In this post, I will explore the TCP and UDP ports used by Active Directory from client to server.
I will use WireShark and a series of tests to determine what ports are used.
Tests I’ll be running:
- Ports Used When a User Logs into a Computer
- Ports used when running gpupdate
- Ports used when joining a computer to the domain
- Ports Used When Rebooting
Test Environment:
- Server 2022 with IP 192.168.100.10 (Active Directory Server)
- Windows 10 Pro with IP 192.168.100.20
- Wireshark is installed on the Active Directory server
- The Active Directory server is a default install
Active Directory Ports Summary
Here is a list of ports used by Active Directory by a default install. This is between the domain controller and a domain-joined computer.
- TCP 135 Microsoft RPC
- TCP/UDP 49152 – 65535 RPC Dynamic Ports
- TCP 88 Kerberos
- TCP 389 LDAP
- UDP 53 DNS
- TCP 445 SMB
TCP 135 Microsoft RPC Mapper
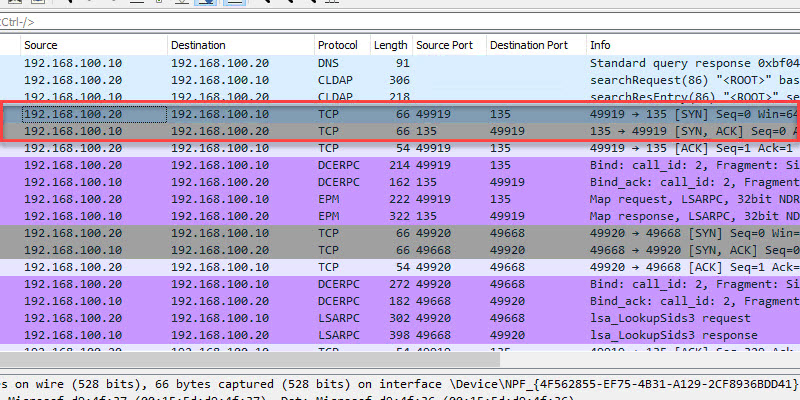
- Description: Port 135 is a critical client/server port. This port is used by many Microsoft services and should not be blocked by a firewall. First the client connects to the RPC mapper service (port 135) and asks the mapper what port a given service is listening on (which will be a dynamic port range… see below). The RPC mapper responds to the client with the port and then the client connects to that port. You can see this in the above screenshot.
- Firewall: Allow between client and server. Port 135 should not be exposed to the internet.
TCP/UDP 49152 – 65535 RPC Dynamic Ports
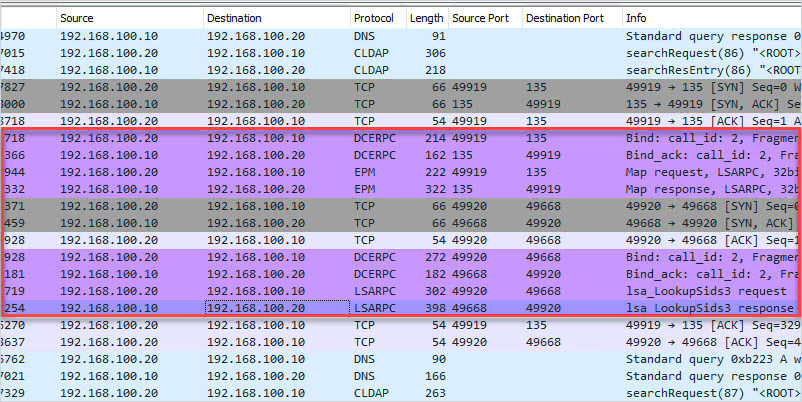
- Description: The dynamic port range is used by various server applications. RPC dynamic port allocation instructs the RPC program to use a particular random port in the range configured for TCP and UDP, based on the implementation of the operating system used. The RPC mapper (port 135) is used to connect clients to services running on these dynamic ports.
- Firewall: Allow between client and server. This port range should not be exposed to the internet.
we recommend that you reconfigure the firewalls to allow traffic between servers in the dynamic port range of 49152 through 65535. This range is in addition to well-known ports that are used by services and applications.
https://docs.microsoft.com/en-US/troubleshoot/windows-server/networking/default-dynamic-port-range-tcpip-chang
TCP 88 Kerberos
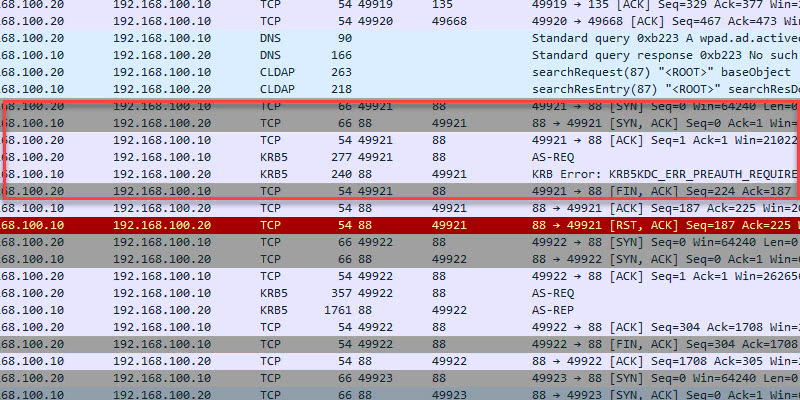
- Description: Kerberos is an authentication protocol that authenticates requests between a client and server in a secure manner. This is Microsoft Window’s default authentication method for domain-joined devices.
- Firewall: Allow between client and server. Port should not be exposed to the internet.
TCP 389 LDAP
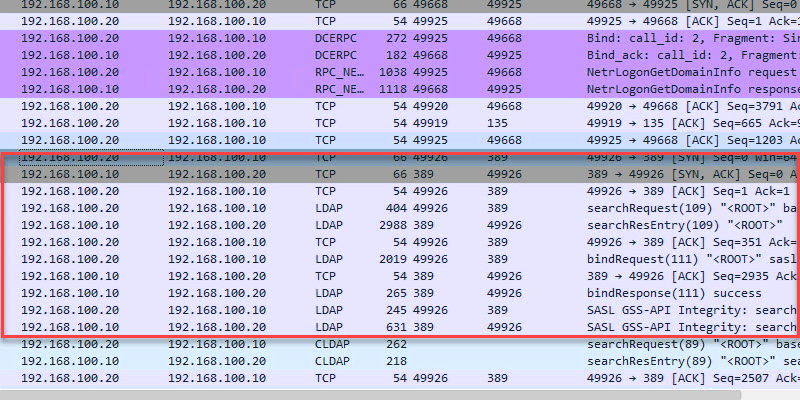
- Description: LDAP is a directory access protocol. This protocol is used to search, add/delete, authenticate and modify data in a Directory Server such as Active Directory.
- Firewall: Allow between client and server. Port should not be exposed to the internet.
UDP 53 DNS
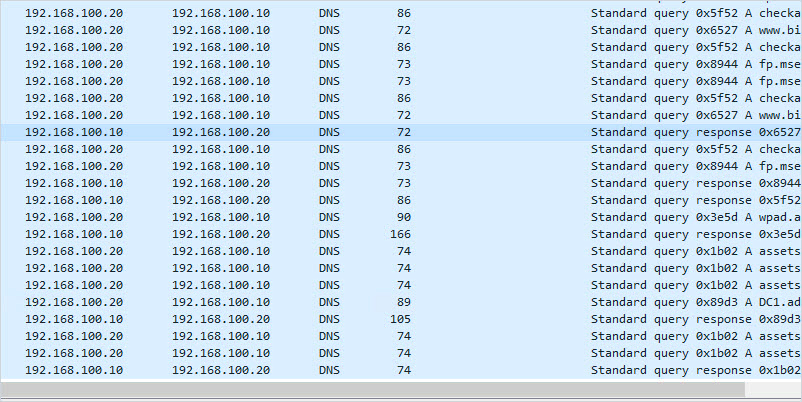
- Description: DNS is a critical service used to map IP addresses to host names. This is a critical service used by clients to locate resource records in the domain and lookup external domain names.
- Firewall: Allow between client and server. If DNS is running on your Active Directory server I do not recommend exposing it to the internet.
TCP 445 SMB
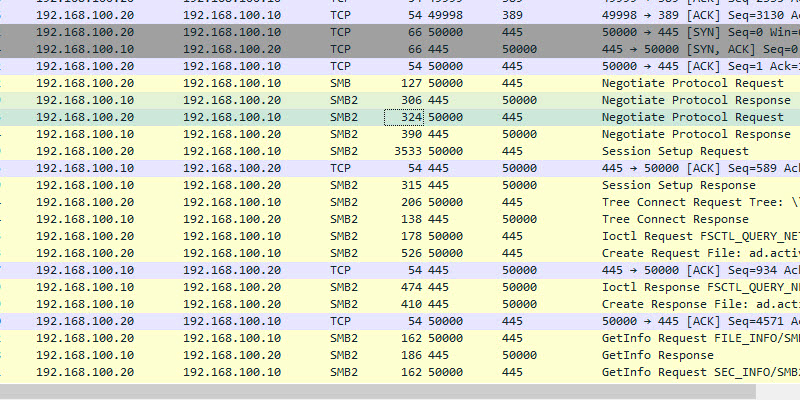
- Description: Server message blocks (SMB protocol) is a client-to-server communication protocol used for accessing files, printers, and data on a network. This port is used during startup to get GPO information, it is also used when running the gpupdate command.
- Firewall: Allow between client and server. Do not expose this port to the internet.
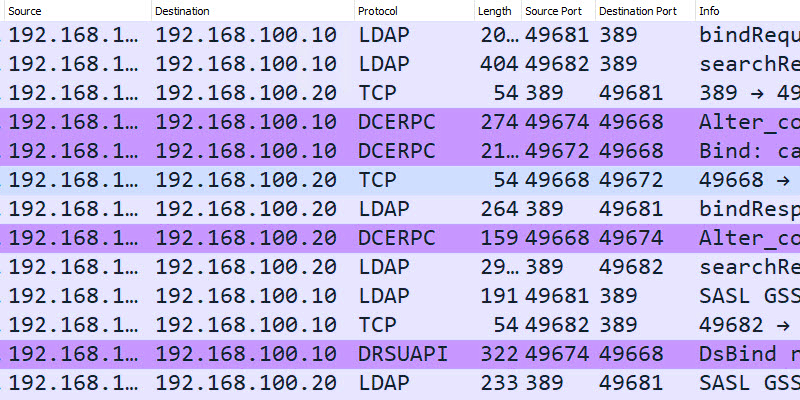
Ports Used When a User Logs into a Domain-Joined Computer
In this example, I will log into computer PC1 (192.168.100.20) and capture the network packets from the domain controller.
Here is a conversation view of the TCP/UDP ports used. This is traffic sent from the client to the domain controller and destination ports.
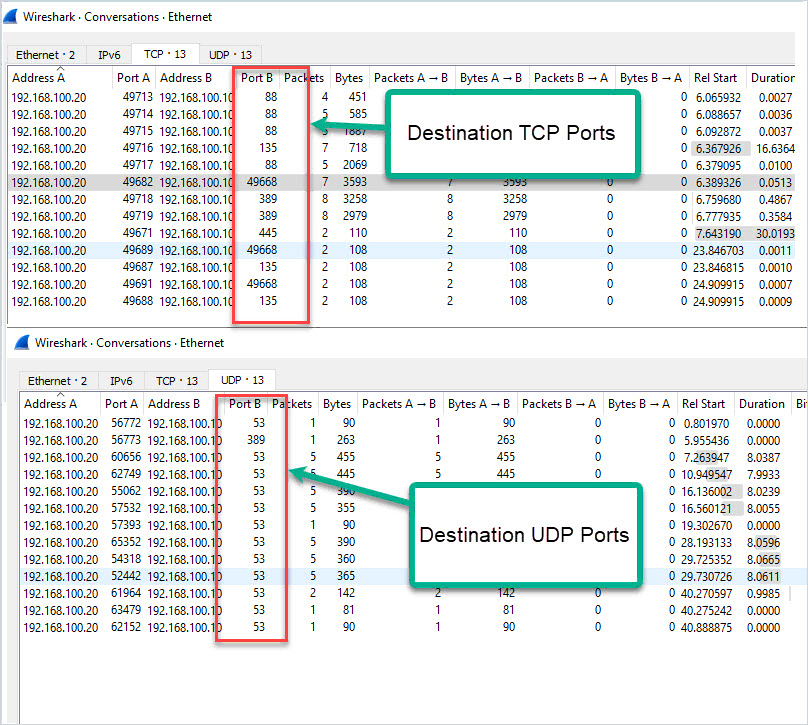
Here is a summary of the destination ports used by the client.
- TCP 88 (Kerberos)
- TCP 135 (Microsoft RPC)
- TCP 389 (LDAP)
- TCP 445 (Microsoft DS)
- TCP 49668 (RPC for LSA, SAM, NetLogon) – This starts with a request to port 135
- UDP 53 (DNS)
- UDP 389 (LDAP)
Ports Used When Running Gpupdate
While logged into the client PC I will run the gpupdate command to see what ports are used.
Results below. It Looks like TCP port 445 is used the most when running a gpupdate.
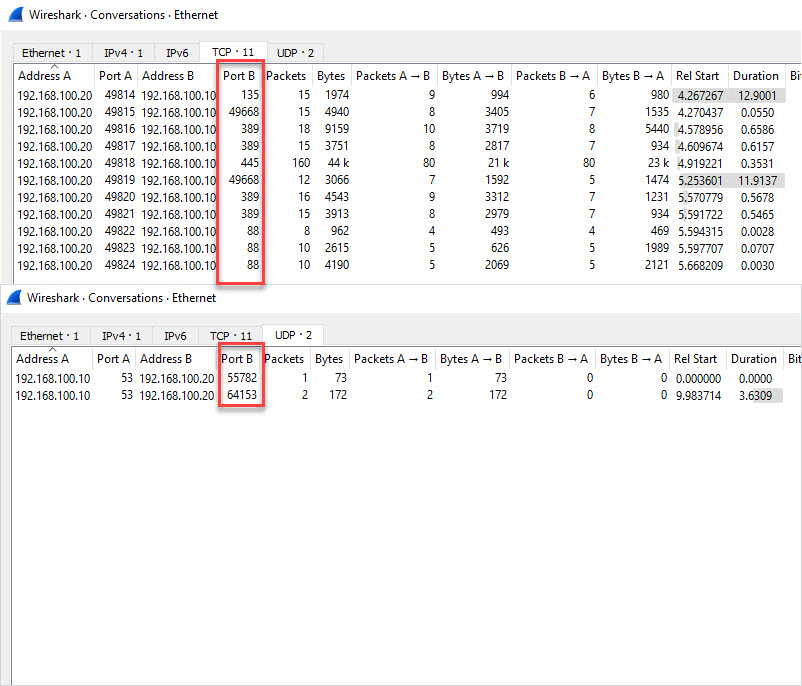
Ports Used When Joining a Computer to The Domain
This looked similar to the other packet captures.
TCP 88 (Kerberos)
TCP 135 (Microsoft RPC)
TCP 389 (LDAP)
TCP 445 (Microsoft DS)
TCP 49668 (RPC for LSA, SAM, NetLogon) – This starts with a request to port 135
UDP 53 (DNS)
Ports Used When Rebooting
Nothing new, I see the same ports used when compared to the other packet captures.
Hopefully, this guide helps you to understand the ports used between a client and an Active Directory server. Keep in mind this test was a default domain controller install with no additional services running, the more services you install the more ports that may be used.
RE: You’re missing the dynamic RPC ports, TCP/UDP 49152 – 65535
I have two DCs in a testlab with Windows Firewall for Advanced Security on for all profiles, and using the Microsoft URL:
https://learn.microsoft.com/en-us/troubleshoot/windows-server/active-directory/config-firewall-for-ad-domains-and-trusts
From my understanding, if I add a Server Role to the Server, the corresponding firewall rules are automatically added to the firewall.
There is an inbound rule:
Active Directory Domain Controller (RPC)
Local port: TCP RPC Dynamic Ports
Remote port: All ports
Does this equate to:
49152-65535/TCP RPC for LSA, SAM, NetLogon (*)
49152-65535/TCP FRS RPC (*)
49152-65535/TCP DFSR RPC (*)
Hi, I do have the dynamic port range listed.
My domain works very well from a segment, I can add a machine to the domain, however, a new vLAN was added and when including a Client machine to the domain, it is added but with an error message:
Changing the Primary Domain DNS name of this computer to “” failed. The name will remain “contoso.local”. The error was: The RPC server is unavailable.
These ports have already been added to the Firewall and the problem persists:
53 -> DNS (TCP, UDP)
88 -> Kerberos (TCP, UDP)
123 -> NTP (UDP)
135 -> RPC/WMI (TCP, UDP)
137 -> NetBIOS (UDP)
138 -> RPC (TCP, UDP)
139 -> NetBIOS (TCP)
389 -> LDAP (TCP, UDP)
445 -> RPC/NP/SMB/ICMP (TCP, UDP)
443 -> SSL sobre HTTPS (TCP)
464 -> Kerberos Password (TCP, UDP)
593 -> RPC sobre HTTP (TCP)
636 -> LDAP SSL (TCP)
3268 -> Catálogo Global (TCP)
3269 -> Catálogo Global (TCP)
Please, I appreciate your help.
Kind regards,
You’re missing the dynamic RPC ports, TCP/UDP 49152 – 65535
great work…
Awesome article!
We are configureing NoTrust from VPN and this is used to secure who net against all servers. Still have trouble to get GPUPDATE to work
I’d love to see another article like this where the environment is configured for LDAPS or DC to DC ports, ADWS etc..
IPsec ISAKMP UDP 500
LDAP SSL UDP 636
LDAP SSL TCP 636
Global Catalog TCP 3268
Global Catalog TCP 3269
NAT-T UDP 4500
Active Directory Web Services (ADWS) TCP 9389