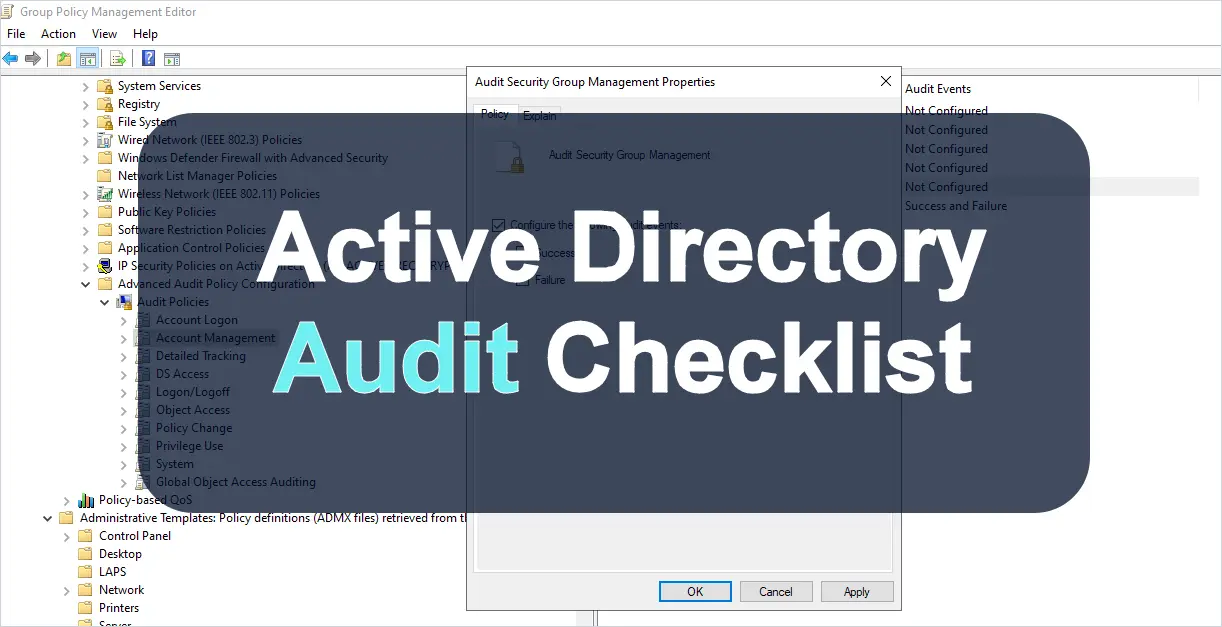
To properly Audit Active Directory you must have the right policy settings enabled. These policy settings ensure your domain controllers are logging security events that meet your compliance and audit requirements.
The challenge is there are many audit policy settings to choose from which can be overwhelming and leave gaps in your auditing needs.
I have created a simple Active Directory Audit Checklist that you can download to use as a quick reference. This checklist will show you which audit settings to enable and the policy setting. These settings are taken from the Microsoft security compliance checklist. When using an Active Directory Audit Tool these policy settings will be required so your domain controllers can generate logs for the tool to analyze.
Active Directory Audit Policy Checklist
Free Audit Policy Checklist.
Active Directory Pro has created an audit policy checklist reference guide.
This free PDF can be used as a reference guide that shows you the recommended audit policy settings for Active Directory. These settings use the Microsoft security baseline recommendations.
The audit policy settings in this guide need to be configured in the Default Domain Controllers Policy GPO.
Policy Location:
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration
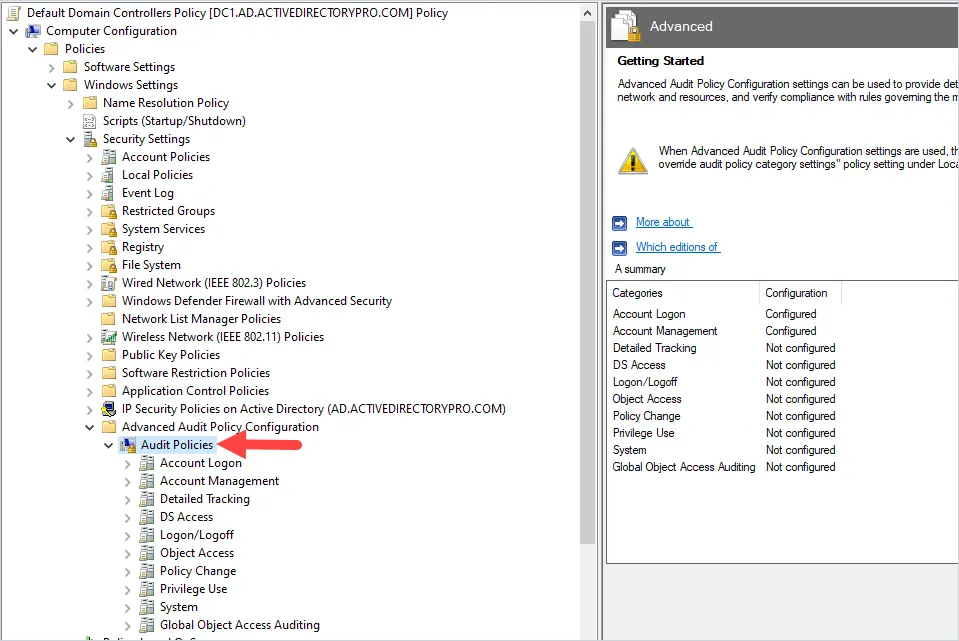
Below are the recommended settings for the Advanced Audit Policy Configuration.
Account Logon
| Name | Policy Setting | Description |
|---|---|---|
| Audit Credential Validation | Failure | This policy setting allows you to audit events generated by validation tests on user account logon credentials. |
| Audit Kerberos Authentication Services | Failure | This policy setting allows you to audit events generated by Kerberos authentication ticket-granting ticket (TGT) requests. |
| Audit Kerberos Service Ticket Operations | Success and Failure | This policy setting allows you to audit events generated by Kerberos authentication ticket-granting ticket (TGT) requests submitted for user accounts. |
Account Management
| Name | Policy Setting | Description |
|---|---|---|
| Audit Computer Account Management | Success | This policy setting allows you to audit events generated by changes to computer accounts such as when a computer account is created, changed, or deleted. |
| Audit Other Account Management Events | Success | This policy setting allows you to audit events generated by other user account changes that are not covered in this category, such as the following: |
| Audit Security Group Management | Success | This policy setting allows you to audit events generated by changes to security groups such as the following: |
| Audit User Account Management | Success and Failure | This policy setting allows you to audit changes to user accounts |
Detailed Tracking
| Name | Policy Setting | Description |
|---|---|---|
| Audit PNP Activity | Success | This policy setting allows you to audit when plug and play detects an external device. |
| Audit Process Creation | Success | This policy setting allows you to audit events generated when a process is created or starts. The name of the application or user that created the process is also audited. |
DS Access
| Name | Policy Setting | Description |
|---|---|---|
| Audit Directory Service Access | Failure | This policy setting allows you to audit events generated when an Active Directory Domain Services (AD DS) object is accessed. |
| Audit Directory Service Changes | Success | This policy setting allows you to audit events generated by changes to objects in Active Directory Domain Services (AD DS). Events are logged when an object is created, deleted, modified, moved, or undeleted. |
Logon/Logoff
| Name | Policy Setting | Description |
|---|---|---|
| Audit Account Lockout | Failure | This policy setting allows you to audit events generated by a failed attempt to log on to an account that is locked out. |
| Audit Group Membership | Success | This policy allows you to audit the group memberhsip information in the user’s logon token |
| Audit Logon | Success and Failure | This policy setting allows you to audit events generated by user account logon attempts on the computer. |
| Audit Other Logon/Logoff Events | Success and Failure | This policy setting allows you to audit other logon/logoff-related events that are not covered in the “Logon/Logoff”. |
| Audit Special Logon | Success | This policy setting allows you to audit events generated by special logons such as those with administrator equivalent privileges. |
Object Access
| Name | Policy Setting | Description |
|---|---|---|
| Audit Detailed File Share | Failure | This policy setting allows you to audit attempts to access files and folders on a shared folder. |
| Audit File Share | Success and Failure | This policy setting allows you to audit attempts to access a shared folder. |
| Audit Other Object Access Events | Success and Failure | This policy setting allows you to audit events generated by the management of task scheduler jobs or COM+ objects. |
| Audit Removable Storage | Success and Failure | This policy setting allows you to audit user attempts to access file system objects on a removable storage device. A security audit event is generated only for all objects for all types of access requested. |
Policy Change
| Name | Policy Setting | Description |
|---|---|---|
| Audit Audit Policy Change | Success | This policy setting allows you to audit changes in the security audit policy settings. |
| Audit Authentication Policy Change | Success | This policy setting allows you to audit events generated by changes to the authentication policy |
| Audit MPSSVC Rule-Level Policy Change | Success and Failure | This policy setting allows you to audit events generated by changes in policy rules used by the Microsoft Protection Service (MPSSVC) |
| Audit Other Policy Change Events | Failure | This policy setting allows you to audit events generated by other security policy changes that are not audited in the policy change category |
Privilege Use
| Name | Policy Setting | Description |
|---|---|---|
| Audit Sensitive Privilege Use | Success and Failure | This policy setting allows you to audit events generated when sensitive privileges (user rights) are used. |
System
| Name | Policy Setting | Description |
|---|---|---|
| Audit Other System Events | Success and Failure | This policy setting allows you to audit systems events such as the startup and shutdown of the Windows firewall. |
| Audit Security State Change | Success | This policy setting allows you to audit systems events such as the startup and shutdown of the Windows firewall. |
| Audit Security System Extension | Success | This policy setting allows you to audit events related to security system extensions or services |
| Audit System Integrity | Success and Failure | This policy setting allows you to audit events that violate the integrity of the security subsystem |
When you have these Windows audit policy settings enabled, the Active Directory Logs will be generated on your domain controllers. These logs can be viewed using the Windows event viewer but it is recommended to use an auditing tool to analyze them. By using the provided audit policy checklist you can ensure you have the policy settings enabled to perform auditing on your domain controller.