In this guide, you will learn how to check NTFS permissions on Windows shared folders.
There are times when you need to check and analyze the security permissions on shared folders to verify who has access to what. This can be for a security audit or at the request of your supervisor. It is also a good practice to review NTFS permissions from time to time.
Unfortunately, the built-in Windows tools do not provide an easy way to check the NTFS permissions on shared folders.
To work around this issue we can use 3rd party tools to analyze NTFS effective permissions and verify access to files and folders.
Check it out.
What are NTFS Effective Permissions?
NTFS effective permissions are the resultant permissions of a file or folder for a user or group. It is the combination of explicit and inherited permissions on an object. In other words, it’s the permissions a user or group has to a file or folder.
When trying to determine the effective permissions you need to consider the following:
- Group Membership
- Inherited Permissions
- Nested groups
- Explicit deny permissions
- Local group membership
When you create a new file or folder, it will either take the operating system’s defaults or inherit permissions from a parent folder.
Seems straightforward right? Yes and No
Depending on how your network shares are structured and how granular you get with access, it can become a big tangled mess.
But, that is not the focus of this tutorial.
Let’s move on to some examples of viewing effective access.
Steps to View NTFS Effective Permissions
In this video, I walk through how to view the effect NTFS permissions on a network share. This is done on Windows Server 2016, the steps are very similar on other Windows versions.

Although the above methods work just fine, let’s take a look at an even faster and more efficient way of checking NTFS permissions.
For this method, I’ll be using the SolarWinds permissions Analyzer tool.
Not only does this tool quickly analyze the NTFS permissions it also analyzes the share permissions.
Step 1: Download and Install Permissions Analyzer
Step 2: Configure Permissions Analyzer
Connect the permissions analyzer to your Active Directory.
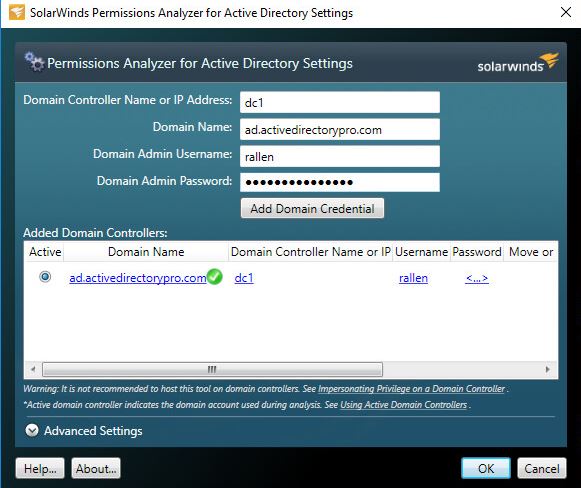
Now, select the user or group that you want to analyze, then the file or folder, and click analyze.
In this example, I will check the user Amanda Gord’s permissions to the HR share.
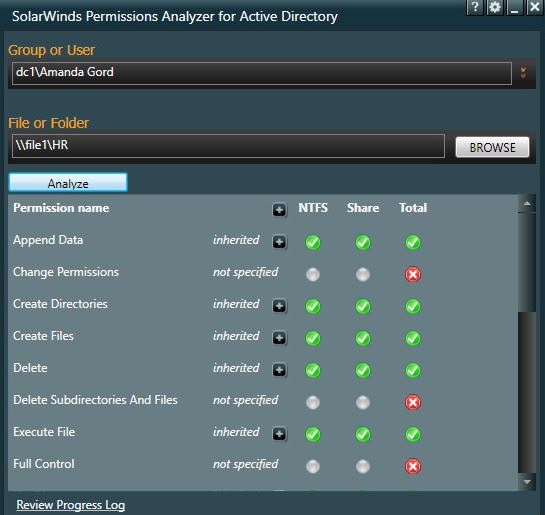
Just with a few clicks, I’m able to see the effective permissions this user has to the HR folder. I can also check the access for Security groups.
Check NTFS Permissions on all folders
In this example, I’ll use the NTFS Permissions Reporter tool that is available with the AD Pro Toolkit. This tool can check the NTFS permissions on the root and all subfolders of a shared folder. This tool will display additional details like the directory owner, rights, and permission type. See the steps below.
Step 1: Select NTFS Permissions
Click here to download a free trial.
From the left menu select the NTFS permissions tool.
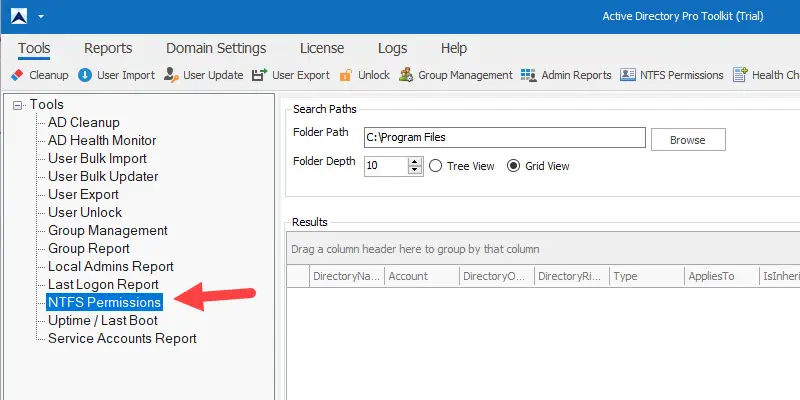
Step 2: Enter folder Path
Next, browse or enter the path to the folder you want to analyze.
Click the “Run” button.
In this example, I’m checking the share folder on server srv-vm1.
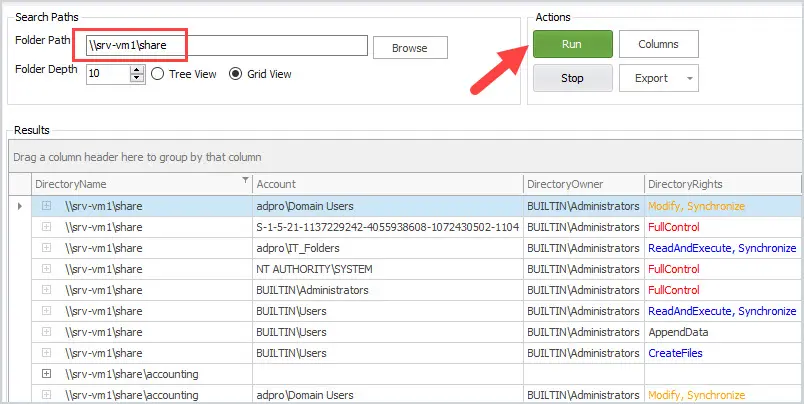
In the results grid, you can see all the folders and the security permissions.
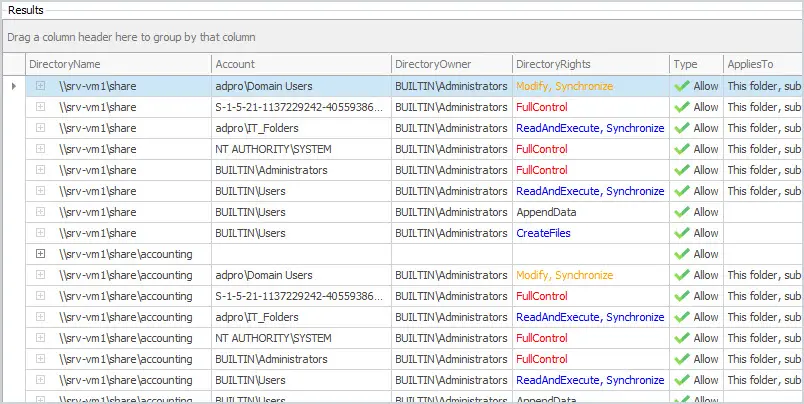
You can sort, filter, and export the results to a CSV file.
Troubleshooting NTFS Permissions With the Permissions Analyzer Tool
Let’s walk through a few more examples of checking permissions with the permission analyzer tool.
The setup:
- HR network share on a Windows Server 2016 file server
- Active Directory Security Groups
- HR Full Security Group: Users in this group have been granted modify access to the HR network share
- HR ReadOnly Security Group: Users in this group have been granted read & execute permissions to the HR network share
- HR Supervisor Folder Security Group: Granted modify permissions to the supervisor folder
Example 1: View Effective Permissions To a Network Shared Folder
I want to verify the effective permissions to the HR network share. I want to make sure there is no unauthorized access.
I’m going to check Dan Warner’s access, he is a member of the HR full group.
TIP: Don’t give users full control to files or folders. This gives them the ability to take ownership, change permissions and really mess things up.
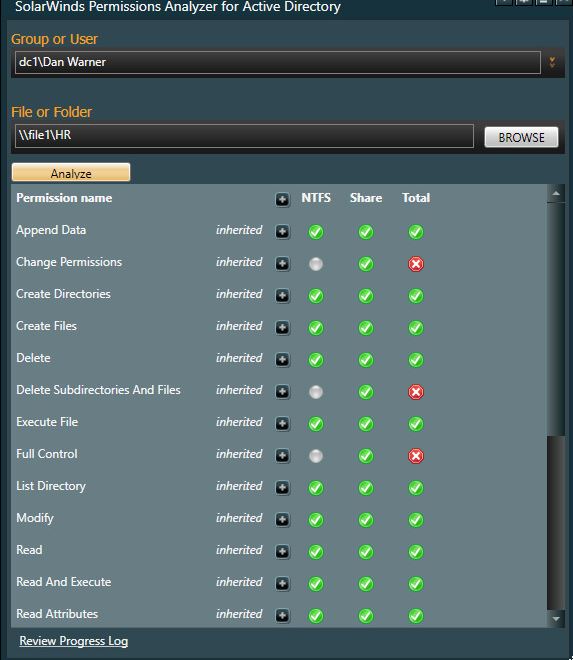
This looks correct. Dan has modify rights but not full control.
Now, let’s look at Sam Rodgers permissions, he is in the HR ReadOnly group.
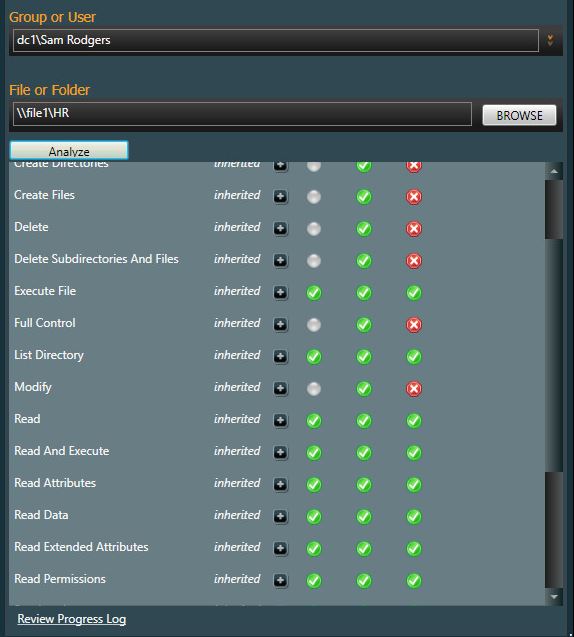
Looks correct, Sam has permissions to read & execute files.
Now, let’s make sure no one outside of HR can get access to the HR folder.
I’m going to check Pam Smith’s access, she is not a member of the HR Full or read only group.
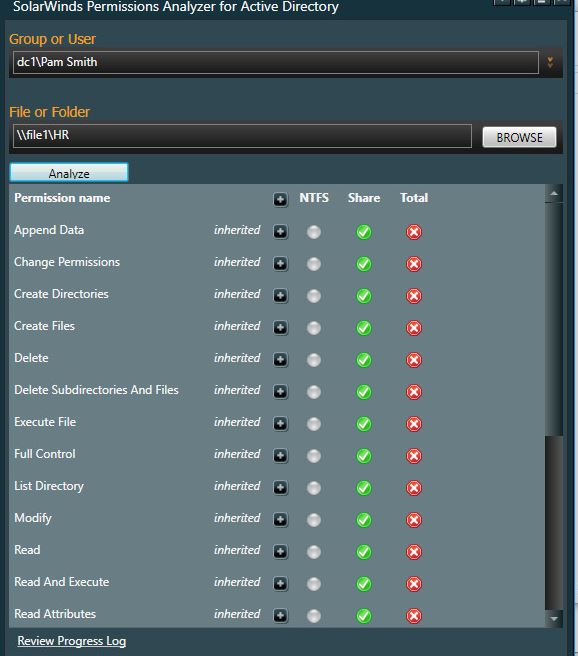
Well, Pam doesn’t have NTFS permissions but she does have share permissions. Even though she won’t be able to access the files and folders she can still see the HR shared folder. There is no need for users to view shares they don’t have access to so I’ll need to remove her share permissions.
This is a good example as to why you should verify and audit file and folder access.
Example 2: View Effective Permissions To a Sub Folder
Departments often want sub folders locked down so that only certain users can access them. They often request to have folders several layers deep locked down, I deny these requests because it becomes a nightmare to manage.
The HR department wants to lock down a folder called supervisor to a few users. I created an Active Directory group called HR Supervisor Folder and add the requested users.
The only user I have set up to access the supervisor folder is Amanda Gord so let’s check her effective permissions.
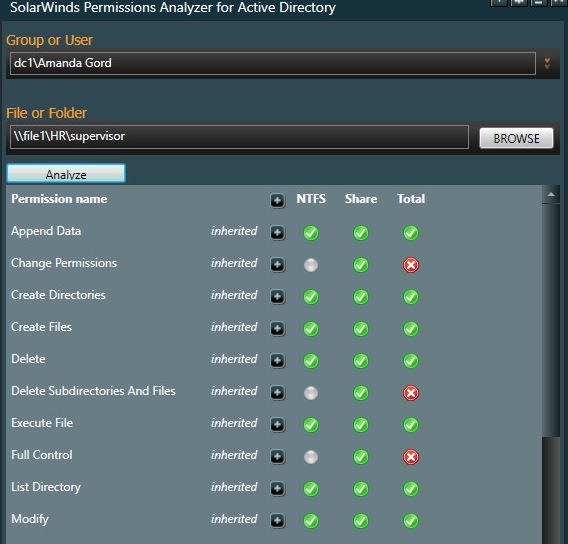
Yes looks good. Amanda has only modify rights.
Now I’ll check Sam Rodgers who is a member of the HR ReadOnly group. I should see that Sam is denied access to this folder.
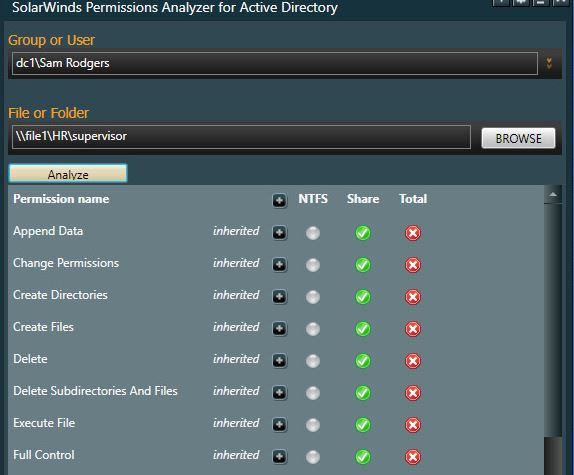
Looks good. Sam you are denied!
It was reported that Dan Warner is able to access the supervisor folder. Dan is not a member of the HR supervisor folder group so he should not have access.
Let me check his effective rights.
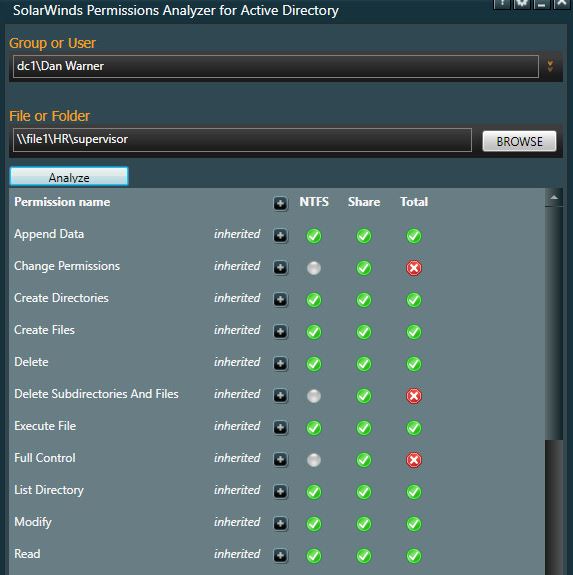
All be damn. Dan does have access even though he is not in the supervisor group.
How could this be?
We can use the permissions analyzer tool to analyze the folder against the groups Dan is a member of.
Dan is a member of Domain Users and HR Full. I’m going to check the HR full groups access.
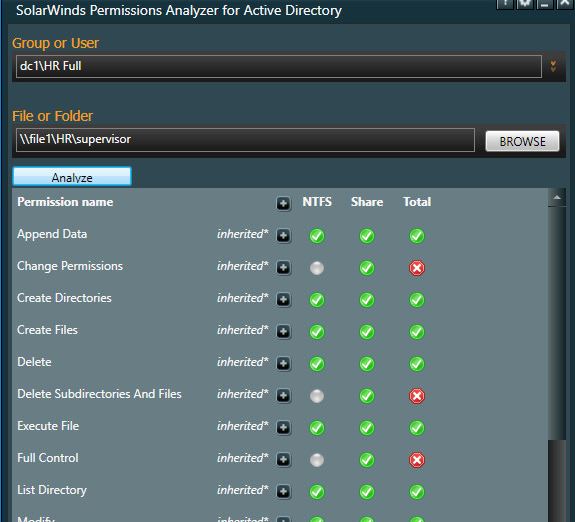
What the bleep. The HR Full group has access to the supervisor folder. This explains why Dan has access.
Let me go check the permissions on the folder.
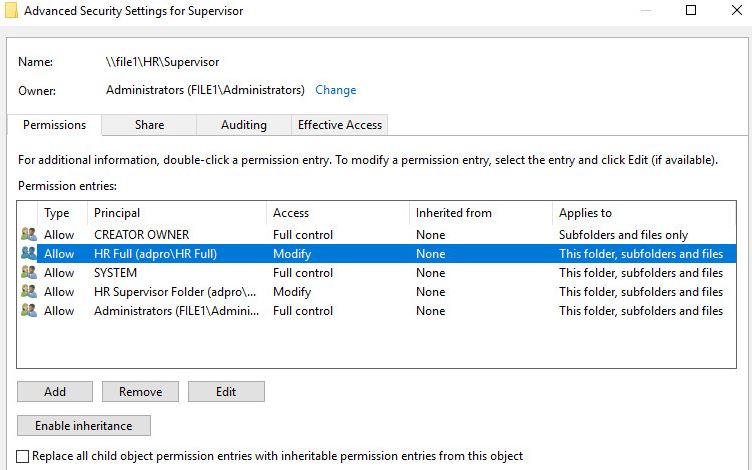
Ah there it is. One of the System Admins forgot to remove the HR Full group from the supervisor folder. This gave anyone in that group access to that folder.
I’ve removed the HR Full group now let me check Dan’s access again.
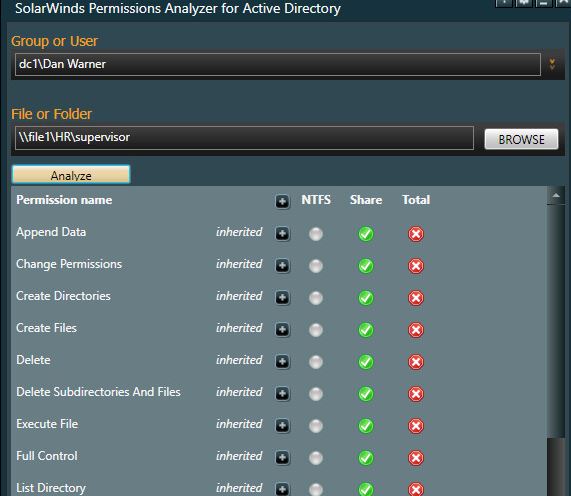
That looks better, Dan no longer has access.
Conclusion
As you can see the permission analyzer tool makes it easy to check for effective NTFS and share permissions. If you haven’t already done so Download your FREE copy of the Permission analyzer and give it a try.
NTFS permissions are critical to ensure unauthorized access to files and folders. One miss configured setting could give a whole group of users access to data they are not authorized for. Knowing how to quickly check file and folder effective permissions helps in troubleshooting and to ensure the rights users and groups and the permissions they only need.
Any questions? Leave a comment below.

Thanks for sharing this information and also thanks to Solar Windows for such a great application!