Are you looking for a way to run Active Directory Users and Computer as a different user?
Then you’re in the right place.
It is a best practice for System Administrators to have at least two accounts, one with regular permissions and one with elevated permissions to perform administrative tasks.
This will increase security and reduce the risk of malicious attacks such as RansomWare.
Logging in with a regular account will require you to launch certain programs such as Active Directory Users and Computers as a different user.
In this tutorial, I’ll show you two different methods for running programs as a different user.
Method 1: Using RUNAS
In Windows 2000 Microsoft introduced the runas command. This command is designed to allow a user to run a specific program with a different account.
To use the runas command you just need to know the path to the program.
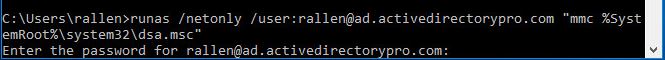
Here is the command to run Active Directory Users and Computers as a different user.
runas /netonly /user:username@domain "mmc %SystemRoot%\system32\dsa.msc"
Note: Change to your username and domain
It will prompt for a password
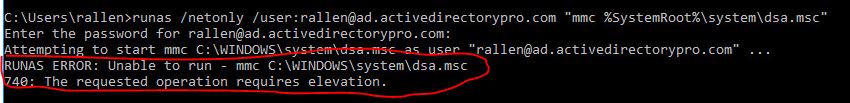
If you get the error below, it means you have UAC enabled. To work around this you will need to right click CMD and Run as administrator.
Now you might be thinking, that’s going to be a pain to type that command out every time to run ADUC.
Easy fix.
I can just put the command into a text file and save it as a .bat file (batch file).
Save the .bat file somewhere for quick access and then it’s just a click away to launch ADUC.
I saved mine to the desktop
You can use this method for other management consoles
Group Policy
runas /netonly /user:username@domain "mmc %SystemRoot%\system32\gpmc.msc"
DNS Management
runas /netonly /user:username@domain "mmc %SystemRoot%\system32\dnsmgmt.msc"
DHCP
runas /netonly /user:username@domain "mmc %SystemRoot%\system32\dhcpmgmt.msc"
AD Domains and Trusts
runas /netonly /user:username@domain "mmc %SystemRoot%\system32\domain.msc"
You get the idea, just find the path and plug it in.
Method 2: Creating shortcuts
This method is very similar to the first, we are just skipping the need to open the command prompt.
Basically, it’s creating shortcuts to the program using the run as command.
Right click the desktop or anywhere you want to create the shortcut.
The shortcut is the same as method one you just need to put the path to the runas.exe.
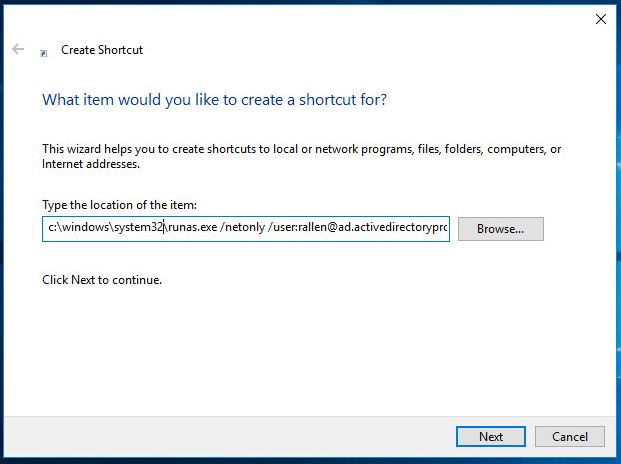
Click Next
Give the shortcut and name and click Finish
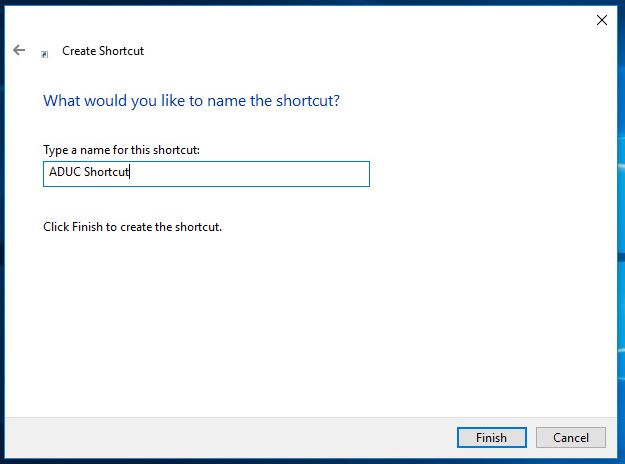
That is it for method two.
If you don’t like either of those methods there is a third option and that is to setup a secure admin workstation or terminal server.
Secure admin workstations are limited use systems designed to perform administrative tasks. The admin workstation should be locked down with no internet access and only the necessary tools installed to reduce the attack footprint.
There are some good documents from Microsoft on this, they are in depth. If you are serious about security I recommend you read them.
Protection High value assets with secure admin workstations
Privileged Access Workstations
To get started this is what I recommend and what I do in my environment.
- Setup a terminal server
- Install only needed admin tools (RSAT tools, putty, access to web consoles)
- No internet access on the terminal server
- Limit some systems to only be accessed by the IP address of the admin workstation
- Implement two factor authentication when connecting to admin workstations
Now when my team needs to perform an admin task they have to connect to the admin workstation. Depending on how you have accounts setup this would reduce what an attacker could do even if they compromise a privileged account. They would have to gain access to the admin workstation plus get around the two factor authentication.
Nothing is bulletproof but it’s a simple way to minimize risk.
Haven’t had to do these tasks in a while, so the article was a great refresher! One thing though, I found sometimes a command window gets left open if you launch these through a batch file. Easy fix is to add the command “exit” as the last line in the batch and that seems to take care of it.
Minor typo DNS management is not dsa.msc it is dnsmgmt.msc
Another cool trick is to built your own mmc console with the tools in it that you need (eg Users and computers, DNS and DHCP. to do this – run the mmc as the required user, add in the components you want and save it as myconsole.mmc. Put the file in Windows\system32 and create a batch script to use the newly creeated myconsole.mmc.
This has additional benefit that you can also save the console with predefined DNS and DHCP servers baked in.
Steve, I fixed the typo. Thanks for pointing that out. Great tip, I actually use this myself. I have a single mmc console for ADUC, DNS, DHCP, and group policy. It seems not a lot of people don’t know about this… I should probably add this tip to the article.
Steve, great suggestion, may I ask what happens if the required user has a password that rotates constantly and automatically (we use BeyondTrust)? Would that mmc still work?
You can also use a powershell script:
Set-ExecutionPolicy unrestricted
Start-Process “C:\Windows\System32\cmd.exe” -workingdirectory $PSHOME -Credential domain_name\domain_admin_account -ArgumentList “/c dsa.msc”
Thanks Kenny
Thank you for providing this clear and well-written tutorial.