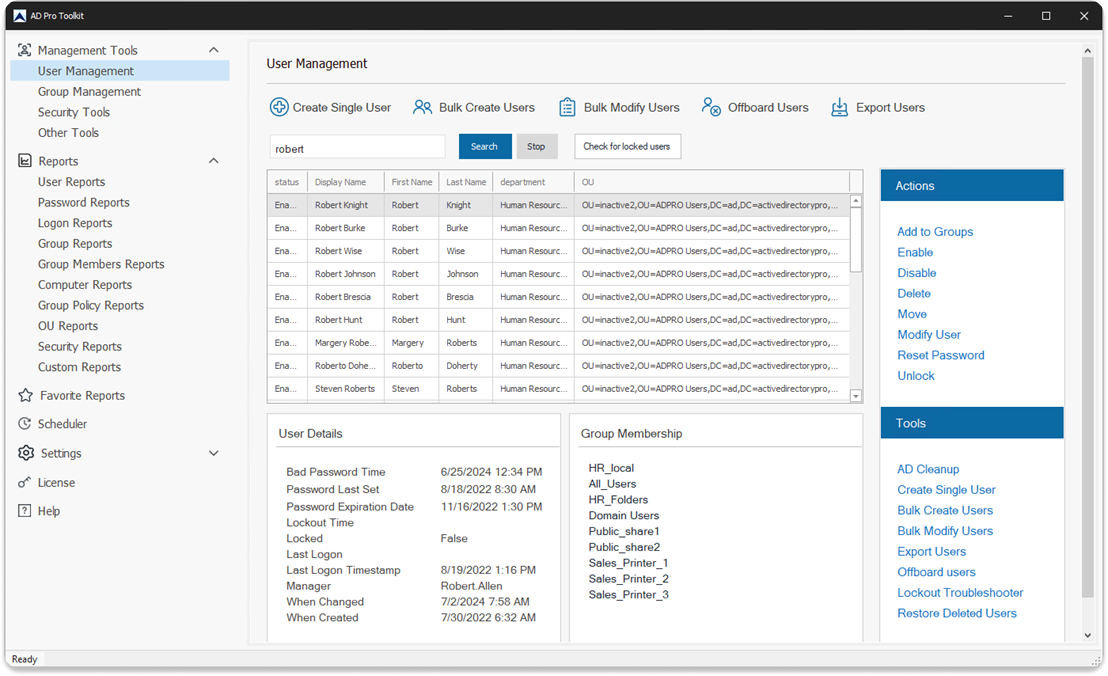
Below is a list of Active Directory event logs that are recommended to monitor for security and performance.
These AD event logs can be monitored with an Active Directory Audit Tool to quickly troubleshoot, audit
and detect potential security threats.
Refer to the article Signs of Active Directory Compromise Guide for more details on the event logs.
I’ve put the events into a table that can be searched and sorted.
| Event ID | Severity | Description | Category |
|---|---|---|---|
| 1102 | Medium to High | The audit log was cleared | |
| 4608 | Low | Windows is starting up. | Security State Change |
| 4609 | Low | Windows is shutting down. | Security State Change |
| 4610 | Low | An authentication package has been loaded by the Local Security Authority. | Security System Extension |
| 4611 | Low | A trusted logon process has been registered with the Local Security Authority. | Security System Extension |
| 4612 | Low | Internal resources allocated for the queuing of audit messages have been exhausted, leading to the loss of some audits. | System Integrity |
| 4614 | Low | A notification package has been loaded by the Security Account Manager. | Security System Extension |
| 4615 | Low | Invalid use of LPC port. | System Integrity |
| 4616 | Low | The system time was changed. | Security State Change |
| 4618 | High | A monitored security event pattern has occurred. | System Integrity |
| 4621 | Medium | Administrator recovered system from CrashOnAuditFail. Users who are not administrators will now be allowed to log on. Some auditable activity might not have been recorded. | Security State Change |
| 4622 | Low | A security package has been loaded by the Local Security Authority. | Security System Extension |
| 4624 | Low | An account was successfully logged on. | Logon |
| 4625 | Low | An account failed to log on. | logon |
| 4634 | Low | An account was logged off. | Logoff |
| 4646 | Low | IKE DoS-prevention mode started. | Ipsec Main Mode |
| 4647 | Low | User initiated logoff. | Logoff |
| 4648 | Low | A logon was attempted using explicit credentials. | Logon |
| 4649 | High | A replay attack was detected. May be a harmless false positive due to misconfiguration error. | Other Account Logon Events |
| 4650 | Low | An IPsec Main Mode security association was established. Extended Mode was not enabled. Certificate authentication was not used. | Ipsec Main Mode |
| 4651 | Low | An IPsec Main Mode security association was established. Extended Mode was not enabled. A certificate was used for authentication. | Ipsec Main Mode |
| 4652 | Low | An IPsec Main Mode negotiation failed. | Ipsec Main Mode |
| 4653 | Low | An IPsec Main Mode negotiation failed. | Ipsec Main Mode |
| 4654 | Low | An IPsec Quick Mode negotiation failed. | |
| 4655 | Low | An IPsec Main Mode security association ended. | Ipsec Main Mode |
| 4656 | Low | A handle to an object was requested. | Handle Manipulation |
| 4657 | Low | A registry value was modified. | Registry |
| 4658 | Low | The handle to an object was closed. | Handle Manipulation |
| 4659 | Low | A handle to an object was requested with intent to delete. | Kernal Object |
| 4660 | Low | An object was deleted. | Kernal Object |
| 4661 | Low | A handle to an object was requested. | Kernal Object |
| 4662 | Low | An operation was performed on an object. | Directory Service Access |
| 4663 | Low | An attempt was made to access an object. | Kernal Object |
| 4664 | Low | An attempt was made to create a hard link. | File System |
| 4665 | Low | An attempt was made to create an application client context. | Application Generated |
| 4666 | Low | An application attempted an operation: | Application Generated |
| 4667 | Low | An application client context was deleted. | Application Generated |
| 4668 | Low | An application was initialized. | Application Generated |
| 4670 | Low | Permissions on an object were changed. | Other Policy Change Events |
| 4671 | Low | An application attempted to access a blocked ordinal through the TBS. | Other Object Access Events |
| 4672 | Low | Special privileges assigned to new logon. | Sensitive Privilege Use |
| 4673 | Low | A privileged service was called. | Sensitive Privilege Use |
| 4674 | Low | An operation was attempted on a privileged object. | Sensitive Privilege Use |
| 4675 | Medium | SIDs were filtered. | Logon |
| 4688 | Low | A new process has been created. | Process Creation |
| 4689 | Low | A process has exited. | Process Termination |
| 4690 | Low | An attempt was made to duplicate a handle to an object. | Handle Manipulation |
| 4691 | Low | Indirect access to an object was requested. | Other Object Access Events |
| 4692 | Medium | Backup of data protection master key was attempted. | DPAPI Activity |
| 4693 | Medium | Recovery of data protection master key was attempted. | DPAPI Activity |
| 4694 | Low | Protection of auditable protected data was attempted. | DPAPI Activity |
| 4695 | Low | Unprotection of auditable protected data was attempted. | DPAPI Activity |
| 4696 | Low | A primary token was assigned to process. | Process Creation |
| 4697 | Low | Attempt to install a service | Security System Extension |
| 4698 | Low | A scheduled task was created. | Other Object Access Events |
| 4699 | Low | A scheduled task was deleted. | Other Object Access Events |
| 4700 | Low | A scheduled task was enabled. | Other Object Access Events |
| 4701 | Low | A scheduled task was disabled. | Other Object Access Events |
| 4702 | Low | A scheduled task was updated. | Other Object Access Events |
| 4704 | Low | A user right was assigned. | Authorization Police Change |
| 4705 | Low | A user right was removed. | Authorization Police Change |
| 4706 | Medium | A new trust was created to a domain. | Authorization Police Change |
| 4707 | Low | A trust to a domain was removed. | Authorization Police Change |
| 4709 | Low | IPsec Services was started. | Filtering Platform Policy Change |
| 4710 | Low | IPsec Services was disabled. | Filtering Platform Policy Change |
| 4711 | Low | May contain any one of the following: PAStore Engine applied locally cached copy of Active Directory storage IPsec policy on the computer. PAStore Engine applied Active Directory storage IPsec policy on the computer. PAStore Engine applied local registry storage IPsec policy on the computer. PAStore Engine failed to apply locally cached copy of Active Directory storage IPsec policy on the computer. PAStore Engine failed to apply Active Directory storage IPsec policy on the computer. PAStore Engine failed to apply local registry storage IPsec policy on the computer. PAStore Engine failed to apply some rules of the active IPsec policy on the computer. PAStore Engine failed to load directory storage IPsec policy on the computer. PAStore Engine loaded directory storage IPsec policy on the computer. PAStore Engine failed to load local storage IPsec policy on the computer. PAStore Engine loaded local storage IPsec policy on the computer.PAStore Engine polled for changes to the active IPsec policy and detected no changes. | Filtering Platform Policy Change |
| 4712 | Low | IPsec Services encountered a potentially serious failure. | |
| 4713 | Medium | Kerberos policy was changed. | Authentication Policy Change |
| 4714 | Medium | Encrypted data recovery policy was changed. | Authorization Police Change |
| 4715 | Medium | The audit policy (SACL) on an object was changed. | Audit Policy Change |
| 4716 | Medium | Trusted domain information was modified. | Authentication Policy Change |
| 4717 | Low | System security access was granted to an account. | Authentication Policy Change |
| 4718 | Low | System security access was removed from an account. | Authentication Policy Change |
| 4719 | High | System audit policy was changed. | Audit Policy Change |
| 4720 | Low | A user account was created. | User Account Management |
| 4722 | Low | A user account was enabled. | User Account Management |
| 4723 | Low | An attempt was made to change an account's password. | User Account Management |
| 4724 | Medium | An attempt was made to reset an account's password. | User Account Management |
| 4725 | Low | A user account was disabled. | User Account Management |
| 4726 | Low | A user account was deleted. | User Account Management |
| 4727 | Medium | A security-enabled global group was created. | Security Group Management |
| 4728 | Low | A member was added to a security-enabled global group. | Security Group Management |
| 4729 | Low | A member was removed from a security-enabled global group. | Security Group Management |
| 4730 | Low | A security-enabled global group was deleted. | Security Group Management |
| 4731 | Low | A security-enabled local group was created. | Security Group Management |
| 4732 | Low | A member was added to a security-enabled local group. | Security Group Management |
| 4733 | Low | A member was removed from a security-enabled local group. | Security Group Management |
| 4734 | Low | A security-enabled local group was deleted. | Security Group Management |
| 4735 | Medium | A security-enabled local group was changed. | Security Group Management |
| 4737 | Medium | A security-enabled global group was changed. | Security Group Management |
| 4738 | Low | A user account was changed. | User Account Management |
| 4739 | Medium | Domain Policy was changed. | Authentication Policy Change |
| 4740 | Low | A user account was locked out. | User Account Management |
| 4741 | Low | A computer account was changed. | Computer Account Management |
| 4742 | Low | A computer account was changed. | Computer Account Management |
| 4743 | Low | A computer account was deleted. | Computer Account Management |
| 4744 | Low | A security-disabled local group was created. | Distribution Group Management |
| 4745 | Low | A security-disabled local group was changed. | Distribution Group Management |
| 4746 | Low | A member was added to a security-disabled local group. | Distribution Group Management |
| 4747 | Low | A member was removed from a security-disabled local group. | Distribution Group Management |
| 4748 | Low | A security-disabled local group was deleted. | Distribution Group Management |
| 4749 | Low | A security-disabled global group was created. | Distribution Group Management |
| 4750 | Low | A security-disabled global group was changed. | Distribution Group Management |
| 4751 | Low | A member was added to a security-disabled global group. | Distribution Group Management |
| 4752 | Low | A member was removed from a security-disabled global group. | Distribution Group Management |
| 4753 | Low | A security-disabled global group was deleted. | Distribution Group Management |
| 4754 | Medium | A security-enabled universal group was created. | Security Group Management |
| 4755 | Medium | A security-enabled universal group was changed. | Security Group Management |
| 4756 | Low | A member was added to a security-enabled universal group. | Security Group Management |
| 4757 | Low | A member was removed from a security-enabled universal group. | Security Group Management |
| 4758 | Low | A security-enabled universal group was deleted. | Security Group Management |
| 4759 | Low | A security-disabled universal group was created. | Distribution Group Management |
| 4760 | Low | A security-disabled universal group was changed. | Distribution Group Management |
| 4761 | Low | A member was added to a security-disabled universal group. | Distribution Group Management |
| 4762 | Low | A member was removed from a security-disabled universal group. | Distribution Group Management |
| 4764 | Medium | A group's type was changed. | Security Group Management |
| 4765 | High | SID History was added to an account. | User Account Management |
| 4766 | High | An attempt to add SID History to an account failed. | User Account Management |
| 4767 | Low | A user account was unlocked. | User Account Management |
| 4768 | Low | A Kerberos authentication ticket (TGT) was requested. | Audit Kerberos Authentication Service |
| 4769 | Low | A Kerberos service ticket was requested. | Audit Kerberos Service Ticket Operations |
| 4770 | Low | A Kerberos service ticket was renewed. | Audit Kerberos Service Ticket Operations |
| 4771 | Low | Kerberos pre-authentication failed. | Audit Kerberos Authentication Service |
| 4772 | Low | A Kerberos authentication ticket request failed. | Audit Kerberos Authentication Service |
| 4774 | Low | An account was mapped for logon. | Audit Credential Validation |
| 4775 | Low | An account could not be mapped for logon. | Audit Credential Validation |
| 4776 | Low | The domain controller attempted to validate the credentials for an account. | Audit Credential Validation |
| 4777 | Low | The domain controller failed to validate the credentials for an account. | Audit Credential Validation |
| 4778 | Low | A session was reconnected to a Window Station. | Other Account Logon Events |
| 4779 | Low | A session was disconnected from a Window Station. | Other Account Logon Events |
| 4780 | Medium | The ACL was set on accounts which are members of administrators groups. | User Account Management |
| 4781 | Low | The name of an account was changed: | User Account Management |
| 4782 | Low | The password hash an account was accessed. | Other Account Management Events |
| 4783 | Low | A basic application group was created. | Application Group Management |
| 4784 | Low | A basic application group was changed. | Application Group Management |
| 4785 | Low | A member was added to a basic application group. | Application Group Management |
| 4786 | Low | A member was removed from a basic application group. | Application Group Management |
| 4787 | Low | A nonmember was added to a basic application group. | Application Group Management |
| 4788 | Low | A nonmember was removed from a basic application group. | Application Group Management |
| 4789 | Low | A basic application group was deleted. | Application Group Management |
| 4790 | Low | An LDAP query group was created. | Application Group Management |
| 4793 | Low | The Password Policy Checking API was called. | Other Account Management Events |
| 4794 | High | An attempt was made to set the Directory Services Restore Mode. | User Account Management |
| 4800 | Low | The workstation was locked. | Other Account Logon Events |
| 4801 | Low | The workstation was unlocked. | Other Account Logon Events |
| 4802 | Low | The screen saver was invoked. | Other Account Logon Events |
| 4803 | Low | The screen saver was dismissed. | Other Account Logon Events |
| 4816 | Medium | RPC detected an integrity violation while decrypting an incoming message. | System Integrity |
| 4817 | Auditing settings on object were changed. | Audit Policy Change | |
| 4864 | Low | A namespace collision was detected. | Authentication Policy Change |
| 4865 | Medium | A trusted forest information entry was added. | Authentication Policy Change |
| 4866 | Medium | A trusted forest information entry was removed. | Authentication Policy Change |
| 4867 | Medium | A trusted forest information entry was modified. | Authentication Policy Change |
| 4868 | Medium | The certificate manager denied a pending certificate request. | Certification Services |
| 4869 | Low | Certificate Services received a resubmitted certificate request. | Certification Services |
| 4870 | Medium | Certificate Services revoked a certificate. | Certification Services |
| 4871 | Low | Certificate Services received a request to publish the certificate revocation list (CRL). | Certification Services |
| 4872 | Low | Certificate Services published the certificate revocation list (CRL). | Certification Services |
| 4873 | Low | A certificate request extension changed. | Certification Services |
| 4874 | Low | One or more certificate request attributes changed. | Certification Services |
| 4875 | Low | Certificate Services received a request to shut down. | Certification Services |
| 4876 | Low | Certificate Services backup started. | Certification Services |
| 4877 | Low | Certificate Services backup completed. | Certification Services |
| 4878 | Low | Certificate Services restore started. | Certification Services |
| 4879 | Low | Certificate Services restore completed. | Certification Services |
| 4880 | Low | Certificate Services started. | Certification Services |
| 4881 | Low | Certificate Services stopped. | Certification Services |
| 4882 | Medium | The security permissions for Certificate Services changed. | Certification Services |
| 4883 | Low | Certificate Services retrieved an archived key. | Certification Services |
| 4884 | Low | Certificate Services imported a certificate into its database. | Certification Services |
| 4885 | Medium | The audit filter for Certificate Services changed. | Certification Services |
| 4886 | Low | Certificate Services received a certificate request. | Certification Services |
| 4887 | Low | Certificate Services approved a certificate request and issued a certificate. | Certification Services |
| 4888 | Low | Certificate Services denied a certificate request. | Certification Services |
| 4889 | Low | Certificate Services set the status of a certificate request to pending. | Certification Services |
| 4890 | Medium | The certificate manager settings for Certificate Services changed. | Certification Services |
| 4891 | Low | A configuration entry changed in Certificate Services. | Certification Services |
| 4892 | Medium | A property of Certificate Services changed. | Certification Services |
| 4893 | Low | Certificate Services archived a key. | Certification Services |
| 4894 | Low | Certificate Services imported and archived a key. | Certification Services |
| 4895 | Low | Certificate Services published the CA certificate to Active Directory Domain Services. | Certification Services |
| 4896 | Medium | One or more rows have been deleted from the certificate database. | Certification Services |
| 4897 | High | Role separation enabled: | Certification Services |
| 4898 | Low | Certificate Services loaded a template. | Certification Services |
| 4902 | Low | The Per-user audit policy table was created. | Audit Policy Change |
| 4904 | Low | An attempt was made to register a security event source. | Audit Policy Change |
| 4905 | Low | An attempt was made to unregister a security event source. | Audit Policy Change |
| 4906 | Medium | The CrashOnAuditFail value has changed. | Audit Policy Change |
| 4907 | Medium | Auditing settings on object were changed. | Audit Policy Change |
| 4908 | Medium | Special Groups Logon table modified. | Audit Policy Change |
| 4909 | Low | The local policy settings for the TBS were changed. | Other Policy Change Events |
| 4910 | Low | The Group Policy settings for the TBS were changed. | Other Policy Change Events |
| 4912 | Medium | Per User Audit Policy was changed. | Audit Policy Change |
| 4928 | Low | An Active Directory replica source naming context was established. | Detailed Directory Service Replication |
| 4929 | Low | An Active Directory replica source naming context was removed. | Detailed Directory Service Replication |
| 4930 | Low | An Active Directory replica source naming context was modified. | Detailed Directory Service Replication |
| 4931 | Low | An Active Directory replica destination naming context was modified. | Detailed Directory Service Replication |
| 4932 | Low | Synchronization of a replica of an Active Directory naming context has begun. | Directory Service Replication |
| 4933 | Low | Synchronization of a replica of an Active Directory naming context has ended. | Directory Service Replication |
| 4934 | Low | Attributes of an Active Directory object were replicated. | Detailed Directory Service Replication |
| 4935 | Low | Replication failure begins. | Detailed Directory Service Replication |
| 4936 | Low | Replication failure ends. | Detailed Directory Service Replication |
| 4937 | Low | A lingering object was removed from a replica. | Detailed Directory Service Replication |
| 4944 | Low | The following policy was active when the Windows Firewall started. | MPSSVC Rule Level Policy Change |
| 4945 | Low | A rule was listed when the Windows Firewall started. | MPSSVC Rule Level Policy Change |
| 4946 | Low | A change has been made to Windows Firewall exception list. A rule was added. | MPSSVC Rule Level Policy Change |
| 4947 | Low | A change has been made to Windows Firewall exception list. A rule was modified. | MPSSVC Rule Level Policy Change |
| 4948 | Low | A change has been made to Windows Firewall exception list. A rule was deleted. | MPSSVC Rule Level Policy Change |
| 4949 | Low | Windows Firewall settings were restored to the default values. | MPSSVC Rule Level Policy Change |
| 4950 | Low | A Windows Firewall setting has changed. | MPSSVC Rule Level Policy Change |
| 4951 | Low | A rule has been ignored because its major version number was not recognized by Windows Firewall. | MPSSVC Rule Level Policy Change |
| 4952 | Low | Parts of a rule have been ignored because its minor version number was not recognized by Windows Firewall. The other parts of the rule will be enforced. | MPSSVC Rule Level Policy Change |
| 4953 | Low | A rule has been ignored by Windows Firewall because it could not parse the rule. | MPSSVC Rule Level Policy Change |
| 4954 | Low | Windows Firewall Group Policy settings have changed. The new settings have been applied. | MPSSVC Rule Level Policy Change |
| 4956 | Low | Windows Firewall has changed the active profile. | MPSSVC Rule Level Policy Change |
| 4957 | Low | Windows Firewall did not apply the following rule: | MPSSVC Rule Level Policy Change |
| 4958 | Low | Windows Firewall did not apply the following rule because the rule referred to items not configured on this computer: | MPSSVC Rule Level Policy Change |
| 4960 | Medium | IPsec dropped an inbound packet that failed an integrity check. If this problem persists, it could indicate a network issue or that packets are being modified in transit to this computer. Verify that the packets sent from the remote computer are the same as those received by this computer. This error might also indicate interoperability problems with other IPsec implementations. | Ipsec Driver |
| 4961 | Medium | IPsec dropped an inbound packet that failed a replay check. If this problem persists, it could indicate a replay attack against this computer. | Ipsec Driver |
| 4962 | Medium | IPsec dropped an inbound packet that failed a replay check. The inbound packet had too low a sequence number to ensure it was not a replay. | Ipsec Driver |
| 4963 | Medium | IPsec dropped an inbound clear text packet that should have been secured. This is usually due to the remote computer changing its IPsec policy without informing this computer. This could also be a spoofing attack attempt. | Ipsec Driver |
| 4964 | High | Special groups have been assigned to a new logon. | Special Logon |
| 4965 | Medium | IPsec received a packet from a remote computer with an incorrect Security Parameter Index (SPI). This is usually caused by malfunctioning hardware that is corrupting packets. If these errors persist, verify that the packets sent from the remote computer are the same as those received by this computer. This error may also indicate interoperability problems with other IPsec implementations. In that case, if connectivity is not impeded, then these events can be ignored. | Ipsec Driver |
| 4976 | Medium | During Main Mode negotiation, IPsec received an invalid negotiation packet. If this problem persists, it could indicate a network issue or an attempt to modify or replay this negotiation. | Ipsec Main Mode |
| 4977 | Medium | During Quick Mode negotiation, IPsec received an invalid negotiation packet. If this problem persists, it could indicate a network issue or an attempt to modify or replay this negotiation. | ipsec quick mode |
| 4978 | Medium | During Extended Mode negotiation, IPsec received an invalid negotiation packet. If this problem persists, it could indicate a network issue or an attempt to modify or replay this negotiation. | Ipsec Extended Mode |
| 4979 | Low | IPsec Main Mode and Extended Mode security associations were established. | Ipsec Extended Mode |
| 4980 | Low | IPsec Main Mode and Extended Mode security associations were established. | Ipsec Extended Mode |
| 4981 | Low | IPsec Main Mode and Extended Mode security associations were established. | Ipsec Extended Mode |
| 4982 | Low | IPsec Main Mode and Extended Mode security associations were established. | Ipsec Extended Mode |
| 4983 | Medium | An IPsec Extended Mode negotiation failed. The corresponding Main Mode security association has been deleted. | Ipsec Extended Mode |
| 4984 | Medium | An IPsec Extended Mode negotiation failed. The corresponding Main Mode security association has been deleted. | Ipsec Extended Mode |
| 4985 | Low | The state of a transaction has changed. | File System |
| 5024 | Low | The Windows Firewall Service has started successfully. | |
| 5025 | Low | The Windows Firewall Service has been stopped. | |
| 5027 | Medium | The Windows Firewall Service was unable to retrieve the security policy from the local storage. The service will continue enforcing the current policy. | |
| 5028 | Medium | The Windows Firewall Service was unable to parse the new security policy. The service will continue with currently enforced policy. | |
| 5029 | Medium | The Windows Firewall Service failed to initialize the driver. The service will continue to enforce the current policy. | |
| 5030 | Medium | The Windows Firewall Service failed to start. | |
| 5031 | Low | The Windows Firewall Service blocked an application from accepting incoming connections on the network. | Filtering Platform Connection |
| 5032 | Low | Windows Firewall was unable to notify the user that it blocked an application from accepting incoming connections on the network. | |
| 5033 | Low | The Windows Firewall Driver has started successfully. | |
| 5034 | Low | The Windows Firewall Driver has been stopped. | |
| 5035 | Medium | The Windows Firewall Driver failed to start. | |
| 5037 | Medium | The Windows Firewall Driver detected critical runtime error. Terminating. | |
| 5038 | Medium | Code integrity determined that the image hash of a file is not valid. The file could be corrupt due to unauthorized modification or the invalid hash could indicate a potential disk device error. | System Integrity |
| 5039 | Low | A registry key was virtualized. | Registry |
| 5040 | Low | A change has been made to IPsec settings. An Authentication Set was added. | |
| 5041 | Low | A change has been made to IPsec settings. An Authentication Set was modified. | |
| 5042 | Low | A change has been made to IPsec settings. An Authentication Set was deleted. | |
| 5043 | Low | A change has been made to IPsec settings. A Connection Security Rule was added. | |
| 5044 | Low | A change has been made to IPsec settings. A Connection Security Rule was modified. | |
| 5045 | Low | A change has been made to IPsec settings. A Connection Security Rule was deleted. | |
| 5046 | Low | A change has been made to IPsec settings. A Crypto Set was added. | |
| 5047 | Low | A change has been made to IPsec settings. A Crypto Set was modified. | |
| 5048 | Low | A change has been made to IPsec settings. A Crypto Set was deleted. | |
| 5049 | Low | An IPsec Security Association was deleted. | Ipsec Main Mode |
| 5050 | Low | An attempt to programmatically disable the Windows Firewall using a call to InetFwProfile.FirewallEnabled(False) | |
| 5051 | Low | A file was virtualized. | File System |
| 5056 | Low | A cryptographic self test was performed. | System Integrity |
| 5057 | Low | A cryptographic primitive operation failed. | System Integrity |
| 5058 | Low | Key file operation. | |
| 5059 | Low | Key migration operation. | |
| 5060 | Low | Verification operation failed. | System Integrity |
| 5061 | Low | Cryptographic operation. | System Integrity |
| 5062 | Low | A kernel-mode cryptographic self test was performed. | System Integrity |
| 5063 | Low | A cryptographic provider operation was attempted. | Other Policy Change Events |
| 5064 | Low | A cryptographic context operation was attempted. | Other Policy Change Events |
| 5065 | Low | A cryptographic context modification was attempted. | Other Policy Change Events |
| 5066 | Low | A cryptographic function operation was attempted. | Other Policy Change Events |
| 5067 | Low | A cryptographic function modification was attempted. | Other Policy Change Events |
| 5068 | Low | A cryptographic function provider operation was attempted. | Other Policy Change Events |
| 5069 | Low | A cryptographic function property operation was attempted. | Other Policy Change Events |
| 5070 | Low | A cryptographic function property modification was attempted. | Other Policy Change Events |
| 5120 | Medium | OCSP Responder Service Started | |
| 5121 | Medium | OCSP Responder Service Stopped | |
| 5122 | Medium | A configuration entry changed in OCSP Responder Service | |
| 5123 | Medium | A configuration entry changed in OCSP Responder Service | |
| 5124 | High | A security setting was updated on the OCSP Responder Service | |
| 5125 | Low | A request was submitted to the OCSP Responder Service | |
| 5126 | Low | Signing Certificate was automatically updated by the OCSP Responder Service | |
| 5127 | Low | The OCSP Revocation Provider successfully updated the revocation information | |
| 5136 | Low | A directory service object was modified. | Directry Service Changes |
| 5137 | Low | A directory service object was created. | Directry Service Changes |
| 5138 | Low | A directory service object was undeleted. | Directry Service Changes |
| 5139 | Low | A directory service object was moved. | Directry Service Changes |
| 5140 | Low | A network share object was accessed. | File Share |
| 5141 | Low | A directory service object was deleted. | Directry Service Changes |
| 5152 | Low | The Windows Filtering Platform blocked a packet. | Filtering Platform Packet Drop |
| 5153 | Low | A more restrictive Windows Filtering Platform filter has blocked a packet. | Filtering Platform Packet Drop |
| 5154 | Low | The Windows Filtering Platform has permitted an application or service to listen on a port for incoming connections. | Detailed File Share |
| 5155 | Low | The Windows Filtering Platform has blocked an application or service from listening on a port for incoming connections. | Filtering Platform Connection |
| 5156 | Low | The Windows Filtering Platform has allowed a connection. | Filtering Platform Connection |
| 5157 | Low | The Windows Filtering Platform has blocked a connection. | Filtering Platform Connection |
| 5158 | Low | The Windows Filtering Platform has permitted a bind to a local port. | Filtering Platform Connection |
| 5159 | Low | The Windows Filtering Platform has blocked a bind to a local port. | Filtering Platform Connection |
| 5376 | Medium | Credential Manager credentials were backed up. | User Account Management |
| 5377 | Medium | Credential Manager credentials were restored from a backup. | User Account Management |
| 5378 | Low | The requested credentials delegation was disallowed by policy. | Other Account Logon Events |
| 5440 | Low | The following callout was present when the Windows Filtering Platform Base Filtering Engine started. | |
| 5441 | Low | The following filter was present when the Windows Filtering Platform Base Filtering Engine started. | |
| 5442 | Low | The following provider was present when the Windows Filtering Platform Base Filtering Engine started. | |
| 5443 | Low | The following provider context was present when the Windows Filtering Platform Base Filtering Engine started. | |
| 5444 | Low | The following sublayer was present when the Windows Filtering Platform Base Filtering Engine started. | |
| 5446 | Low | A Windows Filtering Platform callout has been changed. | |
| 5447 | Low | A Windows Filtering Platform filter has been changed. | Other Policy Change Events |
| 5448 | Low | A Windows Filtering Platform provider has been changed. | |
| 5449 | Low | A Windows Filtering Platform provider context has been changed. | |
| 5450 | Low | A Windows Filtering Platform sublayer has been changed. | |
| 5451 | Low | An IPsec Quick Mode security association was established. | ipsec quick mode |
| 5452 | Low | An IPsec Quick Mode security association ended. | ipsec quick mode |
| 5453 | Medium | An IPsec negotiation with a remote computer failed because the IKE and AuthIP IPsec Keying Modules (IKEEXT) service is not started. | Ipsec Main Mode |
| 5456 | Low | PAStore Engine applied Active Directory storage IPsec policy on the computer. | |
| 5457 | Low | PAStore Engine failed to apply Active Directory storage IPsec policy on the computer. | |
| 5458 | Low | PAStore Engine applied locally cached copy of Active Directory storage IPsec policy on the computer. | |
| 5459 | Low | PAStore Engine failed to apply locally cached copy of Active Directory storage IPsec policy on the computer. | |
| 5460 | Low | PAStore Engine applied local registry storage IPsec policy on the computer. | |
| 5461 | Low | PAStore Engine failed to apply local registry storage IPsec policy on the computer. | |
| 5462 | Low | PAStore Engine failed to apply some rules of the active IPsec policy on the computer. Use the IP Security Monitor snap-in to diagnose the problem. | |
| 5463 | Low | PAStore Engine polled for changes to the active IPsec policy and detected no changes. | |
| 5464 | Low | PAStore Engine polled for changes to the active IPsec policy, detected changes, and applied them to IPsec Services. | |
| 5465 | Low | PAStore Engine received a control for forced reloading of IPsec policy and processed the control successfully. | |
| 5466 | Low | PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory cannot be reached, and will use the cached copy of the Active Directory IPsec policy instead. Any changes made to the Active Directory IPsec policy since the last poll could not be applied. | |
| 5467 | Low | PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory can be reached, and found no changes to the policy. The cached copy of the Active Directory IPsec policy is no longer being used. | |
| 5468 | Low | PAStore Engine polled for changes to the Active Directory IPsec policy, determined that Active Directory can be reached, found changes to the policy, and applied those changes. The cached copy of the Active Directory IPsec policy is no longer being used. | |
| 5471 | Low | PAStore Engine loaded local storage IPsec policy on the computer. | |
| 5472 | Low | PAStore Engine failed to load local storage IPsec policy on the computer. | |
| 5473 | Low | PAStore Engine loaded directory storage IPsec policy on the computer. | |
| 5474 | Low | PAStore Engine failed to load directory storage IPsec policy on the computer. | |
| 5477 | Low | PAStore Engine failed to add quick mode filter. | |
| 5478 | Low | IPsec Services has started successfully. | Ipsec Driver |
| 5479 | Low | IPsec Services has been shut down successfully. The shutdown of IPsec Services can put the computer at greater risk of network attack or expose the computer to potential security risks. | Ipsec Driver |
| 5480 | Medium | IPsec Services failed to get the complete list of network interfaces on the computer. This poses a potential security risk because some of the network interfaces may not get the protection provided by the applied IPsec filters. Use the IP Security Monitor snap-in to diagnose the problem. | Ipsec Driver |
| 5483 | Medium | IPsec Services failed to initialize RPC server. IPsec Services could not be started. | Ipsec Driver |
| 5484 | Medium | IPsec Services has experienced a critical failure and has been shut down. The shutdown of IPsec Services can put the computer at greater risk of network attack or expose the computer to potential security risks. | Ipsec Driver |
| 5485 | Medium | IPsec Services failed to process some IPsec filters on a plug-and-play event for network interfaces. This poses a potential security risk because some of the network interfaces may not get the protection provided by the applied IPsec filters. Use the IP Security Monitor snap-in to diagnose the problem. | Ipsec Driver |
| 5632 | Low | A request was made to authenticate to a wireless network. | Other Account Logon Events |
| 5633 | Low | A request was made to authenticate to a wired network. | Other Account Logon Events |
| 5712 | Low | A Remote Procedure Call (RPC) was attempted. | RPC Events |
| 5827 | Medium | The Netlogon service denied a vulnerable Netlogon secure channel connection from a machine account. | |
| 5828 | Medium | The Netlogon service denied a vulnerable Netlogon secure channel connection using a trust account. | |
| 5888 | Low | An object in the COM+ Catalog was modified. | Other Object Access Events |
| 5889 | Low | An object was deleted from the COM+ Catalog. | Other Object Access Events |
| 5890 | Low | An object was added to the COM+ Catalog. | Other Object Access Events |
| 6008 | Low | The previous system shutdown was unexpected | |
| 6144 | Low | Security policy in the Group Policy objects has been applied successfully. | Other Policy Change Events |
| 6145 | Medium | One or more errors occurred while processing security policy in the Group Policy objects. | Other Policy Change Events |
| 6272 | Low | Network Policy Server granted access to a user. | Network Policy Server |
| 6273 | Medium | Network Policy Server denied access to a user. | Network Policy Server |
| 6274 | Medium | Network Policy Server discarded the request for a user. | Network Policy Server |
| 6275 | Medium | Network Policy Server discarded the accounting request for a user. | Network Policy Server |
| 6276 | Medium | Network Policy Server quarantined a user. | Network Policy Server |
| 6277 | Medium | Network Policy Server granted access to a user but put it on probation because the host did not meet the defined health policy. | Network Policy Server |
| 6278 | Medium | Network Policy Server granted full access to a user because the host met the defined health policy. | Network Policy Server |
| 6279 | Medium | Network Policy Server locked the user account due to repeated failed authentication attempts. | Network Policy Server |
| 6280 | Medium | Network Policy Server unlocked the user account. | Network Policy Server |
| 24577 | Low | Encryption of volume started | |
| 24578 | Low | Encryption of volume stopped | |
| 24579 | Low | Encryption of volume completed | |
| 24580 | Low | Decryption of volume started | |
| 24581 | Low | Decryption of volume stopped | |
| 24582 | Low | Decryption of volume completed | |
| 24583 | Low | Conversion worker thread for volume started | |
| 24584 | Low | Conversion worker thread for volume temporarily stopped | |
| 24586 | Medium | An error was encountered converting volume | |
| 24588 | Low | The conversion operation on volume %2 encountered a bad sector error. Please validate the data on this volume | |
| 24592 | Medium | An attempt to automatically restart conversion on volume %2 failed. | |
| 24593 | Medium | Metadata write: Volume %2 returning errors while trying to modify metadata. If failures continue, decrypt volume | |
| 24594 | Medium | Metadata rebuild: An attempt to write a copy of metadata on volume %2 failed and may appear as disk corruption. If failures continue, decrypt volume. | |
| 24595 | Low | Volume %2 contains bad clusters. These clusters will be skipped during conversion. | |
| 24621 | Low | Initial state check: Rolling volume conversion transaction on %2. | |
| - | Medium | General account database changed | |
| - | Medium | Quality of Service Policy changed | |
| N/A | Medium to High | Possible denial-of-service (DoS) attack | |
| N/A | Low | A handle to an object was requested. | |
| N/A | Low | Object open for delete | |
| N/A | Low | User Account Type Changed | |
| N/A | Low | IPsec policy agent started | |
| N/A | Low | IPsec policy agent disabled | |
| N/A | Low | IPsec policy agent | |
| N/A | Low | IPsec policy agent encountered a potential serious failure |
Refer to the Active Directory Audit Checklist to learn about which audit policy settings to enable. Without the correct policy settings enabled the Active Directory logs will not be generated.