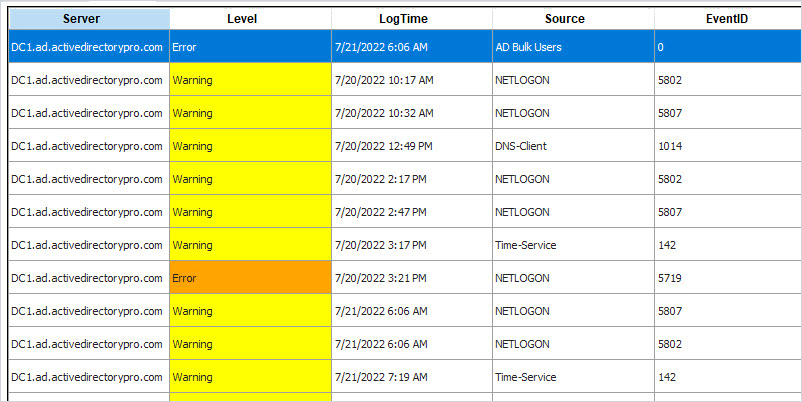
This tool can also get the critical events from your domain controllers. This makes it easy to review the logs and quickly spot potential issues.
You can download a free trial of this GUI health monitoring tool by clicking the button below.
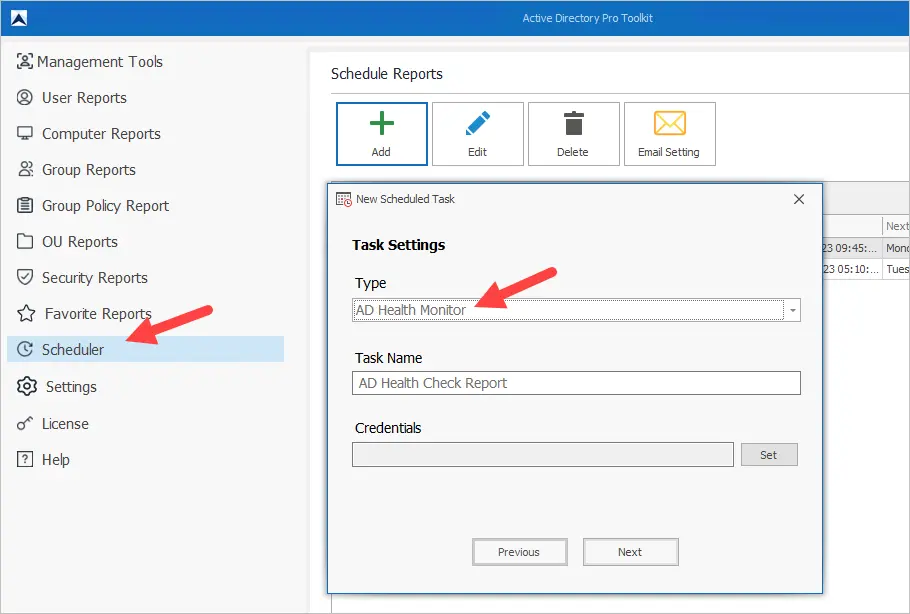
Automate AD Health Check (Email Report)
Automate checking the health of your domain controllers by using the built-in scheduler. Schedule the report to run daily, weekly, or once a month (I recommend daily).
Very nice and helpfull.
send me more AD related stuffs and commands to reduce the workloads.
Thanks and appreciate.
excellent
Your page was informational and directly to the point, thanks for not busting my head up.
Good stuff, homeslice. Appreciate it.
Shake and Bake.
Awesome information and in brief explanation
Hi Shravan, thanks for the feedback.
Nice Article, really help me a lot! Thanks
Is DCDIAG /FIX supported in Windows server 2016
If you run dcdiag /? it is listed as an option. I have not run it but it appears to be supported.
Great article on using DCDiag and providing an example of what a normal server result would look like.
I see one area for update: /E is the switch for all servers; /A is for all servers in the site with your targeted server. Perhaps /E is a newer option in later versions of the tool.
Hi Evan,
I’m not sure if the /E is a newer option. I’m running all 2016 servers, I see it’s also available on Windows 10. Are you not seeing this /E option on older server versions (maybe server 2008)?
Very Nice information
and clear. Awessssssssooooommmme
If i was c.e.o
I would strongly Hire you
thanks a lot
Thanks, lee.
DC can run to Windows server 2012?
Thank you. very well explained.
No problem
Example 6: Use multiple switches (My favorite)
Here tare the commands I like to run. It will run all tests, displays all the details and outputs it to a file.
Believe this should be ‘Here are the commands……’
Great article thanks for putting it together!
Thanks for providing this information
No problem
Very Helpful Thank you
No Problem
just awesome
Thanks. I hope you found it useful.