In this tutorial, you will learn how to deploy printers using Group Policy.
In this example, I will use group policy preferences and item level targeting to install printers based on user security group membership.
For example, users in the “HR_Printers” group will get the HR-OfficeJet9025 printer installed and users in the “Marketing_Printers” group will get the Marketing-HP4200 installed.
Why deploy printers using Group Policy?
This simple answer is it helps to automate the user setup process. It’s a step that almost every computer setup needs so automating this step speeds up the computer configuration process. This is a big win for your helpdesk or another IT staff that helps configure computers. This is also a big win for your customers as it is often a call to the helpdesk to get a printer setup. This will eliminate that phone call because as soon as they login the printer is automatically installed in the background.
Step for installing printers via GPO:
Step 1: Create AD Security Groups
The first step is to create security groups for the printers. In this example, I’m going to install printers by the department so I’ll create a security group for each department. I’ve named my groups the “department_printers”. You can name the groups whatever you like.
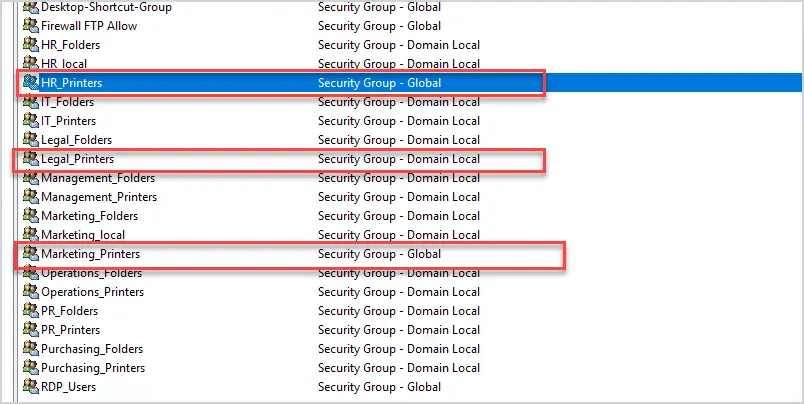
Next, add members to the new groups and move to step 2. You can also use existing groups, but I recommend creating groups for each resource.
Step 2: Create a New GPO
Now I’ll create a new GPO and link it to my Users OU.
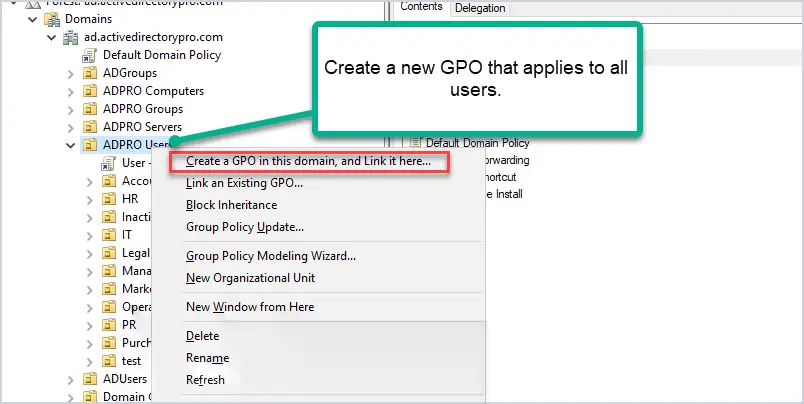
Give the GPO a name. I’ve named mine “Users – Printer Install”
Edit the GPO and browse to User Configuration > Preferences > Control Panel Settings > Printers
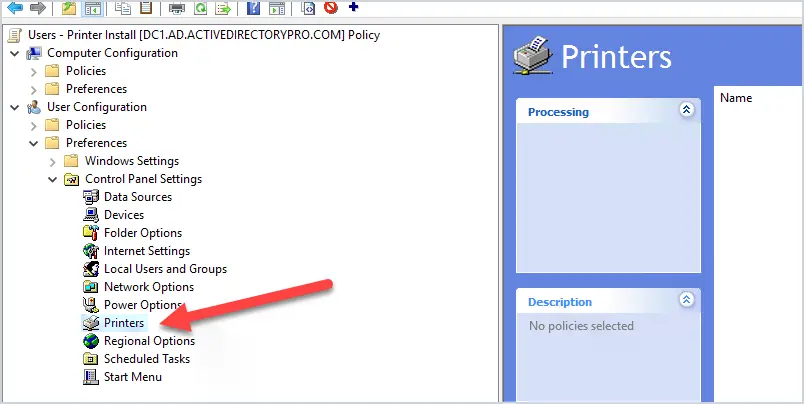
Right click printers, select new, and click “shared printer”
In this example, I’m installing printers from a printer server, you can use TCP/IP or a local printer.
My printer server is “srvwef” and the printer share name is “HR-OfficeJet9025” so the share path will be \\srvwef\HR-OfficeJet9025.
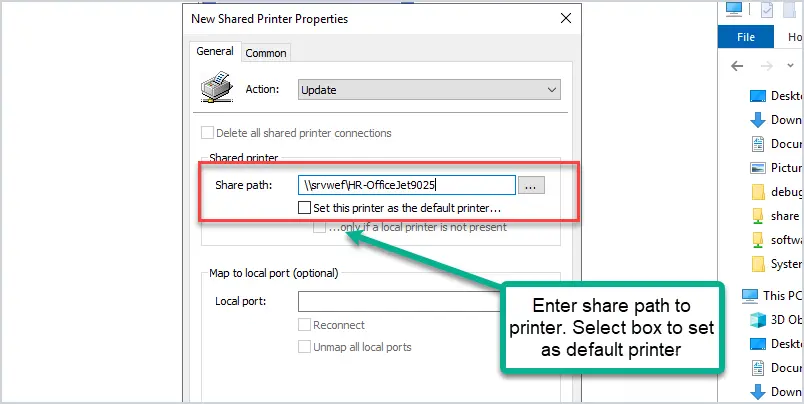
This is the HR department’s printer so I want this to only apply to the HR department security group. This is done using item level targeting.
Click on Common
Check the box “Run in logged-on user’s security context (user policy option).
Select Item-level targeting and click the Targeting button.
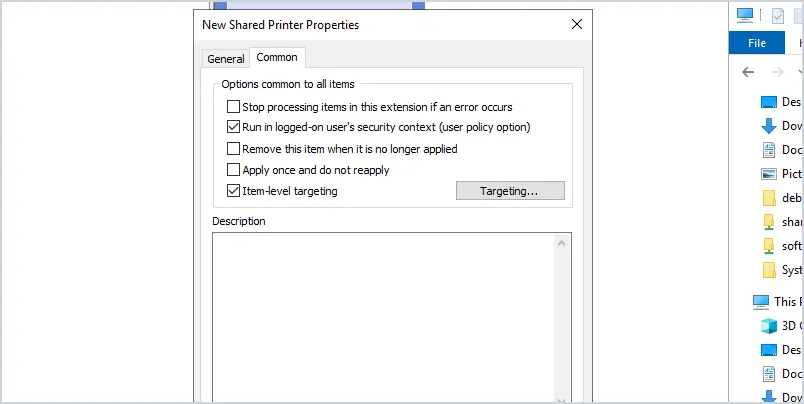
Click the new item arrow and select security group. Enter the security group you want the printer to install for, I selected my HR_Printers group.
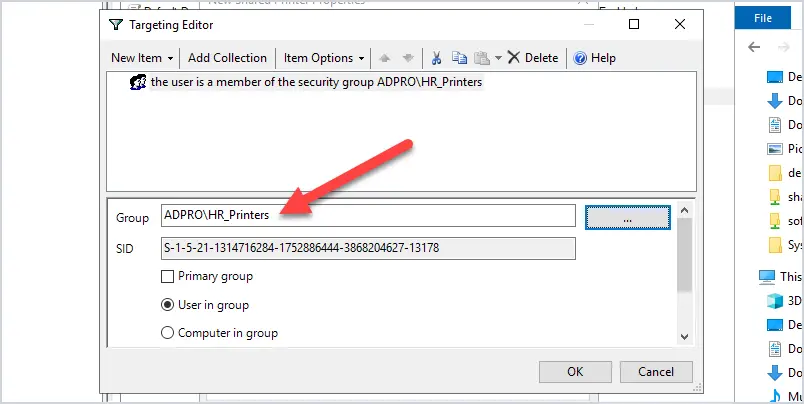
Click ok to get back to the Group Policy Management screen.
This completes the GPO configuration.
Step 3: Reboot or run the gpupdate command
To test the install you will need to log in as a user that is in the security group.
You will need to run gpupdate /force command to refresh the group policies.
First, let me show you that the printer is not installed.
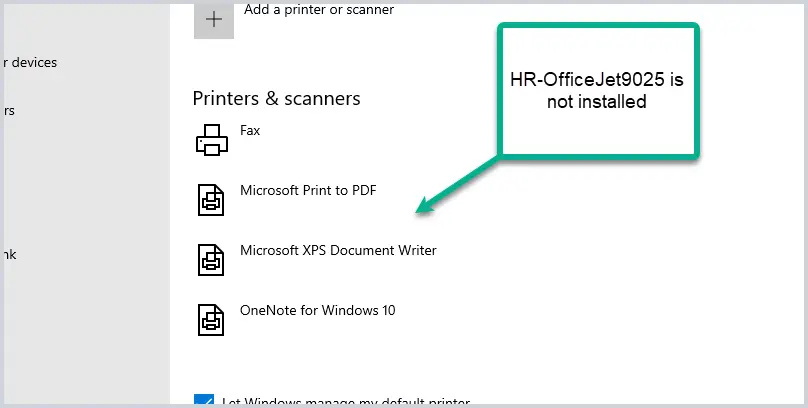
Next, I’ll run gpupdate /force and the printer will install. You could also reboot or wait 90 minutes for GPO to refresh on its own.
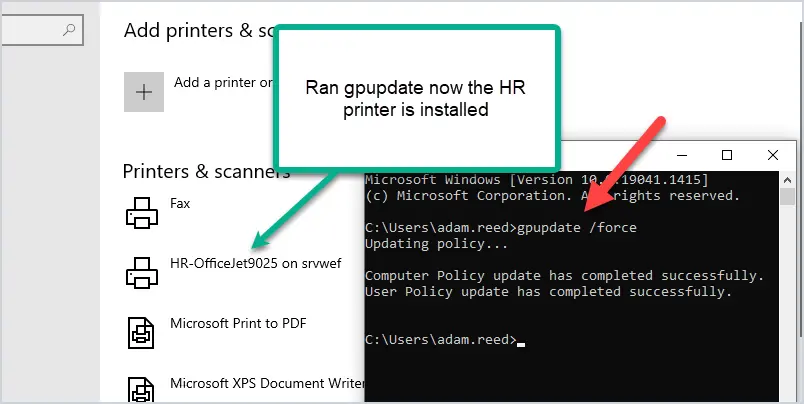
You can see above that the printer is now installed.
Step 4: Repeat for additional printers
Now just repeat this process for any other printers you want to install with group policy. The great thing about this configuration is you don’t need to create additional GPOs. You can add additional printers to this one GPO to install all printers.
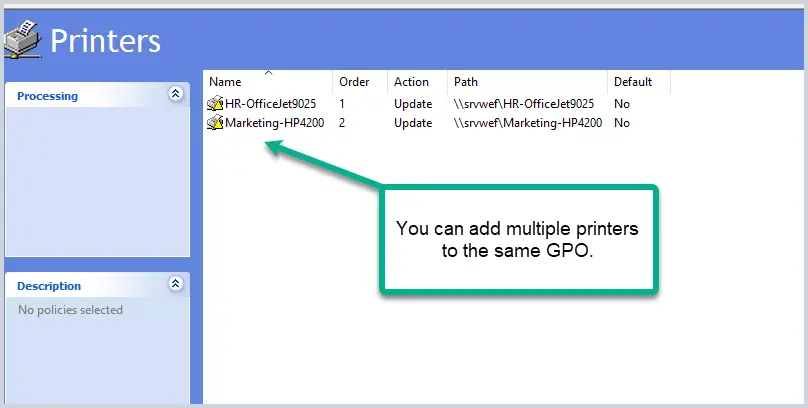
Above you can see I added the Marketing printer to the same GPO. The Marketing printer will only install for users that are part of the Marketing_printers security group.
Summary
Installing printers is often an extra step the helpdesk does when installing computers. By using group policy you can automate the printer install for users. This is a big win for users and staff that configure computers.

Hi @Robert Allen. I love this site man. Thank you!
This post and its comments led me to do a bit of digging on the topic of Point and print and some of the cybersecurity challenges administrators are wrestling with. I came across a great breakdown of the issues and policy based solutions that enable the use of GPOs to allow unprivileged users to automatically deploy printers AND keep things somewhat locked down. I don’t know if linking to another article is frowned upon here so I’ll quote a bit of it:
“Fixing our Point and Print configuration
…The answer lies in a couple of Group Policies in Computer Configuration > Policies > Administrative Templates > Printers:
Only use Package Point and print
Package Point and print – Approved servers
By enabling the policy Only use Package Point and print and configuring the policy Package Point and print – Approved servers, the Print Spooler service will only accept to install signed printer drivers from trusted servers.
…
Key takeaways
I will conclude this blog post with a recap that will hopefully provide clear guidance to both system administrators and offensive security consultants.
First of all, as an administrator, the one key thing to keep in mind is that “There is no combination of mitigations that is equivalent to setting RestrictDriverInstallationToAdministrators to 1” (i.e. Enabled), as pointed out by Microsoft in the KB article KB5005652, which is also the default behavior on up-to-date machines.
However, if you do need to allow domain users to install shared printers, you will have to disable this policy. In this case, the following configuration offers the best compromise between usability and security.
Limits print driver installation to Administrators –> Disabled
Only use Package Point and print –> Enabled
Package Point and print – Approved servers –> List of in-forest print servers
For Package Point and Print to work as intended, printers must be set up with package aware drivers.”
Credit: https://itm4n.github.io/printnightmare-exploitation
Thanks Bill. Good information.
I have successfully configured printers using GPO as this article explains but now we’re looking at not using a print server and just do direct printers configured via GPO.
Is this even possible?
I’m finding many posts online about this and it seems that there is no way of accomplishing this without a print server being configured as the distribution point for drivers, etc.
Hi, Angel.
Unfortunately it will not work. The GPOs are designed to only work with a print server even when deploying local IP printers. One option would be to use startup scripts but that would be a bigger headache than a print server in my opinion.
Hi Robert Allen,
I believe this Print nightmare has been my concern for our Group Policy not successfully deploying printer drivers, because the user logging in is not and admin and we have been forced to login to each staff system and install the print drivers for each new printer or if we migrate print servers. I will try to test some of your setting above, however the last poster “Nicholas Kulkarni” is correct is this not just circumventing the recommended Microsoft Print Nightmare configuration. Please any information would be helpful.
Hello, Robert,
I deployed printers via GPO but they don’t get installed on computers if I don’t add domain user or domain group as local administrator in Windows 10.
You might try settings the policy “Prevent users from installing printer drivers.” to disable.
More info on this page.
https://theitbros.com/allow-non-admins-install-printer-drivers-via-gpo/
You might try settings the policy “Prevent users from installing printer drivers.” to disable.
More info is on this page.
https://theitbros.com/allow-non-admins-install-printer-drivers-via-gpo/
Hi Robert, excellent page and instructions. Sadly you are absolutely correct, Microsoft borked it when fixing another problem. I am having to do this registry hack too. Considering this registry hack is a complete reversal of the recommended security settings to prevent the PrintNightmare elevation of privilege attack and we are two years on from this now is there a way to do this that doesn’t require the hack. Microsoft if you are reading this its time to fix this once and for all.
I added the printer in Computer Configuration>Policies>Windows Settings>Deployed Printers but unfortunately it does not connect after reboot. I need to assign printers to a computer not a user. What am I doing wrong?
To deploy to computer configure the policy under the computer configuration settings instead of users.
Hi Robert,
I have another question… If I use the configuration in your example, but the GPO will be placed in the OU where the computer objects are instead of the users OU ( In our infrastructure, admins are only granted permission in the OU for our own department, where users are placed in a different OU where only Domain Admins have access).
Would this still work if I have Loopback policy enabled?
Thanks.
I just tested and it works!! This is a life saver! Thank you very much for the post Robert!
With the AD security groups, would it be possible to add computer objects instead of users? I’m trying to have a certain printers deployed based on the computers/ location, instead of the specific user who’s logged in. Would it be possible to have that kind of setup? Thanks.
Yes. Configure the printer settings under computer configuration instead of user configuration. Then apply the GPO to your computer objects.
Hi Robert,
Thank you for your reply. On this same note, I’ve configured computer objects to be a part of a security group. I’ve set security group in the OU and applied the policy. Additionally, I’ve added item-level targeting to hit the security group. I’ve enabled point and print and allowed users do download the driver from my DC.
The issue I’m running into is:
1) Old printers are still showing up even when one of the computer policies is to delete all TCP/IP printers.
2) The Shared Printer isn’t showing up
3) When I run gpresult /r and /r /scrope user/computer, the policy is being applied correctly, but there is no printer shown.
Any ideas?
I deploy printers almost exactly this way except I do not check “run in logged in users security context” what difference is leaving that out making?
Every preference item applied is processed under the local SYSTEM account. When you select “Run in Logged on User’s Security Context”, the security context is changed from SYSTEM to the current logged-in User.
This looks promising, so thanks. We have 6 physical locations connected via VPN in one network. Currently, each location has its own DC and printers can be shared/deployed for that location from their local server. All remote site DCs are going away and all users will now go to main office DC. I plan to share all printers from print server here and deploy to all locations for their location’s printers. Will choosing TCP/IP printer and users installing printers over the VPN cause all print jobs to be processed over the VPN as well? Or, will it install the driver from the shared printer the first time, then send print jobs via IP address to the device in their local subnet? We are concerned about lag times if all print jobs have to be processed here and sent back to the device over the VPN. Thanks.
Hi Janet,
Choosing TCP/IP printer in the GPO will install the printer as a local TCP/IP (no printer server). When the computer sends a print job it will send it directly to the IP of the printer.
I’m sorry if I misunderstood. But I reviewed your reply to Pepper above and it says that the installing printer will go to the print server to get the driver to install, so I was confused. Will I need to manually install the drivers separately, or will they auto-install on the first login that triggers the GPO to install the printer? Thanks.
When you choose TCP/IP in the GPO it will install locally as a TCP/IP printer but pulls the drivers from the print server. You will need to configure the printer on the printer server but again it is so the client can download the print drivers.
Thank you for clarifying!
Hello. At the step “Right click printers and click “shared printer”, I do not have shared printer as an option. This is on my 2019 DC. Any idea why I don’t have that? My options are New / TCP/IP Printer or New / Local Printer.
Right click printers select “New” and then “Shared Printer”.
I do not see a response to Gary’s question, and I am also using a 2019 DC to add and configure the GPO. Should we select TCP/IP Printer or Local Printer?
Right click printers select “New” and then “Shared Printer”.
I’m running into the same issue on a 2009 DC. Under the User Configuration I see all three options when I right-click printers. But when I go to Computer Configuration I only see Local Printer and TCP/IP Printers. Any ideas?
The “Shared Printer” option is not available under the computer configuration, this is by design. I’m not sure why I cannot find any documentation of why Microsoft excluded this option from the computer config.
Hi Robert
How if I want to rename the printer (both the object and shared name) later on and keep the security group linked to the printer the same name as the new printer names. Will renaming the security group cause any issues?
Hi Robert, do you know how can delete old printer mapped ?
Did you try using group policy and the “Delete” action?
Hi Robert,
Is it possible to share 1 printer for 2 GPOs(Colored and Black&White)?
This is to restrict users under Black&White Security Groups to strictly print Black&White only. FYI, we’re using a Ricoh Printer. Thank you in advance!
Yes, just create a separate print share and lock it down with a security group.
Hi Roboert:
I know that when installing a printer from the printer server, the driver gets it from the print server. But I have a question… Where does GPO get drivers when installing tcp/ip printers?
It still installs the driver from the print server. In the GPO you specify the UNC path to the printer which is on the print server.
Hi Robert. I have done all of this – but the driver installation gives an error as the users are not administrators of their laptops. I have also tried removing “Run in user context” but that did not make any difference.
Kind regards
Landi
Try setting the GPO policy “Devices: Prevent users from installing printer drivers” to disabled.
Policy is found in the section -> Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.
Hi Robert, if I change this setting, will the users be able to install any printer they want in the domain? Because the printers are not being deployed to the users in the security group I created.
Thanks
Hi Ricky,
Which setting are you referring to?
Doesn’t disabling “Devices: Prevent users from installing printer drivers” completely undo PrintNightmare mitigation?