This is the complete guide to Microsoft Office 365 MFA.
Multi-Factor authentication (MFA) is the most recommended way to secure your Microsoft 365 tenant. In this guide, I will discuss what MFA is, what Legacy Authentication is, and what Modern Authentication is. I will also walk you through checking to see if Legacy Authentication is being used in your tenant and how to turn it off. And finally, I will walk you step-by-step through how to setup MFA in Office 365.
Topics in this guide:
- What is MFA?
- What is Legacy Authentication?
- What is Microsoft Modern Authentication?
- How do I know if my organization is using Legacy Authentication Protocols?
- How do I check to see if Modern Authentication is turned on?
- How to setup Multi Factor Authentication in Office 365
- Enable MFA for a Microsoft 365 Group
- How do I reset MFA for a user?
What is MFA?
Multi-Factor Authentication, aka MFA, allows you to secure user logins by adding multiple authentication methods. These days, just a password is not the most secure, even with complex passwords. It is always a good idea to have more than one authentication method for any platform you use.
To understand MFA a little more, let me explain Legacy Authentication and Modern Authentication, and how it is important to have a successful MFA implementation.
What is Legacy Authentication?
Legacy Authentication is often referred to as Basic Authentication. Basic Authentication is simply referring to an app, client, or protocol that is only passing a username and password for authentication.
Basic Authentication has been the sole form of authentication for most applications and protocols for many years. In today’s world, this is problematic because these usernames and passwords can be easily compromised. Contributing to this is the fact that a lot of usernames and passwords are not encrypted when being sent for authentication. Also, most credentials are stored on the device they are used on. This makes it very easy to steal credentials.
With that said, the push to turn off Legacy Authentication protocols is in full swing. Microsoft is urging organizations to do this as soon as possible. To speed this along, Microsoft has started deprecating Legacy Authentication Protocols in 365. I will go over how to check if your organization is using any of these Legacy Authentication Protocols later in this article.
What is Microsoft 365 Modern Authentication?
Modern Authentication, also referred to as OAuth 2.0, is a lot more than just requiring a username and password for authentication. Modern Authentication encompasses an array of authentication and authorization protocols such as MFA. While a lot of applications still require a username and password with Modern Authentication, the processes behind the scenes are done more securely.
With Modern Authentication, there is an Identity Provider and a Service Provider. For Microsoft 365, an example of a Service Provider is Microsoft Outlook. Azure Active Directory is the Identity Provider. The Identity Provider provides the authentication services. All of this is known as the Microsoft Identity Platform. Applications no longer perform the authentication, instead, it’s passed to the Microsoft Identity Provider to authenticate the user by issuing tokens. The tokens are then used to provide the user information and access rights to the application.
This is a much more secure method of authentication because account credentials are not passed to the apps or websites, and passwords are not stored on the device, instead, a cookie, token, or session state is stored on the device.
One of the most important security aspects of using Modern Authentication is the ability to use MFA. To use MFA, Modern Authentication must be enabled. For MFA to be enforced, Legacy Authentication needs to be blocked completely.
How do I know if my organization is using Legacy Authentication Protocols?
To help see if your organization is using them, you can check a few different ways.
View your messages in the Message Center. Go to https://admin.microsoft.com/#/MessageCenter and look for any messages regarding Basic Authentication summaries. Microsoft has been sending emails to tenants that are using Basic Authentication.
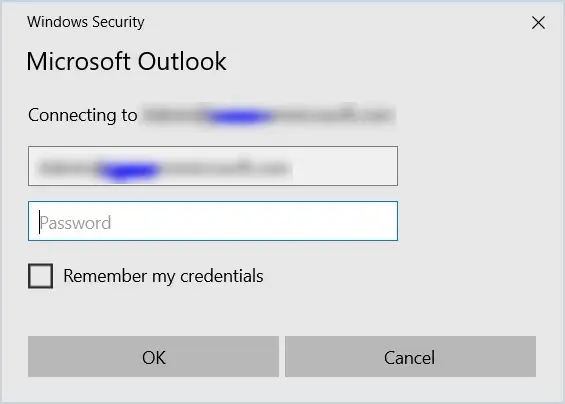
Basic Authentication Prompt
Another way is to keep a look out for basic authentication credential prompts like below when connecting to applications or servers.
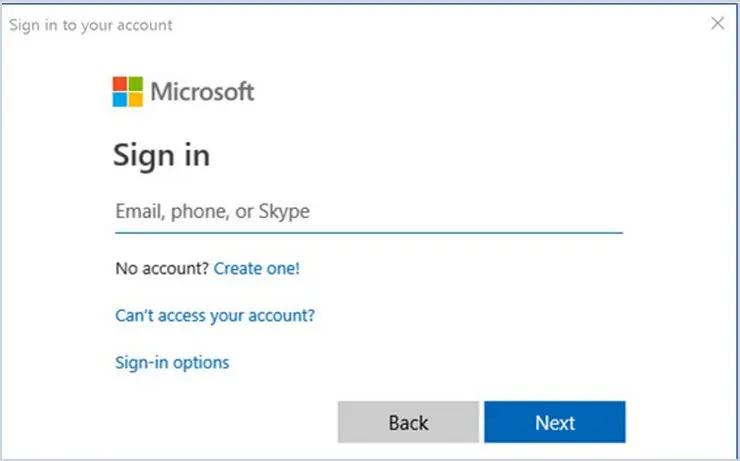
Modern Authentication Prompt
Modern Authentication will use a web-based credential box that looks like this:
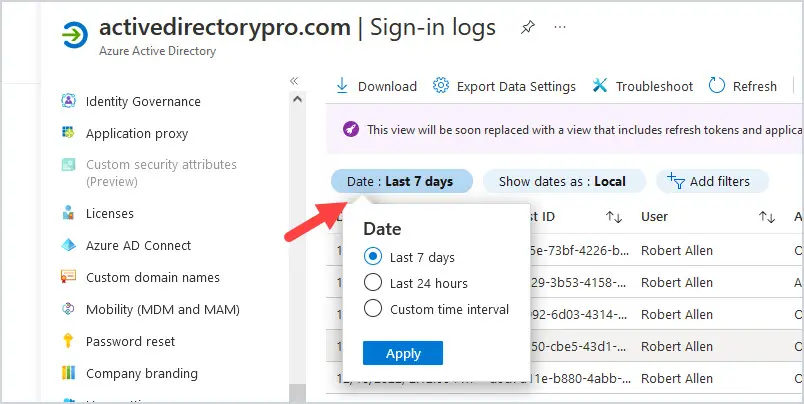
Azure Active Directory Sign-In logs
And finally, take a close look at your Azure Active Directory Sign-In logs.
Log into Azure AD by going to https://aad.portal.azure.com/ and then select Azure Active Directory and then click Sign-in logs under the Monitoring section. Select Date at the top and change to Last 7 days.
Then click on “Add Filters” at the top and select Client app then click Apply.
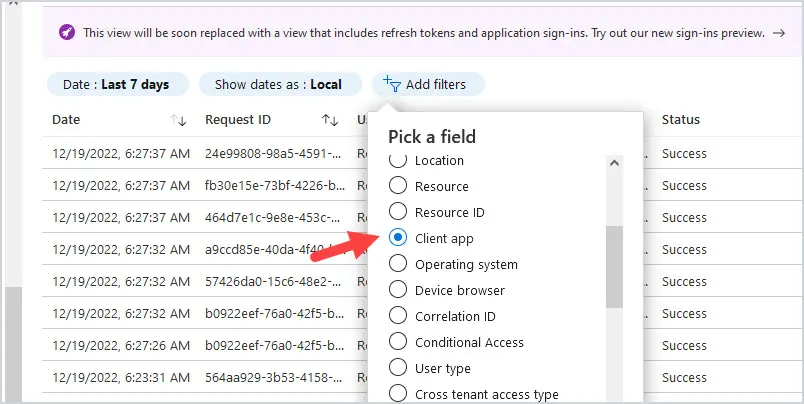
Then click on Client app: None Selected and select all options below Legacy Authentication clients, then click Apply.
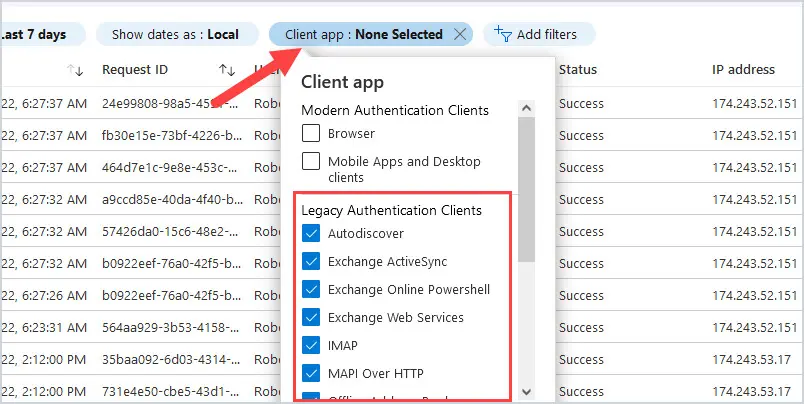
As you can see, the list of Legacy Authentication Protocols includes Autodiscover, Exchange ActiveSync, Exchange Online PowerShell, Exchange Web Services, IMAP, MAPI Over HTTP, Offline Address Book, other clients, Outlook Anywhere, POP, Reporting Web Services, SMTP, and Universal Outlook.
If you get any results back, then your organization is still using Legacy Authentication Protocols.
- If you are using any of these, chances are upgrading to the latest version of the Microsoft Outlook app on all devices, Windows, Apple, and Android, will resolve most of them. Make sure you choose Microsoft 365 as the account type when adding accounts with Mail Apps.
- For the Exchange Online PowerShell, make sure you are using the EXO V2 or EXO V3 module.
- For Exchange Web Services and Reporting Web Services, migrate apps to the Microsoft Graph API.
- Be sure to update any code and upgrade third-party applications using Basic Authentication to use Modern Authentication as well.
Microsoft is in the process of deprecating basic authentication in Exchange Online, which includes most of these protocols. It has been a slow rollout, but if this hasn’t happened for your tenant yet, expect it very soon and prepare. The rollout for the deprecation of these protocols started on October 1, 2022.
Here’s the official article from Microsoft.
Basic Authentication Deprecation in Exchange Online
Also, for those of you using printers, scanners, or apps that you are using Authenticated SMTP (SMTP Auth), this will eventually be deprecated as well. Consider setting up Direct Send or a connector instead of SMTP Auth. I always recommend using TLS whenever possible when sending emails from devices.
Here is the link to the Microsoft article to set this up. You will need to use Option 2 or 3.
How to set up a multifunction device or application to send email using Microsoft 365 or Office 365.
How do I check to see if Modern Authentication is turned on?
For tenants created before August 1, 2017, Modern Authentication is turned off by default. However, if your tenant was created after October 1, 2019, then Security Defaults are enabled by default.
If Security Defaults are enabled, then Modern Authentication is on and Legacy Authentication is blocked.
Timing-wise on that, it’s probably best to check.
To check your organization’s settings, go to https://admin.microsoft.com and select Settings, then Org Settings. Click on Modern Authentication.
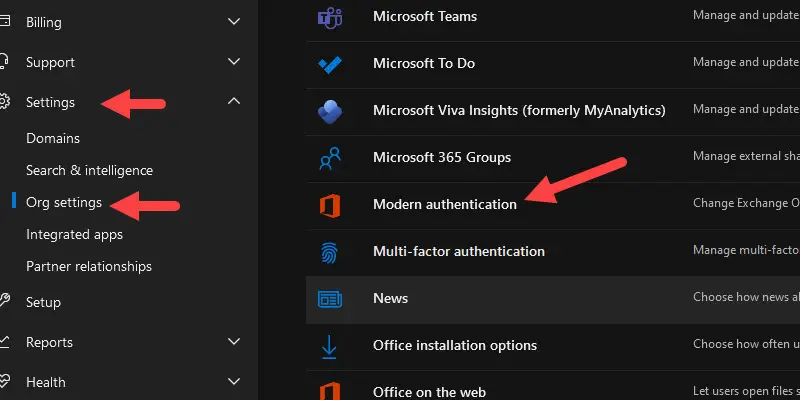
If Security Defaults are enabled, then you will see this screen. There is nothing else you need to do to make sure Modern Authentication is turned on if you get the screen below.
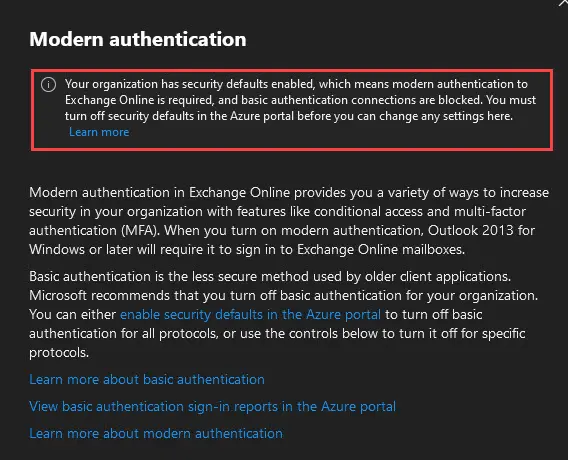
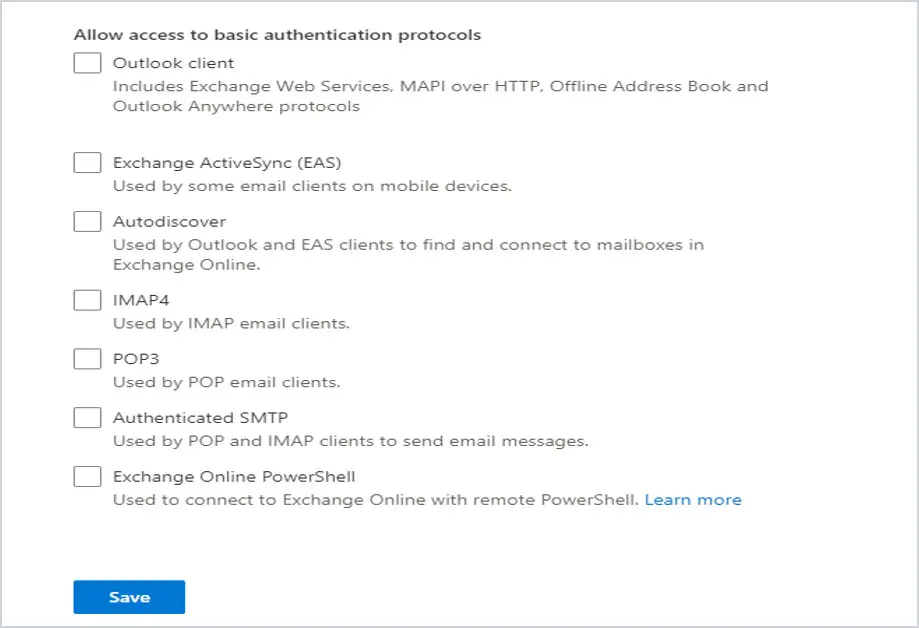
If you get the screen below, then Security Defaults are not enabled. If all the boxes below “Allow Access to basic authentication protocols” are checked, then that means Basic Authentication is enabled for these clients/apps/protocols.
How do I disable Legacy Authentication Protocols?
If you’ve reviewed your Sign-On logs in Azure Active Directory and are confident that your organization is not using any Legacy Authentication, then you should be ready to disable Legacy Authentication Protocols.
There are a few different ways you can do this. You can disable them via the Admin Center, enable security defaults, or use conditional access policies.
Option 1: Disable Legacy Authentication Protocols in the Admin Center
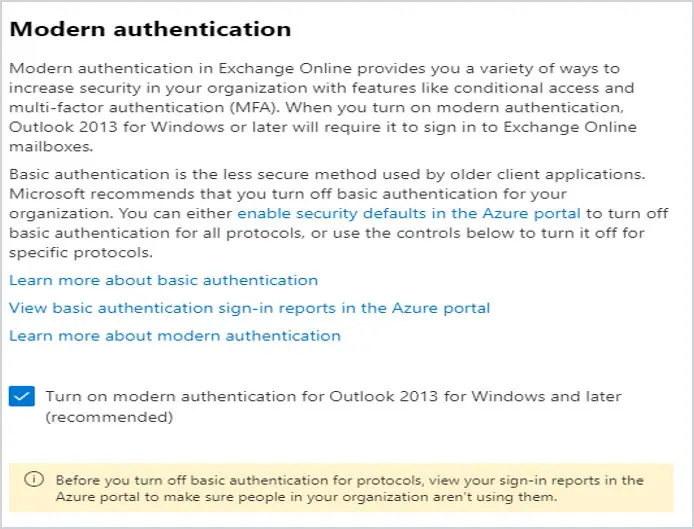
Go to https://admin.microsoft.com and select Settings, then Org Settings. Click on Modern Authentication.
Make sure that there is a check in the box to the left of Turn on Modern Authentication for Outlook 2013 for Windows and later. If there is not, put a checkmark in the box and click Save.
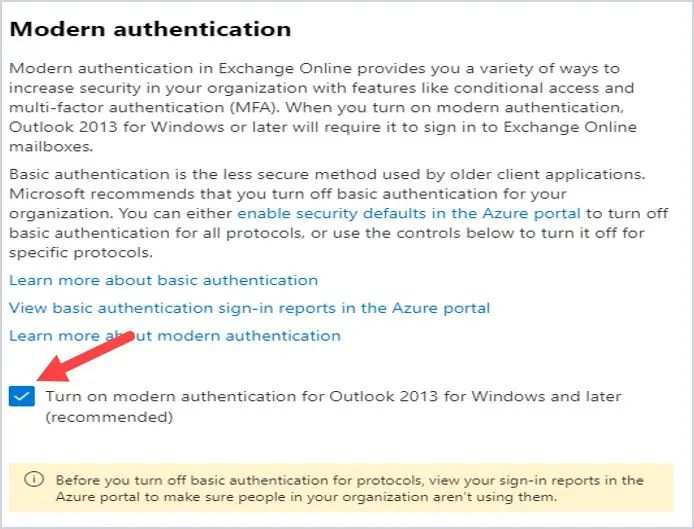
Then under “Allow access to basic authentication protocols”, uncheck the box for all of them and click Save at the bottom.
Option 2: Enable Security Defaults in Azure Active Directory
If you have a tenant that was created after October 21, 2019, then Security Defaults are enabled by default in Azure.
If not, then enabling Security Defaults should be planned out and your users should be notified beforehand. When you enable Security Defaults, users and admins are required to register for MFA using the Microsoft Authenticator app within 14 days or risk being locked out of the tenant. It also blocks legacy authentication protocols. So, you knock out turning on MFA and block Legacy Authentication all in one spot.
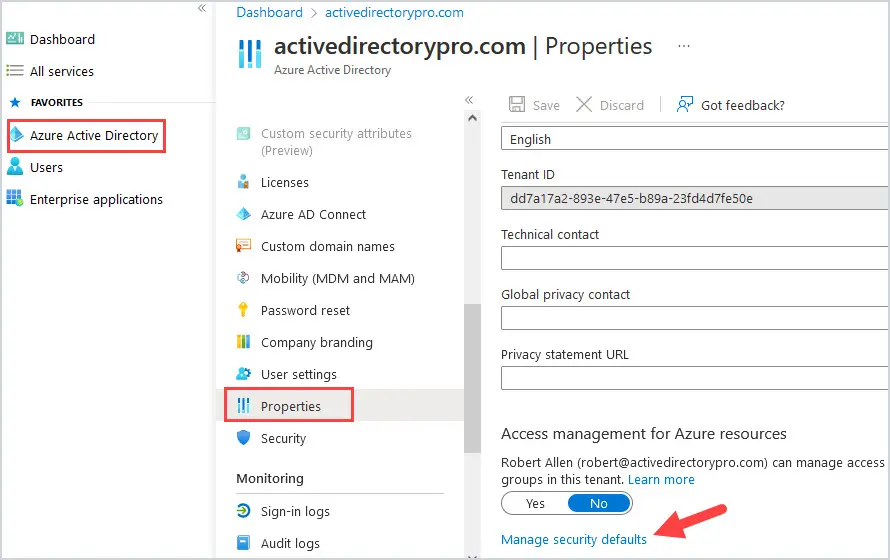
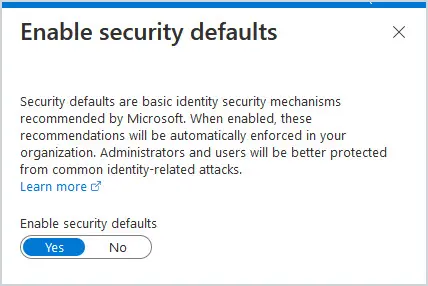
To see if Security Defaults are enabled in your tenant, login to your Azure Active Directory by going to https://aad.portal.azure.com and then click on Properties, then Manage Security Defaults at the bottom.
If it is set to Yes, then it is enabled for your tenant.
I would not enable Security Defaults if you are planning on implementing or already have Conditional Access Policies in place for your tenant. Also, if you are paying for Azure Active Directory P1 or P2 licenses, then using Conditional Access policies allows you more flexibility with your security policies.
Option 3: Conditional Access Policies
You can use Conditional Access Policies in Azure Active Directory to disable Legacy Protocols.
Go to https://aad.portal.azure.com and select Azure Active Directory. Click on Security and then Conditional Access.
We are going to create a rule to disable Legacy Authentication Protocols.
Click on New Policy and give the rule a unique and easily identifiable name.
For Assignments, select User and groups, then Include All Users and Exclude any users you don’t want to have Legacy Authentication disabled for.
IMPORTANT NOTE: ALWAYS exclude a Global Admin when setting up conditional access policies so you don’t lock yourself out of your tenant.
Under Conditions, select Client Apps, click Yes to Configure, and select Exchange ActiveSync clients and Other clients under Legacy Authentication clients.
Under Access Controls, click on Grant, then select Block access.
Leave your rule in Report-Only until you verify it is working as it should be and then turn it to On.
How to setup Multi Factor Authentication in Office 365
You can enable MFA for your tenant in Azure Active Directory by enabling Security Defaults, or by using Conditional Access policies. Enabling MFA on a per-user basis is not recommended.
Option 1: Enable MFA in Office 365 using Security Defaults
IMPORTANT NOTE: This method enables MFA for All users.
As mentioned above, you can enable Security Defaults to enable MFA for your tenant. With this method, you can’t exclude any users. All users, regardless of their role in your tenant, will have MFA turned on. Also, if you have per-user MFA turned on, you must turn it off before you can enable Security Defaults.
To enable Security Defaults in your tenant, login to your Azure Active Directory by going to https://aad.portal.azure.com and then click on Properties, then Manage Security Defaults at the bottom. Toggle Enable Security Defaults to Yes, then click Save.
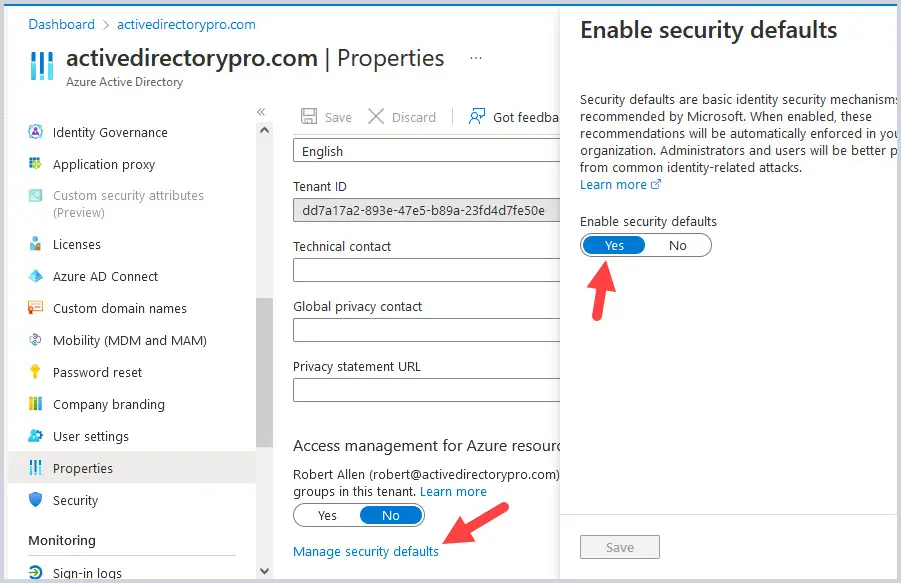
Option 2: Enable MFA in Office 365 using a Conditional Access Policy
You can use a Conditional Access Policy in Azure Active Directory to enable MFA. This allows you a lot more flexibility in including and excluding users, devices, and apps.
Conditional Access Policies require an Azure AD Premium P2 license.
You must turn off Security Defaults and per-user MFA before using Conditional Access policies.
Step 1: Go to https://aad.portal.azure.com and select Azure Active Directory. Click on Security and then Conditional Access.
We are going to create a rule to enable MFA.
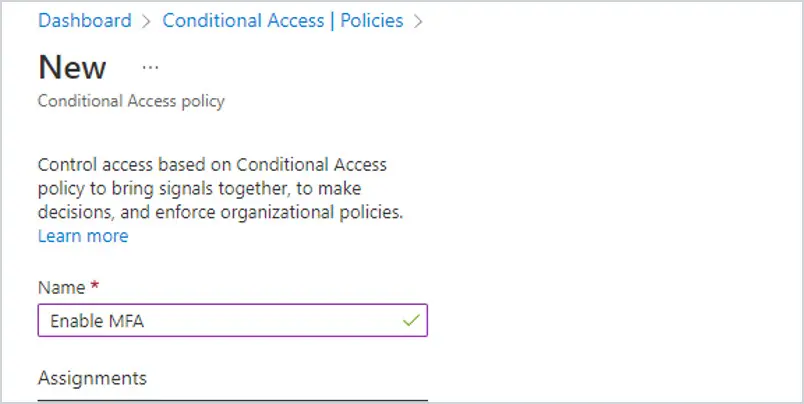
Step 2: Click on New Policy and give the rule a unique and easily identifiable name. In this example, I am naming the rule Enable MFA.
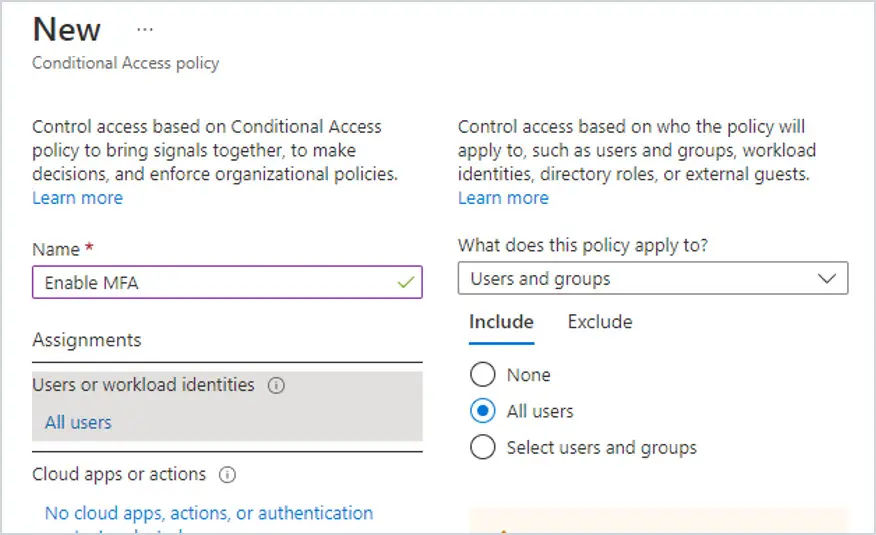
Step 3: Under Assignments, select User and groups, then select Include and choose All Users to enable it for everyone in your tenant.
Enable MFA For a Microsoft 365 Group
Instead of enabling MFA for all users, you can enable it for a specific group.
For instance, I wanted to roll MFA out slowly to my users to make sure the Helpdesk could handle the call volume, so I created a Microsoft 365 group called MFA Enabled. I added the users I wanted to enable it for to the group. Then, instead of choosing All Users, I chose the Microsoft 365 group I had created in Azure Active Directory.
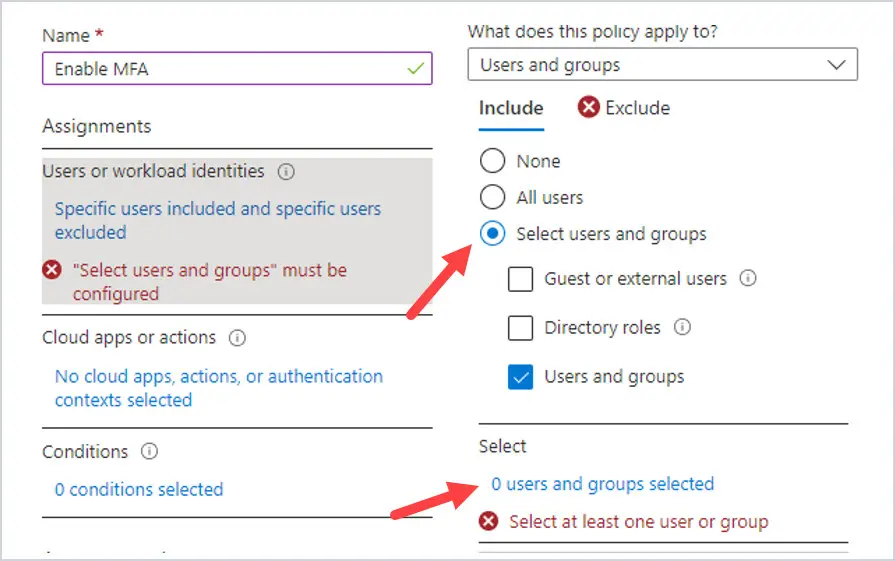
To use the group instead of All users, click on Select users and groups. Then click on where it says 0 users and groups selected.
Search for the group you want to add. In this case, I added group MFA Enabled. Click Select at the bottom.
Now I have the Microsoft 365 Group listed instead of All Users. MFA will ONLY be enabled for the users in this group.
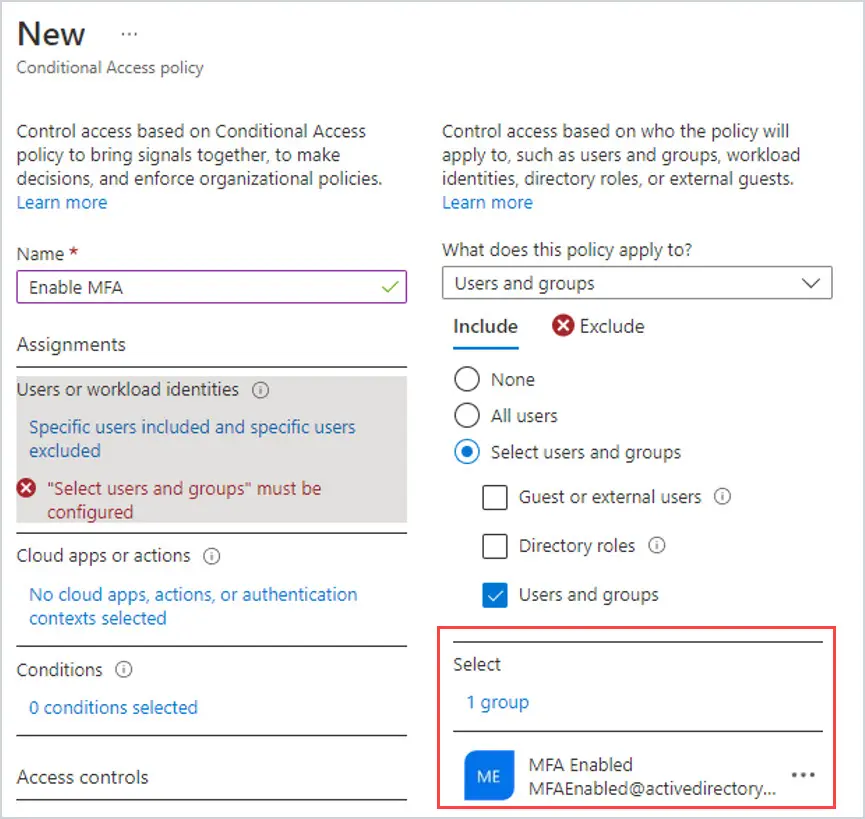
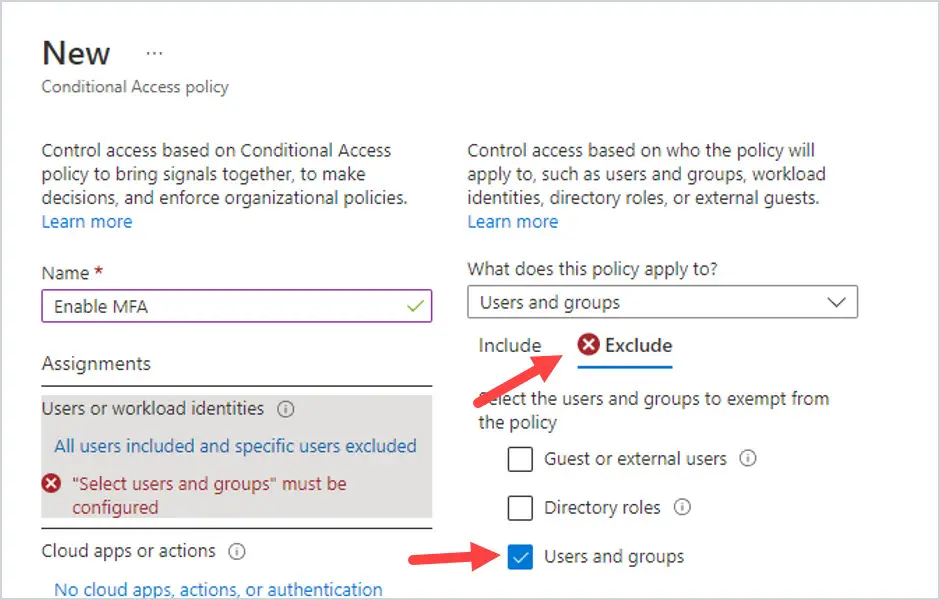
Next, click on Exclude and select Users and groups. Then click on where it says 0 users and groups selected. Add the users you want to Exclude from having MFA enabled. You can also use a Microsoft 365 Group here as well.
IMPORTANT NOTE: ALWAYS exclude a Global Admin when setting up conditional access policies so you don’t lock yourself out of your tenant.
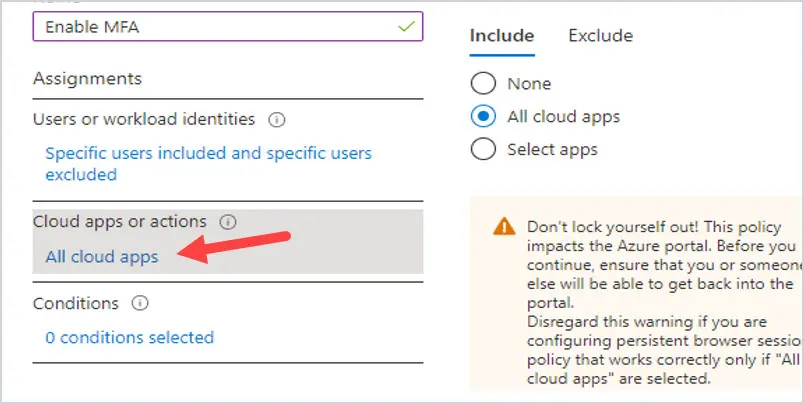
Next, under Cloud Apps or actions, you can include All cloud apps, or select apps. Under Include, select All cloud apps.
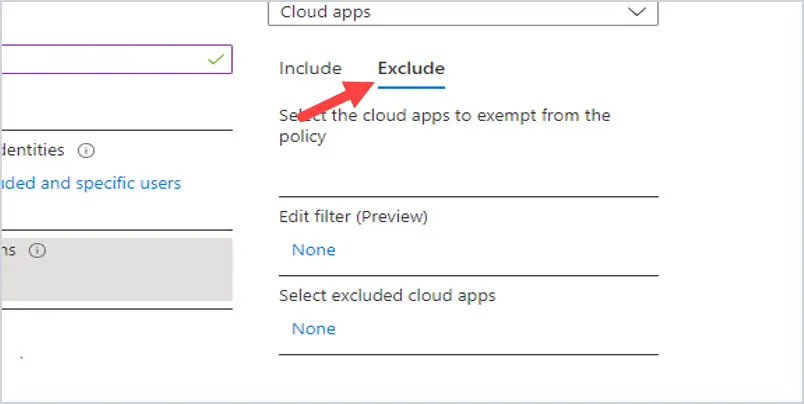
Then click on Exclude. Add any apps you want to exclude from requiring MFA by clicking on the None under Select excluded cloud apps.
Office 365 MFA Conditional Access Options
Conditions are optional. But, if you wanted, you could include or exclude apps, location, device, and OS.
For example, if you wanted to exclude the office where your users sit so that they are not being prompted for MFA while at work, you could add a Named Location under the Exclude under Locations.
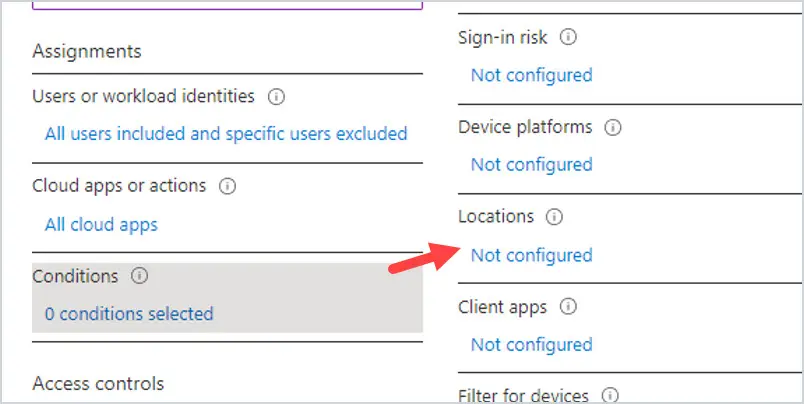
You can also exclude apps, and platforms by clicking on either option and configuring the settings.
How to Reset MFA Office 365 for a User
Sometimes a user gets a new phone and needs their MFA reset.
Go to https://aad.portal.azure.com and select Users. At the top of the screen, click on Per-user MFA.
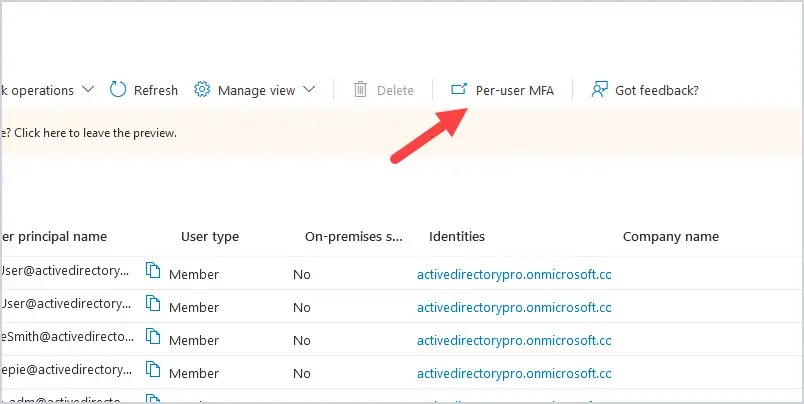
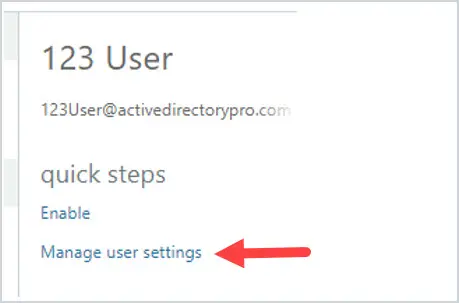
This will put up the multi-factor authentication page. Locate your user in the list and click on the user. In this case, I will choose 123 User.
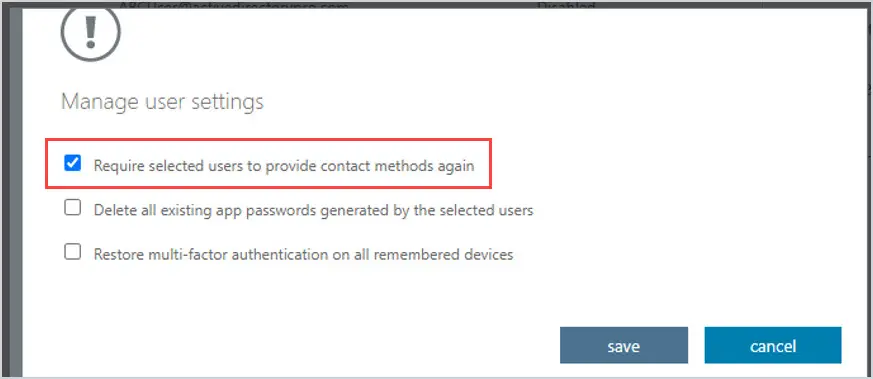
The Manage user settings box appears. Click on Require selected users to provide contact methods again. Click on Save.
Then have the user go to https://aka.ms/mfasetup to have them set up their MFA again.
I hope you found this guide useful. If you have questions or comments post them below.

I have become the admin of an organisation with about 150 users where MFA has always been managed individually per user resulting in us sometimes forgetting to enable MFA for new users. Security Defaults was never enabled (the tenant was created before this was the default). No conditional access policies are in place. We have dozens of guest accounts. I have read that to enable Security Defaults we should first disable per-user MFA. To me this looks difficult and maybe we would then risk phishing attack in the time window between disabling per-user MFA and enabling the Security Defaults. Would we have similar issues with enforcing MFA via conditional access? What would be the impact on guest users?
Any tips welcome.
Thanks,
Richard