In this guide, I’ll show you how to find bad password attempts in Active Directory using PowerShell and the AD Pro Toolkit.
Reasons to check for bad password attempts in Active Directory:
- Identify password spraying attempts or brute force attacks on user accounts.
- Troubleshooting and resolving user account lockout issues.
- Generate Active Directory Reports for auditing and security assessment.
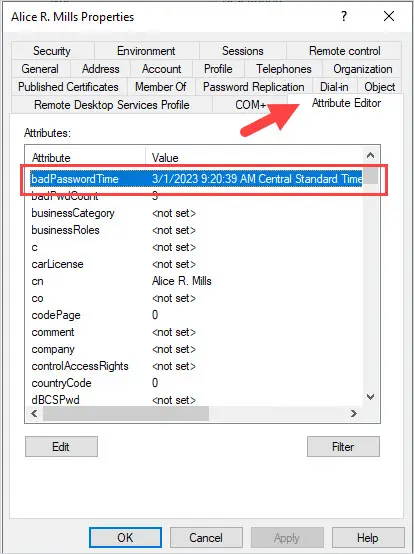
When an AD user account tries to authenticate with a bad password it stores the time in the attribute badPasswordTime. It also increases the badPwdCount attribute value. You can see these values by clicking on the Attribute Editor.
Employees enter their passwords incorrectly all the time, this is no concern. But seeing a large number of employees with bad password attempts in a short period of time is a concern. This could mean a hacker is using a brute force attack at trying to guess users passwords. It is critical you have a proper password policy and account lockout policy configured to mitigate brute force attacks.
Now let’s check out some ways to view and automate finding bad password attempts in your network.
Find Bad Password Attempts using PowerShell
Use the command below to get the bad last bad password attempt and bad password count value using PowerShell.
get-aduser -Identity robert.allen -Properties * | select name, badPwdCount, LastBadPasswordAttempt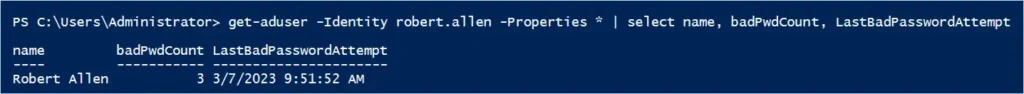
In the screenshot above, you can see the account robert.allen has 3 for bad password count and the last bad password attempt was 3/7/2023 at 9:51 AM.
Find Bad Password Attempts for all users in Active Directory
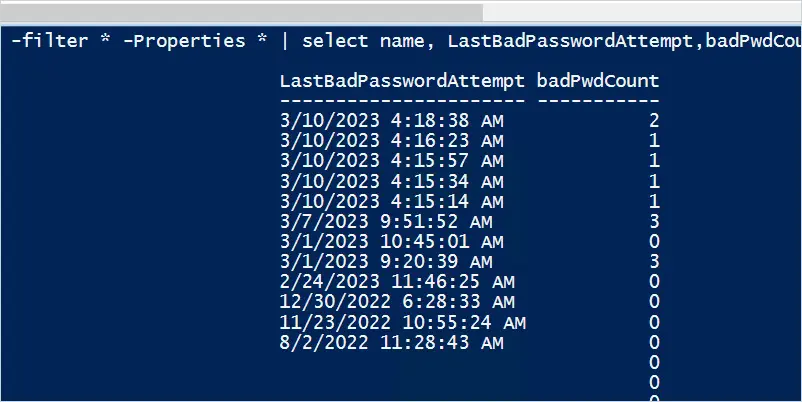
To get all the user’s last bad password attempts use the following command.
get-aduser -filter * -Properties * | select name, badPwdCount, LastBadPasswordAttempt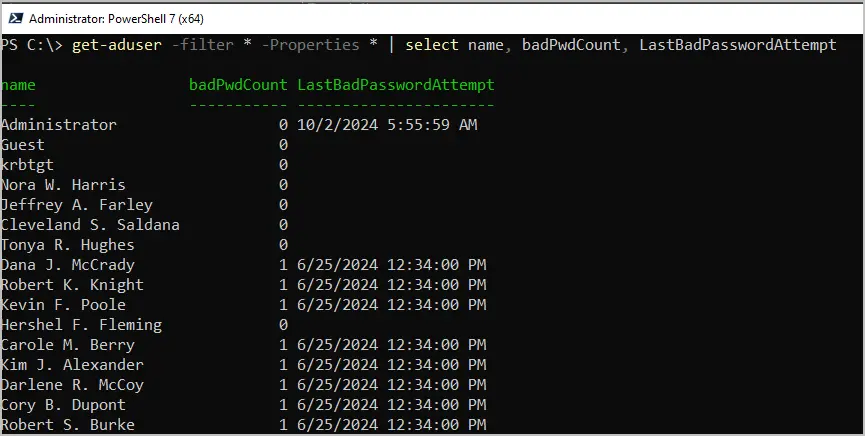
Easily Find Bad Password Attempts using the AD Pro Toolkit
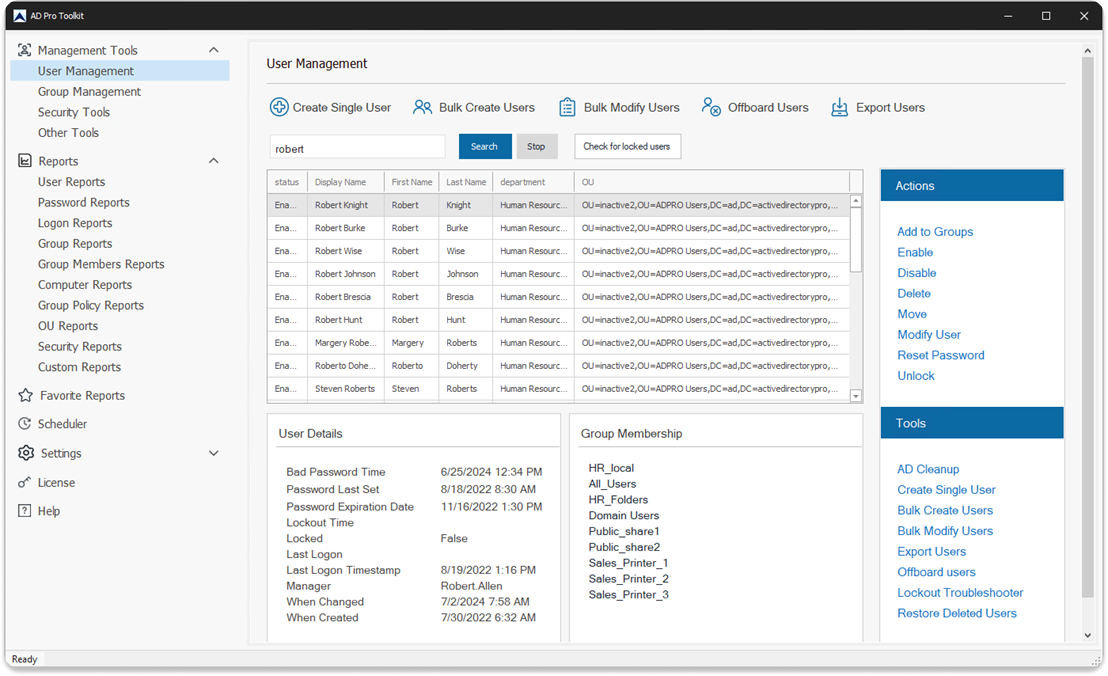
The AD Pro Toolkit has several built-in password status reports. You can get a report of bad password attempts in the last 1, 7, 30 days or a custom time range.
You can download a free trial here.
Click on Users Reports -> Password Reports.
By default, it will find bad password attempts in the last 30 days.
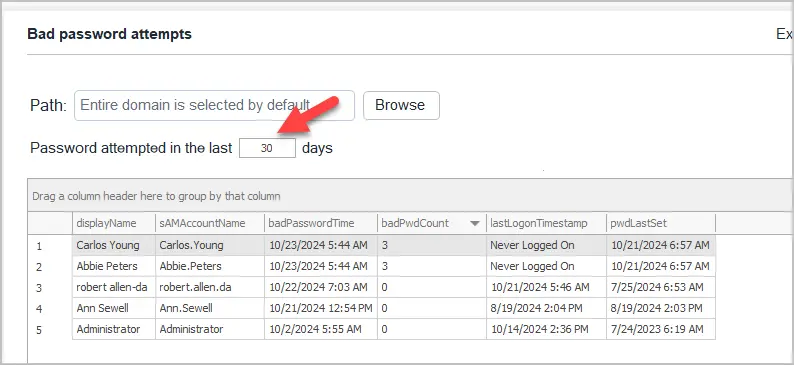
This report can be very useful to audit for suspicious logon attempt activity.
If you see a large number of users with bad password attempts with increasing badPwdCount, this needs to be investigated.
Automate Bad Password Attempts Report
Manually checking for bad password attempts on a daily basis is inefficient. It is better to automate this report in case you forget and it will also save you time.
To automate this report you can use the task scheduler to get a daily, weekly, or monthly report emailed to you.
Click on Scheduler and then click the Add button.
Select Reports
Enter a task name. For example, Bad Password Attempts.
For credentials click on Set and enter your account details.
Click Next.
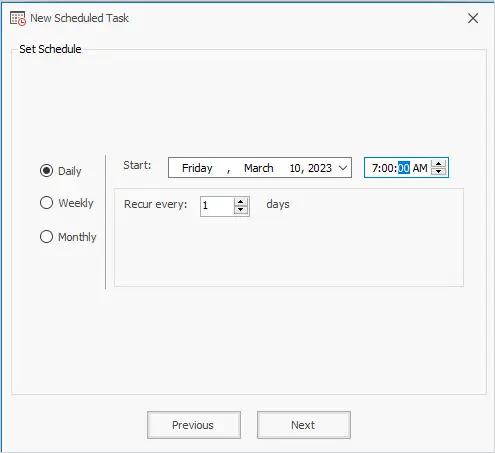
Set the schedule. Choose from Daily, Weekly, or Monthly.
In this example, I’ve set it to run daily at 7:00 AM.
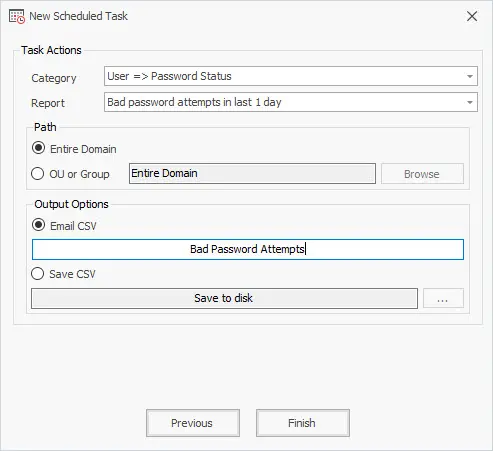
On the last screen for category select User -> Password Status
Then select the report you want to automate. In this example, I’ll select “Bad password attempts in last 1 day.
Next, choose the path. You can choose from the entire domain or select an OU or group.
For the output enter an email subject.
Click Finish.
That completes the steps for creating an automated report. You will now get an email according to the schedule you selected that includes a CSV report.
In this article, I showed you two options to check for users with bad password attempts. The bad password time is stored in an Active Directory attribute when a user enters their password incorrectly. You can easily get the bad password time and count by using PowerShell. I also showed you how to automate the bad password report by using the AD Pro Toolkit. The toolkit includes over 200 built-in AD Reports for users, computers, groups, and group policy. Click the button below to download a free trial of the AD Pro Toolkit.
Download Free Trial