In this article, you will learn how to get members of the local administrators group using PowerShell and the AD Pro Toolkit.
Users that are a member of the local administrators group have full control over their computer. This allows users to install unwanted software, change computer settings, and makes it easier for viruses and malicious software to be installed. It also makes it easier for hackers to take control of your computer.
In this article:
- Get Local Administrators using PowerShell
- Get Local Administrators using PowerShell (Multiple Computers)
- Get Members of Local Administrators group with AD Pro Toolkit
- Get Members of All Local Groups using AD Pro Toolkit
Get Local Administrators using PowerShell
Use the Get-LocalGroupMember cmdlet to get members of the local administrator group.
Get-LocalGroupMember -Group "Administrators"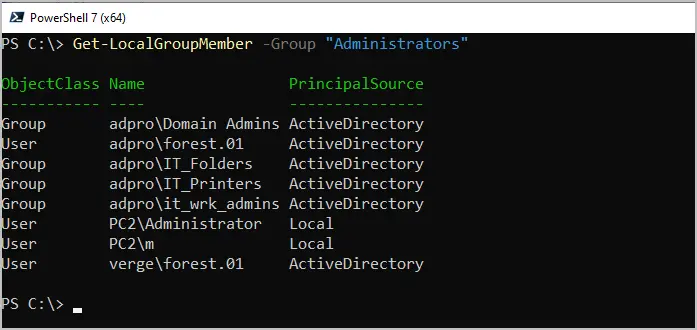
In the above screenshot, you can see I have several groups and users that are a member of the local administrators group. It even shows members that are part of another domain.
Get Local Administrators using PowerShell (Multiple Computers)
To get the local administrators on multiple computers you need to have PowerShell Remoting enabled.
When PowerShell Remoting is enabled you can then use the Invoke-Command to get the local administrator on multiple computers. To run this command on multiple computers just separate them with a comma. Here is an example of running this command on computers with the hostname of PC1 and PC2.
Invoke-Command -ComputerName pc2, pc1 -ScriptBlock {Get-LocalGroupMember -Name 'Administrators'}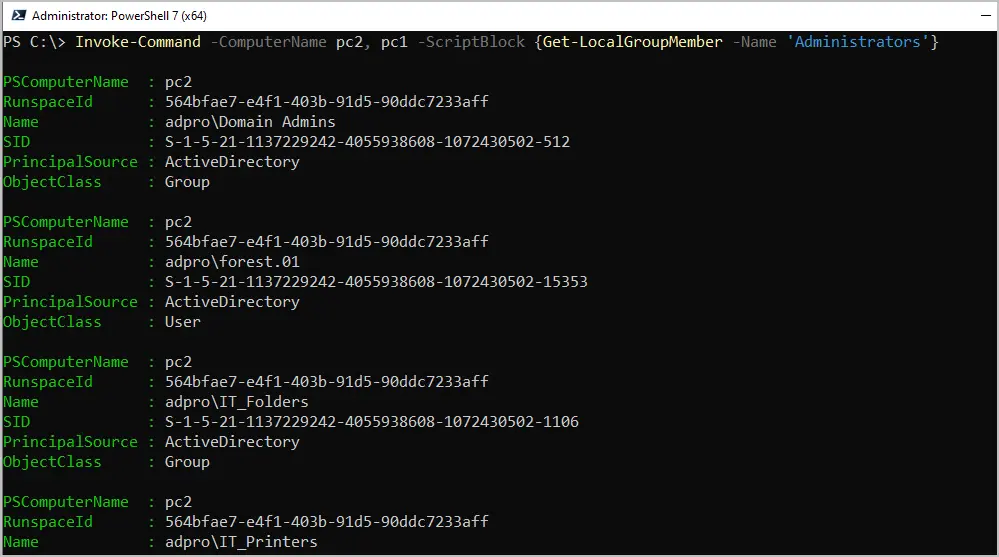
You can see in the above screenshot the output is not ideal and would require some additional work. This is why I created the AD Pro Toolkit, it makes scanning multiple computers for local admins very easy and the output is simple to read.
Get Members of Local Administrators group with AD Pro Toolkit
The AD Pro Toolkit makes it very easy to get local administrators on multiple computers. It also puts the results into a grid view to make the report easy to read, search, filter and export.
Requirements:
WMI needs to be allowed on the Windows Firewall Settings. If you have this blocked you can use group policy to open this up on all computers.
Step 1: Open Local Admins Report Tool
Click on “Security Tools” and then “Local Admins Report”
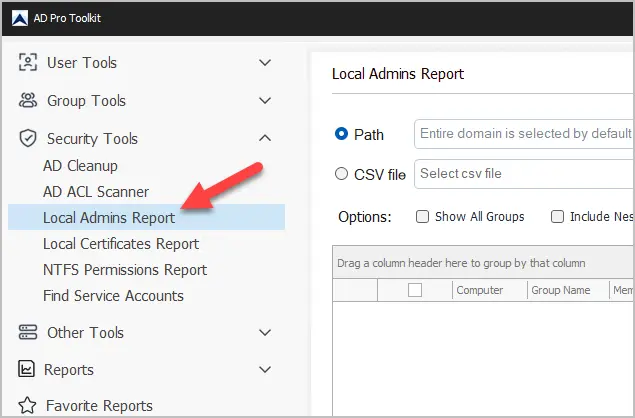
Step 2: Select Computers
- Path = Scan the entire domain or choose an OU or group.
- CSV file = Provide a list of computers to scan.
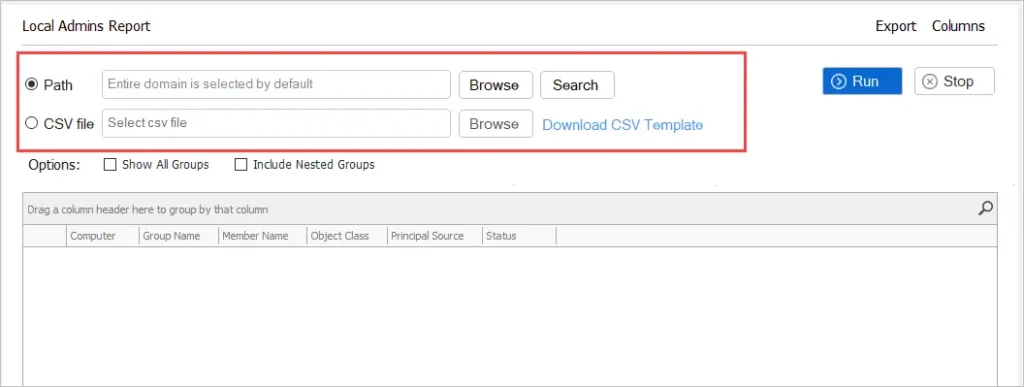
Step 3: Click Run
Now just click the run button to start scanning the computers.
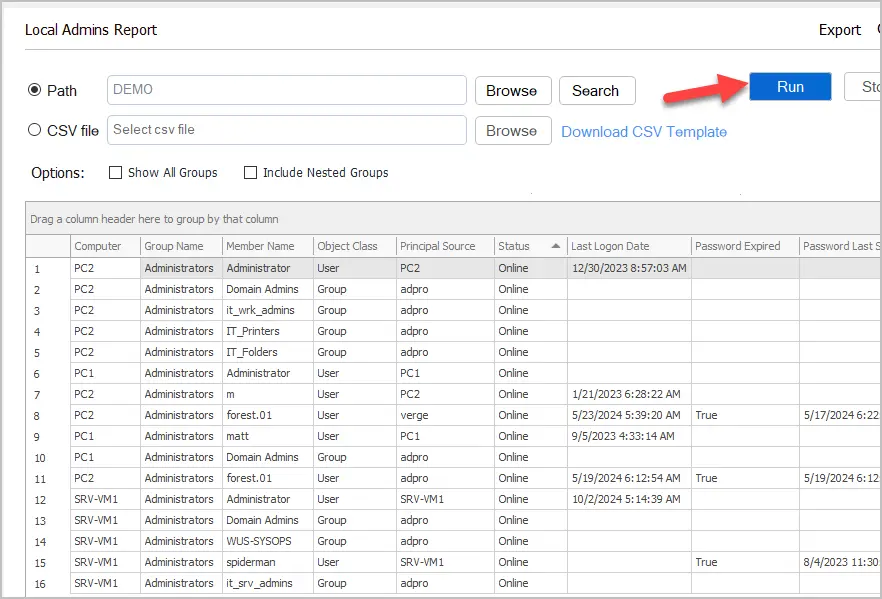
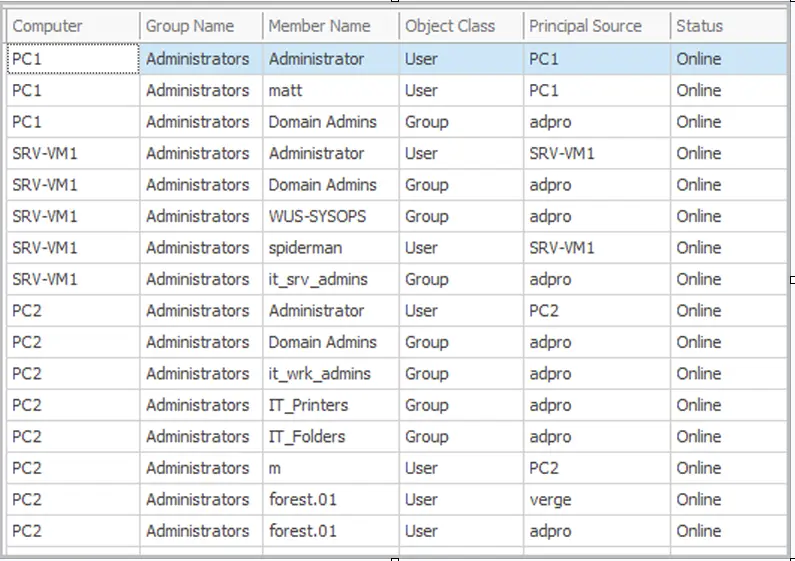
You can see in the above screenshot, I have several users and groups that are a member of the local Administrators group on multiple computers. The Principal Source column will tell you if the account is a local account or a domain account.
Step 3: Export Report
To export the list of local administrators click the “Export” button.
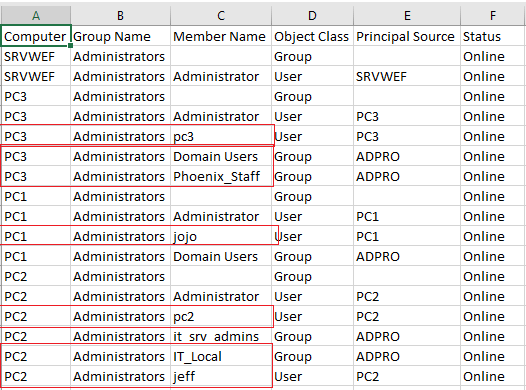
Now you will have a report of all local administrators on all computers. In the screenshot below I highlighted some accounts that should not have admin rights. I’ll need to investigate these computers.
CSV Sample export
Get Members of All Local Groups using AD Pro Toolkit
By default, this toolkit gets the members of the Administrators group only. If you want to get a report of all local groups then select the “Show All Groups” box.
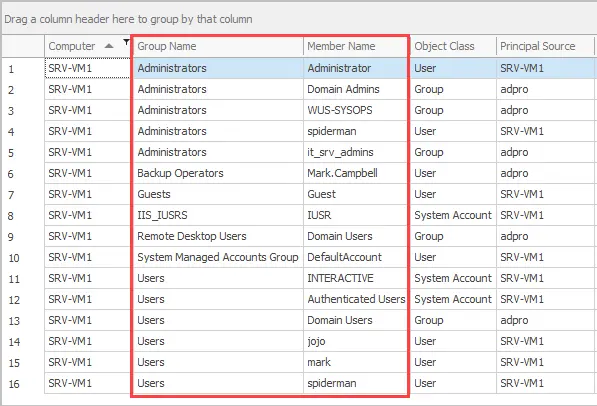
Here is a screenshot show all the local groups and members on my srv-vm1 server.
Download AD Pro Toolkit and try this tool for free.
I’ve just shown you two methods for finding administrator rights. Now you need to identify the users that do not need these rights and remove them.
The best way to remove local administrator rights is to use group policy and Restricted groups. Restricted groups allow you to centrally manage the local groups on all computers in your domain. You can also target specific computers or OUs instead of the entire domain.


If I have an exception list to the local admins, how can I factor that into the powershell ?
Hello,
Can you help me?
I have a problem with administrator local account.
Now, I can get it from computers in domain. But it enabled and disabled account.
Is there any way to only get administrator local account is still enable.
Thank for your advice.
Hello,
If I have 500 computes or server so in this case how I can export that reports.
With the toolkit just click the export button to export the report to CSV.
With PowerShell use export-csv
Invoke-Command -ComputerName pc1, pc2 -ScriptBlock{Get-LocalGroupMember -Name ‘Administrators’} | Export-Csv c:\it\export.csv
very cool, but you should mention that using the AD pro toolkit tool with the trial version you can only see 10 results at a time, not the whole results.
Good point, I’ll add that to the article.
NET USER Administrator is perfect to check the status, is there any command which can show the results for multiple computers and can we export them into .csv file ?
You can do it with PowerShell
Invoke-Command -ComputerName pc1 -ScriptBlock{Get-LocalGroupMember –
Name ‘Administrators’}
Nicely explained! Thanks.
No Problem 🙂