This is a detailed guide on how to delegate permissions to group policy objects for a specific user or group.
Table of Contents
- How to Delegate GPO edit Permissions
- Allow a user or group to create GPOs in specific OU
- Delegate permissions to link GPOs to a specific OU
- GPO delegation best practices
In this guide, I’ll be using the group policy management console (GPMC) to give a specific user permissions to edit, create and link GPOs. You can also use these steps to delegate access to a group.
How to Delegate GPO edit Permissions
By default, the authenticated users group has read permissions on GPOs, this will give all domain users the permissions to read and apply the GPO.
If a user was to open the group policy management console and try to edit a GPO, the edit option would be disabled.
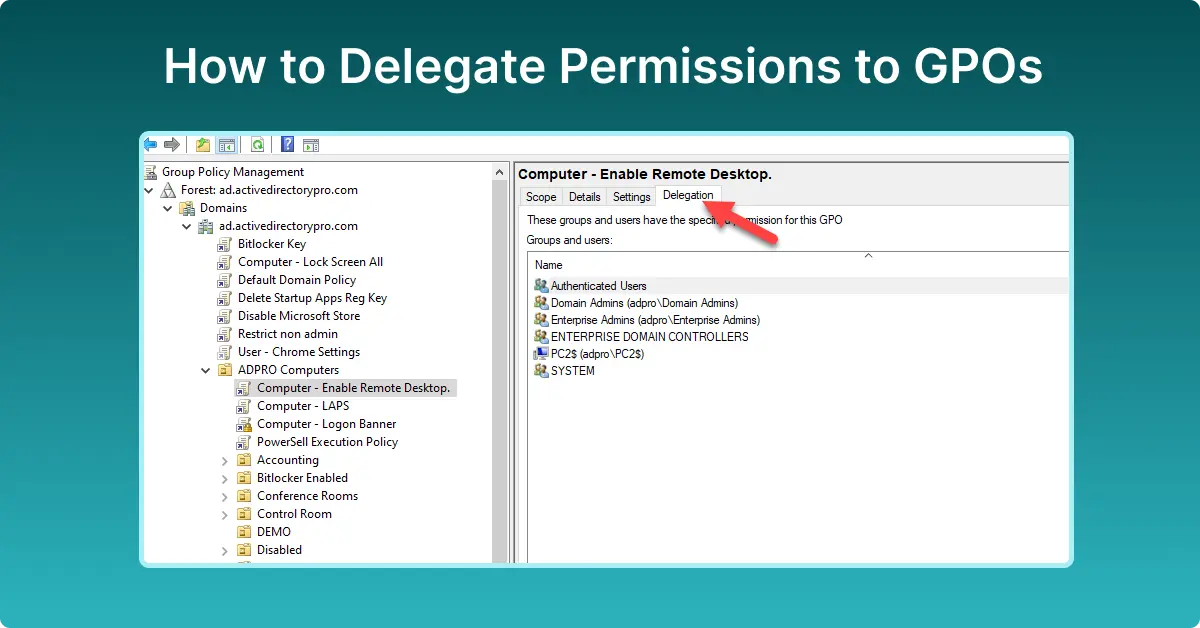
To give a user or group permissions to edit a GPO follow these steps.
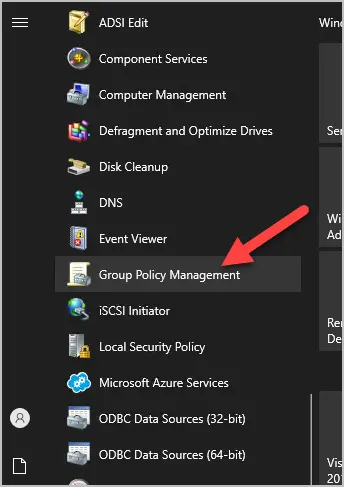
Step #1: Open the group policy management console
Step #2: Click the delegation tab
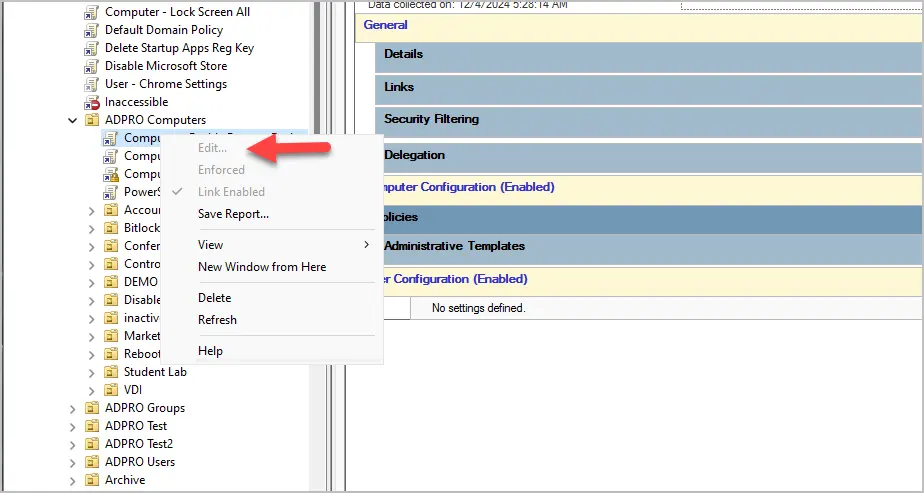
Browse to the GPO you want to delegate edit permissions on and click the “Delegation” tab.
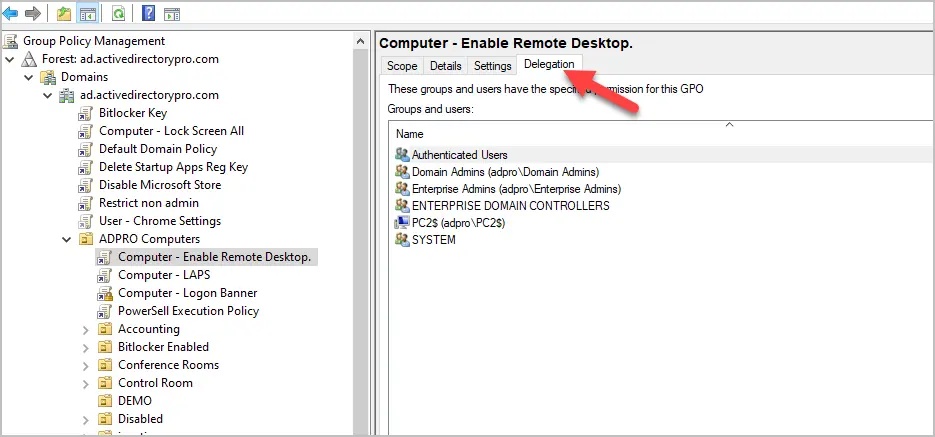
Step #3: Click Add
On the delegation tab click the add button.
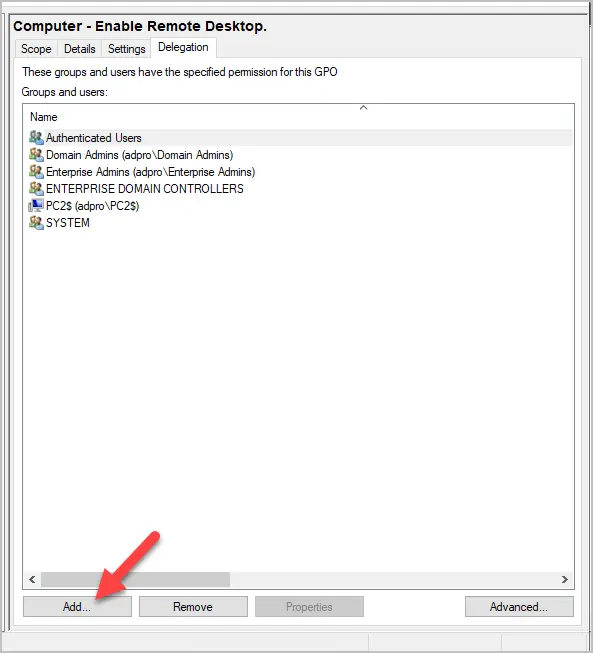
Step #4: Add user or group
In this example, I’m going to give a specific user rights to edit the GPO.
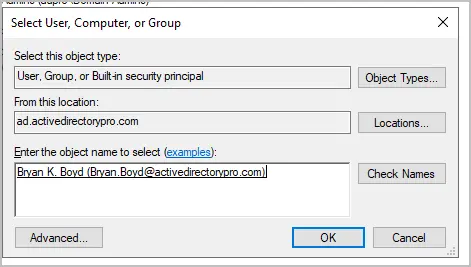
Enter the user or group name and click “OK”. You can also click the advanced button to search active directory.
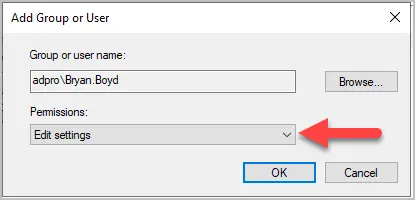
Step #5: Set edit permissions
In the pop-up box change the permissions to “Edit settings” and click “OK”.
The user or group should now have permissions to edit the GPO.
Note: The user will need to have the group police management console installed.
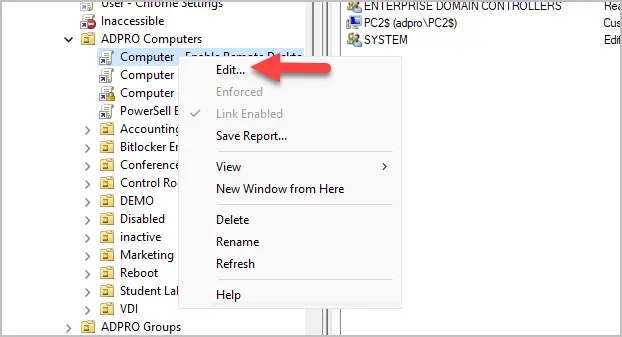
Allow a user or group to create GPOs in specific OU
Note: There is no such thing as create GPOs in an OU. GPOs are created in the domain and then linked to an OU.
To allow a user to create new GPOs and link them to a specific OU follow these steps.
Step 1. Open group policy management console
Step 2. Select “Group Policy Objects”
Expand domains and your domain then select “Group Policy Objects”.
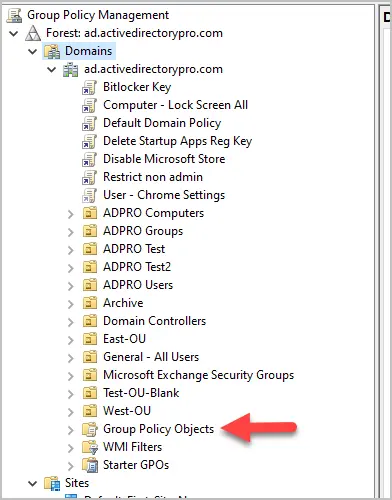
Step 3. Click “Add”
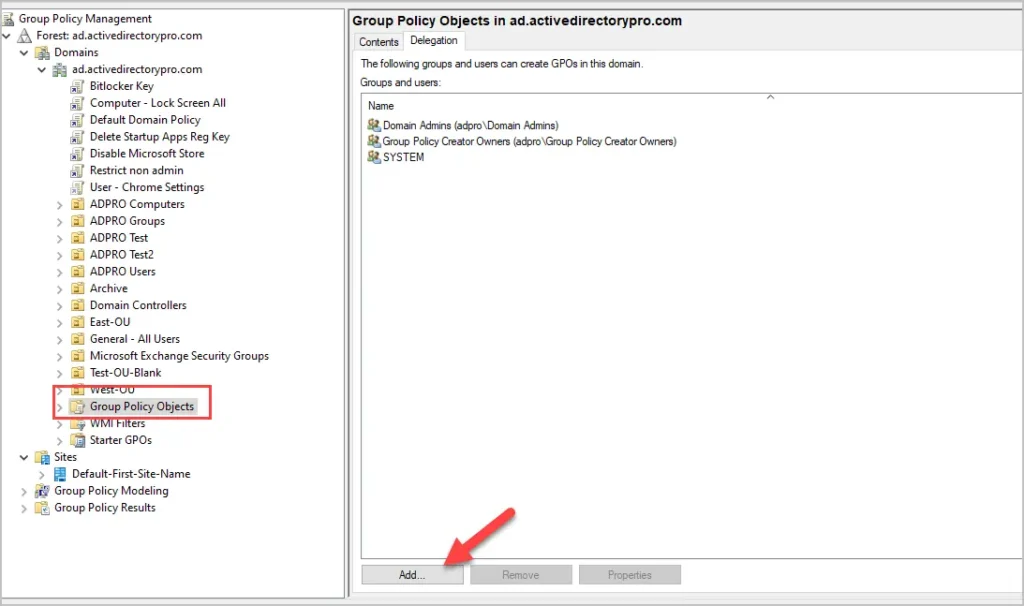
Step 4. Enter the user or group and click “OK”.

At this point the user or group can create new GPOs but cannot link them to an OU or the domain.
Step 5. Select the OU
Select the OU you want to delegate permissions to create new GPOs in (link to).
Click the “Delegate” tab and click “Add”.
In this example, I’m selecting my “Accounting” OU.
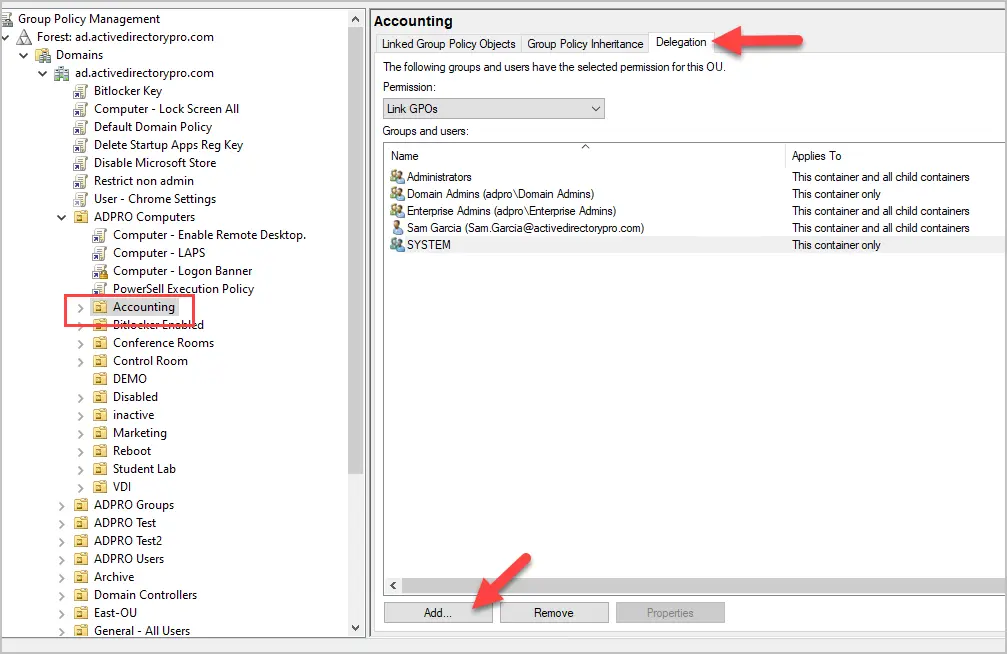
Enter the user or group and click “OK”.
In the popup select the permissions and click “OK.
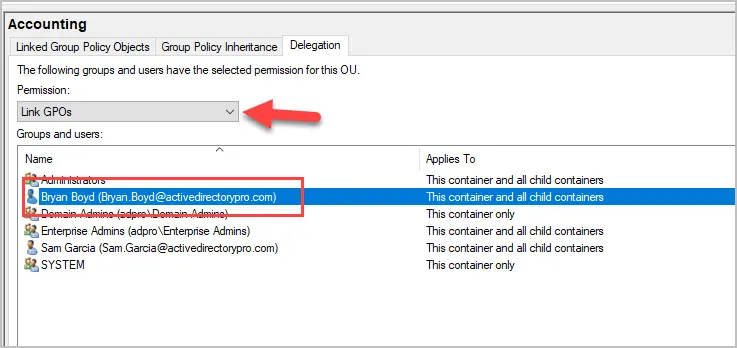
Now the user can create and link GPOs to the “Accounting” OU.
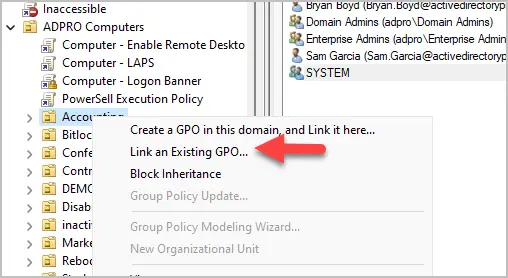
But if the user tries to create and link a GPO to another OU it is not enabled. In the screenshot below, you can see the user tried to create a GPO in the Marketing OU but the options are not enabled. This is expected and is want you want. You don’t want to delegate access to create and link GPOs to all OUs.
Delegate permissions to link GPOs to a specific OU
If you only need a user to link GPOs to an OU follow these steps. This will not allow the user to create new GPOs but link existing ones.
- Open group policy management console
- Click the “delegation” tab
- Click “Add”
- Enter the user or group and click “OK”.
- Select the permissions you want to grant and click “OK”.
When completed it should look like the screenshot below for the user or group you selected.

GPO delegation best practices
- Use groups for delegation
- Delegate permissions to security groups rather than individual accounts. This makes it easier to manage when employees change roles or leaves the company. In this article, I used an individual account rather than a group. My domain is a lab environment only.
- Do not allow link delegation to the domain level
- I would not delegate permissions to link GPOs to the domain level, leave this task to the domain administrators. Only allow non admins to create and link GPOs to specific OUs.
- Change Management
- Even if you delegate GPO responsibilities you should still have a change management process in place. Any new or modifications to GPOs should go through an approval process.
- Documentation
- Keep detail documentation of which users have permissions to create, edit and link GPOs. Using groups will make this easier as you can use the notes section for details.
- Audit and monitor GPOs
- It’s recommended to regularly audit and monitor changes to GPOs. Changes to GPOs are stored in the windows event logs. You can audit GPO permissions with PowerShell and 3rd party tools.
Conclusion
Delegating GPO permissions is an essential part of managing a Windows Active Directory environment, especially in large organizations. This allows you to delegate GPO responsibilities to other staff members to help streamline management of IT assets. By following best practices, you can reduce the risk of allow the wrong users to make changes to GPOs while still being in control of policies.