In this post, I will show you how to list all domain controllers with PowerShell.
To list all domain controllers the Get-ADDomainController PowerShell cmdlet is used. The Get-ADDomainController cmdlet can get all domain controllers or list specific ones with the various search parameters.
Let’s get started!
Example 1: List all domain controllers in the domain
This command will list the name of each domain controller only, with no additional info.
Get-ADDomainController -filter * | Select-Object name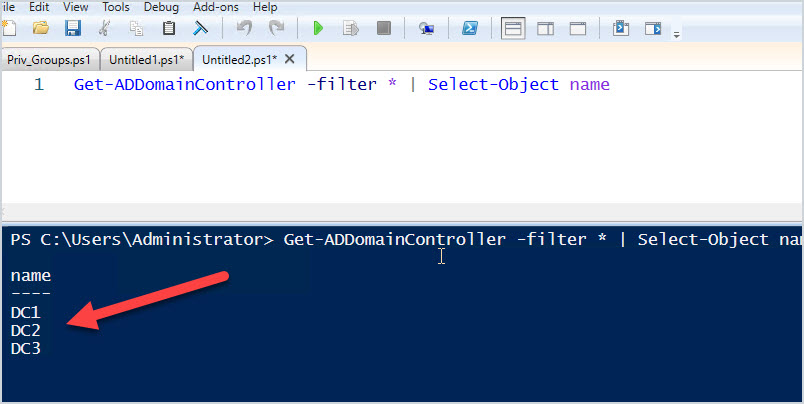
Example 2: List all domain controllers (with full details)
If you want more details like the domain name, forest, IP address, etc use this command.
Get-ADDomainController -filter * 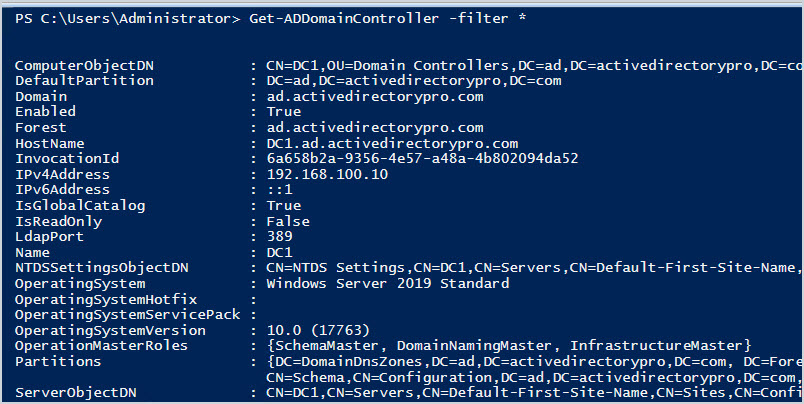
In the above screenshot, you can see this command provides a lot of information on each domain controller. You can use the select object command to list only specific details. The next example will demonstrate this.
Example 3: List Domain Controllers in another domain
To list domain controllers from another domain you can use the -server parameter and then the fully qualified domain name. This example uses select to display just the Name, Domain, Forest, IP address, and site details.
Get-ADDomainController -server arizona.ad.activedirectorypro.com | Select Name, Domain, Forest, IPv4Address, SiteExample 4: List Domain Controllers with Site Information
There is no simple command to list domain controllers from a specific site. So you can list them all and include the site information in the output.
Get-ADDomainController -Filter * | Select hostname, site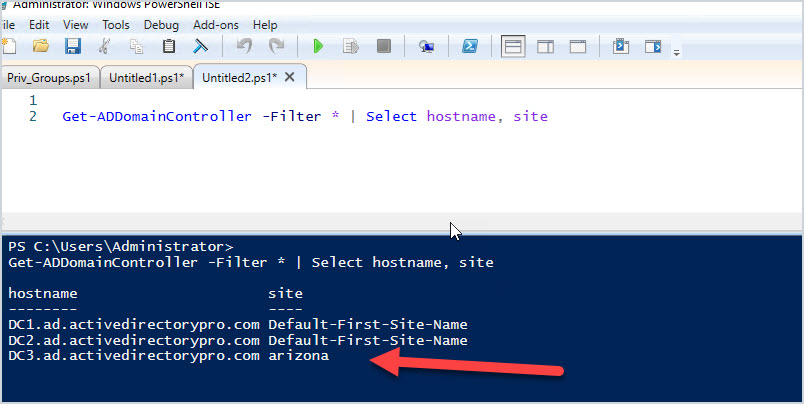
In the screenshot above you can see I have two domain controllers in one site and another dc listed in a separate site.
Example 5: Export list of Domain Controllers to csv
To export any of these commands just add export-csv -path to the end.
Get-ADDomainController -filter * | Select-Object name | export-csv -path c:\temp\all-domain-controllers.csvExample 6: List available domain controllers in the Current Domain
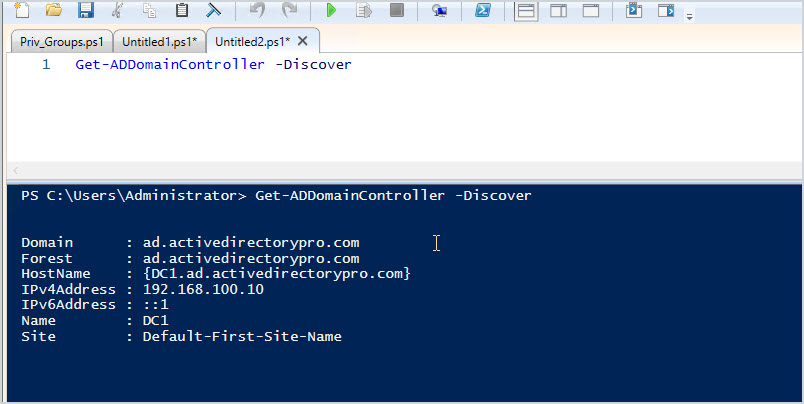
This will not list all domain controllers but will use the DCLocator mechanism to return a discoverable DC.
Get-ADDomainController -DiscoverWhy is this important? The DCLocator is a process used by Windows to locate the closest domain controller. It can be useful to verify that client systems are locating and authenticating to the closest DC. To learn more on this see the Microsoft article How Domain Controllers are located in Windows.
All done! Now you know how to get a list of domain controllers by using PowerShell.

Vey nice and through explanation.