Lesson 1 – How Does Active Directory Work
In this lesson, I’ll explain how Active Directory works by walking through three examples with diagrams.
Lesson 2 – Active Directory Domain Services
Active Directory Domain Services (AD DS) is the main component of Active Directory. Learn about AD DS and its related services.
Lesson 3 – Active Directory Benefits
In this lesson, you will learn the benefits of Active Directory, including examples with network diagrams.
Lesson 4 – Management Tools
Learn about the tools used to Management Active Directory and its related technologies.
Lesson 5 – Other Active Directory Services
Brief description of the other Active Directory services such as LDAP, certificate services, and federation services.
Lesson 6 – Azure Active Directory
In this lesson, you will learn about Azure Active Directory and how it is different from Active Directory Domain Services.
Lesson 1
How Does Active Directory Work
Active Directory was first released with Windows Server 2000. Its primary function is to provide authentication and authorization to users on the network.
- Authentication is the process where Active Directory verifies a user’s credentials (username and password). The user’s credentials are stored in the Active Directory database.
- Authorization is the process that grants or denies a user to do something such as edit a file or access an application.
Since its release, Microsoft has added additional services to Active Directory, more on this in lesson 6. The topic of Active Directory can be very complex as there are many services and components that make it work. Just remember its core function is to authenticate and authorize users to network resources.
Even though there has been a big push to move everything to the cloud, Active Directory is still used by most medium and large organizations. A lot of organizations use Office 365 and cloud services and operate in a hybrid mode. This means the local Active Directory is synced with the cloud to provide seamless authentication to Office 365 resources such as email.
To better understand how Active Directory works let’s look at some examples. These examples provide a high-level overview of how Active Directory works.
Example 1 – Authenticate Users
Jim was recently hired as an accountant for Active Directory Pro. The IT administrator creates an account for Jim in Active Directory, the account is unique to Jim and contains details such as first name, last name, office, phone number, etc. Jim is provided with a username and password so he can log into the company’s network.
- Jim logs into his laptop with the provided username and password.
- The logon request goes to the Active Directory server to verify Jim’s username and password.
- Active Directory looks up Jim’s account and verifies the username and password. The account has been verified.
- Jim is now logged into his laptop and is authenticated to the domain.
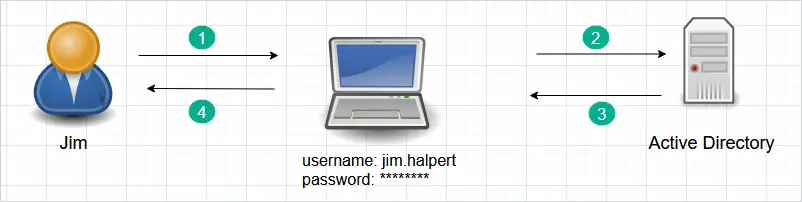
Example 2 – Authorize User (grant or deny permissions)
In this example, the Active Directory server will authorize access to network resources.
- Jim logs into his computer using his username and password and wants to access his email, a contract file, and the accounting database server.
- These network resources check with Active Directory to see if Jim’s account is authorized for access.
- Active Directory verifies Jim’s account is authorized for access.
- Jim’s account is granted access. Jim can now check email, modify the contract file and work on the database server.
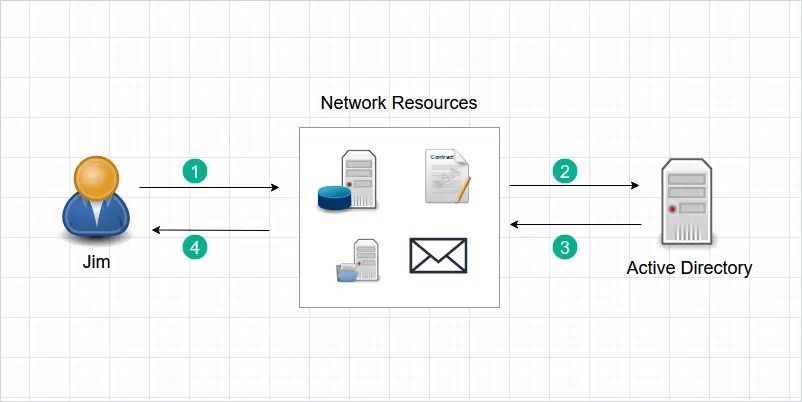
Example 3 – Authorize and Deny User Access
In this last example, we will look at another user that has mixed access (allow and deny permissions.
- Pam logs into the network with her username and password. She tries to access the same resources as Jim (email, a contract file, and a database server. )
- These network resources check with Active Directory to see if Pam’s account is authorized for access.
- Active Directory verifies Pam’s account (Authentication). AD also checks what resources Pam’s account has access to (Authorization).
- Pam can now access email and the contract file but does not have permission to access the accounting database server.
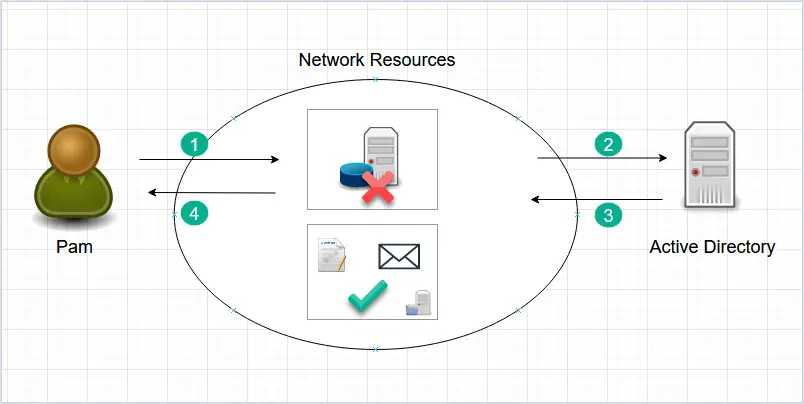
In all of the above examples, Active Directory works by providing authentication and authorization to users and network resources. No matter what technical jargon you hear, that is the core function of Active Directory.
It is important to note that these network resources must be configured to use Active Directory. The resources are typically joined to the Active Directory server (but not all systems require this). There is a lot of configuration and planning that goes into configuring an Active Directory server. Organizations typically have dedicated professionals to implement and manage these systems.
In the next lesson, I’ll go over some of the core components of an Active Directory server.
Lesson 2
Active Directory Domain Services
Active Directory Domain Services (AD DS)
Active Directory Domain Services is the main component of Active Directory.
AD DS can be broken down into three main functions.
- Directory service – A directory service provides methods for storing data in a structured way that makes administration and access easy. For example, Active Directory stores information on users, computers, and groups.
- Authentication Service – Authenticates network users
- Authorization Service – Grants or denies network users access to network resources.
It is important to stop right here and review these three terms. Don’t get confused with the following three terms, they all refer to Active Directory.
- AD – This is just an abbreviation for Active Directory.
- AD DS – This is a server that is running the Active Directory Domain Services Role.
- Domain Controller (DC) – This is also a server running the Active Directory Domain Service Role. A Domain Controller is the same thing as a server running AD DS.
When you install Active Directory you will be installing the AD DS Role on a Windows server.
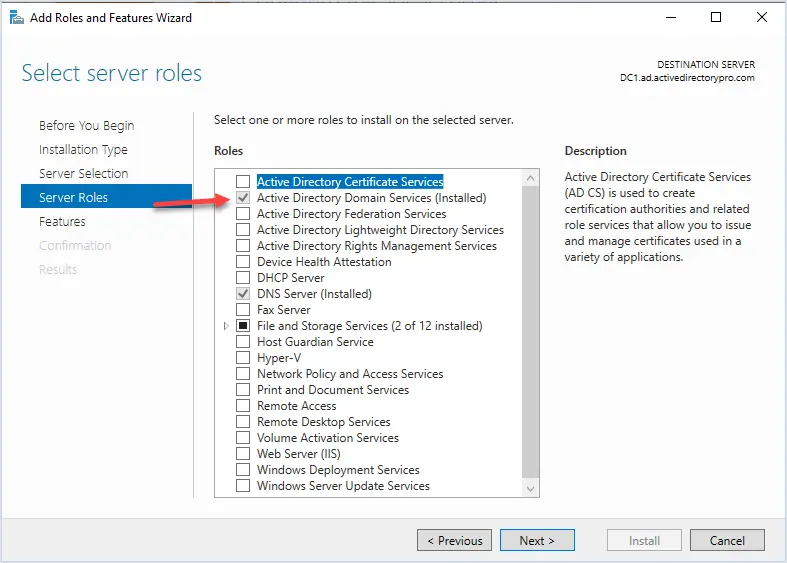
Next, I’ll go over some of the main components of AD DS.
Active Directory Core Components
You are about to see why Active Directory is a complex topic. I’m going to briefly go over some of the core components of an Active Directory environment. I’ll include diagrams to help illustrate the topic. The components below are typical of any Active Directory environment.
Active Directory Domains, Trees and Forest
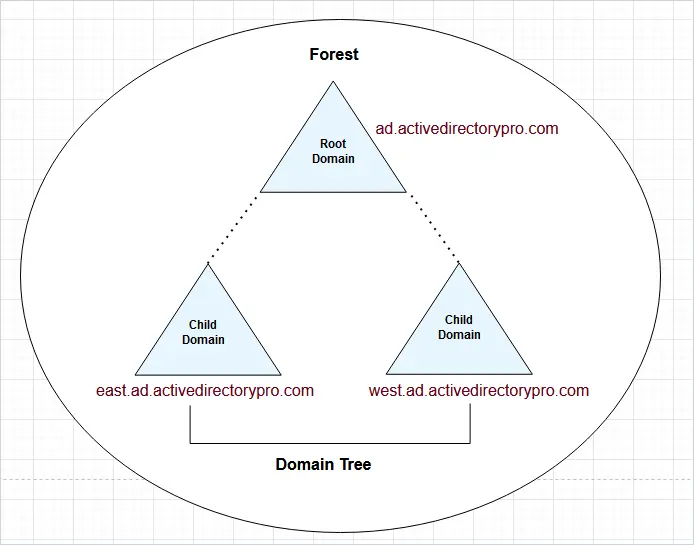
Active Directory organizes resources in a hierarchical logical structure. This logical structure helps to organize objects, define relationships, and control security boundaries.
The forest is the top level container and is a collection of Active Directory domains. The domains in the forest share a directory schema, directory configuration, and global catalog. Domains in the same forest automatically have a two way transitive trust. When you first install Active Directory and create a domain you are also creating a forest.
Active Directory Root Domain is a logical structure of containers and objects within Active Directory. A domain contains the following components:
- A hierarchical structure for users, groups, computers, and other objects.
- Security services that provide authentication and authorization to resources in the domain and other domains
- Policies that are applied to users and computers
- A DNS name to identify the domain. When you log into a computer that is part of a domain you are logging into the DNS domain name. My DNS domain is ad.activedirectorypro.com, this is how my domain is identified.
When you install Active Directory you have to pick a domain name to use. It is recommended to use a subdomain of a routable domain name. For example, ad.activedirecetorypro.com is a subdomain of activedirectorypro.com. The initial installation of Active Directory will create a forest and the root domain.
Child Domain is a domain that shares the same domain name space as the root domain. It is a domain with its own collection of objects. In this example, there are two child domains east.ad.activedirectorypro.com and est.ad.activedirectorypro.com.
Trees are a set of domains that are connected together. When you add a child domain to a parent domain you create what is called a domain tree. A domain tree is just a series of domains connected together in a hierarchical fashion all using the same DNS namespace. In the diagram above the child domains east.ad.activedirectorypro.com and est.ad.activedirectorypro.com are part of the same domain tree.
Schema
The schema is a set of rules that defines the classes of objects and attributes contained in the directory.
Global catalog (GC)
A global catalog contains information about every object in the directory. This allows users and administrators to find directory information regardless of which domain in the directory actually contains the data. By default the first domain controller in a domain is designated as the GC server, it is recommended to have at least one GC server for each site to improve performance.
Replication
The replication service synchronized the Active Directory database with other domain controllers. Active Directory is typically deployed with two or more domain controllers for redundancy reasons. When you create an account on one Domain controller it is replicated to the other one. If one domain controller goes down the other one will have a copy of the database.

In the above diagram, if a user is added to DC1, it will be copied to DC2 and vice versa.
Sites and Services
Active Directory sites are used to combine multiple domain controllers into logical containers that relate to their physical location. Sites are used to optimize the performance of Active Directory when you have multiple branch offices and domain controllers.
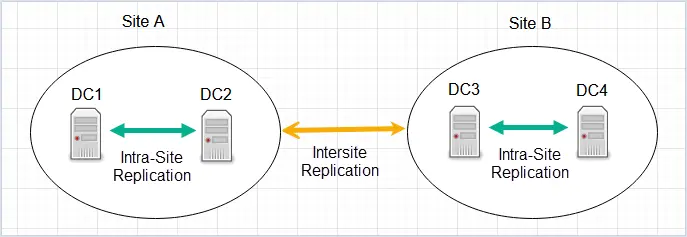
The above example has two sites and each site has two domain controllers. The domain controllers in Site A use intra-site replication to keep all changes synchronized between DC1 and DC2. Site A and Site B use intersite replication to ensure changes in Site A are replicated in Site B and vice versa.
Kerberos
Kerberos is the authentication protocol used by Active Directory to verify the identity of a user or host. The diagrams at the beginning of this guide looked simple but in the background there was a lot of communication between the client and Active Directory server to authenticate and authorize the user.
Here is a diagram that shows the authentication process that happens in the background.
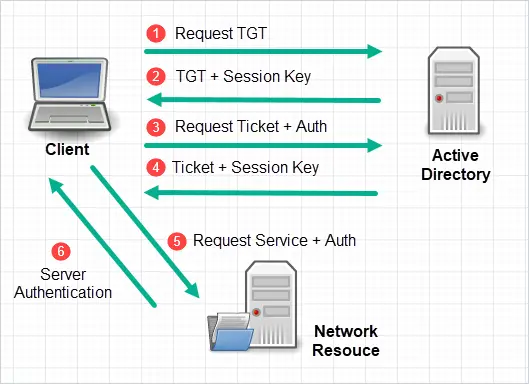
- The client sends a request to the Active Directory server.
- The server responds with a TGT and session key the client can use to encrypt and authenticate with the AD server.
- The client sends a request for a ticket.
- The server validates the request and returns a service ticket.
- The client uses the ticket it received from the AD server to request access to a network resource.
- The server will decrypt the ticket and validate the request.
FSMO Roles
Microsoft introduced flexible single master operation (FSMO) roles in 2003. These FSMO roles can be distributed to different domain controllers, which can help with performance and redundancy. If one domain controller goes down another DC will take over the missing role.
- Schema master role manages the read-write copy of the schema in Active Directory.
- Domain naming master role makes sure you don’t create a second domain with the same name in a forest.
- RID master is in charge of the SID for each object. Each AD object must have a unique SID. To prevent duplicates the RID is in charge.
- PDC emulator is the authoritative DC in the domain. It is responsible for authentication requests, password changes, and group policy.
- Infrastructure master role manages the relationship of GUIDS, SIDs, and DN between domains.
Active Directory Domain
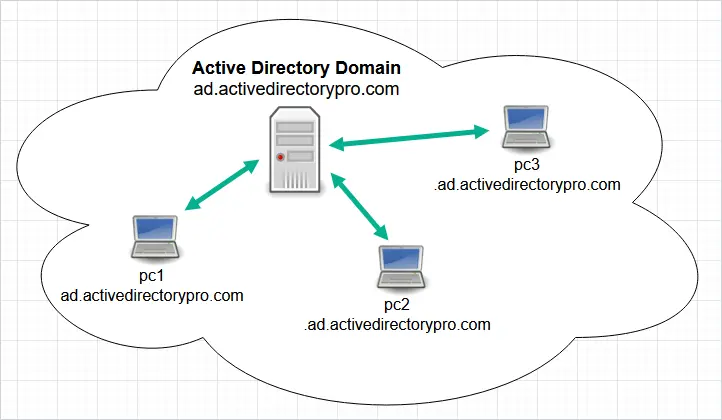
When you install Active Directory you have to pick a domain name to use. It is recommended to use a subdomain of a routable domain name. For example, ad.activedirecetorypro.com is a subdomain of activedirectorypro.com.
When you join a computer to the domain it will have the DNS suffix of your domain name for example, pc1.ad.activedirectorypro.com.
This way all of your domain joined systems are part of the same DNS namespace and can easily communicate with each other.
Also known as domain joined, Active Directory domain, or Active Directory environment.
Windows Domain simply means your active directory server and its domain joined devices or systems using it for authentication and authorization.
User Accounts
User accounts are used to provide employees access to network resources. A user account is typically assigned to each employee but sometimes shared accounts are used. This account is stored in the Active Directory database and can provide details on the employee such as first name, last name, street, state, city, manager, and more.
Screenshot of a user account object in Active Directory.
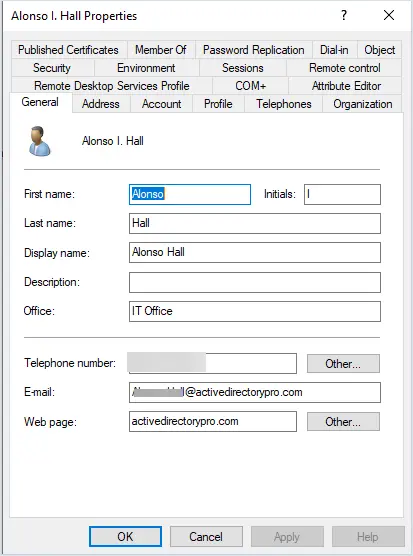
Security Groups
A security group is a collection of users or computers. It simplifies the administration of permissions for a group of objects. For example, if 20 people need access to a file you can create a security group and add the 20 people to the group. Then you would just have to manage file access for the group instead of 20 individual accounts.
Screenshot of a security group.
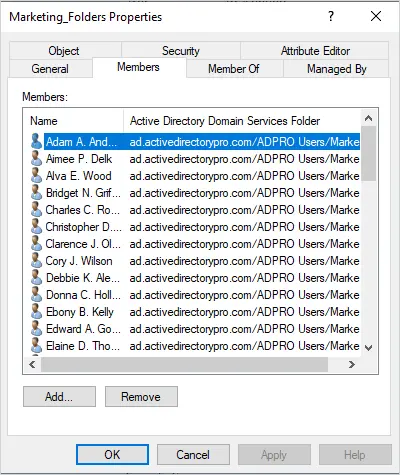
Computers Objects
When a computer is joined to the Active Directory domain a computer object is created. When the object is created in Active Directory, it becomes a trusted object which can be used to gain access to the network. For example, a user needs to log into the network and access a secured file. The user can log into the computer which is trusted and access the secured file (if the user has been granted access).
Screenshot of a computer object.
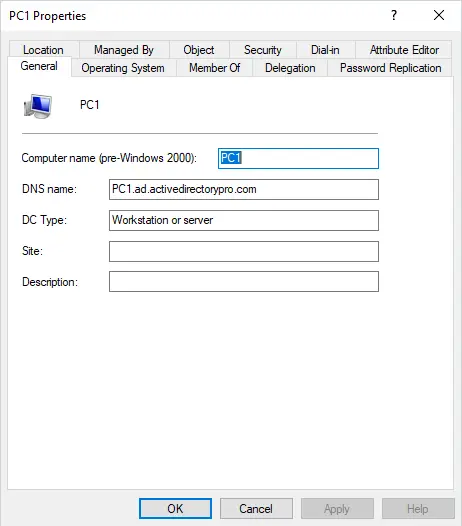
Organizational Units (OU)
In Active Directory, organizational units are used to organize Active Directory Objects (users, groups, computers). Organizing your AD objects makes it easier to administrate and apply policies. For example, you could organize all users into their own department folders. It is recommended to separate users and computers into their own OU.
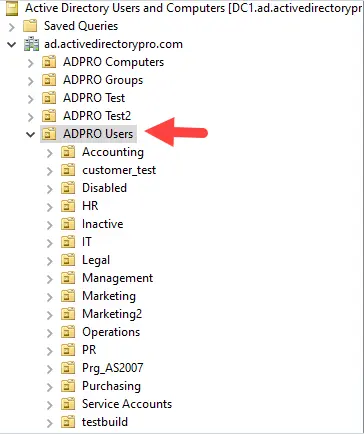
Lesson 3
Active Directory Benefits
The main benefit of Active Directory is its ability to centralizes user management and access to network resources.
Active Directory centralizes the management of the following:
- Centralized management of user accounts
- Centralized management of permissions
- Centralized management of policy settings
Let’s look at each of these benefits with some examples.
Benefit #1. Centralized Management of User Accounts
By using Active Directory you have a single place to create and manage all user accounts.
For example, I’ll pretend Active Directory Pro has 100 employees and they all need the ability to access the network. An Administrator would use the Active Directory users and computer console and create all the accounts in one central location.
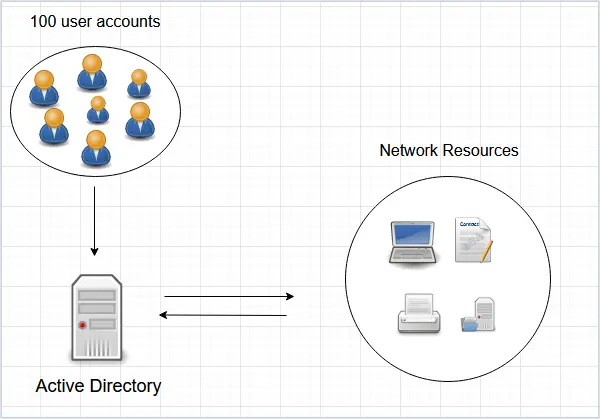
The employees can now log into a computer and access all the resources they have access to.
With no Active Directory, you would have to log into each resource and create an account. This would be a nightmare to manage and would be very time-consuming.
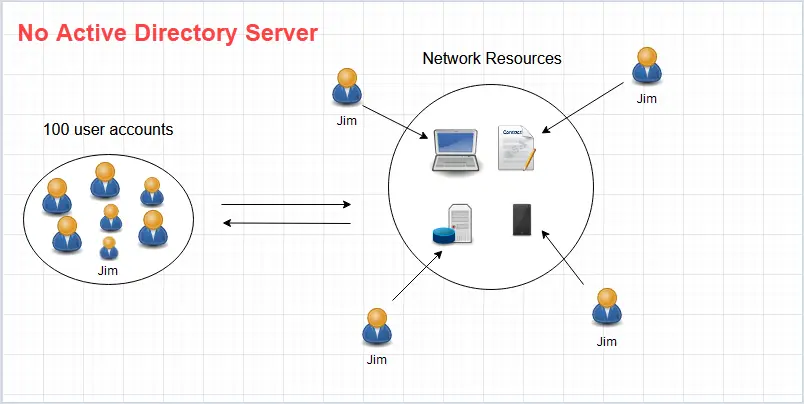
Here is what it would look like with no Active Directory server.
If Jim wanted to access network resources an administrator would have to create the account on each system he needs access to. For example, an account needs to be created on the laptop, on the database server, on the file server, on the email server, and so on. Now you need to do that for 99 more employees. That would be a major pain.
This would be very time-consuming and impossible to create consistency across all users and resources.
Benefit #2. Centralized Management of Permissions
By using Active Directory you can centralize the control and management of permissions to your network resources.
Active Directory has security groups that can be used to give a group of users accounts access to resources.
For example, you have several users that need access to the accounting resources (server, contract file, file share). To easily provide access to all of these resources you would add the users into an Active Directory security group that has permissions to these resources.
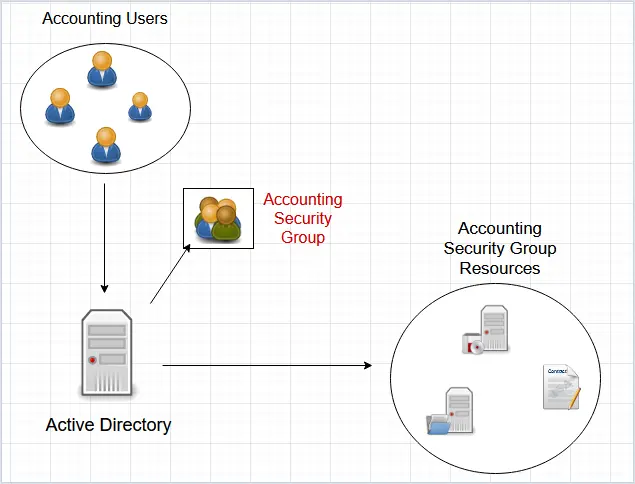
By using Active Directory security groups you can easily grant and remove permissions. When an employee leaves or needs permissions removed, you just remove the account from the group.
Benefit #3 Centralized Management of Policy Settings
In an Active Directory environment, you can use group policy to apply policy settings to users and computers.
For example, if you want all users to change their password every 60 days you can configure a password policy that applies to all users. If you wanted to apply power settings to all computers you can do that with group policy.
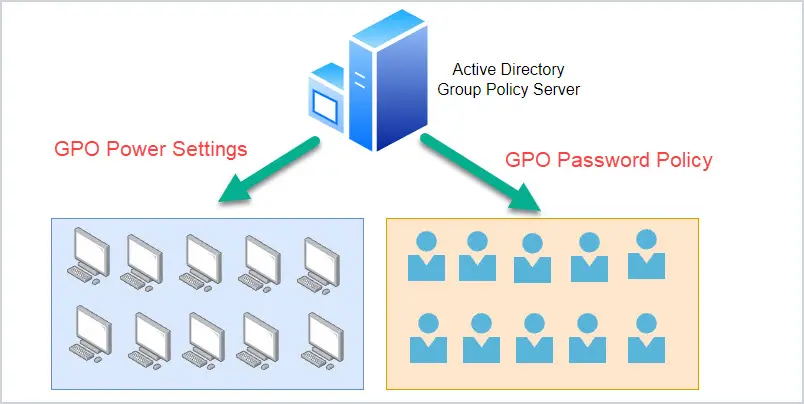
With no Active Directory or group policy you would need to configure the policy settings on each computer. That would be impossible to manage in large environments. Organizations that are 100% in the cloud, use Microsoft Intune to manage policy settings. Intune can also be used in hybrid environments.
Lesson 4
Management Tools
In this lesson, you will learn about the various tools used to manage Active Directory. Most of these are included when you install Active Directory on a server.
On the server running Active Directory, you can access these management tools under the “Windows Administrative Tools” folder. You can also install these tools on another computer by installing the RSAT tools.
Active Directory Users and Computers (ADUC)
This is the console that is used to create and manage user accounts, computers, and groups. For example, to create a new user account you would open the ADUC console to create the new account, set the password, and add the user to groups. It is also used to create OUs and organize your objects.
Active Directory Administrator Center (ADAC)
The ADAC tool was included with server 2008 R2 and higher. It performs many of the same tasks as ADUC and a few additional ones. I’m not sure if Microsoft meant for this to replace ADAC but it is not widely used. Most administrators still use the ADUC tool.
Active Directory Domains and Trusts
This console is used to raise the domain mode or functional level of a domain or forest. It is also used to manage trust relationships. This console is one you will not use very often.
Active Directory Sites and Services
This console is used to manage your sites and subnets. If you only have a single site then you wont need to use this console. If you deploy Active Directory in multiple geographic regions you may need to use this console to manage your subnets, sites, and replication.
Group Policy Management Console
Group policy provides centralized management and policy settings for users and computers in an Active Directory environment. For example, to make sure all users change their password every 90 days you would use group policy and configure a password policy. Understanding how to use group policy is a critical function as a System Administrator. To learn more see my guide on Group Policy Management.
DNS
The DNS console is used to manage and create DNS zones and resource records. Active Directory will not work without DNS, it is included when you install AD. It is important that you know the basics of DNS if working with Active Directory.
DHCP
The DNS console is used to create and manage the DHCP address pools in your network. This is one tool that actually has nothing to do with Active Directory. You don’t need DHCP for Active Directory but it is typically used to simplify assigning IP addresses to client devices.
PowerShell
PowerShell is a command line tool that helps you to automate many routine tasks such as creating, updating, and reporting on objects in Active Directory.
Active Directory Pro Toolkit
The AD Pro Toolkit is a collection of Active Directory Management Tools used to simplify and automate the administration of Active Directory.
I’ve managed many Active Directory environments over my career as a System Administrator/Manager. The tools provided by Microsoft lack many features such as bulk management and reporting. PowerShell can help with automation but it can be time consuming to figure out, and not all admins have this needed free time. That is why I created the toolkit, it is very easy to use and saves you a ton of time.
Lesson 5
Other Active Directory Services
The following is a list of additional Active Directory services that can be installed. These services are optional and are installed by using the add roles, and features wizard on the Windows server.
Active Directory Certificate Services
Certificate services are used to manage and deploy certificates. Certificates are used to digitally sign and encrypt documents and network traffic.
Active Directory Federation Services
The federation services provide single sign on (SSO) for user accounts for web based applications such as Office 365.
Active Directory Lightweight Directory Services
AD LDS is a service that provides directory services for applications and also provides a data store and services for accessing the data store. It uses standard application programming interfaces (APIs) for accessing the application data.
Active Directory Rights Management Services
This service encrypts documents and is used to limit access to documents such as email, office documents, and web pages.
Lesson 6
Azure Active Directory
Azure Active Directory is now called Entra ID.
Azure Active Directory (AD) is a cloud based service for authenticating and authorizing access. Microsoft calls it an identity and access management service, which is a new fancy term that just means authenticate and authorize access.
Azure AD will authenticate users to cloud based applications like Office 365, Azure, and other SaaS applications.
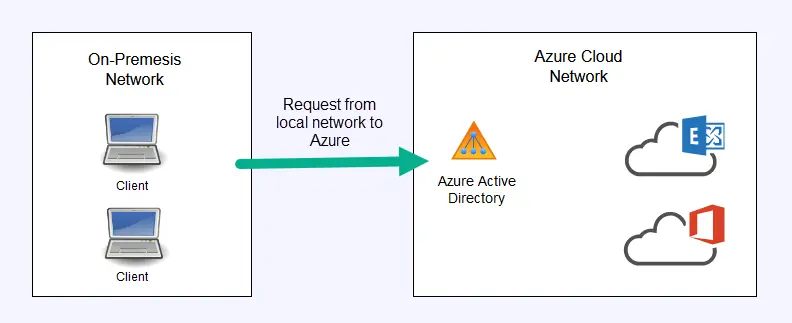
ADDS = Active Directory Domain Services (on premises Active Directory).
AAD – Azure Active Directory (Cloud based Active Directory).
Hybrid Azure AD
A hybrid Active Directory is when you have a local Active Directory (ADDS), and sync it with the cloud Azure Active Directory (AAD). In hybrid mode you can sync your local AD with the Azure AD using a Microsoft software called Azure AD Connect. This enables you to have the same users and passwords on premises and in the cloud. This is done so users will have a single sign on to both local resources and cloud based resources.
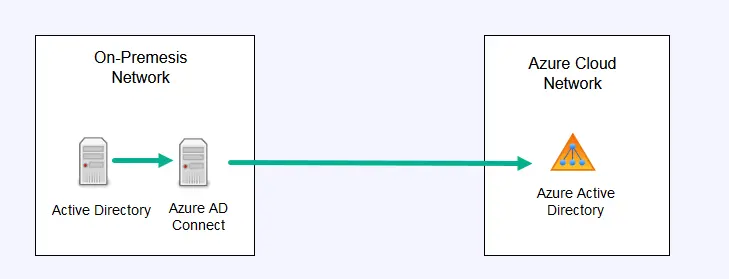
The sync of local AD to cloud AD is a one way sync, but Azure does not sync with the local AD. To learn more about Azure AD see the Microsoft article What is Azure Active Directory?
For someone trying to grasp the foundational concepts of AD before learning more, there are not nearly enough good resources out there like this. Thank you so much for this contribution it was immensely helpful, especially clarifying little things like redundant terms!
You’re welcome.
Hi, this is very helpful, but i would love to learn more about Federation Services, B2B and B2C also can you please help.
Is there any way w AD to keep multiple user’s names on the ‘logon to windows’ page?
The default seems to be the last user, and “other user”.
thnx really help me but how i can active applocker
Hi,
I do not have any articles on applocker. Here is the link to Microsoft documentation on applocker.
https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/applocker/administer-applocker
Policies deployed through GP are only supported on Enterprise and Server editions. Policies deployed through MDM are supported on all editions.
Very informative. Thanks for sharing. Loved The Office references too!
Much Appreciated.
As a total noob to AD, can you suggest me where to start so that I am able to do role based access management?
I’ll be grateful.
Hi Sabra,
Here is a good article on RBAC
https://www.ajtek.ca/guides/role-based-access-security/
A really great introduction to AD services.
Thank you for sharing your knowledge.
Thanks Olivier
Very great and helpful for learning about AD
Thanks for the feedback.