In this tutorial, you will learn how to enable the Active Directory Recycle bin on Windows Server.
I’ll show you how to enable it using the Windows Server Manager or with PowerShell.
The AD recycle bin is a must have feature that allows you to quickly restore deleted Active Directory Objects (users, computers, groups, OUs and more).
Note: The AD Recycle bin is not enabled by default, you must explicitly enable it.
Steps to Enable the AD Recycle Bin on Windows Server
Note: Once you enable the Active Directory Recycle Bin you can’t disable it.
Follow these simple 3 steps:
Step 1: Open Server Manager
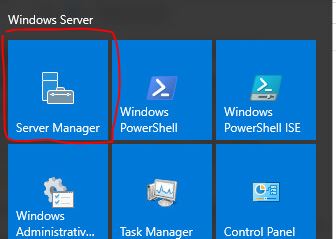
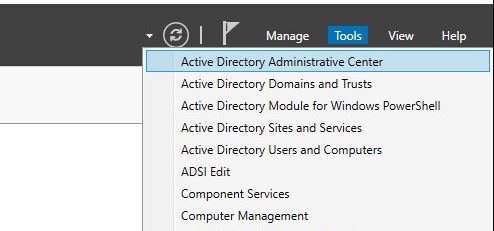
Step 2: Open the Active Directory Administrative Center
From the Server Manager go to tools and select Active Directory Administrative Center
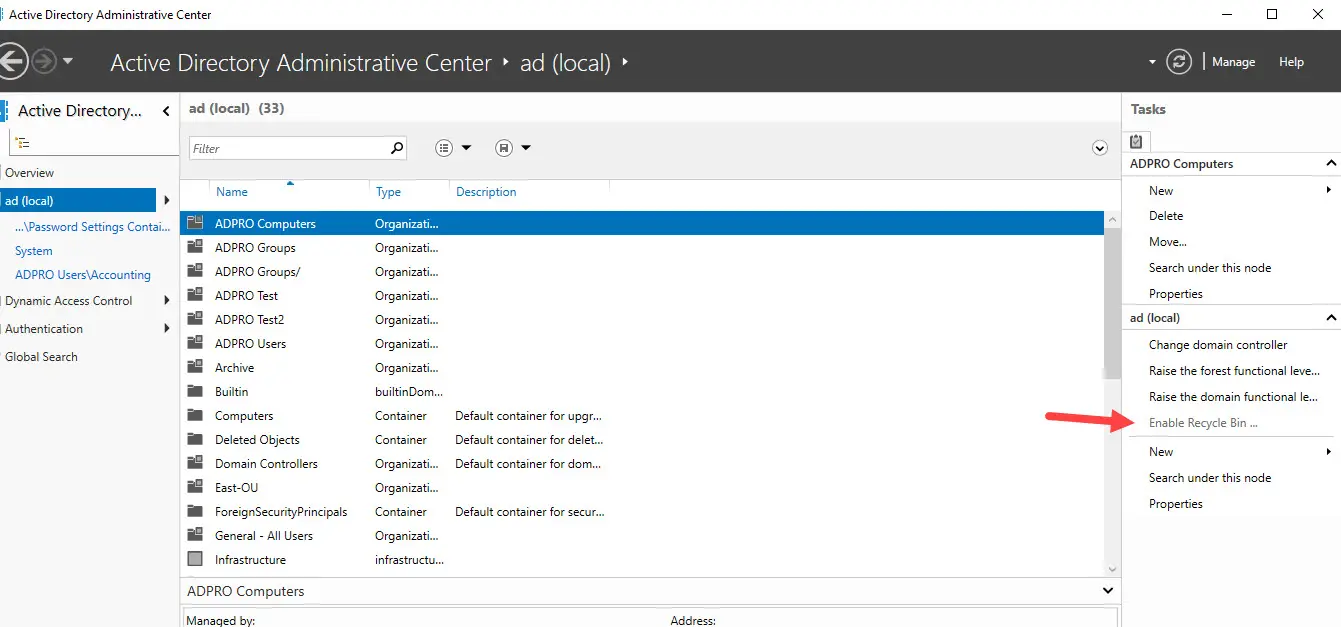
Step 3: Enable Recycle Bin
Within the Active Directory Administrative Center click on your local domain then click on “Enable Recycle Bin”
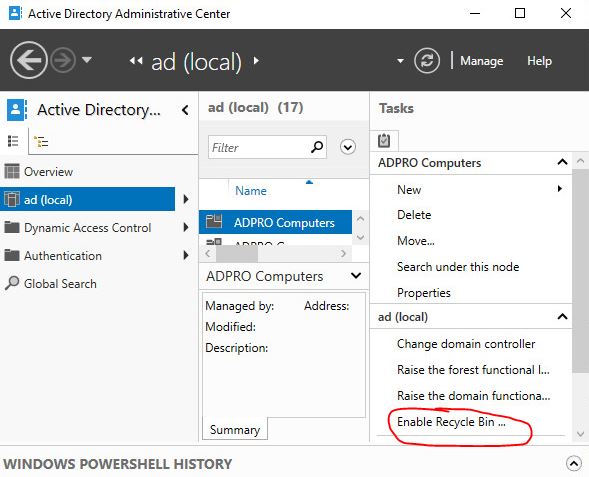
Click OK to confirm
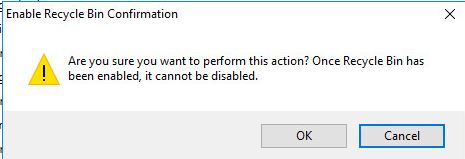
Click OK on the next pop up
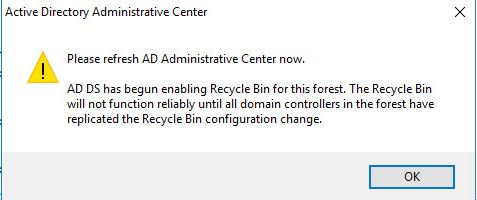
All done, AD recycle bin is now enabled.
Enable AD Recycle Bin with PowerShell
Follow these steps to enable the AD recycle bin with PowerShell
Step 1. Logon to your Domain Controller
Step 2: Load the AD Powershell module
Import-module ActiveDirectory
Step 3: Run the following cmdlet to enable the Recycle Bin
Enable-ADOptionalFeature 'Recycle Bin Feature' -Scope ForestOrConfigurationSet -Target <your forest root domain name>
Here is an example using the ad.activedirectorypro.com domain.
Enable-ADOptionalFeature 'Recycle Bin Feature' -Scope ForestOrConfigurationSet -Target ad.activedirectorypro.com
How to Check if AD Recycle Bin is enabled
Step 1. Open PowerShell
Step 2. Run the below command
Get-ADOptionalFeature -Filter 'Name -like "Recycle Bin*"'
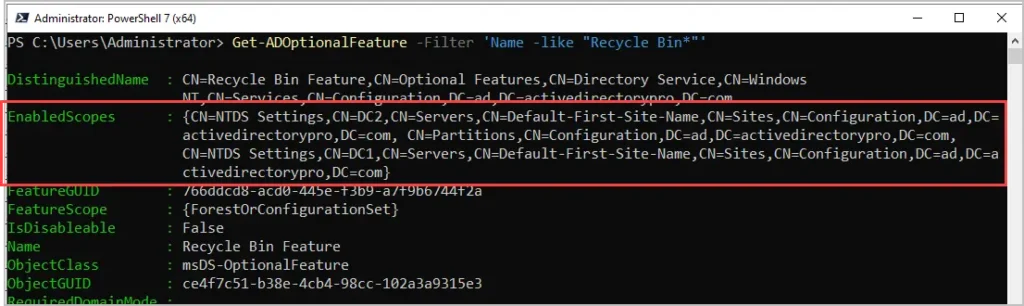
This command will return information about the Recycle Bin feature, look for the EnabledScopes property in the output.
If the AD Recycle Bin is enabled, the EnabledScopes will show the distinguished name of your forest. Example below.
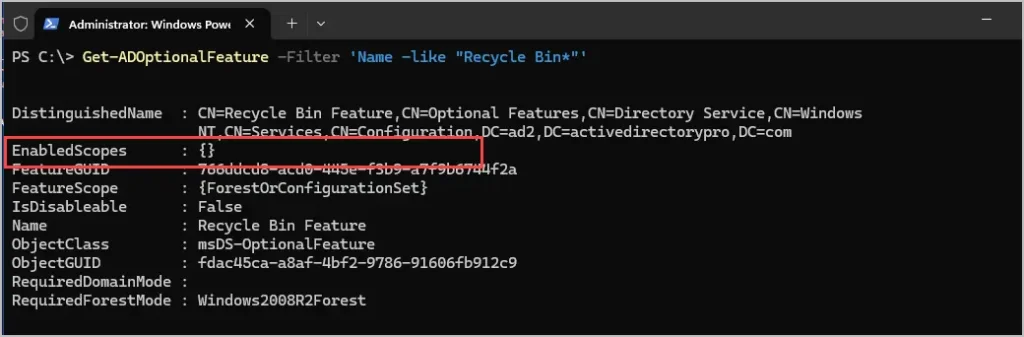
If the AD Recycle Bin is not enabled, the EnabledScopes will be empty like the below screenshot.
Active Directory Recycle Bin Benefits
The AD Recycle bin allows you to quickly recover deleted objects without the need to restore an Active Directory backup.
- Fast Recovery: With the AD recycle bin enabled, you can quickly restore a deleted Active Directory objects without 3rd party software. It is a huge time saver.
- Preserves object settings: The recycle bin feature preserves all link valued and non link valued attributes. This means that a restored object will retain all its settings when restored (attributes and group membership).
- Easy to use: The AD Recycle bin makes it easy to restore deleted objects. Using the Active Directory Administrative center you click on Deleted Objects, select the account and click restore.
- No Downtime: Restoring a deleted object requires no downtime or server reboots. You can restore AD Objects with no service interruptions.
- Its Free: The AD Recycle Bin is included with Windows Server at no additional cost.
- Retention time: By default, a deleted object can be restored within 180 days. This time is controlled by the Deleted Object Lifetime (DOL) which can be set on the msDS-deletedObjectLifetime attribute.
- Reduces dependency on 3rd party backups: First let me say you should still have a full backup of AD, either using the Windows backup feature or 3rd party software. The AD Recycle Bin reduces the need of traditional backups when all you need to do is restore a deleted object.
If you want a deeper dive into these settings, then check the AD Recycle Bin guide from Microsoft.
This is great, Robert. However, Can you show me how to permanently delete users or objects from the Recycle Bin? The delete option is greyed out.
Are there any downsides/negatives of enabling the recycle bin. Reason for asking is because it says once enabled it cannot be disabled. Thanks
I’m not aware of any downsides to turning this on.
If you enable on erver 2008 or 2012, you cannot elevate the function level of the domain to 2016 (on 16, 19 or 22).
I’ve tried to see if there’s a valid reason for this, but there doesn’t appear to be, and no fix at this time.
All DCs must be >= the desired functional level. A domain with a DC running 2008 cannot elevate past 2008. Same with 2012. There is no 2019 nor 2022 functional level. Hope this helps.
the only consideration is that should pay attention to server free storage space, as creating recycle bin will require some space on all DCs.
Nice Article thanks Alot!
Awesome and useful! Appreciated
No problem
Thank you!
Thank you! This helps a lot!
Wow , So easy to understand through this page. Thanks and Keep going.
Thanks Nikki. More tutorials on the way. I’m planning to add more video tutorials for Active Directory tasks. Stay tuned.
Lifesaver 🙂
Great
Helpful dude.. Thanks a lot
very gooooooooooooood,thank you
You’re welcome, bahamin.