In this tutorial, I’ll show you how to find service accounts in Active Directory using PowerShell and the AD Pro Toolkit.
Typically a service or scheduled task is configured to run as the local system account. But there are times when a domain user or local account is configured to run as the service. Lets check out some examples.
Find Service Accounts in Active Directory Using PowerShell
In this example, I’ll use the get-wmiobject cmdlet to list service accounts on a single computer
Step 1: Open PowerShell as Administrator.
Step 2: Copy and paste the command below. Change pc3 to your computers hostname.
get-wmiobject win32_service -comp pc3 | select name, status, startname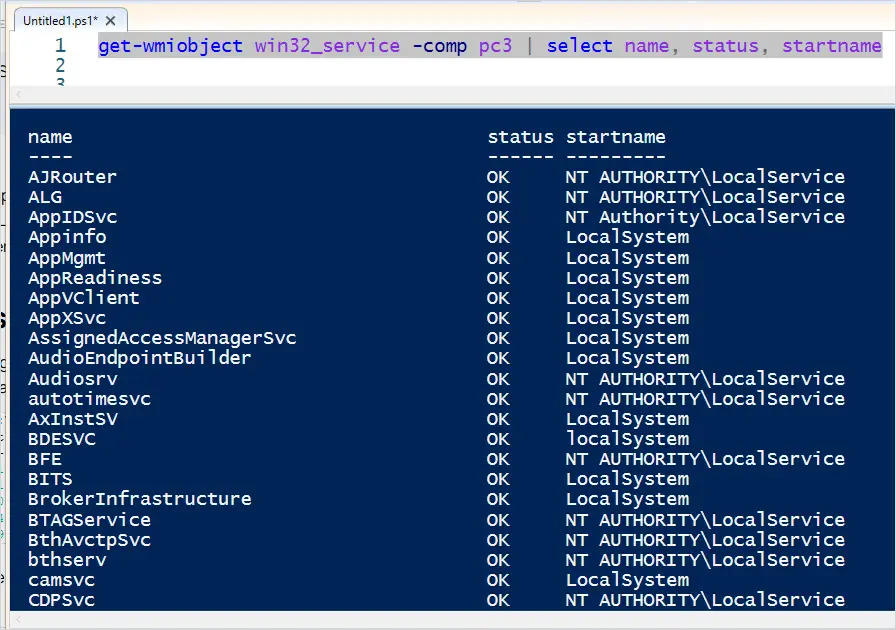
Option #2 Service Account Management Tool
In this example, I’ll use the Service Account Management Tool to create a report of service accounts on all computers
Step 1: Click “Run” to scan all computers or click “Browse” to select an OU or group.
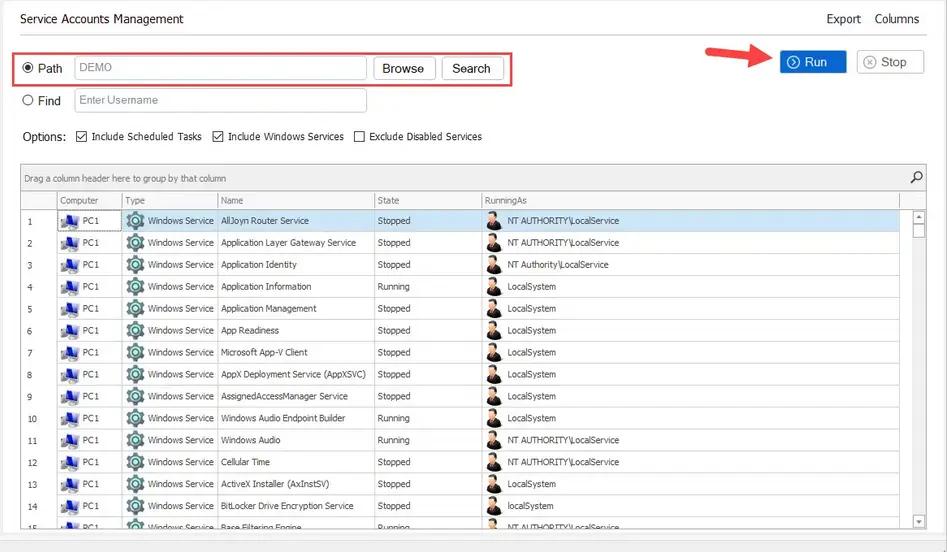
Step 2. Next, use the search box or grid filters to find specific service accounts.
Step 3. To export the report click the export button.
How to List All Service Accounts in the Domain
If you don’t document your service accounts then you could end up with them running on various servers or even computer systems. This situation is very difficult to manage and can be a security concern.
The only solution is to scan all your systems and find which ones have accounts being used to run a service. To simplify this you can use the service account management tool from the AD Pro Toolkit.
Step 1. Open the Service Accounts Management Tool
Click here to download a free trial
The tool is on the management tools page under computer tools.
Step 2. Scan Computers for Service Accounts
Select to scan all computers or select an OU or a specific computer.
In this example, I’ll scan all computers in the domain. If you don’t want to include scheduled tasks, uncheck the “include scheduled tasks” box. Click the Run button to start the scan.
When the scan is complete you will have a list of all the services running on your systems, the state, and which account the service is running as.
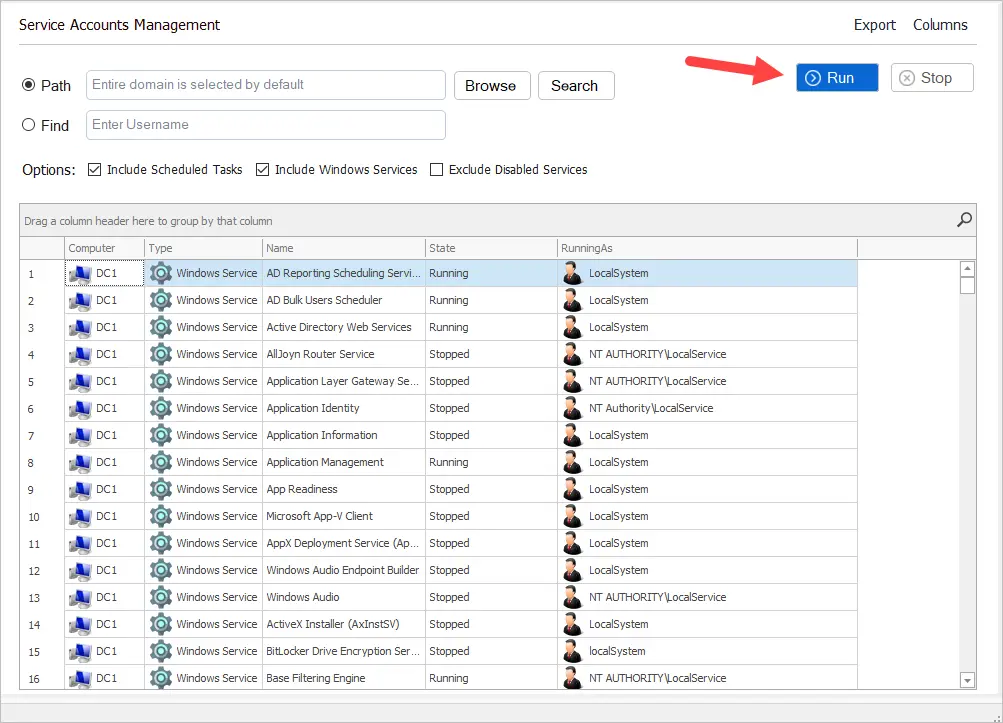
Step 3. Filter Service Accounts Report
To find specific service accounts you can filter the report or click the search icon. First, I’ll click on the RunningAs column and filter the report, I’m looking for domain user accounts that are runningAs.
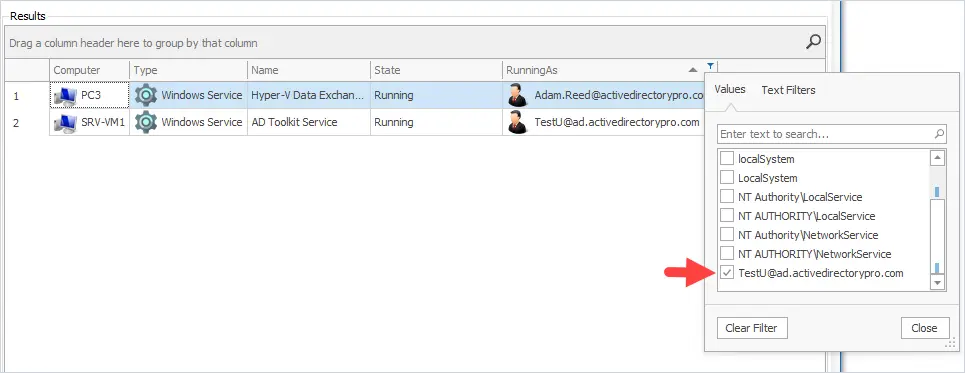
You can see in the screenshot above when I filter the results I found two domain accounts that are being used as service accounts, one is on PC3 and the other is on SRV-VM1.
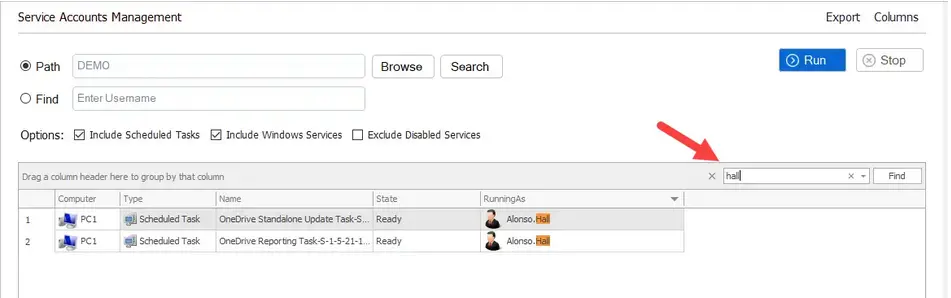
Another option is to use the search icon. For example, I’ll type my domain name and hopefully, it will find all domain accounts.
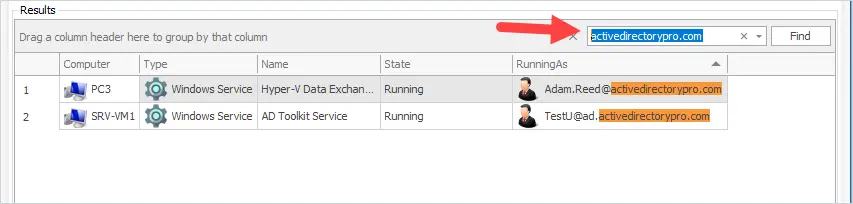
Awesome! The tool quickly found two domain user accounts set to run a Windows service.
How to search for a specific service account?
If you want to scan your computers for a specific service account, then use the find option.
In this example, I’ll scan all computers for the service account “adam.reed”.
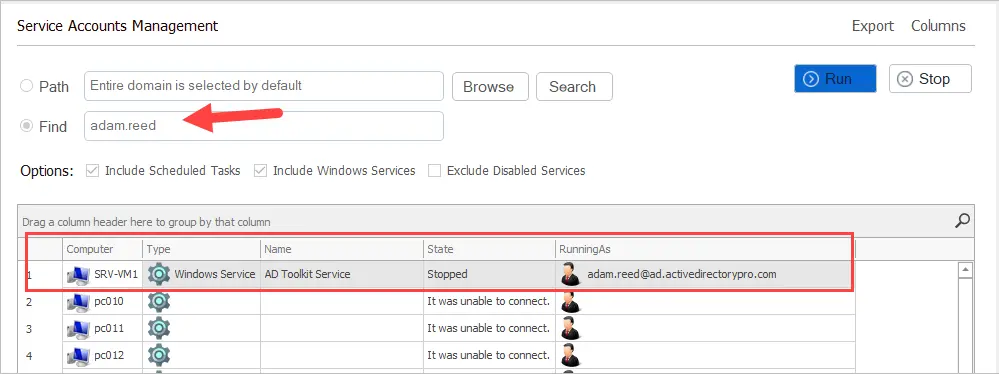
Very nice! This option works great when you know the name of the service account. Unfortunately, that is not always the case.
Powershell list service accounts
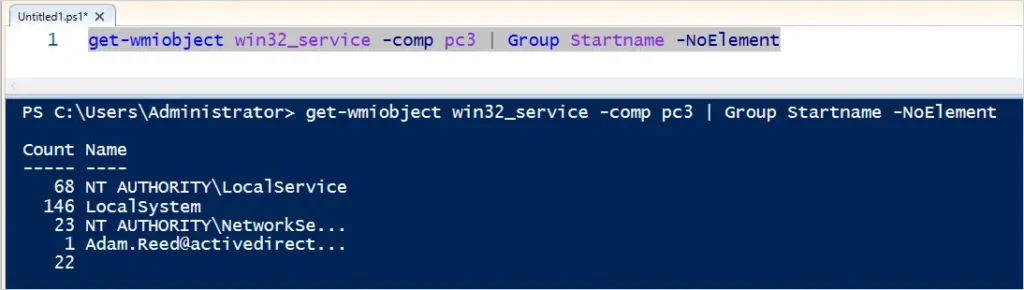
Here is a simple PowerShell command to find service accounts on a single computer.
get-wmiobject win32_service -comp pc3 | Group Startname -NoElementThis command will group the services by the startname, I think it makes it easier to read and get an overview of which accounts are running the service.
If you don’t want to group the results, use this command.
get-wmiobject win32_service -comp pc3 | select name, status, startname
To search for a specific account use this command. I’m doing a wildcard search for service accounts running as a domain user.
get-wmiobject win32_service -comp pc3 -filter "startname like '%activedirectory%'" | select name, status, startname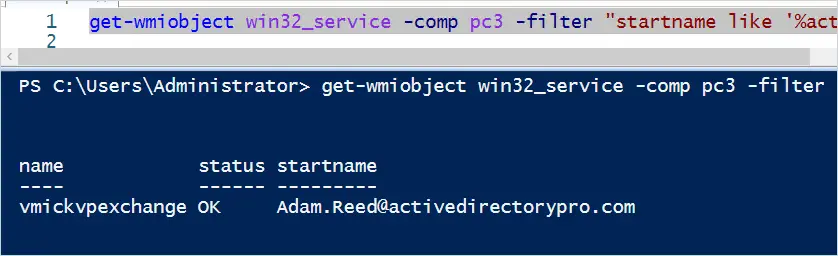
List all service accounts in Active Directory
In this tutorial, I’ve been referring to service accounts as normal domain user accounts. In this scenario, there is no easy way to list all service accounts unless you have documented or implemented a naming convention for them.
Below is what Microsoft says about on-premises service accounts.
We recommend that you add a prefix such as “svc-” to all accounts that you use as service accounts. This naming convention will make the accounts easier to find and manage. Also consider using a description attribute for the service account and the owner of the service account. The description can be a team alias or security team owner.
https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/service-accounts-on-premises#find-on-premises-service-accounts
In addition to adding a prefix, I would create an OU just for service accounts. You may have existing service accounts that you cannot add a prefix to, so by putting them all into an OU you can easily list all service accounts in Active Directory.
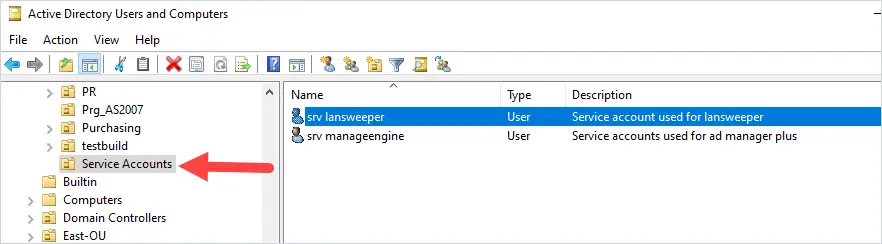
Another option to list all service accounts, is to check the local policy settings. When an account is configured to run as a service, the account will be granted log on as a service rights.
You would need to open the local group policy on each system and check the user rights assignment.
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment – > Log on as a service.
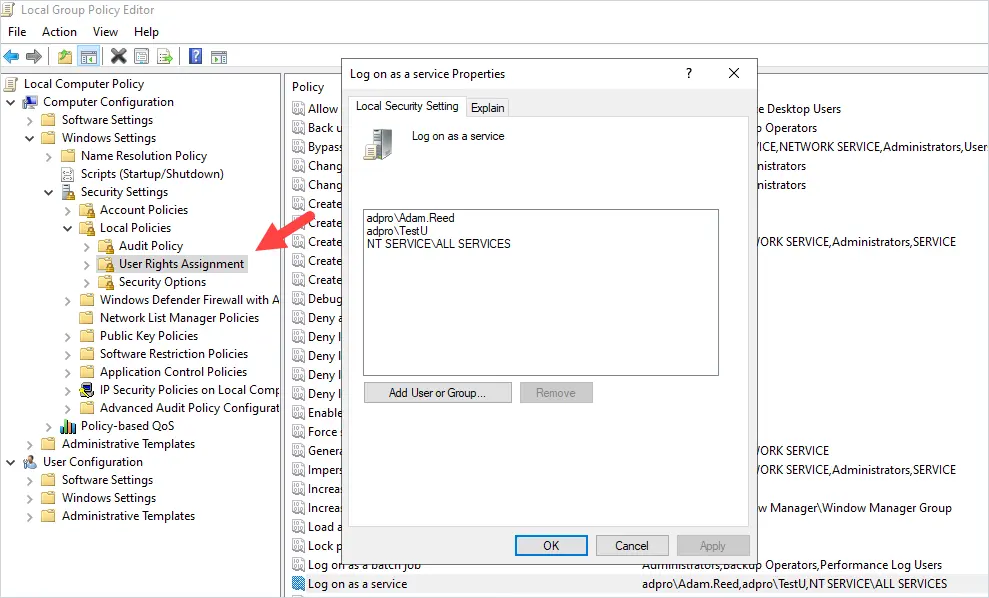
You can see above, I have two domain accounts that have been granted the log on as a service right. Unfortunately, there is no easy way to query this on all computers. It would be easier to use the service accounts report tool or PowerShell to query all computers.
Conclusion
In this tutorial, I showed you two methods for finding where service accounts are being used. By using PowerShell you can easily list all the service accounts on a single computer, but it is challenging for multiple computers. To easily scan all computers I recommend using the service accounts reporting tool from the AD Pro Toolkit. This GUI tool lets you query all computers for domain service accounts, filter the results and export the accounts to a CSV file.