In this guide, I’ll show you how to get the password expiration date for Active Directory User Accounts. This is very easy to do.
I will provide a few examples that go over how to get this information for a single user and how to get the expiration date for all AD users.
PowerShell Get All Users Password Expiration Date
Step 1. Open PowerShell
Step 2. Copy and paste the script below.
Get-ADUser -filter {Enabled -eq $True -and PasswordNeverExpires -eq $False} –Properties "DisplayName", "msDS-UserPasswordExpiryTimeComputed" |
Select-Object -Property "Displayname",@{Name="ExpiryDate";Expression={[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed")}}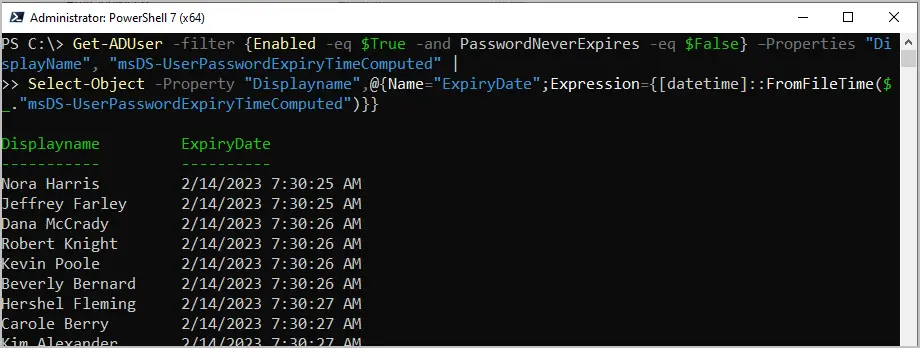
Step 3. Export the list.
To export the list add this to the end of the command.
export-csv -path c:\temp\passwordexpiration.csvEasily Check Password Expiration Date with AD Pro Toolkit
The AD Pro Toolkit includes multiple Active Directory Tools to manage user and computers. With the toolkit you can easily get users password expiration date and other account information.
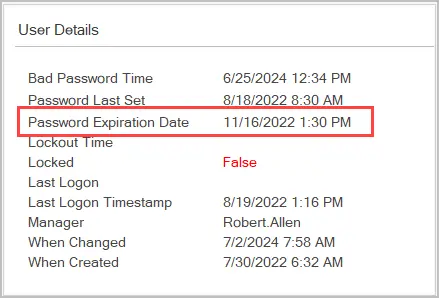
On the user management page search and select a user account. The password expiration date and other user information will be displayed in the “User Details” box.
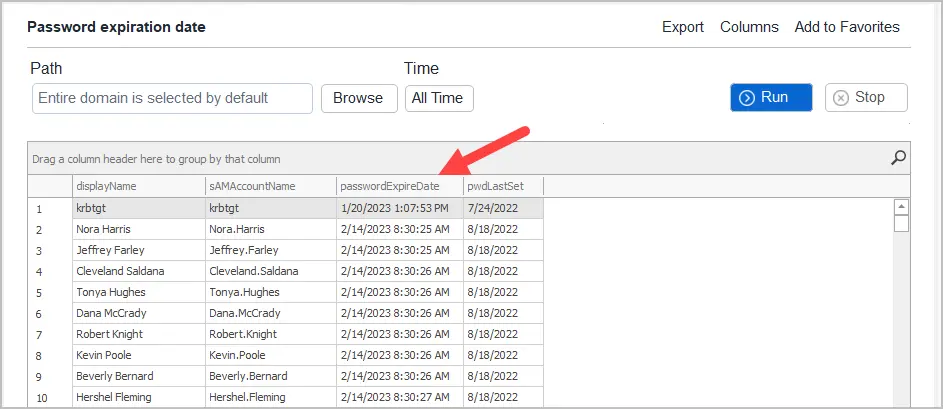
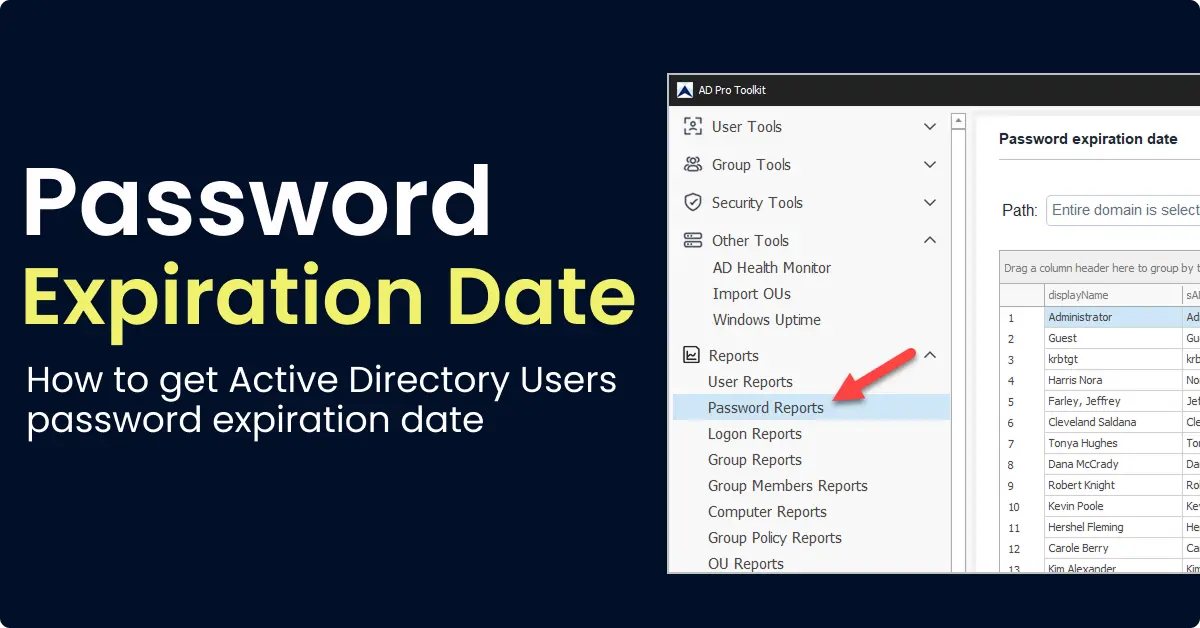
To get the password expiration date for all users follow these steps:
Step 1: Click on Password Reports > Password expiration date and click Run. Click browse to select an OU or group.
Step 2. To export the list, click the export button.
How to Check Password Expiration Date for a Single User
To get the password expiration date for a specific user run this command.
In this example, I’m checking the date for user “robert.allen”.
Get-ADUser -identity robert.allen –Properties "DisplayName", "msDS-UserPasswordExpiryTimeComputed" |
Select-Object -Property "Displayname",@{Name="ExpiryDate";Expression={[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed")}}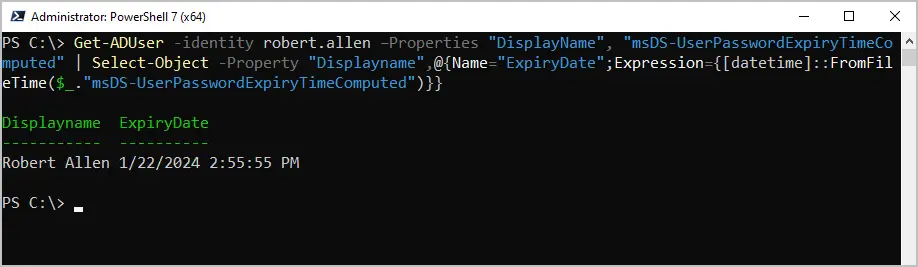
Get Password Expiration Date for Users in an Organizational Unit
To get only users in an OU you will need to use the -SearchBase option and the distinguishedName of the OU.
In this example, I’ll get all users from my Management OU.
Get-ADUser -filter * -SearchBase "OU=Management,OU=ADPRO Users,DC=ad,DC=activedirectorypro,DC=com" –Properties "DisplayName", "msDS-UserPasswordExpiryTimeComputed" | Select-Object -Property "Displayname",@{Name="ExpiryDate";Expression={[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed")}}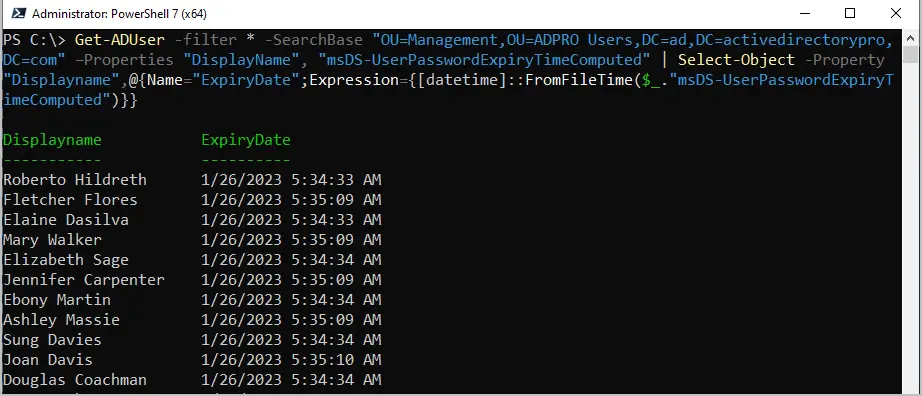
Get Passwords Expiring in the Next 30 Days
With the AD Pro Toolkit, you can choose a time frame for when passwords will be expiring.
Enter a number in the box, it defaults to passwords expiring in the next 30 days.
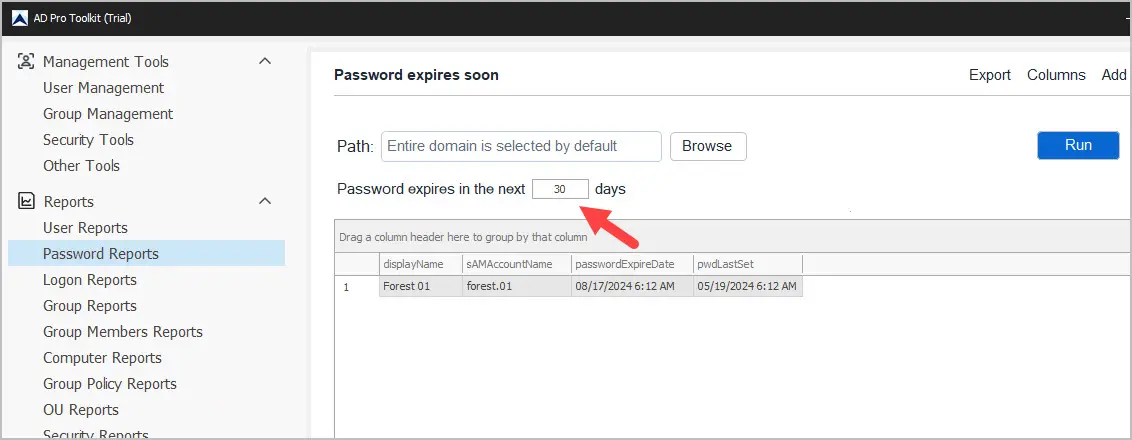
Now you will see a list of users that that has a password expiring in the next 30 days.
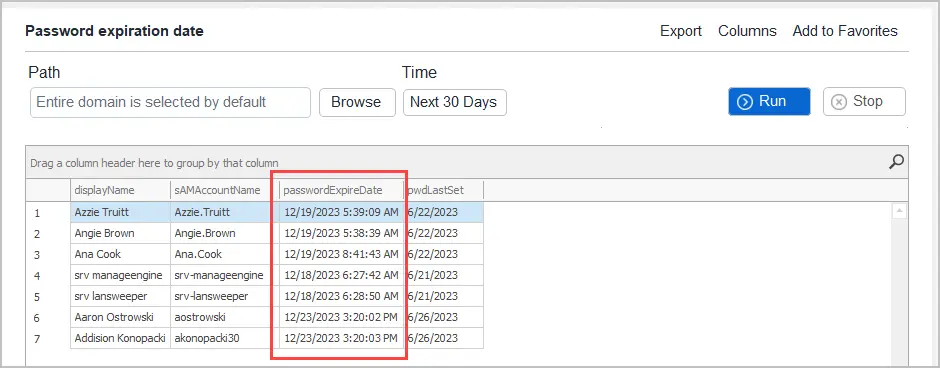
Password Expiration Email Notification
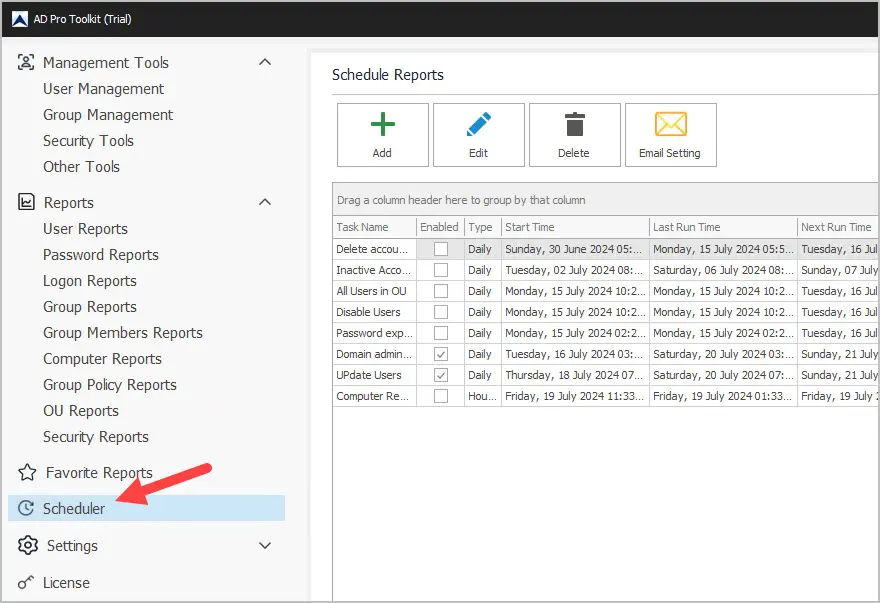
To get an automated email report of password expiration dates use the built in task scheduler.
Click on Scheduler and then click Add to create an automated report.
Download AD Pro Toolkit and try the password expiration date reports.
The toolkit’s Active Directory Reporting Software includes over 200 built-in reports on users, computers, groups, and more.
Using the Net User command to Display Password expiresDate
This last method uses the built in net user command to display a users password expiration date. This is useful to quickly check the password expires date for a single domain user account.
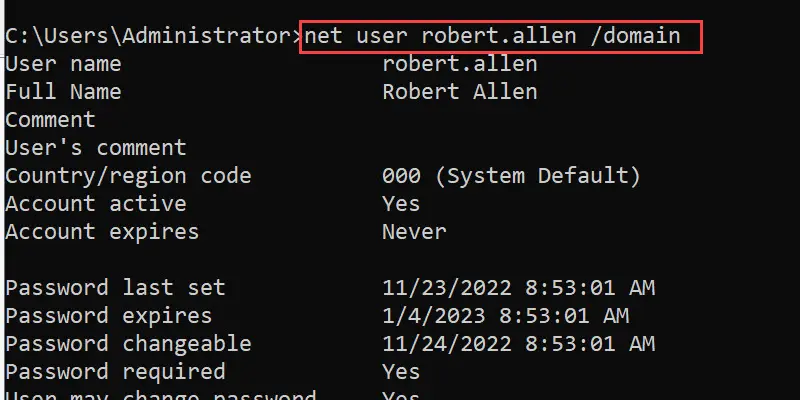
Open the windows command prompt and type the command below.
Net user USERNAME /domain
In this example, I’ll use the account robert.allen.
In addition to displaying the password expires date it also provides other useful information such as password last set, when the password can be changed if the account is active, and so on.
I’ve worked as a System Administrator for years and I’ve never had the need to create a report on users password expiration date. With that said this article is one of the most popular tutorials on my website, so I guess there is a need for it. You should have no problem generating a password expiration date for all domain user accounts using one of the methods from this article.
I’d love to hear your feedback on the use case for this report. Do your computers not notify users the password will expire in x days?

On the powershell method, your example command has “–Properties” instead of “-Properties.” The difference being the – vs -, a dash instead of a hyphen. Just wanted to note this incase someone copy/pastes that line (like I did lol) it will error out.
I could not replicate. I was able to copy and paste the commands with no issues.
I copied/pasted the powershell script on a Server 2016 machine. Some users reported expiry correctly, but most users reported expiry at 12/31/1600 at 5pm. Users report correctly using net user /domain. What could be wrong?
12/31/1600 means the value has never been updated (null value).
I had this issue too. I found that if I opened PowerShell and just ran the command almost all of the users would show 12/31/1600. However, if I use the ‘run as administrator’ option with PowerShell the dates are actually reported correctly.
How do you display what OU the user is in?
Include the distinguishedName
get-aduser -identity healther.jay -properties * | select name, distinguishedname
Not sure what I’m doing wrong – I’ve checked the comments and do not see anyone reporting the same issue – except maybe the most recent comment., and that one was only ‘really close’…
When I copy and past your script into powershell, I get a list of all of the users in AD along with corresponding pw expiration dates. However, the ONLY person whose date is correct is the person that changed his password today. Everyone else shows an expiration date of:
12/31/1600
I’m happy to provide a screenshot if that might help – assistance would be appreciated.
Dan
12/31/1600 is null The “zero” date for LargeInteger datetime. Open the user in ADUC and check the pwdLastSet attribute and see if it is set to 0.
When I run Method #1 I get for most of the users null passworddlastset and Passworddneverexpires as it seems it doesn’t find the field in table {[datetime]::FromFileTime($_.”msDS-UserPasswordExpiryTimeComputed”)}
or it will return date 01/01/01601
but it does return an expiration date when running the Net User command
Is there another field name we can query
Double check your command syntax. In your comment the attributes are spelled wrong.
get-aduser -filter * -properties passwordlastset, passwordneverexpires |ft Name, passwordlastset, Passwordneverexpires
Is there any way in which we can ask users to reset the password. The AD is configured in the VM and LDAP is setup within the VM. We wanted to make it simple for the users by providing the link in email where one user can go and re-set the AD Password. Can you please provide the out of the box url or confirm if i need to write the code to the same.
There is no out of the box URL for resetting passwords, you would need a 3rd party solution. On a windows computer, users can change their own password by using control-alt-delete and then selecting change password.
Hi Robert.
Great script very helpful, I could not see if this question has been asked/answered already however, is there a way to target a AD group using method 1 to get a specific group such as Net user “group-name” /domain to pull a list of all users from that group with their password expiry dates?
Kind regards
Hi Robert,
I want to reset passwordlast set date for a list of users. Any idea how I can achieve this?
Thanks!
I don’t think that is possible.
İt worked for me Thank you for your work
How is it possible to check expiracy for group of users. So instead of either all or just 1 user – i would like to check like user1, user 2 and user 3 – instead of have check one at a time
It’s a nice script, but we have so many users that I like to do the following:
-Filter to only show users with password expriring within 7 days from today (we have fine-grained password policies)
-Output as JSON (on console)
For me, that is quite hard to do, for you guys not I guess, can you show me how ?
Hi Vincent below code should work for that:
$targetDays = 10
$targetDate = (Get-Date).AddDays($targetDays)
Write-Host “Password-Expiration Date before:” $targetDate
# Shows Password expiration Date of Domain (“mydomain.com”) where expiry date is less then 10 days from today
Get-ADUser -filter {Enabled -eq $True -and PasswordNeverExpires -eq $False} –Properties “DisplayName”, “msDS-UserPasswordExpiryTimeComputed” -Server “mydomain.com” |
Select-Object -Property “Displayname”,@{Name=”ExpiryDate”;Expression={[datetime]::FromFileTime($_.”msDS-UserPasswordExpiryTimeComputed”)}} |
Where-Object ExpiryDate -lt $targetDate | Sort DisplayName
Nice, trying to filter on “ExpiryDate” but can’t get that work.
usecase: I want to generate a file of users which have a password experation 5, 4, 3, 2 or 1 day from now.
Hi!
How Can I get the Logon Name if I only have the display name?
Thank you in advance.
You can find the logon name in Active Directory Users and Computers.
Is there a way to display the date in chronological order? I’m getting the expiration date report but not in order by date. Thank you in advance.
Yes. Use the sort-object cmdlet.
get-aduser -filter * -properties passwordlastset, passwordneverexpires | sort-object passwordlastset
how to export the result to file
With Powershell add this to the end | export-csv -path c:\it\export.csv
With the AD Pro Toolkit click the export button and choose the file format.
How do you get it to export? It keeps asking for inputobject in method 2 after adding Export-Csv -Path
I’m still having trouble getting it to sort by date. It’ll sort alphabetically when I do a sort-object, but expiry just puts them in a random order each time, even though the command runs. Any suggestions?
Thanks for sharing 🙂
Do you know how can i extend the password expiration date by 6 months for all users on AD ?
You would need to update the group policy that has your password policy. See this article -> https://activedirectorypro.com/how-to-configure-a-domain-password-policy/
Thanks for sharing this stuff. I have one question
The expiry time it shows, in which time zone is it, central time ? or the time zone set on the server ?
It’s pulling the time value from the user account on the server.
Thanks for sharing this, its helpful.
Is it possible to trim the expiration date..? Just want the date, without time. if so, can you please help with that..?
Can you specify a specific user?
Yes. just use -identity USERNAME. Here is an example
get-aduser -identity robert.allen -properties passwordlastset, passwordneverexpires | select Name, passwordlastset, Passwordneverexpires
Get-ADUser Ryan
I am using the following commandlet to get the list of last password set and then using a variable to get the value and add -365 to it, however this variable is not getting populated.
I can see the commandlet work and output values but the variable I am using $PWdLastSet.passwordlastset is not getting any value, am I doing something wrong ?
$PWdLastSet = get-aduser -filter * -properties passwordlastset, passwordneverexpires -SearchBase “OU=Service Accounts,OU=SG1,OU=AT,DC=wt,DC=ad,DC=cit,DC=cc” |ft Name, passwordlastset, Passwordneverexpires
$expiredDate = $PWdLastSet.passwordlastset.addDays(-365)
Can you do this without using Get-ADUser?
In method 2, is there a way to get the expiring users in the next seven days?
I am looking for a way to do this as well. I am trying to compile a list of users and when their passwords will expire.
I seem to be having an issue using the -searchbase in the Method-2 above. I keep getting a message ” A parameter cannot be found that matches parameter name ‘SearchBase’. ” Is this possibly a location issue where I am not putting it in the correct location within the Method-2 command?
Hi
I need Only OU level
You can target an OU by using the -searchbase and the DN of the OU.
Get-ADUser -Filter * -SearchBase "OU=Finance,OU=UserAccounts,DC=FABRIKAM,DC=COM"Hey robert should I put this command in the line with getaduser after the filter parameters?
Hi Lucas,
I’m not sure what you are asking.
He was just trying to ask you if the command was all on one line. 🙂
Method #1 is great. Thanks!!
Nice trick but how about to get user properties from different domain?
Use the -server to specify the domain server instance
Get-ADUser -Filter “Name -eq ‘ChewDavid'” -SearchBase “DC=AppNC” -Properties “mail” -Server lds.Fabrikam.com
how about specifying the user name in your step 2 query?
Here is an example for a specific user
get-aduser -Identity Alonso.Hall -properties passwordlastset, passwordneverexpires |ft Name, passwordlastset, Passwordneverexpires
If there are multiple OU’s and you want to find the expiring passwords for a specific OU, how would you do that? I’m guessing with ‘-searhbase’, but not sure how. – Thanks
Timely help! Many thanks.
Nice set of commands/scripts, very helpful!
Thank Jim
Great! It was really helpfull!!
Something useful from Method 1:
$m=’Password expires’;($MyExp = net user $env:USERNAME /domain | %{if($_ -match $m){get-date ($_ -replace $m,”).trim()}});rv m;
Hi, how do I query if the password change was successful through powershell?
thanks for this site by the way, it helped guide me quite alot! 🙂
Grazie!
Is there a field like Enabled that we can use to filter out this where this isn’t set for the user that shows up “12/31/1600 7:00:00 PM”.
Yes use the below code to return just the enabled users
get-aduser -filter {Enabled -eq $TRUE} -properties passwordlastset, passwordneverexpires |ft Name, passwordlastset, Passwordneverexpires
EXCELLENT = Do you know how to filter by a date ?
say passwordlastset > today-2
Add
Sort-Object -property ExpiryDate
Any help on getting the sorting corrected?
Get-ADUser -filter {Enabled -eq $True -and PasswordNeverExpires -eq $False} -Properties “DisplayName”, “msDS-UserPasswordExpiryTimeComputed” |
>> Select-Object -Property “Displayname”,@{Name=”ExpiryDate”;Expression={[datetime]::FromFileTime($_.”msDS-UserPasswordExpiryTimeComputed”) | Sort-Object -property ExpiryDate -Descending}}
Sort-Object -property ExpiryDate -Descending <does not sort correctly
$dayb4yesterday = (get-date).AddDays(-2)
get-aduser -filter {passwordlastset -gt $dayb4yesterday}
How to get especially service account password expire date.
Nice tips! 🙂
Found your “Method two” very useful, thanks for publishing!
Awesome ❗ ❗
The second method is more accurate if you have Fine-grained Password Policies enabled in the domain.
Net Use only shows the result from the Default Domain Policy.
Good Tip. Thanks for the comment.
So I have a separate OU users in a different user that I want to see when there password expires.
Were would I make the change for this with in a domain tree?
How do I get the expiration date for few users that I have in a csv format using method 2? I know the command mentioned in here will give me the list of all the users in my org.